|
Threat Model
Threat modeling is a process by which potential threats, such as structural vulnerabilities or the absence of appropriate safeguards, can be identified and enumerated, and countermeasures prioritized. The purpose of threat modeling is to provide defenders with a systematic analysis of what controls or defenses need to be included, given the nature of the system, the probable attacker's profile, the most likely attack vectors, and the assets most desired by an attacker. Threat modeling answers questions like ''“Where am I most vulnerable to attack?”'', ''“What are the most relevant threats?”'', and ''“What do I need to do to safeguard against these threats?”''. Conceptually, most people incorporate some form of threat modeling in their daily life and don't even realize it. Commuters use threat modeling to consider what might go wrong during the morning journey to work and to take preemptive action to avoid possible accidents. Children engage in threat modeling when determ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Structural Vulnerability (computing)
In computing, a structural vulnerability is an IT system weakness that consists of several so-called component vulnerabilities. This type of weakness generally emerges due to several system architecture flaws. An example of a structural vulnerability is a person working in a critical part of the system with no security training, who doesn’t follow the software patch cycles and who is likely to disclose critical information in a phishing Phishing is a type of social engineering where an attacker sends a fraudulent (e.g., spoofed, fake, or otherwise deceptive) message designed to trick a person into revealing sensitive information to the attacker or to deploy malicious softwar ... attack. References {{reflist Vulnerability Computer security exploits Hacking (computer security) ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Christopher Alexander
Christopher Wolfgang John Alexander (4 October 1936 – 17 March 2022) was an Austrian-born British-American architect and design theorist. He was an emeritus professor at the University of California, Berkeley. His theories about the nature of human-centered design have affected fields beyond architecture, including urban design, software, and sociology. Alexander designed and personally built over 100 buildings, both as an architect and a general contractor. In software, Alexander is regarded as the father of the pattern language movement. The first wiki—the technology behind Wikipedia—led directly from Alexander's work, according to its creator, Ward Cunningham. Alexander's work has also influenced the development of agile software development. In architecture, Alexander's work is used by a number of different contemporary architectural communities of practice, including the New Urbanist movement, to help people to reclaim control over their own built environment. How ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
National Security Agency
The National Security Agency (NSA) is a national-level intelligence agency of the United States Department of Defense, under the authority of the Director of National Intelligence (DNI). The NSA is responsible for global monitoring, collection, and processing of information and data for foreign and domestic intelligence and counterintelligence purposes, specializing in a discipline known as signals intelligence (SIGINT). The NSA is also tasked with the protection of U.S. communications networks and information systems. The NSA relies on a variety of measures to accomplish its mission, the majority of which are clandestine. The existence of the NSA was not revealed until 1975. The NSA has roughly 32,000 employees. Originating as a unit to decipher coded communications in World War II, it was officially formed as the NSA by President Harry S. Truman in 1952. Between then and the end of the Cold War, it became the largest of the U.S. intelligence organizations in terms of pers ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
DARPA
The Defense Advanced Research Projects Agency (DARPA) is a research and development agency of the United States Department of Defense responsible for the development of emerging technologies for use by the military. Originally known as the Advanced Research Projects Agency (ARPA), the agency was created on February 7, 1958, by President Dwight D. Eisenhower in response to the Soviet Union, Soviet launching of Sputnik 1 in 1957. By collaborating with academia, industry, and government partners, DARPA formulates and executes research and development projects to expand the frontiers of technology and science, often beyond immediate U.S. military requirements.Dwight D. Eisenhower and Science & Technology, (2008). Dwight D. Eisenhower Memorial CommissionSource ''The Economist'' has called DARPA the agency "that shaped the modern world," and pointed out that "Moderna COVID-19 vaccine, Moderna's COVID-19 vaccine sits alongside weather satellites, Global Positioning System, GPS, Unmann ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Attack Tree
Attack trees are conceptual diagrams showing how an asset, or target, might be attacked. Attack trees have been used in a variety of applications. In the field of information technology, they have been used to describe threats on computer systems and possible attacks to realize those threats. However, their use is not restricted to the analysis of conventional information systems. They are widely used in the fields of defense and aerospace for the analysis of threats against tamper resistant electronics systems (e.g., avionics on military aircraft). Attack trees are increasingly being applied to computer control systems (especially relating to the electric power grid). Attack trees have also been used to understand threats to physical systems. Some of the earliest descriptions of attack trees are found in papers and articles by Bruce Schneier, when he was CTO of Counterpane Internet Security. Schneier was clearly involved in the development of attack tree concepts and was ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bruce Schneier
Bruce Schneier (; born January 15, 1963) is an American cryptographer, computer security professional, privacy specialist, and writer. Schneier is a Lecturer in Public Policy at the Harvard Kennedy School and a Fellow at the Berkman Klein Center for Internet & Society as of November, 2013. He is a board member of the Electronic Frontier Foundation, Access Now, and The Tor Project; and an advisory board member of Electronic Privacy Information Center and VerifiedVoting.org. He is the author of several books on general security topics, computer security and cryptography and is a squid enthusiast. In 2015, Schneier received the EPIC Lifetime Achievement Award from Electronic Privacy Information Center. Early life Bruce Schneier is the son of Martin Schneier, a Brooklyn Supreme Court judge. He grew up in the Flatbush neighborhood of Brooklyn, New York, attending P.S. 139 and Hunter College High School. After receiving a physics bachelor's degree from the University of Roche ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
STRIDE (security)
STRIDE is a model for identifying computer security Threat (computer), threats developed by Praerit Garg and Loren Kohnfelder at Microsoft. It provides a mnemonic for security threats in six categories. The threats are: * Spoofing attack, Spoofing * Tampering (crime), Tampering * Non-repudiation, Repudiation * Information disclosure (data privacy, privacy breach or data leak) * Denial-of-service attack, Denial of service * Privilege escalation, Elevation of privilege The STRIDE was initially created as part of the process of threat modeling. STRIDE is a model of threats, used to help reason and find threats to a system. It is used in conjunction with a model of the target system that can be constructed in parallel. This includes a full breakdown of processes, data stores, data flows, and trust boundaries. Today it is often used by security experts to help answer the question "what can go wrong in this system we're working on?" Each threat is a violation of a desirable prope ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Acrostic
An acrostic is a poem or other word composition in which the ''first'' letter (or syllable, or word) of each new line (or paragraph, or other recurring feature in the text) spells out a word, message or the alphabet. The term comes from the French from post-classical Latin , from Koine Greek , from Ancient Greek "highest, topmost" and "verse". As a form of constrained writing, an acrostic can be used as a mnemonic device to aid memory retrieval. When the ''last'' letter of each new line (or other recurring feature) forms a word it is called a telestich; the combination of an acrostic and a telestich in the same composition is called a double acrostic (e.g. the first-century Latin Sator Square). Acrostics are common in medieval literature, where they usually serve to highlight the name of the poet or his patron, or to make a prayer to a saint. They are most frequent in verse works but can also appear in prose. The Middle High German poet Rudolf von Ems for example opens all h ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Window Snyder
Mwende Window Snyder (born 1975), better known as Window Snyder, is an American computer security expert. She has been a top security officer at Square, Inc., Apple, Fastly, Intel and Mozilla Corporation. She was also a Senior Security Strategist at Microsoft. She is co-author of ''Threat Modeling'', a standard manual on application security. Biography Snyder is the daughter of an African-American father and a Kenyan-born mother, Wayua Muasa. She goes by her middle name Window; her first name is used only by family members. She graduated from Choate Rosemary Hall in 1993 and has served on their board. At college, she got a computer science major, and during that time got interested in cryptography and crypto-analysis and started actively working on the topic of cyber-security with the Boston hacker community in the 1990s, building her own tools and getting familiar with multi-user systems. She went by the nickname Rosie the Riveter in the hacker scene. She then pursued this caree ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cyber Threat Hunting
Cyber threat hunting is a proactive cyber defence activity. It is "the process of proactively and iteratively searching through networks to detect and isolate advanced threats that evade existing security solutions." This is in contrast to traditional threat management measures, such as firewalls, intrusion detection systems (IDS), malware sandbox (computer security) and SIEM systems, which typically involve an investigation of evidence-based data ''after'' there has been a warning of a potential threat. Methodologies Threat hunting has traditionally been a manual process, in which a security analyst sifts through various data information using their own knowledge and familiarity with the network to create hypotheses about potential threats, such as, but not limited to, lateral movement by threat actors. To be even more effective and efficient, however, threat hunting can be partially automated, or machine-assisted, as well. In this case, the analyst uses software that leverage ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
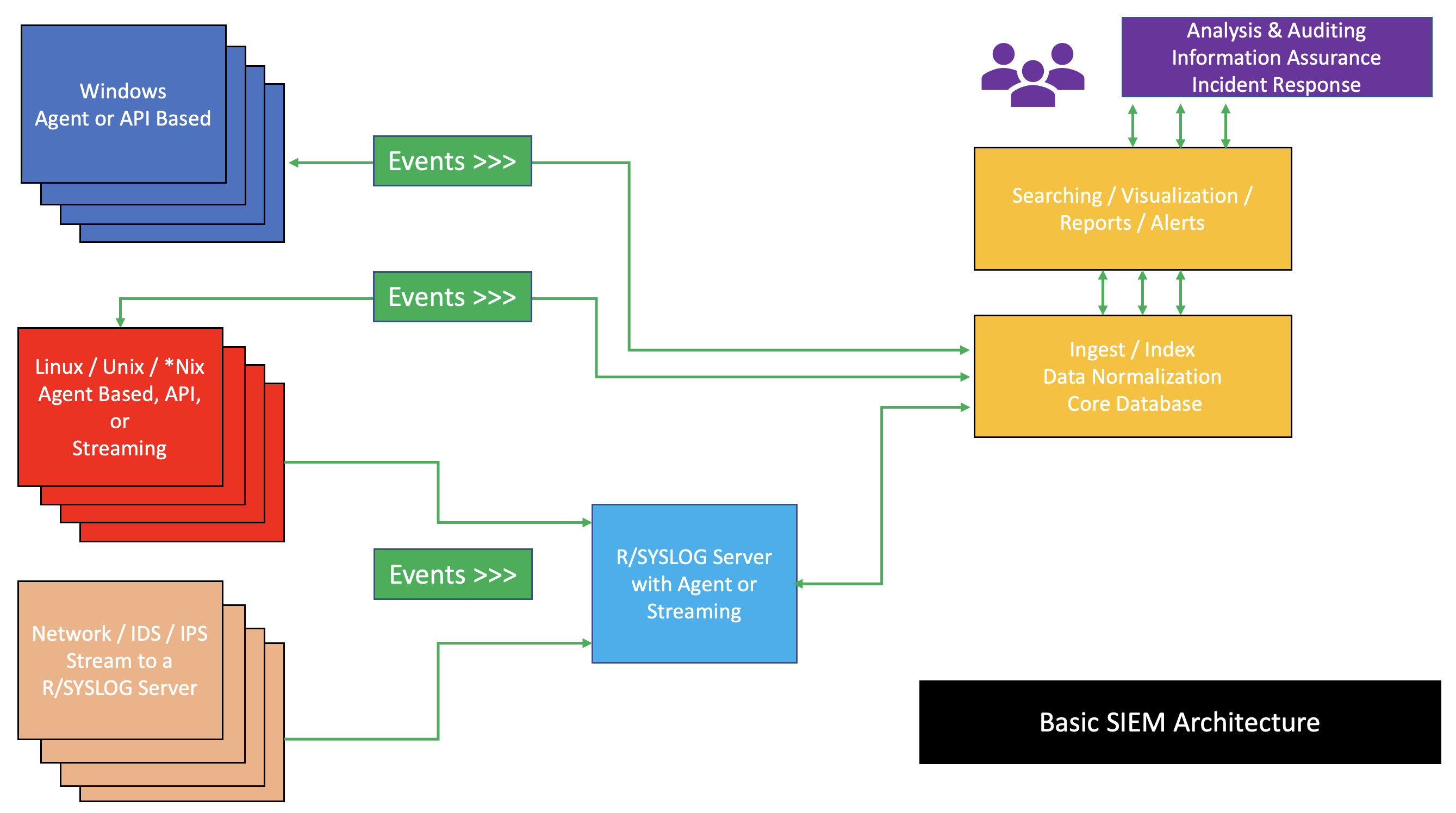
Security Information And Event Management
Security information and event management (SIEM) is a field within the field of computer security, where software products and services combine security information management (SIM) and security event management (SEM). They provide real-time analysis of security alerts generated by applications and network hardware. Vendors sell SIEM as software, as appliances, or as managed services; these products are also used to log security data and generate reports for compliance purposes. The term and the initialism SIEM was coined by Mark Nicolett and Amrit Williams of Gartner in 2005. History Monitoring system logs has grown more prevalent as complex cyber-attacks force compliance and regulatory mechanisms to mandate logging security controls within a Risk Management Framework. Logging levels of a system started with the primary function of troubleshooting system errors or debugging code compiled and run. As operating systems and networks have increased in complexity, so has the event ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Flow Diagram - Online Banking Application
In the pursuit of knowledge, data (; ) is a collection of discrete values that convey information, describing quantity, quality, fact, statistics, other basic units of meaning, or simply sequences of symbols that may be further interpreted. A datum is an individual value in a collection of data. Data is usually organized into structures such as tables that provide additional context and meaning, and which may themselves be used as data in larger structures. Data may be used as variables in a computational process. Data may represent abstract ideas or concrete measurements. Data is commonly used in scientific research, economics, and in virtually every other form of human organizational activity. Examples of data sets include price indices (such as consumer price index), unemployment rates, literacy rates, and census data. In this context, data represents the raw facts and figures which can be used in such a manner in order to capture the useful information out of it. Dat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |