|
Best-effort Service
Best-effort delivery describes a network service in which the network does ''not'' provide any guarantee that data is delivered or that delivery meets any quality of service. In a best-effort network, all users obtain best-effort service. Under best-effort, network performance characteristics such as network delay and packet loss depend on the current network traffic load, and the network hardware capacity. When network load increases, this can lead to packet loss, retransmission, packet delay variation, and further network delay, or even timeout and session disconnect. Best-effort can be contrasted with reliable delivery, which can be built on top of best-effort delivery (possibly without latency and throughput guarantees), or with virtual circuit schemes which can maintain a defined quality of service. Network examples Physical services The postal service (''snail mail'') physically delivers letters using a best-effort delivery approach. The delivery of a certain lett ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Service
In computer networking, a network service is an application running at the network application layer and above, that provides data storage, manipulation, presentation, communication or other capability which is often implemented using a client–server or peer-to-peer architecture based on application layer network protocols. Each service is usually provided by a server component running on one or more computers (often a dedicated server computer offering multiple services) and accessed via a network by client components running on other devices. However, the client and server components can both be run on the same machine. Clients and servers will often have a user interface, and sometimes other hardware associated with it. Examples Examples are the Domain Name System (DNS) which translates domain names to Internet protocol (IP) addresses and the Dynamic Host Configuration Protocol (DHCP) to assign networking configuration information to network hosts. Authentication server ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Telephone Exchange
A telephone exchange, telephone switch, or central office is a telecommunications system used in the public switched telephone network (PSTN) or in large enterprises. It interconnects telephone subscriber lines or virtual circuits of digital systems to establish telephone calls between subscribers. In historical perspective, telecommunication terms have been used with different semantics over time. The term ''telephone exchange'' is often used synonymously with ''central office'', a Bell System term. Often, a ''central office'' is defined as a building used to house the inside plant equipment of potentially several telephone exchanges, each serving a certain geographical area. Such an area has also been referred to as the exchange or exchange area. In North America, a central office location may also be identified as a ''wire center'', designating a facility to which a telephone is connected and obtains dial tone. For business and billing purposes, telecommunication carriers defi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Multiplexing
In telecommunications and computer networking, multiplexing (sometimes contracted to muxing) is a method by which multiple analog or digital signals are combined into one signal over a shared medium. The aim is to share a scarce resource - a physical transmission medium. For example, in telecommunications, several telephone calls may be carried using one wire. Multiplexing originated in telegraphy in the 1870s, and is now widely applied in communications. In telephony, George Owen Squier is credited with the development of telephone carrier multiplexing in 1910. The multiplexed signal is transmitted over a communication channel such as a cable. The multiplexing divides the capacity of the communication channel into several logical channels, one for each message signal or data stream to be transferred. A reverse process, known as demultiplexing, extracts the original channels on the receiver end. A device that performs the multiplexing is called a multiplexer (MUX), and a dev ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
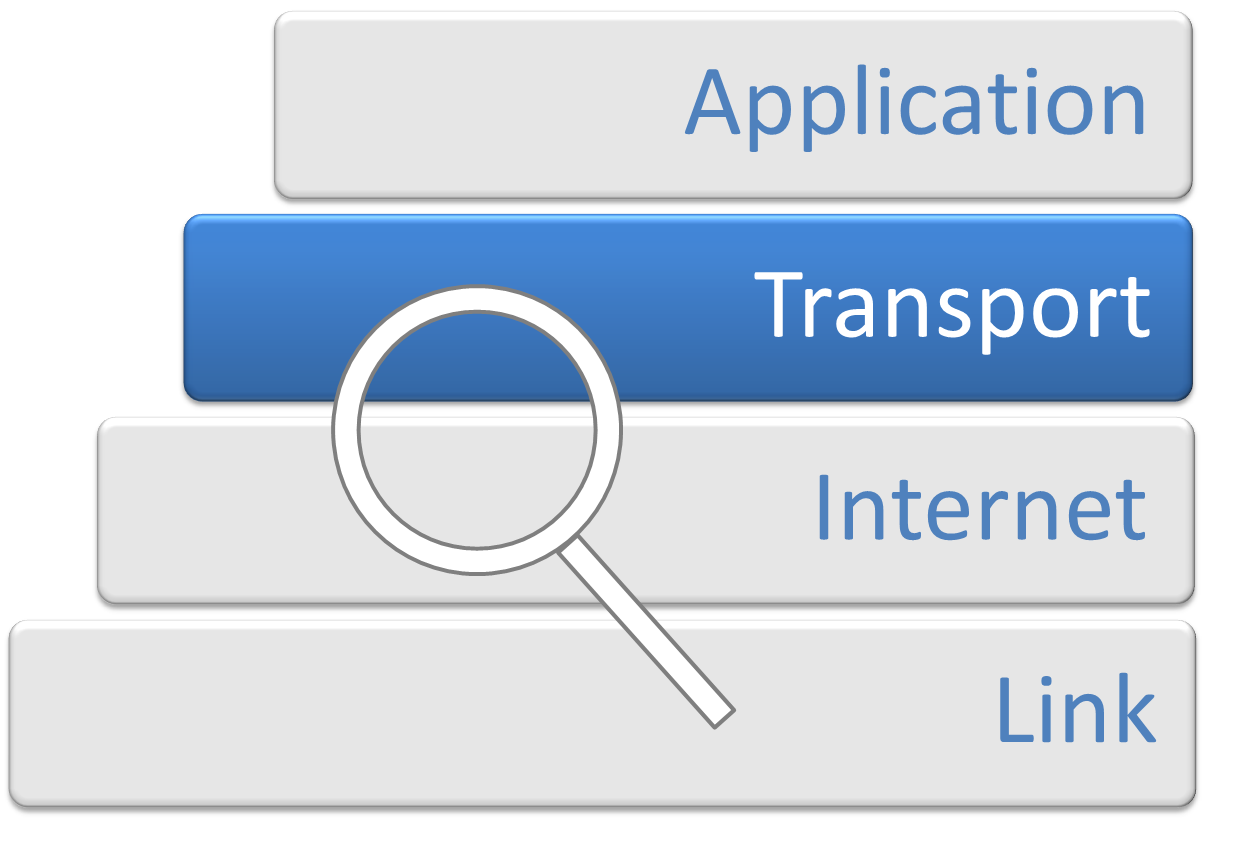
Transport Layer
In computer networking, the transport layer is a conceptual division of methods in the layered architecture of protocols in the network stack in the Internet protocol suite and the OSI model. The protocols of this layer provide end-to-end communication services for applications. It provides services such as connection-oriented communication, reliability, flow control, and multiplexing. The details of implementation and semantics of the transport layer of the Internet protocol suite, which is the foundation of the Internet, and the OSI model of general networking are different. The protocols in use today in this layer for the Internet all originated in the development of TCP/IP. In the OSI model the transport layer is often referred to as Layer 4, or L4, while numbered layers are not used in TCP/IP. The best-known transport protocol of the Internet protocol suite is the Transmission Control Protocol (TCP). It is used for connection-oriented transmissions, whereas the c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Error Detection
In information theory and coding theory with applications in computer science and telecommunication, error detection and correction (EDAC) or error control are techniques that enable reliable delivery of digital data over unreliable communication channels. Many communication channels are subject to channel noise, and thus errors may be introduced during transmission from the source to a receiver. Error detection techniques allow detecting such errors, while error correction enables reconstruction of the original data in many cases. Definitions ''Error detection'' is the detection of errors caused by noise or other impairments during transmission from the transmitter to the receiver. ''Error correction'' is the detection of errors and reconstruction of the original, error-free data. History In classical antiquity, copyists of the Hebrew Bible were paid for their work according to the number of stichs (lines of verse). As the prose books of the Bible were hardly ever ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
User Datagram Protocol
In computer networking, the User Datagram Protocol (UDP) is one of the core communication protocols of the Internet protocol suite used to send messages (transported as datagrams in packets) to other hosts on an Internet Protocol (IP) network. Within an IP network, UDP does not require prior communication to set up communication channels or data paths. UDP uses a simple connectionless communication model with a minimum of protocol mechanisms. UDP provides checksums for data integrity, and port numbers for addressing different functions at the source and destination of the datagram. It has no handshaking dialogues, and thus exposes the user's program to any unreliability of the underlying network; there is no guarantee of delivery, ordering, or duplicate protection. If error-correction facilities are needed at the network interface level, an application may instead use Transmission Control Protocol (TCP) or Stream Control Transmission Protocol (SCTP) which are designed for this ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Transmission Control Protocol
The Transmission Control Protocol (TCP) is one of the main protocols of the Internet protocol suite. It originated in the initial network implementation in which it complemented the Internet Protocol (IP). Therefore, the entire suite is commonly referred to as TCP/IP. TCP provides reliable, ordered, and error-checked delivery of a stream of octets (bytes) between applications running on hosts communicating via an IP network. Major internet applications such as the World Wide Web, email, remote administration, and file transfer rely on TCP, which is part of the Transport Layer of the TCP/IP suite. SSL/TLS often runs on top of TCP. TCP is connection-oriented, and a connection between client and server is established before data can be sent. The server must be listening (passive open) for connection requests from clients before a connection is established. Three-way handshake (active open), retransmission, and error detection adds to reliability but lengthens latency. Applica ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
End-to-end Principle
The end-to-end principle is a design framework in computer networking. In networks designed according to this principle, guaranteeing certain application-specific features, such as reliability and security, requires that they reside in the communicating end nodes of the network. Intermediary nodes, such as gateways and routers, that exist to establish the network, may implement these to improve efficiency but cannot guarantee end-to-end correctness. The essence of what would later be called the end-to-end principle was contained in the work of Paul Baran and Donald Davies on packet-switched networks in the 1960s. Louis Pouzin pioneered the use of the end-to-end strategy in the CYCLADES network in the 1970s. The principle was first articulated explicitly in 1981 by Saltzer, Reed, and Clark. The meaning of the end-to-end principle has been continuously reinterpreted ever since its initial articulation. Also, noteworthy formulations of the end-to-end principle can be found befor ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Protocol
The Internet Protocol (IP) is the network layer communications protocol in the Internet protocol suite for relaying datagrams across network boundaries. Its routing function enables internetworking, and essentially establishes the Internet. IP has the task of delivering packets from the source host to the destination host solely based on the IP addresses in the packet headers. For this purpose, IP defines packet structures that encapsulate the data to be delivered. It also defines addressing methods that are used to label the datagram with source and destination information. IP was the connectionless datagram service in the original Transmission Control Program introduced by Vint Cerf and Bob Kahn in 1974, which was complemented by a connection-oriented service that became the basis for the Transmission Control Protocol (TCP). The Internet protocol suite is therefore often referred to as ''TCP/IP''. The first major version of IP, Internet Protocol Version 4 (IPv4), is the do ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Busy Signal
Reanno Devon Gordon (born 24 January 1979), better known by his stage name Busy Signal, is a Jamaican dancehall reggae artist. Biography Reanno Devon Gordon p/k/a Busy Signal was born in Saint Ann Parish,Johnson, Carolyn (2006)A Very Busy Childhood", ''Jamaica Star'', 21 January 2006, retrieved 1 July 2012 living in areas in West and East Kingston such as Tivoli Gardens, Papine, and Spanish Town. He is a past student of Brown's Town Comprehensive High School. Known as one of the artists leading the contemporary dancehall movement, Busy Signal has been a large part of the scene since 2003, and released his debut single "Step Out" in 2005. A music video for "Step Out" was released shortly afterwards. He was nicknamed Busy Signal by his friends because he is constantly busy. His hit tracks for 2007/2008 were "Nah Go A Jail Again", "Smoke Some High Grade", "Tic Toc" and the track entitled "Unknown Number" has made tremendous airplay and dancehall reviews especially in the Caribbe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Circuit Switching
Circuit switching is a method of implementing a telecommunications network in which two network nodes establish a dedicated communications channel ( circuit) through the network before the nodes may communicate. The circuit guarantees the full bandwidth of the channel and remains connected for the duration of the communication session. The circuit functions as if the nodes were physically connected as with an electrical circuit. Circuit switching originated in analog telephone networks where the network created a dedicated circuit between two telephones for the duration of a telephone call. It contrasts with message switching and packet switching used in modern digital networks in which the trunklines between switching centers carry data between many different nodes in the form of data packets without dedicated circuits. Description The defining example of a circuit-switched network is the early analog telephone network. When a call is made from one telephone to another, swit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
.jpg)