|
Purewire
Barracuda Networks, Inc. is a company providing security, networking and storage products based on network appliances and cloud services. The company's security products include products for protection against email, web surfing, web hackers and instant messaging threats such as spam, spyware, trojans, and viruses. The company's networking and storage products include web filtering, load balancing, application delivery controllers, message archiving, NG firewalls, backup services and data protection. History Barracuda Networks was founded in 2003 by Dean Drako (founding CEO), Michael Perone, and Zach Levow; the company introduced the Barracuda Spam and Virus Firewall in the same year. In 2007 the company moved its headquarters to Campbell, California, and opened an office in Ann Arbor, Michigan. In January 2006, it closed its first outside investment of $40 million from Sequoia Capital and Francisco Partners. On January 29, 2008, Barracuda Networks was sued by Trend Micro over ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Dean Drako
Dean Drako is an American businessman and entrepreneur who has started more than five companies. Drako was founder, president and CEO of Barracuda Networks from 2003 to July 2012. Drako is currently President and CEO of Eagle Eye Networks, IC Manage and Drako Motors. He is also chairman of Brivo. He graduated with a BS in Electrical Engineering from the University of Michigan and an MS in Electrical Engineering from UC Berkeley. As of 2020, Drako is a holder of 53 patents, including patents on video streaming, video storage, video analytics, digital image processing, network security & protocols, digital circuits, biochemical assays, and electric automobiles. Career history In 1982, Drako founded his first company, which sold a bulletin board system software package called T-net, used to share messages via modems. Drako used the profits to fund his college education. In 1992, Drako founded Design Acceleration, Inc, served as its CEO, and sold it to Cadence Design System ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Private Company
A privately held company (or simply a private company) is a company whose shares and related rights or obligations are not offered for public subscription or publicly negotiated in the respective listed markets, but rather the company's stock is offered, owned, traded, exchanged privately, or Over-the-counter (finance), over-the-counter. In the case of a closed corporation, there are a relatively small number of shareholders or company members. Related terms are closely-held corporation, unquoted company, and unlisted company. Though less visible than their public company, publicly traded counterparts, private companies have major importance in the world's economy. In 2008, the 441 list of largest private non-governmental companies by revenue, largest private companies in the United States accounted for ($1.8 trillion) in revenues and employed 6.2 million people, according to ''Forbes''. In 2005, using a substantially smaller pool size (22.7%) for comparison, the 339 companies on ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Appliance
A computer appliance is a home appliance with software or firmware that is specifically designed to provide a specific computing resource. Such devices became known as ''appliances'' because of the similarity in role or management to a home appliance, which are generally ''closed and sealed'', and are not serviceable by the user or owner. The hardware and software are delivered as an integrated product and may even be pre-configured before delivery to a customer, to provide a turn-key solution for a particular application. Unlike general purpose computers, appliances are generally not designed to allow the customers to change the software and the underlying operating system, or to flexibly reconfigure the hardware. Another form of appliance is the virtual appliance, which has similar functionality to a dedicated hardware appliance, but is distributed as a software virtual machine image for a hypervisor-equipped device. Overview Traditionally, software applications run on top ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Firewall (networking)
In computing, a firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted network and an untrusted network, such as the Internet. History The term ''firewall'' originally referred to a wall intended to confine a fire within a line of adjacent buildings. Later uses refer to similar structures, such as the metal sheet separating the engine compartment of a vehicle or aircraft from the passenger compartment. The term was applied in the late 1980s to network technology that emerged when the Internet was fairly new in terms of its global use and connectivity. The predecessors to firewalls for network security were routers used in the late 1980s. Because they already segregated networks, routers could apply filtering to packets crossing them. Before it was used in real-life computing, the term appeared in the 1983 computer-hacking movie ' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Application Delivery
Application streaming is a form of on-demand software distribution. In these scenarios, only essential portions of an application's code need to be installed on the computer: while the end user performs actions in the application, the necessary code and files are delivered over the network as and when they are required. Application streaming is a related concept to application virtualization, where applications are run directly from a virtual machine on a central server that is completely separate from the local system. By contrast, application streaming runs the program locally, but still involves the centralized storage of application code. Stream server An application is ''packaged'' and stored on a streaming server. ''Packaging'' or ''sequencing'' produces an image of the application in a way that orders delivery or predicatively optimizes delivery to the client. Launch and streaming of application The initial launch of an application would be important for the end user and t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Load Balancing (computing)
In computing, load balancing is the process of distributing a set of tasks over a set of resources (computing units), with the aim of making their overall processing more efficient. Load balancing can optimize the response time and avoid unevenly overloading some compute nodes while other compute nodes are left idle. Load balancing is the subject of research in the field of parallel computers. Two main approaches exist: static algorithms, which do not take into account the state of the different machines, and dynamic algorithms, which are usually more general and more efficient but require exchanges of information between the different computing units, at the risk of a loss of efficiency. Problem overview A load-balancing algorithm always tries to answer a specific problem. Among other things, the nature of the tasks, the algorithmic complexity, the hardware architecture on which the algorithms will run as well as required error tolerance, must be taken into account. Therefore c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Web Filtering
An Internet filter is software that restricts or controls the content an Internet user is capable to access, especially when utilized to restrict material delivered over the Internet via the Web, Email, or other means. Content-control software determines what content will be available or be blocked. Such restrictions can be applied at various levels: a government can attempt to apply them nationwide (see Internet censorship), or they can, for example, be applied by an Internet service provider to its clients, by an employer to its personnel, by a school to its students, by a library to its visitors, by a parent to a child's computer, or by an individual users to their own computers. The motive is often to prevent access to content which the computer's owner(s) or other authorities may consider objectionable. When imposed without the consent of the user, content control can be characterised as a form of internet censorship. Some content-control software includes time control funct ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Virus
A computer virus is a type of computer program that, when executed, replicates itself by modifying other computer programs and inserting its own code. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus, a metaphor derived from biological viruses. Computer viruses generally require a host program. The virus writes its own code into the host program. When the program runs, the written virus program is executed first, causing infection and damage. A computer worm does not need a host program, as it is an independent program or code chunk. Therefore, it is not restricted by the host program, but can run independently and actively carry out attacks. Virus writers use social engineering deceptions and exploit detailed knowledge of security vulnerabilities to initially infect systems and to spread the virus. Viruses use complex anti-detection/stealth strategies to evade antivirus software. Motives for creating viruses can inclu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Trojan Horse (computing)
In computing, a Trojan horse is any malware that misleads users of its true intent. The term is derived from the Ancient Greek story of the deceptive Trojan Horse that led to the fall of the city of Troy. Trojans generally spread by some form of social engineering; for example, where a user is duped into executing an email attachment disguised to appear innocuous (e.g., a routine form to be filled in), or by clicking on some fake advertisement on social media or anywhere else. Although their payload can be anything, many modern forms act as a backdoor, contacting a controller who can then have unauthorized access to the affected computer. Ransomware attacks are often carried out using a Trojan. Unlike computer viruses and worms, Trojans generally do not attempt to inject themselves into other files or otherwise propagate themselves. Use of the term It's not clear where or when the concept, and this term for it, was first used, but by 1971 the first Unix manual assumed its r ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spyware
Spyware (a portmanteau for spying software) is software with malicious behaviour that aims to gather information about a person or organization and send it to another entity in a way that harms the user—for example, by violating their privacy or endangering their device's security. This behaviour may be present in malware as well as in legitimate software. Websites may engage in spyware behaviours like web tracking. Hardware devices may also be affected. Spyware is frequently associated with advertising and involves many of the same issues. Because these behaviors are so common, and can have non-harmful uses, providing a precise definition of spyware is a difficult task.FTC Report (2005)." History The first recorded use of the term :wikt:spyware, spyware occurred on October 16, 1995 in a Usenet post that poked fun at Microsoft's business model.Vossen, Roland (attributed); October 21, 1995Win 95 Source code in c!!posted to rec..programmer; retrieved from groups.google.co ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spam (electronic)
Spamming is the use of messaging systems to send multiple unsolicited messages (spam) to large numbers of recipients for the purpose of commercial advertising, for the purpose of non-commercial proselytizing, for any prohibited purpose (especially the fraudulent purpose of phishing), or simply repeatedly sending the same message to the same user. While the most widely recognized form of spam is email spam, the term is applied to similar abuses in other media: instant messaging spam, Usenet newsgroup spam, Web search engine spam, spam in blogs, wiki spam, online classified ads spam, mobile phone messaging spam, Internet forum spam, junk fax transmissions, social spam, spam mobile apps, television advertising and file sharing spam. It is named after Spam, a luncheon meat, by way of a Monty Python sketch about a restaurant that has Spam in almost every dish in which Vikings annoyingly sing "Spam" repeatedly. Spamming remains economically viable because advertisers have no ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
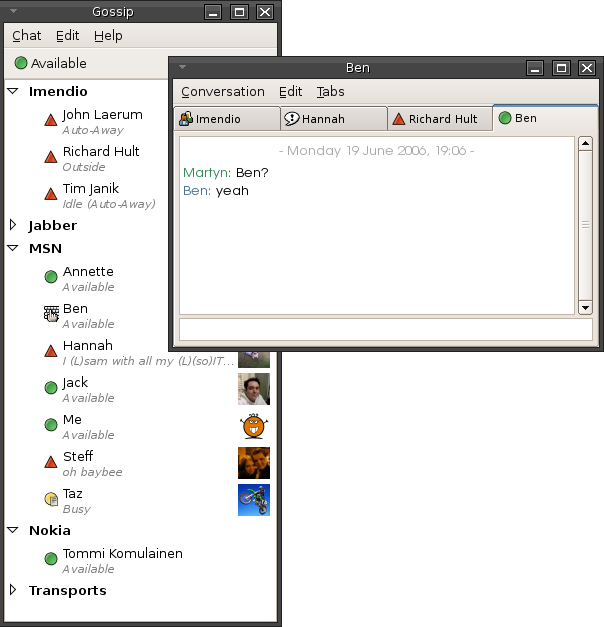
Instant Messaging
Instant messaging (IM) technology is a type of online chat allowing real-time text transmission over the Internet or another computer network. Messages are typically transmitted between two or more parties, when each user inputs text and triggers a transmission to the recipient(s), who are all connected on a common network. It differs from email in that conversations over instant messaging happen in real-time (hence "instant"). Most modern IM application (computing), applications (sometimes called "social messengers", "messaging apps" or "chat apps") use push technology and also add other features such as emojis (or graphical smileys), file transfer, chatbots, voice over IP, or Videotelephony, video chat capabilities. Instant messaging systems tend to facilitate connections between specified known users (often using a contact list also known as a "buddy list" or "friend list"), and can be standalone applications or integrated into e.g. a wider social media platform, or a website ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |




.jpg)