|
Authorization
Authorization or authorisation (see spelling differences) is the function of specifying access rights/privileges to resources, which is related to general information security and computer security, and to access control in particular. More formally, "to authorize" is to define an access policy. For example, human resources staff are normally authorized to access employee records and this policy is often formalized as access control rules in a computer system. During operation, the system uses the access control rules to decide whether access requests from ( authenticated) consumers shall be approved (granted) or disapproved (rejected). Resources include individual files or an item's data, computer programs, computer devices and functionality provided by computer applications. Examples of consumers are computer users, computer software and other hardware on the computer. Overview Access control in computer systems and networks rely on access policies. The access control p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Authorization Hold
Authorization hold (also card authorization, preauthorization, or preauth) is a service offered by credit and debit card providers whereby the provider puts a hold of the amount approved by the cardholder, reducing the balance of available funds until the merchant clears the transaction (also called settlement), after the transaction is completed or aborted, or because the hold expires. In the case of debit cards, authorization holds can fall off the account, thus rendering the balance available again, anywhere from one to eight business days after the transaction date, depending on the bank's policy. In the case of credit cards, holds may last as long as thirty days, depending on the issuing bank. Transactions may be withdrawn but in most cases, especially with smaller banks, will not show up as a deposit on your statement but will instead be directly added to your available balance automatically due to it only being a “temporary charge”. The usual reason for authorization h ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
XACML
XACML stands for "eXtensible Access Control Markup Language". The standard defines a declarative fine-grained, attribute-based access control policy language, an architecture, and a processing model describing how to evaluate access requests according to the rules defined in policies. As a published standard specification, one of the goals of XACML is to promote common terminology and interoperability between access control implementations by multiple vendors. XACML is primarily an attribute-based access control system (ABAC), also known as a policy-based access control (PBAC) system, where attributes (bits of data) associated with a user or action or resource are inputs into the decision of whether a given user may access a given resource in a particular way. Role-based access control (RBAC) can also be implemented in XACML as a specialization of ABAC. The XACML model supports and encourages the separation of enforcement (PEP) from decision making (PDP) from management / d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
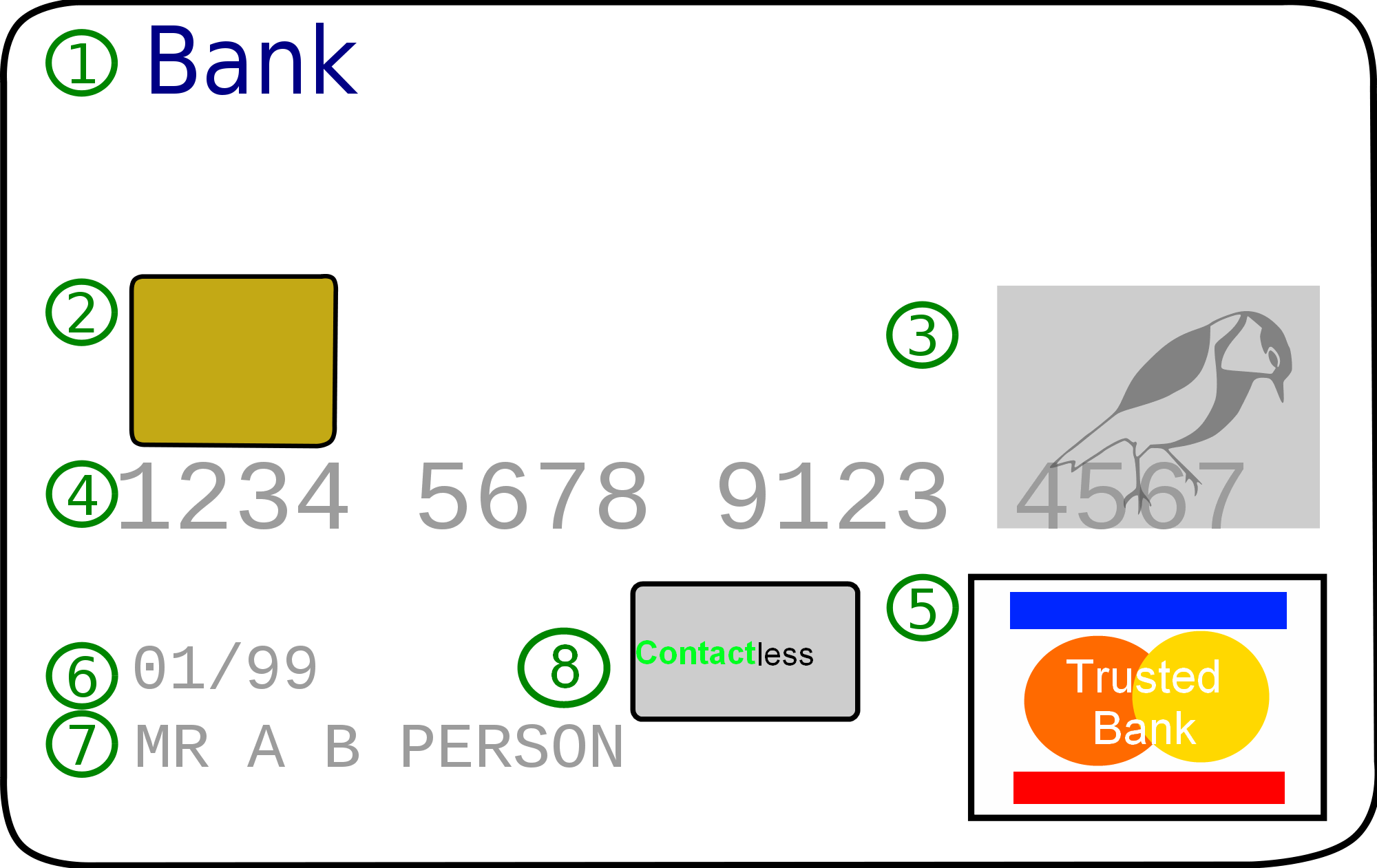
Credit Card
A credit card is a payment card issued to users (cardholders) to enable the cardholder to pay a merchant for goods and services based on the cardholder's accrued debt (i.e., promise to the card issuer to pay them for the amounts plus the other agreed charges). The card issuer (usually a bank or credit union) creates a revolving account and grants a line of credit to the cardholder, from which the cardholder can borrow money for payment to a merchant or as a cash advance. There are two credit card groups: consumer credit cards and business credit cards. Most cards are plastic, but some are metal cards (stainless steel, gold, palladium, titanium), and a few gemstone-encrusted metal cards. A regular credit card is different from a charge card, which requires the balance to be repaid in full each month or at the end of each statement cycle. In contrast, credit cards allow the consumers to build a continuing balance of debt, subject to interest being charged. A credit car ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Debit Card
A debit card, also known as a check card or bank card is a payment card that can be used in place of cash to make purchases. The term ''#Plastic card, plastic card'' includes the above and as an identity document. These are similar to a credit card, but unlike a credit card, the money for the purchase must be in the cardholder's bank account at the time of a purchase and is immediately transferred directly from that account to the merchant's account to pay for the purchase. Some debit cards carry a Stored-value card, stored value with which a payment is made (prepaid card), but most relay a message to the cardholder's bank to withdraw funds from the cardholder's designated bank account. In some cases, the payment card number is assigned exclusively for use on the Internet and there is no physical card. This is referred to as a virtual card. In many countries, the use of debit cards has become so widespread they have overtaken cheque, checks in volume, or have entirely replace ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Authentication
Authentication (from ''authentikos'', "real, genuine", from αὐθέντης ''authentes'', "author") is the act of proving an assertion, such as the identity of a computer system user. In contrast with identification, the act of indicating a person or thing's identity, authentication is the process of verifying that identity. It might involve validating personal identity documents, verifying the authenticity of a website with a digital certificate, determining the age of an artifact by carbon dating, or ensuring that a product or document is not counterfeit. Methods Authentication is relevant to multiple fields. In art, antiques, and anthropology, a common problem is verifying that a given artifact was produced by a certain person or in a certain place or period of history. In computer science, verifying a user's identity is often required to allow access to confidential data or systems. Authentication can be considered to be of three types: The first type of a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Access Control
In the fields of physical security and information security, access control (AC) is the selective restriction of access to a place or other resource, while access management describes the process. The act of ''accessing'' may mean consuming, entering, or using. Permission to access a resource is called ''authorization''. Locks and login credentials are two analogous mechanisms of access control. Physical security Geographical access control may be enforced by personnel (e.g. border guard, bouncer, ticket checker), or with a device such as a turnstile. There may be fences to avoid circumventing this access control. An alternative of access control in the strict sense (physically controlling access itself) is a system of checking authorized presence, see e.g. Ticket controller (transportation). A variant is exit control, e.g. of a shop (checkout) or a country. The term access control refers to the practice of restricting entrance to a property, a building, or a room ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Network
A computer network is a set of computers sharing resources located on or provided by network nodes. The computers use common communication protocols over digital interconnections to communicate with each other. These interconnections are made up of telecommunication network technologies, based on physically wired, optical, and wireless radio-frequency methods that may be arranged in a variety of network topologies. The nodes of a computer network can include personal computers, servers, networking hardware, or other specialised or general-purpose hosts. They are identified by network addresses, and may have hostnames. Hostnames serve as memorable labels for the nodes, rarely changed after initial assignment. Network addresses serve for locating and identifying the nodes by communication protocols such as the Internet Protocol. Computer networks may be classified by many criteria, including the transmission medium used to carry signals, bandwidth, communications ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Security
Information security, sometimes shortened to InfoSec, is the practice of protecting information by mitigating information risks. It is part of information risk management. It typically involves preventing or reducing the probability of unauthorized/inappropriate access to data, or the unlawful use, disclosure, disruption, deletion, corruption, modification, inspection, recording, or devaluation of information. It also involves actions intended to reduce the adverse impacts of such incidents. Protected information may take any form, e.g. electronic or physical, tangible (e.g. paperwork) or intangible (e.g. knowledge). Information security's primary focus is the balanced protection of the confidentiality, integrity, and availability of data (also known as the CIA triad) while maintaining a focus on efficient policy implementation, all without hampering organization productivity. This is largely achieved through a structured risk management process that involves: * identify ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Security
Computer security, cybersecurity (cyber security), or information technology security (IT security) is the protection of computer systems and networks from attack by malicious actors that may result in unauthorized information disclosure, theft of, or damage to hardware, software, or data, as well as from the disruption or misdirection of the services they provide. The field has become of significance due to the expanded reliance on computer systems, the Internet, and wireless network standards such as Bluetooth and Wi-Fi, and due to the growth of smart devices, including smartphones, televisions, and the various devices that constitute the Internet of things (IoT). Cybersecurity is one of the most significant challenges of the contemporary world, due to both the complexity of information systems and the societies they support. Security is of especially high importance for systems that govern large-scale systems with far-reaching physical effects, such as power distribu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Role-based Access Control
In computer systems security, role-based access control (RBAC) or role-based security is an approach to restricting system access to authorized users. It is an approach to implement mandatory access control (MAC) or discretionary access control (DAC). Role-based access control is a policy-neutral access-control mechanism defined around roles and privileges. The components of RBAC such as role-permissions, user-role and role-role relationships make it simple to perform user assignments. A study by NIST has demonstrated that RBAC addresses many needs of commercial and government organizations. RBAC can be used to facilitate administration of security in large organizations with hundreds of users and thousands of permissions. Although RBAC is different from MAC and DAC access control frameworks, it can enforce these policies without any complication. Design Within an organization, roles are created for various job functions. The permissions to perform certain operations are ass ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
American And British English Spelling Differences
Despite the various English dialects spoken from country to country and within different regions of the same country, there are only slight regional variations in English orthography, the two most notable variations being British and American spelling. Many of the differences between American and British English date back to a time before spelling standards were developed. For instance, some spellings seen as "American" today were once commonly used in Britain, and some spellings seen as "British" were once commonly used in the United States. A "British standard" began to emerge following the 1755 publication of Samuel Johnson's ''A Dictionary of the English Language'', and an "American standard" started following the work of Noah Webster and, in particular, his '' An American Dictionary of the English Language'', first published in 1828. Webster's efforts at spelling reform were somewhat effective in his native country, resulting in certain well-known patterns of spelli ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |

.jpg)



