|
Simple API For Grid Applications
The Simple API for Grid Applications (SAGA) is a family of related standards specified by the Open Grid Forum to define an application programming interface (API) for common distributed computing functionality. Overview The SAGA specification for distributed computing originally consisted of a single document, GFD.90, which was released in 2009. The SAGA API does not strive to replace Globus or similar grid computing middleware systems, and does not target middleware developers, but application developers with no background on grid computing. Such developers typically wish to devote their time to their own goals and minimize the time spent coding infrastructure functionality. The API insulates application developers from middleware. The specification of services, and the protocols to interact with them, is out of the scope of SAGA. Rather, the API seeks to hide the detail of any service infrastructures that may or may not be used to implement the functionality that the ap ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Logo Saga
A logo (abbreviation of logotype; ) is a graphic mark, emblem, or symbol used to aid and promote public identification and recognition. It may be of an abstract or figurative design or include the text of the name it represents as in a wordmark. In the days of hot metal typesetting, a logotype was one word cast as a single piece of type (e.g. "The" in ATF Garamond), as opposed to a Typographic ligature, ligature, which is two or more letters joined, but not forming a word. By extension, the term was also used for a uniquely set and arranged typeface or colophon (publishing), colophon. At the level of mass communication and in common usage, a company's logo is today often synonymous with its trademark or brand.Wheeler, Alina. ''Designing Brand Identity'' © 2006 John Wiley & Sons, Inc. (page 4) Etymology Online Etymology Dictionary, Douglas Harper's Online Etymology Dictionary states that the term 'logo' used in 1937 "probably a shortening of logogram". History Numerous inv ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SAGA Architecture
is a series of science fantasy role-playing video games by Square Enix. The series originated on the Game Boy in 1989 as the creation of Akitoshi Kawazu at Square. It has since continued across multiple platforms, from the Super NES to the PlayStation 2. The series is notable for its emphasis on open world exploration, non-linear branching plots, and occasionally unconventional gameplay. This distinguishes the games from most of Square's other franchises. Development The ''SaGa'' series was created by game designer Akitoshi Kawazu, whose contributions prior to the franchise's introduction include ''Final Fantasy'' and ''Final Fantasy II''. At a time when Nintendo's Game Boy was becoming popular worldwide due to the puzzle game ''Tetris'', then-Square president Masashi Miyamoto requested that a development team create a game for the handheld console. Kawazu and fellow designer Koichi Ishii suggested that the company develop a role-playing video game, thus making ''Makai Tous ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Condor High-Throughput Computing System
HTCondor is an open-source high-throughput computing software framework for coarse-grained distributed parallelization of computationally intensive tasks. It can be used to manage workload on a dedicated cluster of computers, or to farm out work to idle desktop computersso-called cycle scavenging. HTCondor runs on Linux, Unix, Mac OS X, FreeBSD, and Microsoft Windows operating systems. HTCondor can integrate both dedicated resources (rack-mounted clusters) and non-dedicated desktop machines (cycle scavenging) into one computing environment. HTCondor is developed by the HTCondor team at the University of Wisconsin–Madison and is freely available for use. HTCondor follows an open-source philosophy and is licensed under the Apache License 2.0. While HTCondor makes use of unused computing time, leaving computers turned on for use with HTCondor will increase energy consumption and associated costs. Starting from version 7.1.1, HTCondor can hibernate and wake machines based on ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Amazon EC2
Amazon Elastic Compute Cloud (EC2) is a part of Amazon.com's cloud-computing platform, Amazon Web Services (AWS), that allows users to rent virtual computers on which to run their own computer applications. EC2 encourages scalable deployment of applications by providing a web service through which a user can boot an Amazon Machine Image (AMI) to configure a virtual machine, which Amazon calls an "instance", containing any software desired. A user can create, launch, and terminate server-instances as needed, paying by the second for active servershence the term "elastic". EC2 provides users with control over the geographical location of instances that allows for latency optimization and high levels of redundancy. In November 2010, Amazon switched its own retail website platform to EC2 and AWS. History Amazon announced a limited public beta test of EC2 on August 25, 2006, offering access on a first-come, first-served basis. Amazon added two new instance types (Large and Extra ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Plug-in (computing)
In computing, a plug-in (or plugin, add-in, addin, add-on, or addon) is a software component that adds a specific feature to an existing computer program. When a program supports plug-ins, it enables customization. A theme or skin is a preset package containing additional or changed graphical appearance details, achieved by the use of a graphical user interface (GUI) that can be applied to specific software and websites to suit the purpose, topic, or tastes of different users to customize the look and feel of a piece of computer software or an operating system front-end GUI (and window managers). Purpose and examples Applications may support plug-ins to: * enable third-party developers to extend an application * support easily adding new features * reduce the size of an application by not loading unused features * separate source code from an application because of incompatible software licenses. Types of applications and why they use plug-ins: * Digital audio workstation ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Program Lifecycle Phase
{{about, a technical topic, project management, software development process Program lifecycle phases are the stages a computer program undergoes, from initial creation to deployment and execution. The phases are edit time, compile time, link time, distribution time, installation time, load time, and run time. Lifecycle phases do not necessarily happen in a linear order, and they can be intertwined in various ways. For example, when modifying a program, software developers may need to repeatedly edit, compile, install, and execute it on their own computers to ensure sufficient quality before it can be distributed to users; copies of the modified program are then downloaded, installed, and executed by users on their computers. Phases Edit time is when the source code of the program is being edited. This spans initial creation to any bug fix, refactoring, or addition of new features. Editing is typically performed by a person, but automated design tools and metaprogramming sy ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Late Binding
In computing, late binding or dynamic linkage—though not an identical process to dynamically linking imported code libraries—is a computer programming mechanism in which the method being called upon an object, or the function being called with arguments, is looked up by name at runtime. In other words, a name is associated with a particular operation or object at runtime, rather than during compilation. The name dynamic binding is sometimes used, but is more commonly used to refer to dynamic scope. With early binding, or static binding, in an object-oriented language, the compilation phase fixes all types of variables and expressions. This is usually stored in the compiled program as an offset in a virtual method table ("v-table"). In contrast, with late binding, the compiler does not read enough information to verify the method exists or bind its slot on the v-table. Instead, the method is looked up by name at runtime. The primary advantage of using late binding in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Design Pattern
In software engineering, a software design pattern is a general, reusable solution to a commonly occurring problem within a given context in software design. It is not a finished design that can be transformed directly into source or machine code. Rather, it is a description or template for how to solve a problem that can be used in many different situations. Design patterns are formalized best practices that the programmer can use to solve common problems when designing an application or system. Object-oriented design patterns typically show relationships and interactions between classes or objects, without specifying the final application classes or objects that are involved. Patterns that imply mutable state may be unsuited for functional programming languages. Some patterns can be rendered unnecessary in languages that have built-in support for solving the problem they are trying to solve, and object-oriented patterns are not necessarily suitable for non-object-oriented ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
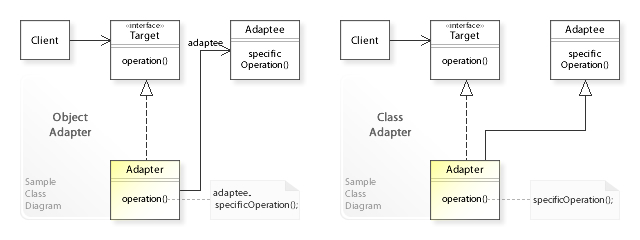
Adaptor Pattern
In software engineering, the adapter pattern is a software design pattern (also known as wrapper, an alternative naming shared with the decorator pattern) that allows the interface of an existing class to be used as another interface. It is often used to make existing classes work with others without modifying their source code. An example is an adapter that converts the interface of a Document Object Model of an XML document into a tree structure that can be displayed. Overview The adapter design pattern is one of the twenty-three well-known Gang of Four design patterns that describe how to solve recurring design problems to design flexible and reusable object-oriented software, that is, objects that are easier to implement, change, test, and reuse. The adapter design pattern solves problems like: * How can a class be reused that does not have an interface that a client requires? * How can classes that have incompatible interfaces work together? * How can an alternative interfac ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Service Discovery
Service discovery is the process of automatically detecting devices and services on a computer network. This reduces the need for manual configuration by users and administrators. A service discovery protocol (SDP) is a network protocol that helps accomplish service discovery. Service discovery aims to reduce the configuration efforts required by users and administrators. Service discovery requires a common language to allow software agents to make use of one another's services without the need for continuous user intervention. Protocols There are many service discovery protocols, including: * Bluetooth Service Discovery Protocol (SDP) * DNS Service Discovery (DNS-SD), a component of zero-configuration networking * DNS, as used for example in Kubernetes * Dynamic Host Configuration Protocol (DHCP) * Internet Storage Name Service (iSNS) * Jini for Java objects. * Lightweight Service Discovery (LSD), for mobile ad hoc networks * Link Layer Discovery Protocol (LLDP) standar ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Remote Procedure Call
In distributed computing, a remote procedure call (RPC) is when a computer program causes a procedure ( subroutine) to execute in a different address space (commonly on another computer on a shared network), which is coded as if it were a normal (local) procedure call, without the programmer explicitly coding the details for the remote interaction. That is, the programmer writes essentially the same code whether the subroutine is local to the executing program, or remote. This is a form of client–server interaction (caller is client, executor is server), typically implemented via a request–response message-passing system. In the object-oriented programming paradigm, RPCs are represented by remote method invocation (RMI). The RPC model implies a level of location transparency, namely that calling procedures are largely the same whether they are local or remote, but usually, they are not identical, so local calls can be distinguished from remote calls. Remote calls are usually ord ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Replication (computing)
Replication in computing involves sharing information so as to ensure consistency between redundant resources, such as software or hardware components, to improve reliability, fault-tolerance, or accessibility. Terminology Replication in computing can refer to: * ''Data replication'', where the same data is stored on multiple storage devices * ''Computation replication'', where the same computing task is executed many times. Computational tasks may be: ** ''Replicated in space'', where tasks are executed on separate devices ** ''Replicated in time'', where tasks are executed repeatedly on a single device Replication in space or in time is often linked to scheduling algorithms. Access to a replicated entity is typically uniform with access to a single non-replicated entity. The replication itself should be transparent to an external user. In a failure scenario, a failover of replicas should be hidden as much as possible with respect to quality of service. Computer scien ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |