|
Spring Framework
The Spring Framework is an application framework and inversion of control container for the Java platform. The framework's core features can be used by any Java application, but there are extensions for building web applications on top of the Java EE (Enterprise Edition) platform. The framework does not impose any specific programming model.. The framework has become popular in the Java community as an addition to the Enterprise JavaBeans (EJB) model. The Spring Framework is free and open source software. Version history The first version was written by Rod Johnson, who released the framework with the publication of his book ''Expert One-on-One J2EE Design and Development'' in October 2002. The framework was first released under the Apache 2.0 license in June 2003. The first production release, 1.0, was released in March 2004. The Spring 1.2.6 framework won a Jolt productivity award and a JAX Innovation Award in 2006. Spring 2.0 was released in October 2006, Spring 2.5 in N ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Reactive Streams
Reactive Streams is an initiative to provide a Technical standard, standard for asynchronous serial communication, asynchronous stream processing with Asynchronous I/O, non-blocking back pressure. __TOC__ Origin Reactive Streams started as an initiative in late 2013 between engineers at Netflix, Pivotal Software, Pivotal and Lightbend. Some of the earliest discussions began in 2013 between the Play Framework, Play and Akka (toolkit), Akka teams at Lightbend. Lightbend is one of the main contributors of Reactive Streams. Other contributors include Red Hat, Oracle Corporation, Oracle, Twitter and spray.io. Goals The main goal of Reactive Streams is to govern the exchange of stream data across an asynchronous boundary like passing elements on to another Thread (computing), thread or thread-pool while ensuring that the receiving side is not forced to Data buffer, buffer arbitrary amounts of data. In other words, back pressure is an integral part of this model in order to allow th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Inversion Of Control
In software engineering, inversion of control (IoC) is a design principle in which custom-written portions of a computer program receive the flow of control from an external source (e.g. a framework). The term "inversion" is historical: a software architecture with this design "inverts" control as compared to procedural programming. In procedural programming, a program's custom code calls reusable libraries to take care of generic tasks, but with inversion of control, it is the external code or framework that is in control and calls the custom code. Inversion of control has been widely used by application development frameworks since the rise of GUI environments and continues to be used both in GUI environments and in web server application frameworks. Inversion of control makes the framework extensible by the methods defined by the application programmer. Event-driven programming is often implemented using IoC so that the custom code need only be concerned with the handling ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
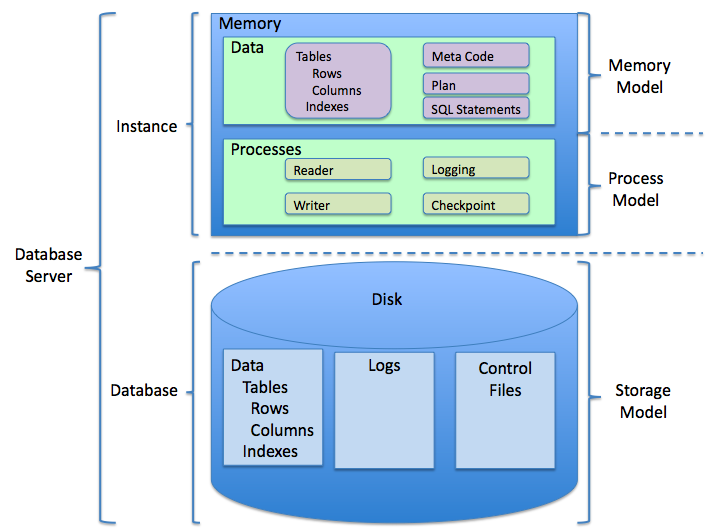
NoSQL
NoSQL (originally meaning "Not only SQL" or "non-relational") refers to a type of database design that stores and retrieves data differently from the traditional table-based structure of relational databases. Unlike relational databases, which organize data into rows and columns like a spreadsheet, NoSQL databases use a single data structure—such as key–value pairs, wide columns, graphs, or documents—to hold information. Since this non-relational design does not require a fixed schema, it scales easily to manage large, often unstructured datasets. NoSQL systems are sometimes called ''"Not only SQL"'' because they can support SQL-like query languages or work alongside SQL databases in polyglot-persistent setups, where multiple database types are combined. Non-relational databases date back to the late 1960s, but the term "NoSQL" emerged in the early 2000s, spurred by the needs of Web 2.0 companies like social media platforms. NoSQL databases are popular in big data ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Java Database Connectivity
Java Database Connectivity (JDBC) is an application programming interface (API) for the Java programming language which defines how a client may access a database. It is a Java-based data access technology used for Java database connectivity. It is part of the Java Standard Edition platform, from Oracle Corporation. It provides methods to query and update data in a database, and is oriented toward relational databases. A JDBC-to-ODBC bridge enables connections to any ODBC-accessible data source in the Java virtual machine (JVM) host environment. History and implementation Sun Microsystems released JDBC as part of Java Development Kit (JDK) 1.1 on February 19, 1997. Since then it has been part of the Java Platform, Standard Edition (Java SE). The JDBC classes are contained in the Java package and . Starting with version 3.1, JDBC has been developed under the Java Community Process. JSR 54 specifies JDBC 3.0 (included in J2SE 1.4), JSR 114 specifies the JDBC Rowset additions, a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
RDBMS
A relational database (RDB) is a database based on the relational model of data, as proposed by E. F. Codd in 1970. A Relational Database Management System (RDBMS) is a type of database management system that stores data in a structured format using rows and columns. Many relational database systems are equipped with the option of using SQL (Structured Query Language) for querying and updating the database. History The concept of relational database was defined by E. F. Codd at IBM in 1970. Codd introduced the term ''relational'' in his research paper "A Relational Model of Data for Large Shared Data Banks". In this paper and later papers, he defined what he meant by ''relation''. One well-known definition of what constitutes a relational database system is composed of Codd's 12 rules. However, no commercial implementations of the relational model conform to all of Codd's rules, so the term has gradually come to describe a broader class of database systems, which at a minim ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Access
Data access is a generic term referring to a process which has both an IT-specific meaning and other connotations involving access rights in a broader legal and/or political sense. In the former it typically refers to software and activities related to storing, retrieving, or acting on data housed in a database or other information repository, repository. Details Two fundamental types of data access exist: # sequential access (as in magnetic tape data storage, magnetic tape, for example) # random access (as in indexed digital media, media) Data access crucially involves authorization to access different data repositories. Data access can help distinguish the abilities of administrators and users. For example, administrators may have the ability to remove, edit and add data, while general users may not even have "read" rights if they lack access to particular information. Historically, each repository (including each different database, file system, etc.), might require the use of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spring Roo
Spring Roo is a Open-source software, open-source software tool that uses convention over configuration, convention-over-configuration principles to provide rapid application development of Java (programming language), Java-based enterprise software. The project has been deprecated and active development has ended. Motivation and history Spring Roo's mission statement is to ''"fundamentally improve Java developer productivity without compromising engineering integrity or flexibility"''. The technology was first demonstrated during the opening keynote at the SpringOne Europe developer conference on 27 April 2009, with an initial alpha release concurrently being published. During the keynote an application was built live on-stage that would be used by conference attendees to vote on the preferred name for the project (which at that time was codenamed "Roo" within SpringSource). Ultimately the name "Spring Roo" was preferred over alternatives including Spring Boost, Spring Spark, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Convention Over Configuration
Convention over configuration (also known as coding by convention) is a software design paradigm used by software frameworks that attempts to decrease the number of decisions that a developer using the framework is required to make without necessarily losing flexibility and don't repeat yourself (DRY) principles. The concept was introduced by David Heinemeier Hansson to describe the philosophy of the Ruby on Rails web framework, but is related to earlier ideas like the concept of "sensible defaults" and the principle of least astonishment in user interface design. The phrase essentially means a developer only needs to specify unconventional aspects of the application. For example, if there is a class Sales in the model, the corresponding table in the database is called "sales" by default. It is only if one deviates from this convention, such as the table "product sales", that one needs to write code regarding these names. When the convention implemented by the tool ma ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spring Security
Spring Security is a Java/Java EE framework that provides authentication, authorization and other security features for enterprise applications. The project was started in late 2003 as 'Acegi Security' (pronounced ''Ah-see-gee'' , whose letters are the first, third, fifth, seventh, and ninth characters from the English alphabet, in order to prevent name conflicts) by Ben Alex, with it being publicly released under the Apache License in March 2004. Subsequently, Acegi was incorporated into the Spring portfolio as Spring Security, an official Spring sub-project. The first public release under the new name was Spring Security 2.0.0 in April 2008, with commercial support and training available from SpringSource. Authentication flow Diagram 1 shows the basic flow of an authentication request using the Spring Security system. It shows the different filters and how they interact from the initial browser request, to either a successful authentication or an HTTP 403 error. Key authenti ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Authorization
Authorization or authorisation (see American and British English spelling differences#-ise, -ize (-isation, -ization), spelling differences), in information security, computer security and identity management, IAM (Identity and Access Management), is the function of specifying rights/privileges for accessing resources, in most cases through an access policy, and then deciding whether a particular ''subject'' has privilege to access a particular ''resource''. Examples of ''subjects'' include human users, computer software and other Computer hardware, hardware on the computer. Examples of ''resources'' include individual files or an item's data, computer programs, computer Computer hardware, devices and functionality provided by computer applications. For example, user accounts for human resources staff are typically configured with authorization for accessing employee records. Authorization is closely related to access control, which is what enforces the authorization policy by d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |