|
UDP Hole Punching
UDP hole punching is a commonly used technique employed in network address translation (NAT) applications for maintaining User Datagram Protocol (UDP) packet streams that traverse the NAT. NAT traversal techniques are typically required for client-to-client networking applications on the Internet involving hosts connected in private networks, especially in peer-to-peer, Direct Client-to-Client (DCC) and Voice over Internet Protocol (VoIP) deployments. UDP hole punching establishes connectivity between two hosts communicating across one or more network address translators. Typically, third-party hosts on the public transit network are used to establish UDP port states that may be used for direct communications between the communicating hosts. Once port state has been successfully established and the hosts are communicating, port state may be maintained either by normal communications traffic, or in the prolonged absence thereof, by keep-alive packets, usually consisting of empt ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Transmission Control Protocol
The Transmission Control Protocol (TCP) is one of the main protocols of the Internet protocol suite. It originated in the initial network implementation in which it complemented the Internet Protocol (IP). Therefore, the entire suite is commonly referred to as TCP/IP. TCP provides reliable, ordered, and error-checked delivery of a stream of octets (bytes) between applications running on hosts communicating via an IP network. Major internet applications such as the World Wide Web, email, remote administration, and file transfer rely on TCP, which is part of the Transport Layer of the TCP/IP suite. SSL/TLS often runs on top of TCP. TCP is connection-oriented, and a connection between client and server is established before data can be sent. The server must be listening (passive open) for connection requests from clients before a connection is established. Three-way handshake (active open), retransmission, and error detection adds to reliability but lengthens latency. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Port Control Protocol
Port Control Protocol (PCP) is a computer networking protocol that allows hosts on IPv4 or IPv6 networks to control how the incoming IPv4 or IPv6 packets are translated and forwarded by an upstream router that performs network address translation (NAT) or packet filtering. By allowing hosts to create explicit port forwarding rules, handling of the network traffic can be easily configured to make hosts placed behind NATs or firewalls reachable from the rest of the Internet (so they can also act as network servers), which is a requirement for many applications. Additionally, explicit port forwarding rules available through PCP allow hosts to reduce the amount of generated traffic by eliminating workarounds in form of outgoing NAT keepalive messages, which are required for maintaining connections to servers and for various NAT traversal techniques such as TCP hole punching. At the same time, less generated traffic reduces the power consumption, directly improving the ba ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
WebRTC
WebRTC (Web Real-Time Communication) is a free and open-source project providing web browsers and mobile applications with real-time communication (RTC) via application programming interfaces (APIs). It allows audio and video communication to work inside web pages by allowing direct peer-to-peer communication, eliminating the need to install plugins or download native apps. Supported by Apple, Google, Microsoft, Mozilla, and Opera, WebRTC specifications have been published by the World Wide Web Consortium (W3C) and the Internet Engineering Task Force (IETF). According to the webrtc.org website, the purpose of the project is to "enable rich, high-quality RTC applications to be developed for the browser, mobile platforms, and IoT devices, and allow them all to communicate via a common set of protocols". History In May 2010, Google bought Global IP Solutions or GIPS, a VoIP and videoconferencing software company that had developed many components required for RTC, such as co ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hole Punching (networking)
Hole punching (or sometimes punch-through) is a technique in computer networking for establishing a direct connection between two parties in which one or both are behind firewalls or behind routers that use network address translation (NAT). To punch a hole, each client connects to an unrestricted third-party server that temporarily stores external and internal address and port information for each client. The server then relays each client's information to the other, and using that information each client tries to establish direct connection; as a result of the connections using valid port numbers, restrictive firewalls or routers accept and forward the incoming packets on each side. Hole punching does not require any knowledge of the network topology to function. ICMP hole punching, UDP hole punching and TCP hole punching respectively use Internet Control Message, User Datagram and Transmission Control Protocols. Overview Networked devices with public or globally accessibl ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
TCP Hole Punching
TCP NAT traversal and TCP hole punching (sometimes NAT punch-through) in computer networking occurs when two hosts behind a network address translation (NAT) are trying to connect to each other with outbound TCP connections. Such a scenario is particularly important in the case of peer-to-peer communications, such as Voice-over-IP (VoIP), file sharing, teleconferencing, chat systems and similar applications. TCP hole punching is an experimentally used NAT traversal technique for establishing a TCP connection between two peers on the Internet behind NAT devices. ''NAT traversal'' is a general term for techniques that establish and maintain TCP/IP network and/or TCP connections traversing NAT gateways. Terminology In the following, the terms host, client and peer are used almost interchangeably. ; ''local endpoint'', ''internal endpoint'' : the local IP:port as seen locally by the host and the internal part of the NAT. ; ''public endpoint'', ''external endpoint'' : the externa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
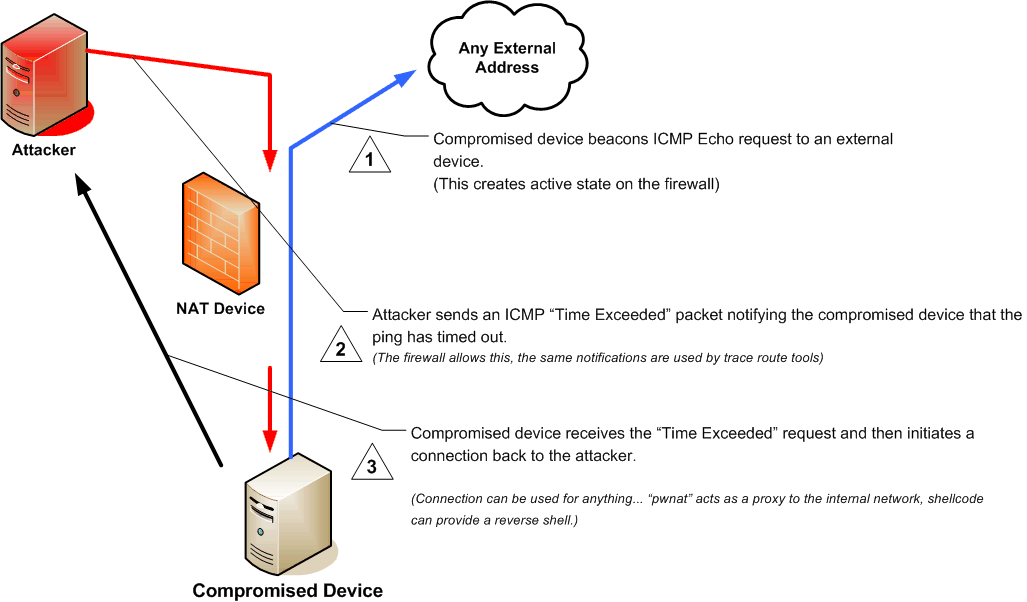
ICMP Hole Punching
ICMP hole punching is a technique employed in network address translator (NAT) applications for maintaining Internet Control Message Protocol (ICMP) packet streams that traverse the NAT. NAT traversal techniques are typically required for client-to-client networking applications on the Internet involving hosts connected in private networks, especially in peer-to-peer and Voice over Internet Protocol (VoIP) deployments. ICMP hole punching establishes connectivity between two hosts communicating across one or more network address translators in either a peer-to-peer or client–server model. Typically, third party hosts on the public transit network are used to establish UDP or TCP port states that may be used for direct communications between the communicating hosts, however ICMP hole punching requires no third party involvement to pass information between one or more NATs by exploiting a NAT's loose acceptance of inbound ICMP Time Exceeded packets. Once an ICMP Time Exc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Freenet
Freenet is a peer-to-peer platform for censorship-resistant, anonymous communication. It uses a decentralized distributed data store to keep and deliver information, and has a suite of free software for publishing and communicating on the Web without fear of censorship.What is Freenet? , ''Freenet: The Free network official website''.Taylor, Ian J. ''From P2P to Web Services and Grids: Peers in a Client/Server World''. London: Springer, 2005. Both Freenet and some of its associated tools were originally designed by Ian Clarke, who defined Freenet's goal as providing [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hamachi (software)
LogMeIn Hamachi is a virtual private network (VPN) application developed and released in 2004 by Alex Pankratov. It is capable of establishing direct links between computers that are behind network address translation ("NAT") firewalls without requiring reconfiguration (when the user's PC can be accessed directly without relays from the Internet/WAN side); in other words, it establishes a connection over the Internet that emulates the connection that would exist if the computers were connected over a local area network ("LAN"). Hamachi was acquired from Pankratov by LogMeIn in 2009. It is currently available as a production version for Microsoft Windows and macOS, as a beta version for Linux, and as a system-VPN-based client compatible with Android and iOS. For paid subscribers Hamachi runs in the background on idle computers. The feature was previously available to all users but became restricted to paid subscribers only. Operational summary Hamachi is a proprietary centra ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tuple
In mathematics, a tuple is a finite ordered list (sequence) of elements. An -tuple is a sequence (or ordered list) of elements, where is a non-negative integer. There is only one 0-tuple, referred to as ''the empty tuple''. An -tuple is defined inductively using the construction of an ordered pair. Mathematicians usually write tuples by listing the elements within parentheses "" and separated by a comma and a space; for example, denotes a 5-tuple. Sometimes other symbols are used to surround the elements, such as square brackets " nbsp; or angle brackets "⟨ ⟩". Braces "" are used to specify arrays in some programming languages but not in mathematical expressions, as they are the standard notation for sets. The term ''tuple'' can often occur when discussing other mathematical objects, such as vectors. In computer science, tuples come in many forms. Most typed functional programming languages implement tuples directly as product types, tightly associated with a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |