|
VPPA
The Video Privacy Protection Act (VPPA) is a bill that was passed by the United States Congress in 1988 as and signed into law by President Ronald Reagan. It was created to prevent what it refers to as "wrongful disclosure of video tape rental or sale records video_games.html" ;"title="r similar audio visual materials, to cover items such as video games">r similar audio visual materials, to cover items such as video games and the future DVD format]." Congress passed the VPPA after Robert Bork's video rental history was published during Robert Bork Supreme Court nomination, his Supreme Court nomination. It makes any "video tape service provider" that discloses rental information outside the ordinary course of business liable for up to $2500 in actual damages. Computer-based VPPA litigation Prior to 2007, VPPA had not been cited by privacy attorneys as a cause of action involving computing devices. With the emergence of new-age computing technology and devices in the early 2000 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Private Information
Privacy (, ) is the ability of an individual or group to seclude themselves or information about themselves, and thereby express themselves selectively. The domain of privacy partially overlaps with security, which can include the concepts of appropriate use and protection of information. Privacy may also take the form of bodily integrity. The right not to be subjected to unsanctioned invasions of privacy by the government, corporations, or individuals is part of many countries' privacy laws, and in some cases, constitutions. The concept of universal individual privacy is a modern concept primarily associated with Western culture, particularly British and North American, and remained virtually unknown in some cultures until recent times. Now, most cultures recognize the ability of individuals to withhold certain parts of personal information from wider society. With the rise of technology, the debate regarding privacy has shifted from a bodily sense to a digital sense. As the wo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Patrick Leahy
Patrick Joseph Leahy (; born March 31, 1940) is an American politician and attorney who is the senior United States senator from Vermont and serves as the president pro tempore of the United States Senate. A member of the Democratic Party, Leahy was first elected in 1974 and is in his eighth term. He is the chair of the Appropriations Committee, and served as president pro tempore from 2012 to 2015 and again since 2021. Upon Representative Don Young's death in March 2022, he became the most senior member of Congress. Leahy is also the last of the Senate's "Watergate Babies"—Democrats first elected to Congress in the wave election of 1974 that followed President Richard Nixon's resignation over the Watergate scandal. , Leahy is one of three members of Congress to have served during Gerald Ford's presidency and one of eight to have served during Jimmy Carter's. The dean of his state's congressional delegation, Leahy is Vermont's longest-serving U.S. senator, as well a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Privacy Violations
The right to privacy is an element of various legal traditions that intends to restrain governmental and private actions that threaten the privacy of individuals. Over 150 national constitutions mention the right to privacy. On 10 December 1948, the United Nations General Assembly adopted the Universal Declaration of Human Rights (UDHR), originally written to guarantee individual rights of everyone everywhere; while ''right to privacy'' does not appear in the document, many interpret this through Article 12, which states: "No one shall be subjected to arbitrary interference with his privacy, family, home or correspondence, nor to attacks upon his honour and reputation. Everyone has the right to the protection of the law against such interference or attacks." Since the global surveillance disclosures of 2013, initiated by ex-NSA employee Edward Snowden, the right to privacy has been a subject of international debate. Government agencies, such as the NSA, FBI, CIA, R&AW and GCH ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
TCP/IP
The Internet protocol suite, commonly known as TCP/IP, is a framework for organizing the set of communication protocols used in the Internet and similar computer networks according to functional criteria. The foundational protocols in the suite are the Transmission Control Protocol (TCP), the User Datagram Protocol (UDP), and the Internet Protocol (IP). In the development of this networking model, early versions of it were known as the Department of Defense (DoD) model because the research and development were funded by the United States Department of Defense through DARPA. The Internet protocol suite provides end-to-end data communication specifying how data should be packetized, addressed, transmitted, routed, and received. This functionality is organized into four abstraction layers, which classify all related protocols according to each protocol's scope of networking. An implementation of the layers for a particular application forms a protocol stack. From lowest to high ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Monetization
Monetization ( also spelled monetisation) is, broadly speaking, the process of converting something into money. The term has a broad range of uses. In banking, the term refers to the process of converting or establishing something into legal tender. While it usually refers to the coining of currency or the printing of banknotes by central banks, it may also take the form of a promissory currency. The term "monetization" may also be used informally to refer to exchanging possessions for cash or cash equivalents, including selling a security interest, charging fees for something that used to be free, or attempting to make money on goods or services that were previously unprofitable or had been considered to have the potential to earn profits. And data monetization refers to a spectrum of ways information assets can be converted into economic value. Another meaning of "monetization" denotes the process by which the U.S. Treasury accounts for the face value of outstanding coinage. Th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
HTTPS
Hypertext Transfer Protocol Secure (HTTPS) is an extension of the Hypertext Transfer Protocol (HTTP). It is used for secure communication over a computer network, and is widely used on the Internet. In HTTPS, the communication protocol is encrypted using Transport Layer Security (TLS) or, formerly, Secure Sockets Layer (SSL). The protocol is therefore also referred to as HTTP over TLS, or HTTP over SSL. The principal motivations for HTTPS are authentication of the accessed website, and protection of the privacy and integrity of the exchanged data while in transit. It protects against man-in-the-middle attacks, and the bidirectional encryption of communications between a client and server protects the communications against eavesdropping and tampering. The authentication aspect of HTTPS requires a trusted third party to sign server-side digital certificates. This was historically an expensive operation, which meant fully authenticated HTTPS connections were usually found only ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
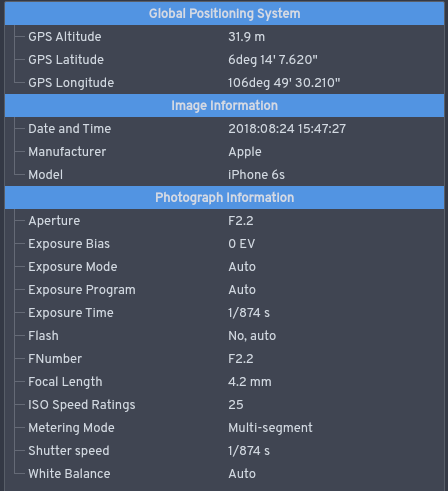
Exif
Exchangeable image file format (officially Exif, according to JEIDA/JEITA/CIPA specifications) is a standard that specifies formats for images, sound, and ancillary tags used by digital cameras (including smartphones), scanners and other systems handling image and sound files recorded by digital cameras. The specification uses the following existing encoding formats with the addition of specific metadata tags: JPEG lossy coding for compressed image files, TIFF Rev. 6.0 (RGB or YCbCr) for uncompressed image files, and RIFF WAV for audio files (linear PCM or ITU-T G.711 μ-law PCM for uncompressed audio data, and IMA-ADPCM for compressed audio data). It does not support JPEG 2000 or GIF encoded images. This standard consists of the Exif image file specification and the Exif audio file specification. Background Exif is supported by almost all camera manufacturers. The metadata tags defined in the Exif standard cover a broad spectrum: * Camera settings: This includes static ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Web Tracking
Web tracking is the practice by which operators of websites and third parties collect, store and share information about visitors’ activities on the World Wide Web. Analysis of a user's behaviour may be used to provide content that enables the operator to infer their preferences and may be of interest to various parties, such as advertisers. Web tracking can be part of visitor management. Uses of web tracking The uses of web tracking include the following: * Advertising companies actively collect information about users and make profiles that are used to individualize advertisements. User activities include websites visited, watched videos, interactions on social networks, and online transactions. Websites like Netflix, YouTube collect information about what shows users watch, which helps them suggest more shows that they might like. Search engines like Google will keep a record of what users search for, which could help them suggest more relevant searches in the future. * L ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Online Advertising
Online advertising, also known as online marketing, Internet advertising, digital advertising or web advertising, is a form of marketing and advertising which uses the Internet to promote products and services to audiences and platform users. Online advertising includes email marketing, search engine marketing (SEM), social media marketing, many types of display advertising (including web banner advertising), and mobile advertising. Advertisements are increasingly being delivered via automated software systems operating across multiple websites, media services and platforms, known as programmatic advertising. Like other advertising media, online advertising frequently involves a publisher, who integrates advertisements into its online content, and an advertiser, who provides the advertisements to be displayed on the publisher's content. Other potential participants include advertising agencies who help generate and place the ad copy, an ad server which technologically deliver ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Driver's Privacy Protection Act
The Driver's Privacy Protection Act of 1994 (also referred to as the "DPPA"), Title XXX of the Violent Crime Control and Law Enforcement Act, is a United States federal statute governing the privacy and disclosure of personal information gathered by state Departments of Motor Vehicles. The law was passed in 1994. It was introduced by Democratic Rep. Jim Moran of Virginia in 1992, after an increase in some opponents of abortion using public driving license databases to track down and harass abortion providers and patients. Prominent among such cases was physician Susan Wicklund, who faced protests and harassment including her house being picketed for a month. The law is currently codified at Chapter 123 of Title 18 of the United States Code. Substantive provisions of the act The statute prohibits the disclosure of personal information (as defined in ) without the express consent of the person to whom such information applies, with the exception of certain circumstances set fort ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Privacy Law
Privacy law is the body of law that deals with the regulating, storing, and using of personally identifiable information, personal healthcare information, and financial information of individuals, which can be Personally identifiable information (PII) gathering, collected by governments, public or private organisations, or other individuals. It also applies in the commercial sector to things like trade secrets and the liability that directors, officers, and employees have when handing sensitive information. Privacy laws are considered within the context of an individual's privacy rights or within reasonable expectation of privacy. The Universal Declaration of Human Rights states that everyone has the right to privacy. The interpretation of these rights varies by country and are not always universal. Classification of privacy laws Privacy laws can be broadly classified into: * General privacy laws that have an overall bearing on the personal information of individuals and affect ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Lane V
In road transport, a lane is part of a roadway that is designated to be used by a single line of vehicles to control and guide drivers and reduce traffic conflicts. Most public roads (highways) have at least two lanes, one for traffic in each direction, separated by lane markings. On multilane roadways and busier two-lane roads, lanes are designated with road surface markings. Major highways often have two multi-lane roadways separated by a median. Some roads and bridges that carry very low volumes of traffic are less than wide, and are only a single lane wide. Vehicles travelling in opposite directions must slow or stop to pass each other. In rural areas, these are often called country lanes. In urban areas, alleys are often only one lane wide. Urban and suburban one lane roads are often designated for one-way traffic. History For much of human history, roads did not need lane markings because most people walked or rode horses at relatively slow speeds. However, when ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |