|
Code Signing
Code signing is the process of digitally signing executables and scripts to confirm the software author and guarantee that the code has not been altered or corrupted since it was signed. The process employs the use of a cryptographic hash to validate authenticity and integrity. Code signing was invented in 1995 by Michael Doyle, as part of the Eolas WebWish browser plug-in, which enabled the use of public-key cryptography to sign downloadable Web app program code using a secret key, so the plug-in code interpreter could then use the corresponding public key to authenticate the code before allowing it access to the code interpreter’s APIs. Code signing can provide several valuable features. The most common use of code signing is to provide security when deploying; in some programming languages, it can also be used to help prevent namespace conflicts. Almost every code signing implementation will provide some sort of digital signature mechanism to verify the identity of the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Digital Signatures And Law
Worldwide, legislation concerning the effect and validity of electronic signatures, including, but not limited to, cryptographic digital signatures, includes: ArgentinaLey Nº 25.506(B.O. 14/12/2001).(B.O. 20/12/2002).(B.O. 13/06/06).(B.O. 03/11/14). Bermuda Electronic Transactions Act 1999Certification Service Providers (Relevant Criteria and Security Guidelines) Regulations 2002 Brazil- Brazilian law states that any digital document is valid for the law if it is certified by ICP-Brasil (the official Brazilian PKI) or if it is certified by other PKI and the concerned parties agree as to the validity of the document. Canada - Canadian law distinguishes between the generic "electronic signature" and the "secure electronic signature". Federasecure electronic signature regulationsmake it clear that a secure electronic signature is a digital signature created and verified in a specific manner. Canada'Evidence Actcontains evidentiary presumptions about both the integrity and validity ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
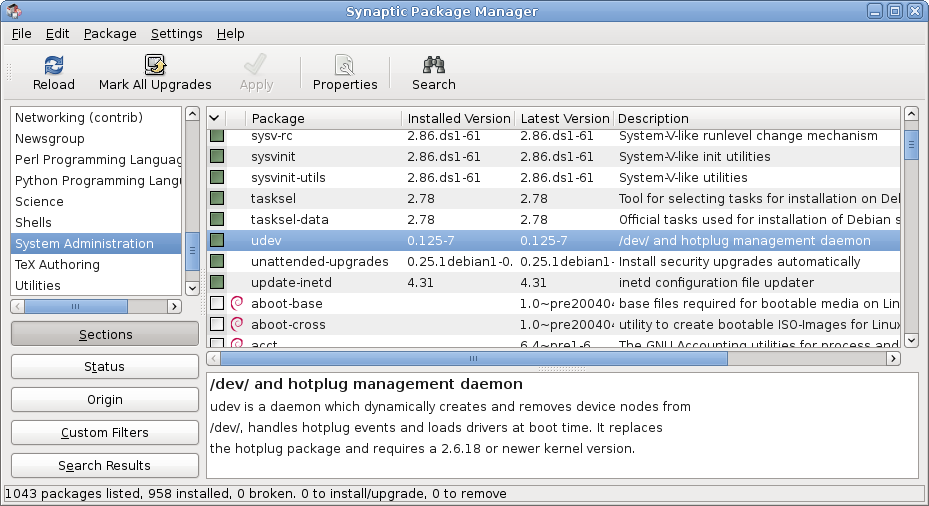
Package Manager
A package manager or package-management system is a collection of software tools that automates the process of installing, upgrading, configuring, and removing computer programs for a computer in a consistent manner. A package manager deals with ''packages'', distributions of software and data in archive files. Packages contain metadata, such as the software's name, description of its purpose, version number, vendor, checksum (preferably a cryptographic hash function), and a list of dependencies necessary for the software to run properly. Upon installation, metadata is stored in a local package database. Package managers typically maintain a database of software dependencies and version information to prevent software mismatches and missing prerequisites. They work closely with software repositories, binary repository managers, and app stores. Package managers are designed to eliminate the need for manual installs and updates. This can be particularly useful for large ent ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Strong Key
Strong Key is a naming convention used in computer programming. There can be more than one component (e.g.: DLL) with the same naming, but with different versions. This can lead to many conflicts. A Strong Key (also called SN Key or Strong Name) is used in the Microsoft .NET Framework to uniquely identify a component. This is done partly with Public-key cryptography. Strong keys or names provide security of reference from one component to another or from a root key to a component. This is not the same as tamper resistance of the file containing any given component. Strong names also are a countermeasure against dll hell In computing, DLL Hell is a term for the complications that arise when one works with dynamic-link libraries (DLLs) used with Microsoft Windows operating systems, particularly legacy 16-bit editions, which all run in a single memory space. DLL H .... This key is produced by another computer program as a pair. References External linksCodeProject: Strong Name ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Random-access Memory
Random-access memory (RAM; ) is a form of computer memory that can be read and changed in any order, typically used to store working data and machine code. A random-access memory device allows data items to be read or written in almost the same amount of time irrespective of the physical location of data inside the memory, in contrast with other direct-access data storage media (such as hard disks, CD-RWs, DVD-RWs and the older magnetic tapes and drum memory), where the time required to read and write data items varies significantly depending on their physical locations on the recording medium, due to mechanical limitations such as media rotation speeds and arm movement. RAM contains multiplexing and demultiplexing circuitry, to connect the data lines to the addressed storage for reading or writing the entry. Usually more than one bit of storage is accessed by the same address, and RAM devices often have multiple data lines and are said to be "8-bit" or "16-bit", etc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
App Store (iOS)
The App Store is an app store platform, developed and maintained by Apple Inc., for mobile apps on its iOS and iPadOS operating systems. The store allows users to browse and download approved apps developed within Apple's iOS Software Development Kit. Apps can be downloaded on the iPhone, iPod Touch, or the iPad, and some can be transferred to the Apple Watch smartwatch or 4th-generation or newer Apple TVs as extensions of iPhone apps. The App Store was opened on July 10, 2008, with an initial 500 applications available. The number of apps peaked at around 2.2 million in 2017, but declined slightly over the next few years as Apple began a process to remove old or 32-bit apps that do not function as intended or that do not follow current app guidelines. , the store features more than 1.8 million apps. While Apple touts the role of the App Store in creating new jobs in the "app economy" and claims to have paid over $155 billion to developers, the App Store has also at ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Xcode
Xcode is Apple's integrated development environment (IDE) for macOS, used to develop software for macOS, iOS, iPadOS, watchOS, and tvOS. It was initially released in late 2003; the latest stable release is version 14.2, released on December 13, 2022, via the Mac App Store with macOS Monterey. The software suite is offered free of charge. Registered developers can download preview releases and prior versions of the suite through the Apple Developer website. Xcode includes command-line tools which enable UNIX-style development via the Terminal app in macOS. They can also be downloaded and installed without the GUI. Major features Xcode supports source code for the programming languages: C, C++, Objective-C, Objective-C++, Java, AppleScript, Python, Ruby, ResEdit (Rez), and Swift, with a variety of programming models, including but not limited to Cocoa, Carbon, and Java. Third parties have added support for GNU Pascal, Free Pascal, Ada, C#, Go, Perl, and D. Xcode can ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Trust On First Use
Trust on first use (TOFU), or trust upon first use (TUFU), is an authentication scheme used by client software which needs to establish a trust relationship with an unknown or not-yet-trusted endpoint. In a TOFU model, the client will try to look up the endpoint's identifier, usually either the public identity key of the endpoint, or the fingerprint of said identity key, in its local trust database. If no identifier exists yet for the endpoint, the client software will either prompt the user to confirm they have verified the purported identifier is authentic, or if manual verification is not assumed to be possible in the protocol, the client will simply trust the identifier which was given and record the trust relationship into its trust database. If in a subsequent connection a different identifier is received from the opposing endpoint, the client software will consider it to be untrusted. TOFU implementations In the SSH protocol, most client software (though not all) will, up ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SmartScreen
SmartScreen (officially called Windows SmartScreen, Windows Defender SmartScreen and SmartScreen Filter in different places) is a cloud-based anti-phishing and anti-malware component included in several Microsoft products, including operating systems Windows 8 and later, the applications Internet Explorer, Microsoft Edge. SmartScreen intelligence is also used in the backend of Microsoft's online services such as the web app Outlook.com and Microsoft Bing search engine. SmartScreen as a business unit includes the intelligence platform, backend, serving frontend, UX, policy, expert graders, and closed-loop intelligence (including machine learning and statistical techniques) designed to help protect Microsoft customers against safety threats like social engineering and drive-by downloads. SmartScreen in Internet Explorer Internet Explorer 7: Phishing Filter SmartScreen was first introduced in Internet Explorer 7, then known as the Phishing Filter. Phishing Filter does not check ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Extended Validation
An Extended Validation Certificate (EV) is a certificate conforming to X.509 that proves the legal entity of the owner and is signed by a certificate authority key that can issue EV certificates. EV certificates can be used in the same manner as any other X.509 certificates, including securing web communications with HTTPS and signing software and documents. Unlike domain-validated certificates and organization-validation certificates, EV certificates can be issued only by a subset of certificate authorities (CAs) and require verification of the requesting entity's legal identity before certificate issuance. As of February 2021, all major web browsers (Google Chrome, Mozilla Firefox, Microsoft Edge and Apple Safari) have menus which show the EV status of the certificate and the verified legal identity of EV certificates. Mobile browsers typically display EV certificates the same way they do Domain Validation (DV) and Organization Validation (OV) certificates. Of the ten most po ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Private Key
Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a public key and a corresponding private key. Key pairs are generated with cryptographic algorithms based on mathematical problems termed one-way functions. Security of public-key cryptography depends on keeping the private key secret; the public key can be openly distributed without compromising security. In a public-key encryption system, anyone with a public key can encrypt a message, yielding a ciphertext, but only those who know the corresponding private key can decrypt the ciphertext to obtain the original message. For example, a journalist can publish the public key of an encryption key pair on a web site so that sources can send secret messages to the news organization in ciphertext. Only the journalist who knows the corresponding private key can decrypt the ciphertexts to obtain the sources' messages—an eavesdro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Public Key Infrastructure
A public key infrastructure (PKI) is a set of roles, policies, hardware, software and procedures needed to create, manage, distribute, use, store and revoke digital certificates and manage public-key encryption. The purpose of a PKI is to facilitate the secure electronic transfer of information for a range of network activities such as e-commerce, internet banking and confidential email. It is required for activities where simple passwords are an inadequate authentication method and more rigorous proof is required to confirm the identity of the parties involved in the communication and to validate the information being transferred. In cryptography, a PKI is an arrangement that ''binds'' public keys with respective identities of entities (like people and organizations). The binding is established through a process of registration and issuance of certificates at and by a certificate authority (CA). Depending on the assurance level of the binding, this may be carried out by an aut ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |