|
Black Hole (networking)
In networking, a black hole refers to a place in the network where incoming or outgoing traffic is silently discarded (or "dropped"), without informing the source that the data did not reach its intended recipient. When examining the topology of the network, the black holes themselves are invisible, and can only be detected by monitoring the lost traffic; hence the name as astronomical Black holes cannot be directly observed. Dead addresses The most common form of black hole is simply an IP address that specifies a host machine that is not running or an address to which no host has been assigned. Even though TCP/IP provides a means of communicating the delivery failure back to the sender via ICMP, traffic destined for such addresses is often just dropped. Note that a dead address will be undetectable only to protocols that are both connectionless and unreliable (e.g., UDP). Connection-oriented or reliable protocols (TCP, RUDP) will either fail to connect to a dead addr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Networking
A computer network is a set of computers sharing resources located on or provided by network nodes. The computers use common communication protocols over digital interconnections to communicate with each other. These interconnections are made up of telecommunication network technologies, based on physically wired, optical, and wireless radio-frequency methods that may be arranged in a variety of network topologies. The nodes of a computer network can include personal computers, servers, networking hardware, or other specialised or general-purpose hosts. They are identified by network addresses, and may have hostnames. Hostnames serve as memorable labels for the nodes, rarely changed after initial assignment. Network addresses serve for locating and identifying the nodes by communication protocols such as the Internet Protocol. Computer networks may be classified by many criteria, including the transmission medium used to carry signals, bandwidth, communications protocols ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Routing Table
In computer networking, a routing table, or routing information base (RIB), is a data table stored in a router or a network host that lists the routes to particular network destinations, and in some cases, metrics (distances) associated with those routes. The routing table contains information about the topology of the network immediately around it. The construction of routing tables is the primary goal of routing protocols. Static routes are entries that are fixed, rather than resulting from routing protocols and network topology discovery procedures. Overview A routing table is analogous to a distribution map in package delivery. Whenever a node needs to send data to another node on a network, it must first know ''where'' to send it. If the node cannot directly connect to the destination node, it has to send it via other nodes along a route to the destination node. Each node needs to keep track of which way to deliver various packages of data, and for this it uses a routing ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spamming
Spamming is the use of messaging systems to send multiple unsolicited messages (spam) to large numbers of recipients for the purpose of commercial advertising, for the purpose of non-commercial proselytizing, for any prohibited purpose (especially the fraudulent purpose of phishing), or simply repeatedly sending the same message to the same user. While the most widely recognized form of spam is email spam, the term is applied to similar abuses in other media: instant messaging spam, Usenet newsgroup spam, Web search engine spam, spam in blogs, wiki spam, online classified ads spam, mobile phone messaging spam, Internet forum spam, junk fax transmissions, social spam, spam mobile apps, television advertising and file sharing spam. It is named after Spam, a luncheon meat, by way of a Monty Python sketch about a restaurant that has Spam in almost every dish in which Vikings annoyingly sing "Spam" repeatedly. Spamming remains economically viable because advertisers have n ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Domain Name System
The Domain Name System (DNS) is a hierarchical and distributed naming system for computers, services, and other resources in the Internet or other Internet Protocol (IP) networks. It associates various information with domain names assigned to each of the associated entities. Most prominently, it translates readily memorized domain names to the numerical IP addresses needed for locating and identifying computer services and devices with the underlying network protocols. The Domain Name System has been an essential component of the functionality of the Internet since 1985. The Domain Name System delegates the responsibility of assigning domain names and mapping those names to Internet resources by designating authoritative name servers for each domain. Network administrators may delegate authority over sub-domains of their allocated name space to other name servers. This mechanism provides distributed and fault tolerance, fault-tolerant service and was designed to avoid a single ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Card
A network interface controller (NIC, also known as a network interface card, network adapter, LAN adapter or physical network interface, and by similar terms) is a computer hardware component that connects a computer to a computer network. Early network interface controllers were commonly implemented on expansion cards that plugged into a computer bus. The low cost and ubiquity of the Ethernet standard means that most newer computers have a network interface built into the motherboard, or is contained into a USB-connected dongle. Modern network interface controllers offer advanced features such as interrupt and DMA interfaces to the host processors, support for multiple receive and transmit queues, partitioning into multiple logical interfaces, and on-controller network traffic processing such as the TCP offload engine. Purpose The network controller implements the electronic circuitry required to communicate using a specific physical layer and data link layer standard su ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Classless Inter-Domain Routing
Classless Inter-Domain Routing (CIDR ) is a method for allocating IP addresses and for IP routing. The Internet Engineering Task Force introduced CIDR in 1993 to replace the previous classful network addressing architecture on the Internet. Its goal was to slow the growth of routing tables on routers across the Internet, and to help slow the rapid exhaustion of IPv4 addresses. IP addresses are described as consisting of two groups of bits in the address: the most significant bits are the network prefix, which identifies a whole network or subnet, and the least significant set forms the ''host identifier'', which specifies a particular interface of a host on that network. This division is used as the basis of traffic routing between IP networks and for address allocation policies. Whereas classful network design for IPv4 sized the network prefix as one or more 8-bit groups, resulting in the blocks of Class A, B, or C addresses, under CIDR address space is allocated to Internet ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
State (computer Science)
In information technology and computer science, a system is described as stateful if it is designed to remember preceding events or user interactions; the remembered information is called the state of the system. The set of states a system can occupy is known as its state space. In a discrete system, the state space is countable and often finite. The system's internal behaviour or interaction with its environment consists of separately occurring individual actions or events, such as accepting input or producing output, that may or may not cause the system to change its state. Examples of such systems are digital logic circuits and components, automata and formal language, computer programs, and computers. The output of a digital circuit or deterministic computer program at any time is completely determined by its current inputs and its state. Digital logic circuit state Digital logic circuits can be divided into two types: combinational logic, whose output signals are dependen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Collateral Damage
Collateral damage is any death, injury, or other damage inflicted that is an incidental result of an activity. Originally coined by military operations, it is now also used in non-military contexts. Since the development of precision guided munitions in the 1970s, military forces often claim to have gone to great lengths to minimize collateral damage. Critics of use of the term "collateral damage" see it as a euphemism that dehumanizes non-combatants killed or injured during combat, used to reduce the perceived culpability of military leadership in failing to prevent non-combatant casualties. Collateral damage does not include civilian casualties caused by military operations that are intended to terrorize or kill enemy civilians (e.g., the bombing of Chongqing during World War II). Etymology The word "collateral" comes from medieval Latin word ''collateralis'', from ''col-'', "together with" + ''lateralis'' (from ''latus'', ''later-'', "side" ) and is otherwise mainly use ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
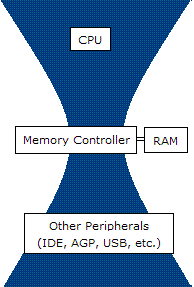
Bottleneck (engineering)
In engineering, a bottleneck is a phenomenon by which the performance or capacity of an entire system is severely limited by a single component. The component is sometimes called a bottleneck point. The term is metaphorically derived from the neck of a bottle, where the flow speed of the liquid is limited by its neck. Formally, a bottleneck lies on a system's critical path and provides the lowest throughput. Bottlenecks are usually avoided by system designers, also a great amount of effort is directed at locating and tuning them. Bottleneck may be for example a processor, a communication link, a data processing software, etc. Bottlenecks in software In computer programming, tracking down bottlenecks (sometimes known as "hot spots" - sections of the code that execute most frequently - i.e. have the highest execution count) is called performance analysis. Reduction is usually achieved with the help of specialized tools, known as performance analyzers or profilers. The objecti ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Core Router
A core router is a router designed to operate in the Internet backbone, or core. To fulfill this role, a router must be able to support multiple telecommunications interfaces of the highest speed in use in the core Internet and must be able to forward IP packets at full speed on all of them. It must also support the routing protocols being used in the core. A core router is distinct from an edge router: edge routers sit at the edge of a backbone network and connect to core routers. History Like the term "supercomputer", the term "core router" refers to the largest and most capable routers of the then-current generation. A router that was a core router when introduced would likely not be a core router ten years later. Although the local area NPL network was using line speeds of 768 kbit/s from 1967, at the inception of the ARPANET (the Internet's predecessor) in 1969, the fastest links were 56 kbit/s. A given routing node had at most six links. The "core router" was a dedicated ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Localhost
In computer networking, localhost is a hostname that refers to the current device used to access it. It is used to access the network services that are running on the host via the loopback network interface. Using the loopback interface bypasses any local network interface hardware. Loopback The local loopback mechanism may be used to run a network service on a host without requiring a physical network interface, or without making the service accessible from the networks the computer may be connected to. For example, a locally installed website may be accessed from a Web browser by the URL it is mainly used for web development purposes ''http://localhost'' to display its home page. The name ''localhost'' normally resolves to the IPv4 loopback address , and to the IPv6 loopback address . Name resolution IPv4 network standards reserve the entire address block 127.0.0.0/8 (more than 16 million addresses) for loopback purposes. Updated by RFC 8190. That means any packet sent ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Denial-of-service Attack
In computing, a denial-of-service attack (DoS attack) is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to a network. Denial of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled. In a distributed denial-of-service attack (DDoS attack), the incoming traffic flooding the victim originates from many different sources. More sophisticated strategies are required to mitigate this type of attack, as simply attempting to block a single source is insufficient because there are multiple sources. A DoS or DDoS attack is analogous to a group of people crowding the entry door of a shop, making it hard for legitimate customers to enter, thus disrupting trade. Criminal perpetrators of DoS attacks oft ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |

.jpg)