|
Vulnerability Mitigation
Vulnerability management is the "cyclical practice of identifying, classifying, prioritizing, remediating, and mitigating" software vulnerabilities. Vulnerability management is integral to computer security and network security, and must not be confused with vulnerability assessment. Vulnerabilities can be discovered with a vulnerability scanner, which analyzes a computer system in search of known vulnerabilities,Anna-Maija Juuso and Ari Takanen ''Unknown Vulnerability Management'', Codenomicon whitepaper, October 201 such as open ports, insecure software configurations, and susceptibility to malware infections. They may also be identified by consulting public sources, such as NVD, or subscribing to a commercial vulnerability alerting service such as Symantec's DeepSight Vulnerability Datafeed or Accenture's Vulnerability Intelligence Service. Unknown vulnerabilities, such as a zero-day, may be found with fuzz testing. Fuzzy testing can identify certain kinds of vulnerabilit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Vulnerability
Vulnerabilities are flaws in a computer system that weaken the overall security of the device/system. Vulnerabilities can be weaknesses in either the hardware itself, or the software that runs on the hardware. Vulnerabilities can be exploited by a threat actor, such as an attacker, to cross privilege boundaries (i.e. perform unauthorized actions) within a computer system. To exploit a vulnerability, an attacker must have at least one applicable tool or technique that can connect to a system weakness. In this frame, vulnerabilities are also known as the attack surface. Vulnerability management is a cyclical practice that varies in theory but contains common processes which include: discover all assets, prioritize assets, assess or perform a complete vulnerability scan, report on results, remediate vulnerabilities, verify remediation - repeat. This practice generally refers to software vulnerabilities in computing systems. Agile vulnerability management refers preventing attacks by ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Patch (computing)
A patch is a set of changes to a computer program or its supporting data designed to update, fix, or improve it. This includes fixing security vulnerabilities and other bugs, with such patches usually being called bugfixes or bug fixes. Patches are often written to improve the functionality, usability, or performance of a program. The majority of patches are provided by software vendors for operating system and application updates. Patches may be installed either under programmed control or by a human programmer using an editing tool or a debugger. They may be applied to program files on a storage device, or in computer memory. Patches may be permanent (until patched again) or temporary. Patching makes possible the modification of compiled and machine language object programs when the source code is unavailable. This demands a thorough understanding of the inner workings of the object code by the person creating the patch, which is difficult without close study of the sourc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Security Procedures
A computer is a machine that can be programmed to carry out sequences of arithmetic or logical operations ( computation) automatically. Modern digital electronic computers can perform generic sets of operations known as programs. These programs enable computers to perform a wide range of tasks. A computer system is a nominally complete computer that includes the hardware, operating system (main software), and peripheral equipment needed and used for full operation. This term may also refer to a group of computers that are linked and function together, such as a computer network or computer cluster. A broad range of industrial and consumer products use computers as control systems. Simple special-purpose devices like microwave ovens and remote controls are included, as are factory devices like industrial robots and computer-aided design, as well as general-purpose devices like personal computers and mobile devices like smartphones. Computers power the Internet, which l ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Project Management
Project management is the process of leading the work of a team to achieve all project goals within the given constraints. This information is usually described in project documentation, created at the beginning of the development process. The primary constraints are scope, time, and budget. The secondary challenge is to optimize the allocation of necessary inputs and apply them to meet pre-defined objectives. The objective of project management is to produce a complete project which complies with the client's objectives. In many cases, the objective of project management is also to shape or reform the client's brief to feasibly address the client's objectives. Once the client's objectives are clearly established, they should influence all decisions made by other people involved in the project – for example, project managers, designers, contractors, and subcontractors. Ill-defined or too tightly prescribed project management objectives are detrimental to decision-maki ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IT Risk
Information technology risk, IT risk, IT-related risk, or cyber risk is any risk related to information technology. While information has long been appreciated as a valuable and important asset, the rise of the knowledge economy and the Digital Revolution has led to organizations becoming increasingly dependent on information, information processing and especially IT. Various events or incidents that compromise IT in some way can therefore cause adverse impacts on the organization's business processes or mission, ranging from inconsequential to catastrophic in scale. Assessing the probability or likelihood of various types of event/incident with their predicted impacts or consequences, should they occur, is a common way to assess and measure IT risks. Alternative methods of measuring IT risk typically involve assessing other contributory factors such as the threats, vulnerabilities, exposures, and asset values. Definitions ISO IT risk: ''the potential that a given threat will e ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Long-term Support
Long-term support (LTS) is a product lifecycle management policy in which a stable release of computer software is maintained for a longer period of time than the standard edition. The term is typically reserved for open-source software, where it describes a software edition that is supported for months or years longer than the software's standard edition. ''Short term support'' (STS) is a term that distinguishes the support policy for the software's standard edition. STS software has a comparatively short life cycle, and may be afforded new features that are omitted from the LTS edition to avoid potentially compromising the stability or compatibility of the LTS release. Characteristics LTS applies the tenets of reliability engineering to the software development process and software release life cycle. Long-term support extends the period of software maintenance; it also alters the type and frequency of software updates ( patches) to reduce the risk, expense, and disruption of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Full Disclosure (computer Security)
In the field of computer security, independent researchers often discover flaws in software that can be abused to cause unintended behaviour; these flaws are called vulnerabilities. The process by which the analysis of these vulnerabilities is shared with third parties is the subject of much debate, and is referred to as the researcher's ''disclosure policy''. Full disclosure is the practice of publishing analysis of software vulnerabilities as early as possible, making the data accessible to everyone without restriction. The primary purpose of widely disseminating information about vulnerabilities is so that potential victims are as knowledgeable as those who attack them. In his 2007 essay on the topic, Bruce Schneier stated "Full disclosure – the practice of making the details of security vulnerabilities public – is a damned good idea. Public scrutiny is the only reliable way to improve security, while secrecy only makes us less secure". Leonard Rose, co-creator of an elec ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Application Security
Application security (short AppSec) includes all tasks that introduce a secure software development life cycle to development teams. Its final goal is to improve security practices and, through that, to find, fix and preferably prevent security issues within applications. It encompasses the whole application life cycle from requirements analysis, design, implementation, verification as well as maintenance. Approaches Different approaches will find different subsets of the security vulnerabilities lurking in an application and are most effective at different times in the software lifecycle. They each represent different tradeoffs of time, effort, cost and vulnerabilities found. * Design review. Before code is written the application's architecture and design can be reviewed for security problems. A common technique in this phase is the creation of a threat model. * Whitebox security review, or code review. This is a security engineer deeply understanding the application through ma ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
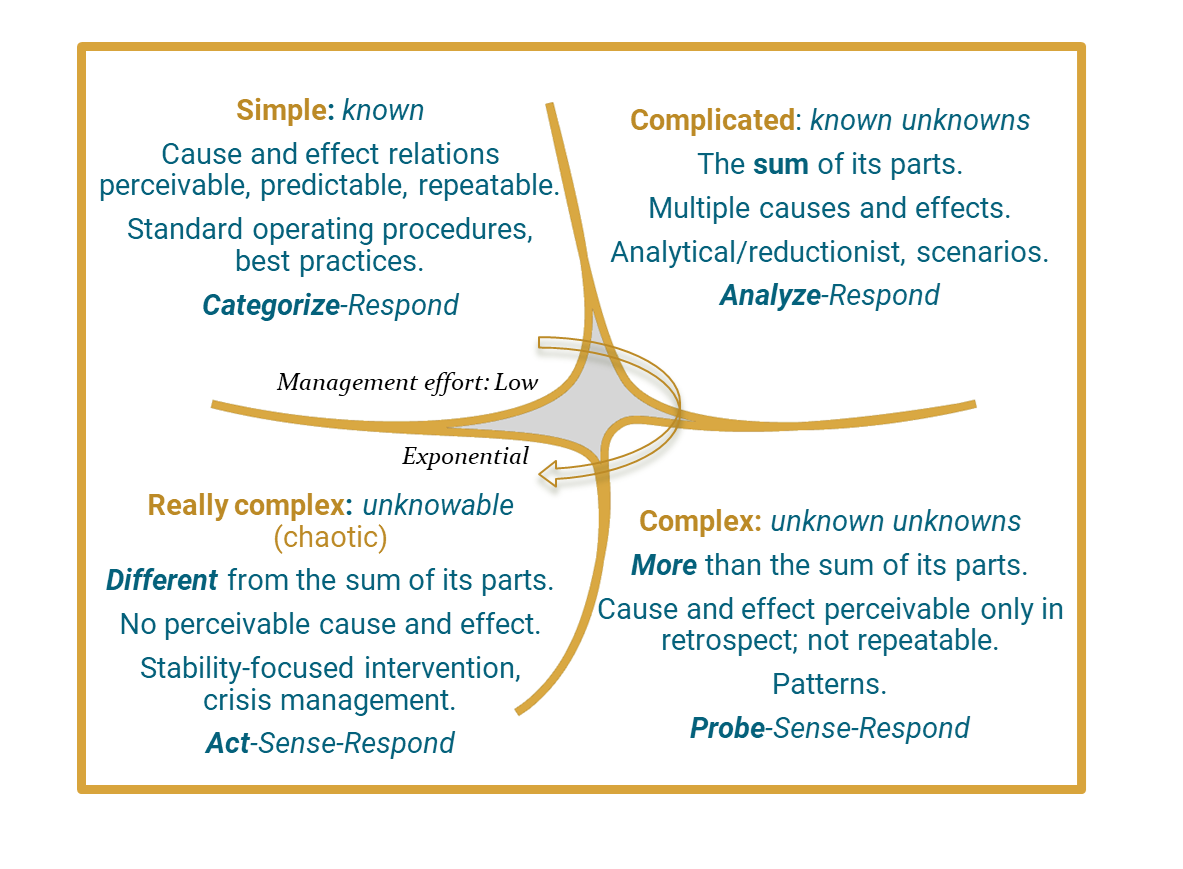
Project Complexity
Project complexity is the property of a project which makes it difficult to understand, foresee, and keep under control its overall behavior, even when given reasonably complete information about the project system. With a lens of systems thinking, project complexity can be defined as an intricate arrangement of the varied interrelated parts in which the elements can change and evolve constantly with an effect on the project objectives. The identification of complex projects is specifically important to multi-project engineering environments. The domain was introduced by D. Baccarini in 1996. Types of complexity Complexity can be: * Structural complexity (also known as detail complexity, or complicatedness), i.e. consisting of many varied interrelated parts. It is typically expressed in terms of size, variety, and interdependence of project components, and described by technological and organizational factors. * Dynamic complexity, which refers to phenomena, characteristics, and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Nassim Nicholas Taleb
Nassim Nicholas Taleb (; alternatively ''Nessim ''or'' Nissim''; born 12 September 1960) is a Lebanese-American essayist, mathematical statistician, former option trader, risk analyst, and aphorist whose work concerns problems of randomness, probability, and uncertainty. ''The Sunday Times'' called his 2007 book '' The Black Swan'' one of the 12 most influential books since World War II. Taleb is the author of the ''Incerto'', a five-volume philosophical essay on uncertainty published between 2001 and 2018 (of which the best-known books are ''The Black Swan'' and ''Antifragile''). He has been a professor at several universities, serving as a Distinguished Professor of Risk Engineering at the New York University Tandon School of Engineering since September 2008. He has been co-editor-in-chief of the academic journal ''Risk and Decision Analysis'' since September 2014. He has also been a practitioner of mathematical finance, a hedge fund manager, and a derivatives trader, and i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Antifragility
Antifragility is a property of systems in which they increase in capability to thrive as a result of stressors, shocks, volatility, noise, mistakes, faults, attacks, or failures. The concept was developed by Nassim Nicholas Taleb in his book, '' Antifragile'', and in technical papers., As Taleb explains in his book, antifragility is fundamentally different from the concepts of resiliency (i.e. the ability to recover from failure) and robustness (that is, the ability to resist failure). The concept has been applied in risk analysis, physics,Naji, A., Ghodrat, M., Komaie-Moghaddam, H., & Podgornik, R. (2014)Asymmetric Coulomb fluids at randomly charged dielectric interfaces: Anti-fragility, overcharging and charge inversion J. Chem. Phys. 141 174704. molecular biology, transportation planning,Levin, J. S., Brodfuehrer, S. P., & Kroshl, W. M. (2014, March)Detecting antifragile decisions and models lessons from a conceptual analysis model of Service Life Extension of aging vehicles In ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |