|
Shim (computing)
In computer programming, a shim is a library that transparently intercepts API calls and changes the arguments passed, handles the operation itself or redirects the operation elsewhere. Shims can be used to support an old API in a newer environment, or a new API in an older environment. Shims can also be used for running programs on different software platforms than they were developed for. Shims for older APIs typically come about when the behavior of an API changes, thereby causing compatibility issues for older applications which still rely on the older functionality; in such cases, the older API can still be supported by a thin compatibility layer on top of the newer code. Shims for newer APIs are defined as: "a library that brings a new API to an older environment, using only the means of that environment." Examples * Web polyfills implement newer web standards using older standards and JavaScript, if the newer standard is not available in a given web browser. * S ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Shared Memory
In computer science, shared memory is memory that may be simultaneously accessed by multiple programs with an intent to provide communication among them or avoid redundant copies. Shared memory is an efficient means of passing data between programs. Depending on context, programs may run on a single processor or on multiple separate processors. Using memory for communication inside a single program, e.g. among its multiple threads, is also referred to as shared memory. In hardware In computer hardware, ''shared memory'' refers to a (typically large) block of random access memory (RAM) that can be accessed by several different central processing units (CPUs) in a multiprocessor computer system. Shared memory systems may use: * uniform memory access (UMA): all the processors share the physical memory uniformly; * non-uniform memory access (NUMA): memory access time depends on the memory location relative to a processor; * cache-only memory architecture (COMA): the local memo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Apple Computer
Apple Inc. is an American multinational technology company headquartered in Cupertino, California, United States. Apple is the largest technology company by revenue (totaling in 2021) and, as of June 2022, is the world's biggest company by market capitalization, the fourth-largest personal computer vendor by unit sales and second-largest mobile phone manufacturer. It is one of the Big Five American information technology companies, alongside Alphabet, Amazon, Meta, and Microsoft. Apple was founded as Apple Computer Company on April 1, 1976, by Steve Wozniak, Steve Jobs and Ronald Wayne to develop and sell Wozniak's Apple I personal computer. It was incorporated by Jobs and Wozniak as Apple Computer, Inc. in 1977 and the company's next computer, the Apple II, became a best seller and one of the first mass-produced microcomputers. Apple went public in 1980 to instant financial success. The company developed computers featuring innovative graphical user interfaces, in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Glue Code
Adhesive, also known as glue, cement, mucilage, or paste, is any non-metallic substance applied to one or both surfaces of two separate items that binds them together and resists their separation. The use of adhesives offers certain advantages over other binding techniques such as sewing, mechanical fastenings, or welding. These include the ability to bind different materials together, the more efficient distribution of stress across a joint, the cost-effectiveness of an easily mechanized process, and greater flexibility in design. Disadvantages of adhesive use include decreased stability at high temperatures, relative weakness in bonding large objects with a small bonding surface area, and greater difficulty in separating objects during testing. Adhesives are typically organized by the method of adhesion followed by ''reactive'' or ''non-reactive'', a term which refers to whether the adhesive chemically reacts in order to harden. Alternatively, they can be organized eithe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Glide Wrapper
Glide is a 3D graphics API developed by 3dfx Interactive for their ''Voodoo Graphics'' 3D accelerator cards. Although it originally started as a proprietary API, it was later open sourced by 3dfx. It was dedicated to rendering performance, supporting geometry and texture mapping primarily, in data formats identical to those used internally in their cards. Wide adoption of 3Dfx led to Glide being extensively used in the late 1990s, but further refinement of Microsoft's Direct3D and the appearance of full OpenGL implementations from other graphics card vendors, in addition to growing diversity in 3D hardware, eventually caused it to become superfluous. Glide wrappers and emulators Glide emulator development has been in progress since the late 1990s. During 3dfx's lifetime, the company was aggressive at trying to stop these attempts to emulate their proprietary API, shutting down early emulation projects with legal threats. However, just before it ceased operations and had its ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Driver Wrapper
A driver wrapper is a subroutine in a software library that functions as an adapter between an operating system and a driver, such as a device driver, that was not designed for that operating system. It can enable the use of devices for which no drivers for the particular operating system are available. In particular, Microsoft Windows is the dominant family of operating systems for IBM PC compatible computers, and many devices are supplied with drivers for Windows but not other operating systems. Windows driver wrappers for Linux Several open source software projects allow using Microsoft Windows drivers under another operating system, such as Linux. Examples include network drivers for wireless cards (such as NDISwrapper for Linux or Project Evil for FreeBSD) and the NTFS file system (see Captive NTFS). The common thread among these examples is the use of ''wrapper'' technology, which allows execution of the drivers in a foreign environment. Limitations for driver wrappers ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Application Virtualization
Application virtualization is a software technology that encapsulates computer programs from the underlying operating system on which they are executed. A fully virtualized application is not installed in the traditional sense, although it is still executed as if it were. The application behaves at runtime like it is directly interfacing with the original operating system and all the resources managed by it, but can be isolated or sandboxed to varying degrees. In this context, the term "virtualization" refers to the artifact being encapsulated (application), which is quite different from its meaning in hardware virtualization, where it refers to the artifact being abstracted (physical hardware). Description Full application virtualization requires a virtualization layer. Application virtualization layers replace part of the runtime environment normally provided by the operating system. The layer intercepts all disk operations of virtualized applications and transparently redirec ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
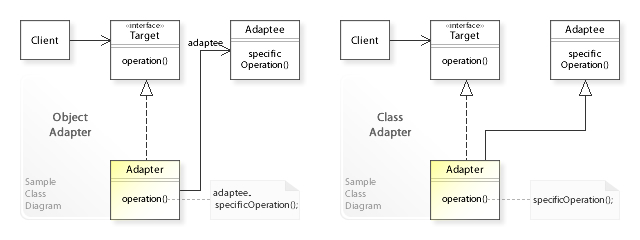
Adapter Pattern
In software engineering, the adapter pattern is a software design pattern (also known as wrapper, an alternative naming shared with the decorator pattern) that allows the interface of an existing class to be used as another interface. It is often used to make existing classes work with others without modifying their source code. An example is an adapter that converts the interface of a Document Object Model of an XML document into a tree structure that can be displayed. Overview The adapter design pattern is one of the twenty-three well-known Gang of Four design patterns that describe how to solve recurring design problems to design flexible and reusable object-oriented software, that is, objects that are easier to implement, change, test, and reuse. The adapter design pattern solves problems like: * How can a class be reused that does not have an interface that a client requires? * How can classes that have incompatible interfaces work together? * How can an alternative interfa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
LD PRELOAD
In computing, a dynamic linker is the part of an operating system that loads and links the shared libraries needed by an executable when it is executed (at "run time"), by copying the content of libraries from persistent storage to RAM, filling jump tables and relocating pointers. The specific operating system and executable format determine how the dynamic linker functions and how it is implemented. Linking is often referred to as a process that is performed when the executable is compiled, while a dynamic linker is a special part of an operating system that loads external shared libraries into a running process and then binds those shared libraries dynamically to the running process. This approach is also called dynamic linking or late linking. Implementations Microsoft Windows Dynamic-link library, or DLL, is Microsoft's implementation of the shared library concept in the Microsoft Windows and OS/2 operating systems. These libraries usually have the file extension ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Linux
Linux ( or ) is a family of open-source Unix-like operating systems based on the Linux kernel, an operating system kernel first released on September 17, 1991, by Linus Torvalds. Linux is typically packaged as a Linux distribution, which includes the kernel and supporting system software and libraries, many of which are provided by the GNU Project. Many Linux distributions use the word "Linux" in their name, but the Free Software Foundation uses the name "GNU/Linux" to emphasize the importance of GNU software, causing some controversy. Popular Linux distributions include Debian, Fedora Linux, and Ubuntu, the latter of which itself consists of many different distributions and modifications, including Lubuntu and Xubuntu. Commercial distributions include Red Hat Enterprise Linux and SUSE Linux Enterprise. Desktop Linux distributions include a windowing system such as X11 or Wayland, and a desktop environment such as GNOME or KDE Plasma. Distributions intended for ser ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microsoft
Microsoft Corporation is an American multinational technology corporation producing computer software, consumer electronics, personal computers, and related services headquartered at the Microsoft Redmond campus located in Redmond, Washington, United States. Its best-known software products are the Windows line of operating systems, the Microsoft Office suite, and the Internet Explorer and Edge web browsers. Its flagship hardware products are the Xbox video game consoles and the Microsoft Surface lineup of touchscreen personal computers. Microsoft ranked No. 21 in the 2020 Fortune 500 rankings of the largest United States corporations by total revenue; it was the world's largest software maker by revenue as of 2019. It is one of the Big Five American information technology companies, alongside Alphabet, Amazon, Apple, and Meta. Microsoft was founded by Bill Gates and Paul Allen on April 4, 1975, to develop and sell BASIC interpreters for the Altair 8800. It rose to do ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Bug
A software bug is an error, flaw or fault in the design, development, or operation of computer software that causes it to produce an incorrect or unexpected result, or to behave in unintended ways. The process of finding and correcting bugs is termed " debugging" and often uses formal techniques or tools to pinpoint bugs. Since the 1950s, some computer systems have been designed to deter, detect or auto-correct various computer bugs during operations. Bugs in software can arise from mistakes and errors made in interpreting and extracting users' requirements, planning a program's design, writing its source code, and from interaction with humans, hardware and programs, such as operating systems or libraries. A program with many, or serious, bugs is often described as ''buggy''. Bugs can trigger errors that may have ripple effects. The effects of bugs may be subtle, such as unintended text formatting, through to more obvious effects such as causing a program to crash, freezing th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Principle Of Least Privilege
In information security, computer science, and other fields, the principle of least privilege (PoLP), also known as the principle of minimal privilege (PoMP) or the principle of least authority (PoLA), requires that in a particular abstraction layer of a computing environment, every module (such as a process, a user, or a program, depending on the subject) must be able to access only the information and resources that are necessary for its legitimate purpose. Details The principle means giving a user account or process only those privileges which are essential to perform its intended function. For example, a user account for the sole purpose of creating backups does not need to install software: hence, it has rights only to run backup and backup-related applications. Any other privileges, such as installing new software, are blocked. The principle applies also to a personal computer user who usually does work in a normal user account, and opens a privileged, password protected ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |


.jpg)

