|
TCP Wrappers
__NOTOC__ TCP Wrappers (also known as tcp_wrappers) is a host-based networking ACL system, used to filter network access to Internet Protocol servers on (Unix-like) operating systems such as Linux or BSD. It allows host or subnetwork IP addresses, names and/or ident query replies, to be used as tokens on which to filter for access control purposes. The original code was written by Wietse Venema in 1990 to monitor a cracker's activities on the Unix workstations at the Department of Math and Computer Science at the Eindhoven University of Technology. He maintained it until 1995, and on June 1, 2001, released it under its own BSD-style license. The tarball includes a library named libwrap that implements the actual functionality. Initially, only services that were spawned for each connection from a super-server (such as inetd) got ''wrapped'', utilizing the tcpd program. However most common network service daemons today can be linked against libwrap directly. This is used by ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Wietse Venema
Wietse Zweitze Venema (born 1951) is a Dutch programmer and physicist best known for writing the Postfix email system. He also wrote TCP Wrapper and collaborated with Dan Farmer to produce the computer security tools SATAN and The Coroner's Toolkit. Biography He studied physics at the University of Groningen, continuing there to get a PhD in 1984 with the dissertation ''Left-right symmetry in nuclear beta decay''. He spent 12 years at Eindhoven University as a systems architect in the Mathematics and Computer Science department, and spent part of this time writing tools for Electronic Data Interchange. Since emigrating to the U.S. in 1996 and until 2015, he has been working for the IBM Thomas J. Watson Research Center in New York State. On March 24, 2015, he announced he was leaving IBM for Google. Awards Awards Venema has received for his work: * Security Summit Hall of Fame Award (July 1998) * SAGE Outstanding Achievement Award (November 1999) * NLUUG Award (November 2 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Tar (file Format)
In computing, tar is a shell command for combining multiple computer files into a single archive file. It was originally developed for magnetic tape storage reading and writing data for a sequential I/O device with no file system, and the name is short for the format description "tape archive". When stored in a file system, a file that tar reads and writes is often called a ''tarball''. A tarball contains metadata for the contained files including the name, ownership, timestamps, permissions and directory organization. As a file containing other files with associated metadata, a tarball is useful for software distribution and backup. POSIX abandoned ''tar'' in favor of '' pax'', yet ''tar'' continues to have widespread use. History The command was introduced to Unix in January 1979, replacing the tp program (which in turn replaced "tap"). The file structure was standardized in POSIX.1-1988 and later POSIX.1-2001, and became a format supported by most modern file arc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Userspace
A modern computer operating system usually uses virtual memory to provide separate address spaces or regions of a single address space, called user space and kernel space. This separation primarily provides memory protection and hardware protection from malicious or errant software behaviour. Kernel space is strictly reserved for running a privileged operating system kernel, kernel extensions, and most device drivers. In contrast, user space is the memory area where application software and some drivers execute, typically with one address space per process. Overview The term user space (or userland) refers to all code that runs outside the operating system's kernel. User space usually refers to the various programs and libraries that the operating system uses to interact with the kernel: software that performs input/output, manipulates file system objects, application software, etc. Each user space process usually runs in its own virtual memory space, and, unless explici ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Internet Control Message Protocol
The Internet Control Message Protocol (ICMP) is a supporting protocol in the Internet protocol suite. It is used by network devices, including routers, to send error messages and operational information indicating success or failure when communicating with another IP address. For example, an error is indicated when a requested service is not available or that a host or router could not be reached. ICMP differs from transport protocols such as TCP and UDP in that it is not typically used to exchange data between systems, nor is it regularly employed by end-user network applications (with the exception of some diagnostic tools like ping and traceroute). A separate Internet Control Message Protocol (called ICMPv6) is used with IPv6. Technical details ICMP is part of the Internet protocol suite as defined in RFC 792. ICMP messages are typically used for diagnostic or control purposes or generated in response to errors in IP operations (as specified in RFC 1122). ICMP ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
User Datagram Protocol
In computer networking, the User Datagram Protocol (UDP) is one of the core communication protocols of the Internet protocol suite used to send messages (transported as datagrams in Network packet, packets) to other hosts on an Internet Protocol (IP) network. Within an IP network, UDP does not require prior communication to set up communication channels or data paths. UDP is a connectionless protocol, meaning that messages are sent without negotiating a connection and that UDP does not keep track of what it has sent. UDP provides checksums for data integrity, and port numbers for addressing different functions at the source and destination of the datagram. It has no Handshake (computing), handshaking dialogues and thus exposes the user's program to any Reliability (computer networking), unreliability of the underlying network; there is no guarantee of delivery, ordering, or duplicate protection. If error-correction facilities are needed at the network interface level, an applica ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Transmission Control Protocol
The Transmission Control Protocol (TCP) is one of the main communications protocol, protocols of the Internet protocol suite. It originated in the initial network implementation in which it complemented the Internet Protocol (IP). Therefore, the entire suite is commonly referred to as TCP/IP. TCP provides reliability (computer networking), reliable, ordered, and error detection and correction, error-checked delivery of a reliable byte stream, stream of octet (computing), octets (bytes) between applications running on hosts communicating via an IP network. Major internet applications such as the World Wide Web, email, remote administration, and file transfer rely on TCP, which is part of the transport layer of the TCP/IP suite. Transport Layer Security, SSL/TLS often runs on top of TCP. TCP is Connection-oriented communication, connection-oriented, meaning that sender and receiver firstly need to establish a connection based on agreed parameters; they do this through three-way Ha ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Fail2ban
Fail2Ban is an intrusion prevention system, intrusion prevention software framework. Written in the Python (programming language), Python programming language, it is designed to prevent brute-force attacks. It is able to run on POSIX systems that have an interface to a packet-control system or firewall installed locally, such as iptables or TCP Wrapper. Functionality Fail2ban operates by monitoring Computer data logging, log files (e.g. , , etc.) for selected entries and running scripts based on them. Most commonly this is used to block selected IP addresses that may belong to Host (network), hosts that are trying to breach the system's security. It can ban any host IP address that makes too many login attempts or performs any other unwanted action within a time frame defined by the administrator. It includes support for both IPv4 and IPv6. Optionally longer bans can be custom-configured for "recidivist" abusers that keep coming back. Fail2Ban is typically set up to unban a block ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
DenyHosts
DenyHosts is a log-based intrusion-prevention security tool for SSH servers written in Python. It is intended to prevent brute-force attacks on SSH servers by monitoring invalid login attempts in the authentication log and blocking the originating IP addresses. DenyHosts is developed by Phil Schwartz, who is also the developer of Kodos Python Regular Expression Debugger. Operation DenyHosts checks the end of the authentication log for recent failed login attempts. It records information about their originating IP addresses and compares the number of invalid attempts to a user-specified threshold. If there have been too many invalid attempts it assumes a dictionary attack is occurring and prevents the IP address from making any further attempts by adding it to /etc/hosts.deny on the server. DenyHosts 2.0 and above support centralized synchronization, so that repeat offenders are blocked from many computers. The sitdenyhosts.netgathers statistics from computers running the software. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Worm (computing)
A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. It often uses a computer network to spread itself, relying on security failures on the target computer to access it. It will use this machine as a host to scan and infect other computers. When these new worm-invaded computers are controlled, the worm will continue to scan and infect other computers using these computers as hosts, and this behaviour will continue. Computer worms use recursive methods to copy themselves without host programs and distribute themselves based on exploiting the advantages of exponential growth, thus controlling and infecting more and more computers in a short time. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a targeted computer. Many worms are designed only to spread, and do not attempt to change the systems they pass throu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
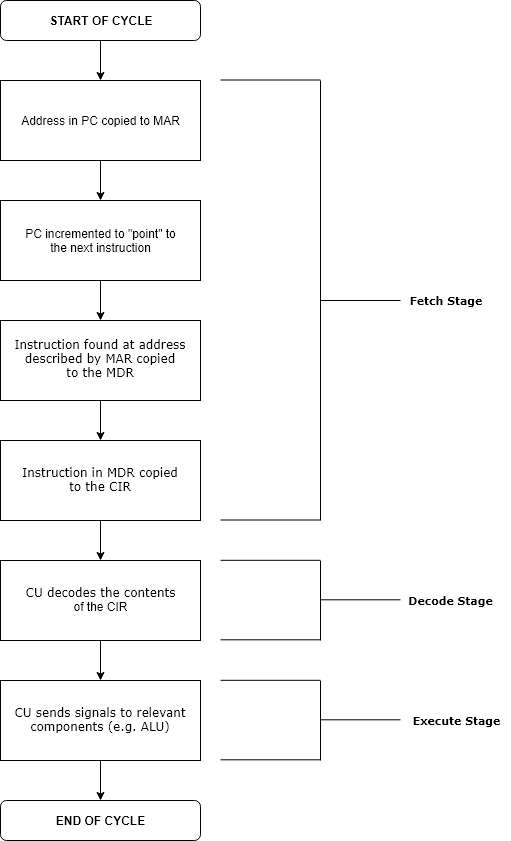
Run Time (program Lifecycle Phase)
Execution in computer and software engineering is the process by which a computer or virtual machine interprets and acts on the instructions of a computer program. Each instruction of a program is a description of a particular action which must be carried out, in order for a specific problem to be solved. Execution involves repeatedly following a " fetch–decode–execute" cycle for each instruction done by the control unit. As the executing machine follows the instructions, specific effects are produced in accordance with the semantics of those instructions. Programs for a computer may be executed in a batch process without human interaction or a user may type commands in an interactive session of an interpreter. In this case, the "commands" are simply program instructions, whose execution is chained together. The term run is used almost synonymously. A related meaning of both "to run" and "to execute" refers to the specific action of a user starting (or ''launching'' o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Linker (computing)
A linker or link editor is a computer program that combines intermediate software build files such as object file, object and library (computing), library files into a single executable file such as a program or library. A linker is often part of a toolchain that includes a compiler and/or assembler (computing), assembler that generates intermediate files that the linker processes. The linker may be integrated with other toolchain development tool, tools such that the user does not interact with the linker directly. A simpler version that writes its Input/output, output directly to Computer memory, memory is called the ''loader'', though loader (computing), loading is typically considered a separate process. Overview Computer programs typically are composed of several parts or modules; these parts/modules do not need to be contained within a single object file, and in such cases refer to each other using symbol (computing), symbols as addresses into other modules, which are ma ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Daemon (computer Software)
In computing, a daemon is a program that runs as a background process, rather than being under the direct control of an interactive user. Customary convention is to name a daemon process with the letter ''d'' as a suffix to indicate that it's a daemon. For example, is a daemon that implements system logging facility, and is a daemon that serves incoming SSH connections. Even though the concept can apply to many computing systems, the term ''daemon'' is used almost exclusively in the context of Unix-based systems. In other contexts, different terms are used for the same concept. Systems often start daemons at boot time that will respond to network requests, hardware activity, or other programs by performing some task. Daemons such as cron may also perform defined tasks at scheduled times. Terminology In the context of computing, the word is generally pronounced either as or . The term was coined by the programmers at MIT's Project MAC. According to Fernando J. Corbat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |