|
Browser History
Web browsing history refers to the list of web pages a user has visited, as well as associated metadata such as page title and time of visit. It is usually stored locally by web browsers in order to provide the user with a history list to go back to previously visited pages. It can reflect the user's interests, needs, and browsing habits.Du, Weidman, Zhenyu Cheryl Qian, Paul Parsons, Yingjie Victor Chen. 2018. “Personal Web Library: organizing and visualizing Web browsing history”. ''International Journal of Web Information Systems'' 14(2): 212-232. All major browsers have a private browsing mode in which browsing history is not recorded. This is to protect against browsing history being collected by third parties for targeted advertising or other purposes. Applications Local history Locally stored browsing history can facilitate rediscovering lost previously visited web pages of which one only has a vague memory in mind, or pages difficult to find due to being located ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Status Quo
is a Latin phrase meaning the existing state of affairs, particularly with regard to social, political, religious or military issues. In the sociological sense, the ''status quo'' refers to the current state of social structure and/or values. With regard to policy debate, it means how conditions are, contrasted with a possible change. For example: "The countries are now trying to maintain the ''status quo'' with regard to their nuclear arsenals." To maintain the ''status quo'' is to keep things the way they presently are. The related phrase '' status quo ante'', literally "the status before", refers to the state of affairs that existed previously. Political usage Via social movements the status quo might be overhauled. These seek to alleviate or prevent a particular issue and often to shape social feeling and cultural expression of a society or nation. The status quo is at least in part rejected by their protagonists – progressives – leading the movement. Advo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Whitelisting
A whitelist, allowlist, or passlist is a mechanism which explicitly allows some identified entities to access a particular privilege, service, mobility, or recognition i.e. it is a List (information), list of things allowed when everything is denied by default. It is the opposite of a Blacklist (computing), blacklist, which is a list of things denied when everything is allowed by default. Email whitelists Spam filters often include the ability to "whitelist" certain sender IP addresses, email addresses or domain names to protect their email from being rejected or sent to a junk mail folder. These can be manually maintained by the user or system administrator - but can also refer to externally maintained whitelist services. Non-commercial whitelists Non-commercial whitelists are operated by various non-profit organisations, ISPs, and others interested in blocking spam. Rather than paying fees, the sender must pass a series of tests; for example, their email server must not be an op ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
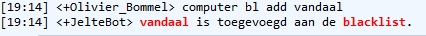
Blacklisting
Blacklisting is the action of a group or authority compiling a blacklist (or black list) of people, countries or other entities to be avoided or distrusted as being deemed unacceptable to those making the list. If someone is on a blacklist, they are seen by a government or other organization as being one of a number of people who cannot be trusted or who is considered to have done something wrong. As a verb, blacklist can mean to put an individual or entity on such a list. Origins of the term The English dramatist Philip Massinger used the phrase "black list" in his 1639 tragedy ''The Unnatural Combat''. After the restoration of the English monarchy brought Charles II of England to the throne in 1660, a list of regicides named those to be punished for the execution of his father. The state papers of Charles II say "If any innocent soul be found in this black list, let him not be offended at me, but consider whether some mistaken principle or interest may not have misled ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ad Blocking
Ad blocking or ad filtering is a software capability for blocking or altering online advertising in a web browser, an application or a network. This may be done using browser extensions or other methods. Technologies and native countermeasures Online advertising exists in a variety of forms, including web banners, pictures, animations, embedded audio and video, text, or pop-up windows, and can even employ audio and video autoplay. Many browsers offer some ways to remove or alter advertisements: either by targeting technologies that are used to deliver ads (such as embedded content delivered through browser plug-ins or via HTML5), targeting URLs that are the source of ads, or targeting behaviors characteristic to ads (such as the use of HTML5 AutoPlay of both audio and video). Prevalence Use of mobile and desktop ad blocking software designed to remove traditional advertising grew by 41% worldwide and by 48% in the U.S. between Q2 2014 and Q2 2015. As of Q2 2015, 45 mill ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Web Tracking
Web tracking is the practice by which operators of websites and third parties collect, store and share information about visitors’ activities on the World Wide Web. Analysis of a user's behaviour may be used to provide content that enables the operator to infer their preferences and may be of interest to various parties, such as advertisers. Web tracking can be part of visitor management. Uses of web tracking The uses of web tracking include the following: * Advertising companies actively collect information about users and make profiles that are used to individualize advertisements. User activities include websites visited, watched videos, interactions on social networks, and online transactions. Websites like Netflix, YouTube collect information about what shows users watch, which helps them suggest more shows that they might like. Search engines like Google will keep a record of what users search for, which could help them suggest more relevant searches in the future. * L ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Avast
Avast Software s.r.o. is a Czech multinational cybersecurity software company headquartered in Prague, Czech Republic that researches and develops computer security software, machine learning and artificial intelligence. Avast has more than 435 million monthly active users and the second largest market share among anti-malware application vendors worldwide as of April 2020. The company has approximately 1,700 employees across its 25 offices worldwide. In July 2021, NortonLifeLock, an American cybersecurity company, announced that it is in talks to merge with Avast Software. In August 2021, Avast's board of directors agreed to an offer of US$8 billion. Avast was founded by Pavel Baudiš and Eduard Kučera in 1988 as a cooperative. It had been a private company since 2010 and had its IPO in May 2018. In July 2016, Avast acquired competitor AVG Technologies for $1.3 billion. At the time, AVG was the third-ranked antivirus product. It was dual-listed on the Prague Stock Exc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
AOL Search Data Leak
In 2006, the internet company AOL released a large excerpt from its Web search query logs to the public. AOL did not identify users in the report, but personally identifiable information was present in many of the queries. This allowed some users to be identified by their search queries. Although AOL took down the file within a few days, it had already been widely copied and still remains available. Overview On August 4, 2006, AOL Research, headed by Dr. Abdur Chowdhury, released a compressed text file on one of its websites containing twenty million search queries for over 650,000 users over a 3-month period; it was intended for research. AOL deleted the file on their site by August 7, but not before it had been copied and distributed on the Internet. AOL did not identify users in the report; however, personally identifiable information was present in many of the queries. As the queries were attributed by AOL to particular user numerically identified accounts, an individual ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Avast Software Logo 2016
Avast Software s.r.o. is a Czech multinational cybersecurity software company headquartered in Prague, Czech Republic that researches and develops computer security software, machine learning and artificial intelligence. Avast has more than 435 million monthly active users and the second largest market share among anti-malware application vendors worldwide as of April 2020. The company has approximately 1,700 employees across its 25 offices worldwide. In July 2021, NortonLifeLock, an American cybersecurity company, announced that it is in talks to merge with Avast Software. In August 2021, Avast's board of directors agreed to an offer of US$8 billion. Avast was founded by Pavel Baudiš and Eduard Kučera in 1988 as a cooperative. It had been a private company since 2010 and had its IPO in May 2018. In July 2016, Avast acquired competitor AVG Technologies for $1.3 billion. At the time, AVG was the third-ranked antivirus product. It was dual-listed on the Prague Stock Exc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Third-party Cookies
HTTP cookies (also called web cookies, Internet cookies, browser cookies, or simply cookies) are small blocks of data created by a web server while a user is browsing a website and placed on the user's computer or other device by the user's web browser. Cookies are placed on the device used to access a website, and more than one cookie may be placed on a user's device during a session. Cookies serve useful and sometimes essential functions on the web. They enable web servers to store stateful information (such as items added in the shopping cart in an online store) on the user's device or to track the user's browsing activity (including clicking particular buttons, logging in, or recording which pages were visited in the past). They can also be used to save for subsequent use information that the user previously entered into form fields, such as names, addresses, passwords, and payment card numbers. Authentication cookies are commonly used by web servers to authenticate t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
First-party Cookie
HTTP cookies (also called web cookies, Internet cookies, browser cookies, or simply cookies) are small blocks of Data (computing), data created by a web server while a User (computing), user is browsing a website and placed on the user's computer or other device by the user's web browser. Cookies are placed on the device used to access a website, and more than one cookie may be placed on a user's device during a session. Cookies serve useful and sometimes essential functions on the World Wide Web, web. They enable web servers to store program state, stateful information (such as items added in the shopping cart in an Online shopping, online store) on the user's device or to track the user's browsing activity (including clicking particular buttons, access control, logging in, or recording which Web browsing history, pages were visited in the past). They can also be used to save for subsequent use information that the user previously entered into Form (HTML), form fields, such as ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Potentially Unwanted Program
A potentially unwanted program (PUP) or potentially unwanted application (PUA) is software that a user may perceive as unwanted or unnecessary. It is used as a subjective tagging criterion by security and parental control products. Such software may use an implementation that can compromise privacy or weaken the computer's security. Companies often bundle a wanted program download with a wrapper application and may offer to install an unwanted application, and in some cases without providing a clear opt-out method. Antivirus companies define the software bundled as potentially unwanted programs which can include software that displays intrusive advertising (adware), or tracks the user's Internet usage to sell information to advertisers (spyware), injects its own advertising into web pages that a user looks at, or uses premium SMS services to rack up charges for the user. A growing number of open-source software projects have expressed dismay at third-party websites wrapping their d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |