|
Anti-keylogger
An anti-keylogger (or anti–keystroke logger) is a type of software specifically designed for the detection of keystroke logger software; often, such software will also incorporate the ability to delete or at least immobilize hidden keystroke logger software on a computer. In comparison to most anti-virus or anti-spyware software, the primary difference is that an anti-keylogger does not make a distinction between a ''legitimate'' keystroke-logging program and an ''illegitimate'' keystroke-logging program (such as malware); all keystroke-logging programs are flagged and optionally removed, whether they appear to be legitimate keystroke-logging software or not. The anti-keylogger is efficient in managing malicious users. It can detect the keyloggers and terminate them from the system. Use of anti-keyloggers Keyloggers are sometimes part of malware packages downloaded onto computers without the owners' knowledge. Detecting the presence of a keylogger on a computer can be difficult. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Keystroke Logger
Keystroke logging, often referred to as keylogging or keyboard capturing, is the action of recording (logging) the keys struck on a keyboard, typically covertly, so that a person using the keyboard is unaware that their actions are being monitored. Data can then be retrieved by the person operating the logging program. A keystroke recorder or keylogger can be either software or hardware. While the programs themselves are legal, with many designed to allow employers to oversee the use of their computers, keyloggers are most often used for stealing passwords and other confidential information. Keylogging can also be used to study keystroke dynamics or human-computer interaction. Numerous keylogging methods exist, ranging from hardware and software-based approaches to acoustic cryptanalysis. Application of keylogger Software-based keyloggers A software-based keylogger is a computer program designed to record any input from the keyboard. Keyloggers are used in IT organizatio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Keystroke Logging
Keystroke logging, often referred to as keylogging or keyboard capturing, is the action of recording (logging) the keys struck on a keyboard, typically covertly, so that a person using the keyboard is unaware that their actions are being monitored. Data can then be retrieved by the person operating the logging program. A keystroke recorder or keylogger can be either software or hardware. While the programs themselves are legal, with many designed to allow employers to oversee the use of their computers, keyloggers are most often used for stealing passwords and other confidential information. Keylogging can also be used to study keystroke dynamics or human-computer interaction. Numerous keylogging methods exist, ranging from hardware and software-based approaches to acoustic cryptanalysis. Application of keylogger Software-based keyloggers A software-based keylogger is a computer program designed to record any input from the keyboard. Keyloggers are used in IT organizatio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Keystroke Logger
Keystroke logging, often referred to as keylogging or keyboard capturing, is the action of recording (logging) the keys struck on a keyboard, typically covertly, so that a person using the keyboard is unaware that their actions are being monitored. Data can then be retrieved by the person operating the logging program. A keystroke recorder or keylogger can be either software or hardware. While the programs themselves are legal, with many designed to allow employers to oversee the use of their computers, keyloggers are most often used for stealing passwords and other confidential information. Keylogging can also be used to study keystroke dynamics or human-computer interaction. Numerous keylogging methods exist, ranging from hardware and software-based approaches to acoustic cryptanalysis. Application of keylogger Software-based keyloggers A software-based keylogger is a computer program designed to record any input from the keyboard. Keyloggers are used in IT organizatio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Security Software
Computer security software or cybersecurity software is any computer program designed to influence information security. This is often taken in the context of defending computer systems or data, yet can incorporate programs designed specifically for subverting computer systems due to their significant overlap, and the adage that the best defense is a good offense. The defense of computers against intrusion and unauthorized use of resources is called ''computer security''. Similarly, the defense of computer networks is called ''network security''. The subversion of computers or their unauthorized use is referred to using the terms ''cyberwarfare'', ''cybercrime'', or ''security hacking'' (later shortened to ''hacking'' for further references in this article due to issues with ''hacker'', ''hacker culture'' and differences in white/grey/black 'hat' color identification). Types Below, various software implementations of Cybersecurity patterns and groups outlining ways a host syste ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anti-virus
Antivirus software (abbreviated to AV software), also known as anti-malware, is a computer program used to prevent, detect, and remove malware. Antivirus software was originally developed to detect and remove computer viruses, hence the name. However, with the proliferation of other malware, antivirus software started to protect from other computer threats. In particular, modern antivirus software can protect users from malicious browser helper objects (BHOs), browser hijackers, ransomware, keyloggers, backdoors, rootkits, trojan horses, worms, malicious LSPs, dialers, fraud tools, adware, and spyware. Some products also include protection from other computer threats, such as infected and malicious URLs, spam, scam and phishing attacks, online identity (privacy), online banking attacks, social engineering techniques, advanced persistent threat (APT), and botnet DDoS attacks. History 1949–1980 period (pre-antivirus days) Although the roots of the computer viru ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anti-spyware
Spyware (a portmanteau for spying software) is software with malicious behaviour that aims to gather information about a person or organization and send it to another entity in a way that harms the user—for example, by violating their privacy or endangering their device's security. This behaviour may be present in malware as well as in legitimate software. Websites may engage in spyware behaviours like web tracking. Hardware devices may also be affected. Spyware is frequently associated with advertising and involves many of the same issues. Because these behaviors are so common, and can have non-harmful uses, providing a precise definition of spyware is a difficult task.FTC Report (2005)." History The first recorded use of the term :wikt:spyware, spyware occurred on October 16, 1995 in a Usenet post that poked fun at Microsoft's business model.Vossen, Roland (attributed); October 21, 1995Win 95 Source code in c!!posted to rec..programmer; retrieved from groups.google.com ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Malware
Malware (a portmanteau for ''malicious software'') is any software intentionally designed to cause disruption to a computer, server, client, or computer network, leak private information, gain unauthorized access to information or systems, deprive access to information, or which unknowingly interferes with the user's computer security and privacy. By contrast, software that causes harm due to some deficiency is typically described as a software bug. Malware poses serious problems to individuals and businesses on the Internet. According to Symantec's 2018 Internet Security Threat Report (ISTR), malware variants number has increased to 669,947,865 in 2017, which is twice as many malware variants as in 2016. Cybercrime, which includes malware attacks as well as other crimes committed by computer, was predicted to cost the world economy $6 trillion USD in 2021, and is increasing at a rate of 15% per year. Many types of malware exist, including computer viruses, worms, Trojan horses, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Public Computer
A public computer (or public access computer) is any of various computers available in public areas. Some places where public computers may be available are libraries, schools, or dedicated facilities run by government. Public computers share similar hardware and software components to personal computers, however, the role and function of a public access computer is entirely different. A public access computer is used by many different untrusted individuals throughout the course of the day. The computer must be locked down and secure against both intentional and unintentional abuse. Users typically do not have authority to install software or change settings. A personal computer, in contrast, is typically used by a single responsible user, who can customize the machine's behavior to their preferences. Public access computers are often provided with tools such as a PC reservation system to regulate access. The world's first public access computer center was the Marin Computer Cen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
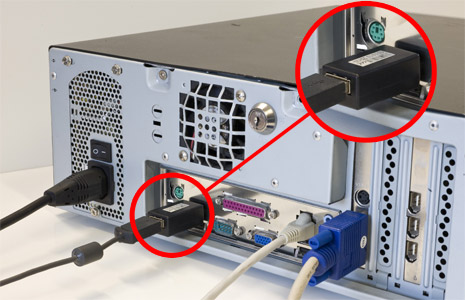
Hardware Keylogger
Hardware keyloggers are used for keystroke logging, a method of capturing and recording computer users' keystrokes, including sensitive passwords. They can be implemented sala madarevel firmware, or alternatively, via a device plugged inline between a computer keyboard and a computer. They log all keyboard activity to their internal memory. Description Hardware keyloggers have an advantage over software keyloggers as they can begin logging from the moment a computer is turned on (and are therefore able to intercept passwords for the BIOS or disk encryption software). All hardware keylogger devices have to have the following: * A microcontroller - this interprets the datastream between the keyboard and computer, processes it, and passes it to the non-volatile memory * A non-volatile memory device, such as flash memory - this stores the recorded data, retaining it even when power is lost Generally, recorded data is retrieved by typing a special password into a computer text edi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
World Of Warcraft
''World of Warcraft'' (''WoW'') is a massively multiplayer online role-playing game (MMORPG) released in 2004 by Blizzard Entertainment. Set in the ''Warcraft'' fantasy universe, ''World of Warcraft'' takes place within the world of Azeroth (world), Azeroth, approximately four years after the events of the previous game in the series, ''Warcraft III: The Frozen Throne.'' The game was announced in 2001, and was released for the 10th anniversary of the ''Warcraft'' franchise on November 23, 2004. Since launch, ''World of Warcraft'' has had nine major expansion packs: ''The Burning Crusade'' (2007), ''Wrath of the Lich King'' (2008), ''World of Warcraft: Cataclysm, Cataclysm'' (2010), ''Mists of Pandaria'' (2012), ''Warlords of Draenor'' (2014), ''World of Warcraft: Legion, Legion'' (2016), ''Battle for Azeroth'' (2018), ''World of Warcraft: Shadowlands, Shadowlands'' (2020), and ''World of Warcraft: Dragonflight, Dragonflight'' (2022). Similar to other MMORPGs, the game allows ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Financial Institution
Financial institutions, sometimes called banking institutions, are business entities that provide services as intermediaries for different types of financial monetary transactions. Broadly speaking, there are three major types of financial institutions: # Depository institutions – deposit-taking institutions that accept and manage deposits and make loans, including banks, building societies, credit unions, trust companies, and mortgage loan companies; # Contractual institutions – insurance companies and pension funds # Investment institutions – investment banks, underwriters, and other different types of financial entities managing investments. Financial institutions can be distinguished broadly into two categories according to ownership structure: * Commercial banks * Cooperative banks Some experts see a trend toward homogenisation of financial institutions, meaning a tendency to invest in similar areas and have similar business strategies. A consequence of this might ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Personal Identification Number
A personal identification number (PIN), or sometimes redundantly a PIN number or PIN code, is a numeric (sometimes alpha-numeric) passcode used in the process of authenticating a user accessing a system. The PIN has been the key to facilitating the private data exchange between different data-processing centers in computer networks for financial institutions, governments, and enterprises. PINs may be used to authenticate banking systems with cardholders, governments with citizens, enterprises with employees, and computers with users, among other uses. In common usage, PINs are used in ATM or POS transactions, secure access control (e.g. computer access, door access, car access), internet transactions, or to log into a restricted website. History The PIN originated with the introduction of the automated teller machine (ATM) in 1967, as an efficient way for banks to dispense cash to their customers. The first ATM system was that of Barclays in London, in 1967; it accepted ch ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |