|
Windows Filtering Platform
Windows Filtering Platform (WFP) is a set of system services in Windows Vista and later that allows Windows software to process and filter network traffic. Microsoft intended WFP for use by firewalls, antimalware software, and parental controls apps. Additionally, WFP is used to implement NAT and to store IPSec policy configuration. WFP relies on Windows Vista's Next Generation TCP/IP stack. It provides features such as integrated communication and per-application processing logic. Since Windows 8 and Windows Server 2012, WFP allows filtering at the second layer of TCP/IP suite. Components The filtering platform includes the following components: * Shims, which expose the internal structure of a packet as properties. Different shims exist for protocols at different layers. WFP comes with a set of shims; users can register shims for other protocols using the API. The in-built set of shims includes: ** Application Layer Enforcement (ALE) shim ** Transport Layer Module ( ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Windows Service
In Windows NT operating systems, a Windows service is a computer program that operates in the background. It is similar in concept to a Unix daemon. A Windows service must conform to the interface rules and protocols of the Service Control Manager, the component responsible for managing Windows services. It is the Services and Controller app, services.exe, that launches all the services and manages their actions, such as start, end, etc. Windows services can be configured to start when the operating system is started and run in the background as long as Windows is running. Alternatively, they can be started manually or by an event. Windows NT operating systems include numerous services which run in context of three user accounts: System, Network Service and Local Service. These Windows components are often associated with Host Process for Windows Services. Because Windows services operate in the context of their own dedicated user accounts, they can operate when a user is not l ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Layer
In the seven-layer OSI model of computer networking, the network layer is layer 3. The network layer is responsible for packet forwarding including routing through intermediate Router (computing), routers. Functions The network layer provides the means of transferring variable-length network packets from a source to a destination Host (network), host via one or more networks. Within the service layering semantics of the OSI (Open Systems Interconnection) network architecture, the network layer responds to service requests from the transport layer and issues service requests to the data link layer. Functions of the network layer include: ; Connectionless communication : For example, Internet Protocol is connectionless, in that a data packet can travel from a sender to a recipient without the recipient having to send an acknowledgement. Connection-oriented protocols exist at other, higher layers of the OSI model. ; Host addressing :Every host in the network must have a unique addr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Blue Screen Of Death
The blue screen of death (BSoD) or blue screen error, blue screen, fatal error, bugcheck, and officially known as a stop erroris a fatal system error, critical error screen displayed by the Microsoft Windows operating systems to indicate a crash (computing), system crash, in which the operating system reaches a critical condition where it can no longer operate safely. The name comes from the blue colored background used predominately on the error screens found in the majority of Windows releases. Possible issues contributing to a BSoD may include hardware failures, an issue with or without a device driver, computer virus, viruses, malware, and other factors such as intentional user action. __TOC__ History Blue screen errors have been around since the very first version of Windows in 1985. In the Beta Release of Windows 1.0, if it detected a version of DOS that is newer than the OS expects, the boot screen would have the text "Incorrect DOS version" alongside other messages ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Remote Desktop Connection
Remote Desktop Protocol clients allow users to connect to servers running Remote Desktop Services, Azure Virtual Desktop, or non-Microsoft server software to enable Remote desktop software, remote desktop functionality. Since the release of Remote Desktop Connection, there have been several additional Remote Desktop Protocol clients created by both Microsoft and other parties. By Microsoft Remote Desktop Connection Remote Desktop Connection (RDC, also called Remote Desktop or just RD) is the client application for RDS. The program has the filename mstsc.exe and in Windows 2000 and prior, it was known as Microsoft Terminal Services Client (MSTSC or tsclient). It allows a user to remotely log into a networked computer running the Remote Desktop Services. RDC presents the desktop interface (or application GUI) of the remote system, as if it were accessed locally. In addition to regular username/password for authorizing for the remote session, RDC also supports using smart cards ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Netsh
In computing, netsh, or network shell, is a command-line utility included in Microsoft's Windows NT line of operating systems beginning with Windows 2000. It allows local or remote configuration of network devices such as the interface. Overview A common use of netsh is to reset the TCP/IP stack to default, known-good parameters, a task that in Windows 98 required reinstallation of the TCP/IP adapter. netsh, among many other things, also allows the user to change the IP address on their machine. Starting from Windows Vista, one can also edit wireless settings (for example, SSID) using netsh. netsh can also be used to read information from the IPv6 stack. The command netsh winsock reset can be used to reset TCP/IP problems when communicating with a networked device. References Further reading * * External links Using Netshfrom Microsoft TechNet Microsoft TechNet was a Microsoft web portal and web service for IT professionals. It included a library containing docum ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Windows 7
Windows 7 is a major release of the Windows NT operating system developed by Microsoft. It was Software release life cycle#Release to manufacturing (RTM), released to manufacturing on July 22, 2009, and became generally available on October 22, 2009. It is the successor to Windows Vista, released nearly three years earlier. Windows 7's Windows Server, server counterpart, Windows Server 2008 R2, was released at the same time. It sold over 630 million copies before it was succeeded by Windows 8 in October 2012. Extended support ended on January 14, 2020, over 10 years after the release of Windows 7, and the operating system ceased receiving further updates. A paid support program was available for enterprises, providing security updates for Windows 7 for up to three years since the official end of life. Windows 7 was intended to be an incremental upgrade to Windows Vista, addressing the previous OS's poor reception while maintaining hardware and software compatibility as well as ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Callback (computer Science)
In computer programming, a callback is a Function (computer programming), function that is stored as data (a Reference (computer science), reference) and designed to be called by another function often ''back'' to the original Abstraction (computer science), abstraction layer. A function that accepts a callback Parameter (computer programming), parameter may be designed to call back before Return statement, returning to its caller which is known as ''Synchronization (computer science), synchronous'' or ''blocking''. The function that accepts a callback may be designed to store the callback so that it can be called back after returning which is known as ''asynchronous'', ''Non-blocking algorithm, non-blocking'' or ''deferred''. Programming languages support callbacks in different ways such as function pointers, Lambda (programming), lambda expressions and block (programming), blocks. A callback can be likened to leaving instructions with a tailor for what to do when a suit is ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
User-mode
In computer science, hierarchical protection domains, often called protection rings, are mechanisms to protect data and functionality from faults (by improving fault tolerance) and malicious behavior (by providing computer security). Computer operating systems provide different levels of access to resources. A protection ring is one of two or more hierarchical ''levels'' or ''layers'' of Privilege (computing), privilege within the architecture of a computer system. This is generally hardware-enforced by some Central processing unit, CPU Computer architecture, architectures that provide different CPU modes at the hardware or microcode abstraction layer, level. Rings are arranged in a hierarchy from most privileged (most trusted, usually numbered zero) to least privileged (least trusted, usually with the highest ring number). On most operating systems, Ring 0 is the level with the most privileges and interacts most directly with the physical hardware such as certain CPU functiona ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Control Message Protocol
The Internet Control Message Protocol (ICMP) is a supporting protocol in the Internet protocol suite. It is used by network devices, including routers, to send error messages and operational information indicating success or failure when communicating with another IP address. For example, an error is indicated when a requested service is not available or that a host or router could not be reached. ICMP differs from transport protocols such as TCP and UDP in that it is not typically used to exchange data between systems, nor is it regularly employed by end-user network applications (with the exception of some diagnostic tools like ping and traceroute). A separate Internet Control Message Protocol (called ICMPv6) is used with IPv6. Technical details ICMP is part of the Internet protocol suite as defined in RFC 792. ICMP messages are typically used for diagnostic or control purposes or generated in response to errors in IP operations (as specified in RFC 1122). ICMP ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Remote Procedure Call
In distributed computing, a remote procedure call (RPC) is when a computer program causes a procedure (subroutine) to execute in a different address space (commonly on another computer on a shared computer network), which is written as if it were a normal (local) procedure call, without the programmer explicitly writing the details for the remote interaction. That is, the programmer writes essentially the same code whether the subroutine is local to the executing program, or remote. This is a form of server interaction (caller is client, executor is server), typically implemented via a request–response message passing system. In the object-oriented programming paradigm, RPCs are represented by remote method invocation (RMI). The RPC model implies a level of location transparency, namely that calling procedures are largely the same whether they are local or remote, but usually, they are not identical, so local calls can be distinguished from remote calls. Remote calls are usually o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
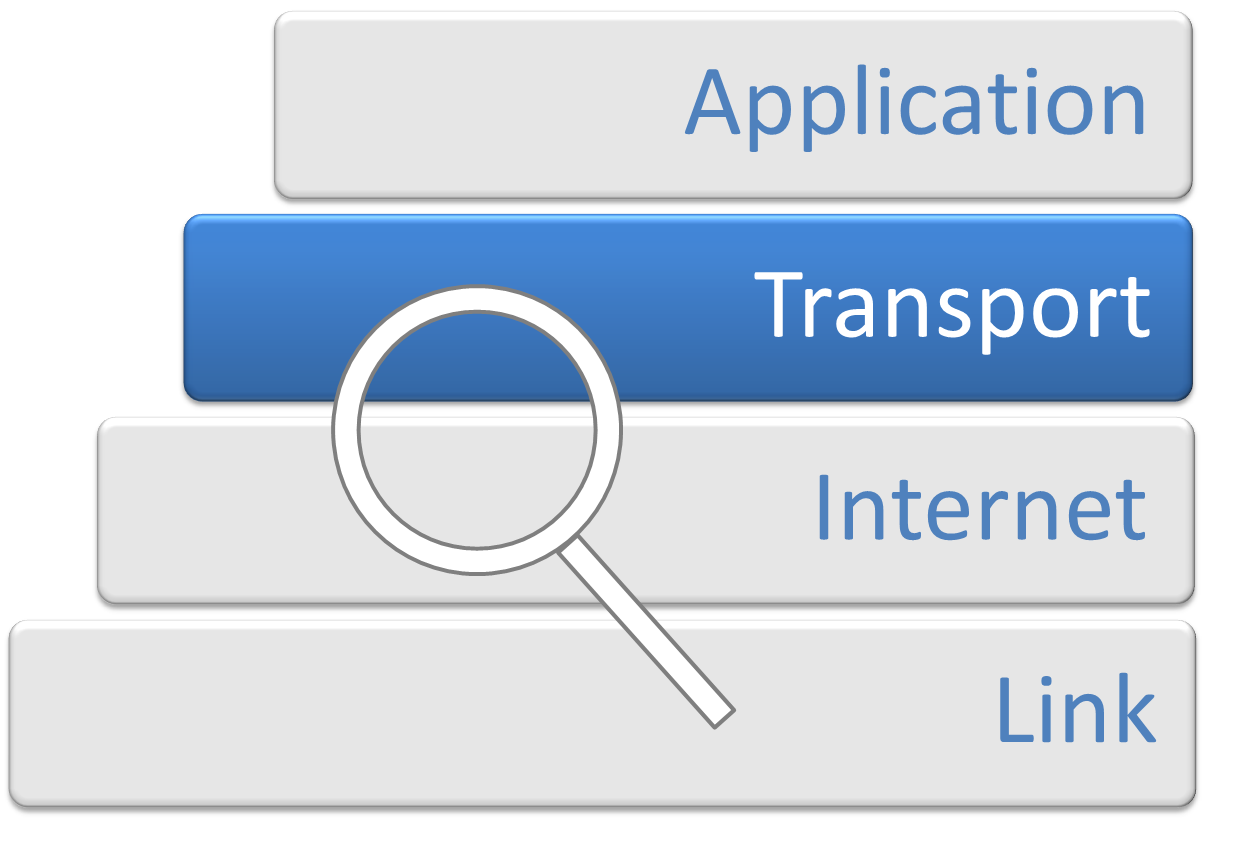
Transport Layer
In computer networking, the transport layer is a conceptual division of methods in the layered architecture of protocols in the network stack in the Internet protocol suite and the OSI model. The protocols of this layer provide end-to-end communication services for applications. It provides services such as connection-oriented communication, reliability, flow control, and multiplexing. The details of implementation and semantics of the transport layer of the Internet protocol suite, which is the foundation of the Internet, and the OSI model of general networking are different. The protocols in use today in this layer for the Internet all originated in the development of TCP/IP. In the OSI model the transport layer is often referred to as Layer 4, or L4, while numbered layers are not used in TCP/IP. The best-known transport protocol of the Internet protocol suite is the Transmission Control Protocol (TCP). It is used for connection-oriented transmissions, whereas the con ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |