|
Sunset Provision
In public policy, a sunset provision or sunset clause is a measure within a statute, regulation or other law that provides that the law shall cease to have effect after a specific date, unless further legislative action is taken to extend the law. Most laws do not have sunset clauses and therefore remain in force indefinitely, except under systems in which desuetude applies. Origin The roots of sunset provisions are laid in Roman law of the mandate but the first philosophical reference is traced in the laws of Plato. At the time of the Roman Republic, the empowerment of the Roman Senate to collect special taxes and to activate troops was limited in time and extent. Those empowerments ended before the expiration of an electoral office, such as the Proconsul. The rule ''Ad tempus concessa post tempus censetur denegata'' is translated as "what is admitted for a period will be refused after the period". The same rules were applied in the Roman emergency legislation. The fundamenta ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Public Policy
Public policy is an institutionalized proposal or a decided set of elements like laws, regulations, guidelines, and actions to solve or address relevant and real-world problems, guided by a conception and often implemented by programs. Public policy can be considered to be the sum of government direct and indirect activities and has been conceptualized in a variety of ways. They are created and/or enacted on behalf of the public typically by a government. Sometimes they are made by nonprofit organisations or are made in co-production with communities or citizens, which can include potential experts, scientists, engineers and stakeholders or scientific data, or sometimes use some of their results. They are typically made by policy-makers affiliated with (in democratic polities) currently elected politicians. Therefore, the "policy process is a complex political process in which there are many actors: elected politicians, political party leaders, pressure groups, civil serva ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
USA PATRIOT Act
The USA PATRIOT Act (commonly known as the Patriot Act) was a landmark Act of the United States Congress, signed into law by President George W. Bush. The formal name of the statute is the Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism (USA PATRIOT) Act of 2001, and the commonly used short name is a contrived acronym that is embedded in the name set forth in the statute. The Patriot Act was enacted following the September 11 attacks and the 2001 anthrax attacks with the stated goal of tightening U.S. national security, particularly as it related to foreign terrorism. In general, the act included three main provisions: * expanded surveillance abilities of law enforcement, including by tapping domestic and international phones; * easier interagency communication to allow federal agencies to more effectively use all available resources in counterterrorism efforts; and * increased penalties for terrorism crimes a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Robert C
The name Robert is an ancient Germanic given name, from Proto-Germanic "fame" and "bright" (''Hrōþiberhtaz''). Compare Old Dutch ''Robrecht'' and Old High German ''Hrodebert'' (a compound of '' Hruod'' ( non, Hróðr) "fame, glory, honour, praise, renown" and ''berht'' "bright, light, shining"). It is the second most frequently used given name of ancient Germanic origin. It is also in use as a surname. Another commonly used form of the name is Rupert. After becoming widely used in Continental Europe it entered England in its Old French form ''Robert'', where an Old English cognate form (''Hrēodbēorht'', ''Hrodberht'', ''Hrēodbēorð'', ''Hrœdbœrð'', ''Hrœdberð'', ''Hrōðberχtŕ'') had existed before the Norman Conquest. The feminine version is Roberta. The Italian, Portuguese, and Spanish form is Roberto. Robert is also a common name in many Germanic languages, including English, German, Dutch, Norwegian, Swedish, Scots, Danish, and Icelandic. It can ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Filibuster
A filibuster is a political procedure in which one or more members of a legislative body prolong debate on proposed legislation so as to delay or entirely prevent decision. It is sometimes referred to as "talking a bill to death" or "talking out a bill", and is characterized as a form of obstruction in a legislature or other decision-making body. Etymology The term "filibuster" ultimately derives from the Dutch ("freebooter", a pillaging and plundering adventurer), but the precise history of the word's borrowing into English is obscure.''Oxford English Dictionary'', "filibuster", pp. F:212–213. The ''Oxford English Dictionary'' finds its only known use in early modern English in a 1587 book describing "flibutors" who robbed supply convoys. In the late 18th century, the term was re-borrowed into English from its French form , a form that was used until the mid-19th century. The modern English form "filibuster" was borrowed in the early 1850s from the Spanish (lawless plund ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Congressional Budget And Impoundment Control Act Of 1974
The Congressional Budget and Impoundment Control Act of 1974 (, , ) is a United States federal law that governs the role of the Congress in the United States budget process. The Congressional budget process Titles I through IX of the law are also known as the Congressional Budget Act of 1974. Title II created the Congressional Budget Office. Title III governs the procedures by which Congress annually adopts a budget resolution, a concurrent resolution that is not signed by the President, which sets fiscal policy for the Congress. This budget resolution sets limits on revenues and spending that may be enforced in Congress through procedural objections called points of order. The budget resolution can also specify that a budget reconciliation bill be written, which the Congress will then consider under expedited procedures. Later amendments The act has been amended several times, including provisions in the Balanced Budget and Emergency Deficit Control Act of 1985, the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Federal Assault Weapons Ban
The Public Safety and Recreational Firearms Use Protection Act, popularly known as the Federal Assault Weapons Ban (AWB), was a subsection of the Violent Crime Control and Law Enforcement Act of 1994, a United States federal law which included a prohibition on the manufacture for civilian use of certain semi-automatic firearms that were defined as assault weapons as well as certain ammunition magazines that were defined as large capacity. The 10-year ban was passed by the U.S. Congress on August 25, 1994 and was signed into law by President Bill Clinton on September 13, 1994. The ban applied only to weapons manufactured after the date of the ban's enactment. It expired on September 13, 2004, in accordance with its sunset provision. Several constitutional challenges were filed against provisions of the ban, but all were rejected by the courts. There have been multiple attempts to renew the ban, but none have succeeded. Criminologists and other researchers found that the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Civil Liability
In law, liable means "responsible or answerable in law; legally obligated". Legal liability concerns both civil law and criminal law and can arise from various areas of law, such as contracts, torts, taxes, or fines given by government agencies. The claimant is the one who seeks to establish, or prove, liability. Theories of liability Claimants can prove liability through a myriad of different theories, known as theories of liability. Which theories of liability are available in a given case depends on nature of the law in question. For example, in case involving a contractual dispute, one available theory of liability is breach of contract; or in the tort context, negligence, negligence per se, respondeat superior, vicarious liability, strict liability, or intentional conduct are all valid theories of liability. Each theory of liability has certain conditions, or elements, that must be proven by the claimant before liability will be established. For example, the theory of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Privacy
Privacy (, ) is the ability of an individual or group to seclude themselves or information about themselves, and thereby express themselves selectively. The domain of privacy partially overlaps with security, which can include the concepts of appropriate use and protection of information. Privacy may also take the form of bodily integrity. The right not to be subjected to unsanctioned invasions of privacy by the government, corporations, or individuals is part of many countries' privacy laws, and in some cases, constitutions. The concept of universal individual privacy is a modern concept primarily associated with Western culture, particularly British and North American, and remained virtually unknown in some cultures until recent times. Now, most cultures recognize the ability of individuals to withhold certain parts of personal information from wider society. With the rise of technology, the debate regarding privacy has shifted from a bodily sense to a digital sense. As the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Voicemail
A voicemail system (also known as voice message or voice bank) is a computer-based system that allows users and subscribers to exchange personal voice messages; to select and deliver voice information; and to process transactions relating to individuals, organizations, products, and services, using an ordinary phone. The term is also used more broadly to denote any system of conveying a stored telecommunications voice messages, including using an answering machine. Most cell phone services offer voicemail as a basic feature; many corporate private branch exchanges include versatile internal voice-messaging services, and *98 vertical service code subscription is available to most individual and small business landline subscribers (in the US). History The term ''Voicemail'' was coined by Televoice International (later Voicemail International, or VMI) for their introduction of the first US-wide Voicemail service in 1980. Although VMI trademarked the term, it eventually became a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Foreign Intelligence Surveillance Act
The Foreign Intelligence Surveillance Act of 1978 ("FISA" , ) is a United States federal law that establishes procedures for the physical and electronic surveillance and the collection of "foreign intelligence information" between "foreign powers" and "agents of foreign powers" suspected of espionage or terrorism.50 USC §1801(b) "'Agent of a foreign power' means— (1) any person other than a United States person, who— (A) acts in the United States as an officer or employee of a foreign power, or as a member of a foreign power as defined in subsection (a)(4), irrespective of whether the person is inside the United States; (B) acts for or on behalf of a foreign power which engages in clandestine intelligence activities in the United States contrary to the interests of the United States, when the circumstances indicate that such person may engage in such activities, or when such person knowingly aids or abets any person in the conduct of such activities or knowingly conspire ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
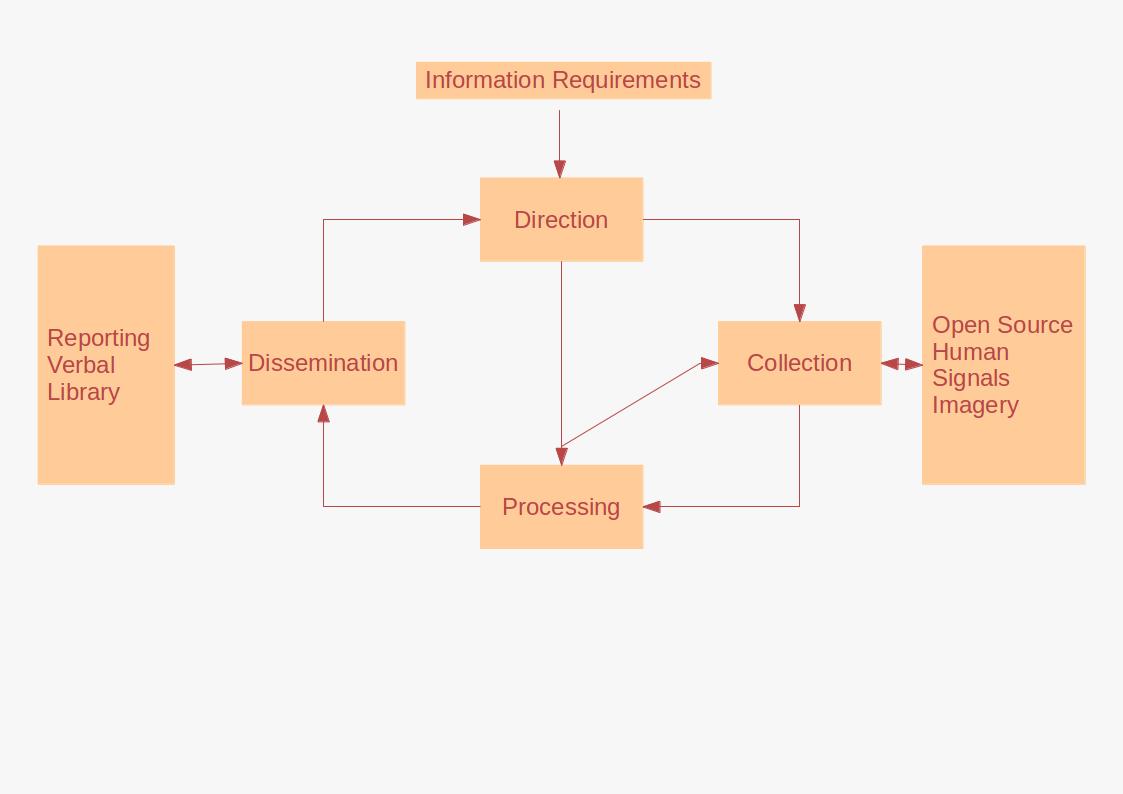
Foreign Intelligence
Intelligence assessment, or simply intel, is the development of behavior forecasts or recommended courses of action to the leadership of an organisation, based on wide ranges of available overt and covert information (intelligence). Assessments develop in response to leadership declaration requirements to inform decision-making. Assessment may be executed on behalf of a state, military or commercial organisation with ranges of information sources available to each. An intelligence assessment reviews available information and previous assessments for relevance and currency. Where there requires additional information, the analyst may direct some collection. Intelligence studies is the academic field concerning intelligence assessment, especially relating to international relations and military science. Process Intelligence assessment is based on a customer requirement or need, which may be a standing requirement or tailored to a specific circumstance or a Request for Infor ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Fraud
Computer fraud is a cybercrime and the act of using a computer to take or alter electronic data, or to gain unlawful use of a computer or system. In the United States, computer fraud is specifically proscribed by the Computer Fraud and Abuse Act, which criminalizes computer-related acts under federal jurisdiction. Types of computer fraud include: *Distributing hoax emails *Accessing unauthorized computers *Engaging in data mining via spyware and malware * Hacking into computer systems to illegally access personal information, such as credit cards or Social Security numbers *Sending computer viruses or worms with the intent to destroy or ruin another party's computer or system. Phishing, social engineering, viruses, and DDoS attacks are fairly well-known tactics used to disrupt service or gain access to another's network, but this list is not inclusive. Notable incidents The Melissa Virus/Worm The Melissa Virus appeared on thousands of email systems on 26 March 1999. It was ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |