|
Protected Streaming
Protected Streaming is a DRM technology by Adobe. The aim of the technology is to protect digital content (video or audio) from unauthorized use. Protected Streaming consists of many different techniques; basically there are two main components: encryption and SWF verification. This technique is used by the Hulu desktop player and the RTÉ Player. Fifa.com also uses this technique to serve the videos on the official site. Some videos on YouTube also use RTMPE, including those uploaded there by BBC Worldwide. Encryption Streamed content is encrypted by the Flash Media Server "on the fly", so that the source file itself does not need to be encrypted (a significant difference from Microsoft's DRM). For transmission ("streaming"), a special protocol is required, either RTMPE or RTMPS. RTMPS uses SSL-encryption. In contrast, RTMPE is designed to be simpler than RTMPS, by removing the need to acquire a SSL Certificate. RTMPE makes use of well-known industry standard cryptographic ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Digital Rights Management
Digital rights management (DRM) is the management of legal access to digital content. Various tools or technological protection measures (TPM) such as access control technologies can restrict the use of proprietary hardware and copyrighted works. DRM technologies govern the use, modification, and distribution of copyrighted works (such as software and multimedia content), as well as systems that enforce these policies within devices. Laws in many countries criminalize the circumvention of DRM, communication about such circumvention, and the creation and distribution of tools used for such circumvention. Such laws are part of the United States' Digital Millennium Copyright Act (DMCA), and the European Union's Information Society Directive (the French DADVSI is an example of a member state of the European Union implementing the directive). DRM techniques include licensing agreements and encryption. The industry has expanded the usage of DRM to various hardware products, such as K ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Diffie–Hellman Key Exchange
Diffie–Hellman key exchangeSynonyms of Diffie–Hellman key exchange include: * Diffie–Hellman–Merkle key exchange * Diffie–Hellman key agreement * Diffie–Hellman key establishment * Diffie–Hellman key negotiation * Exponential key exchange * Diffie–Hellman protocol * Diffie–Hellman handshake is a mathematical method of securely exchanging cryptographic keys over a public channel and was one of the first public-key protocols as conceived by Ralph Merkle and named after Whitfield Diffie and Martin Hellman. DH is one of the earliest practical examples of public key exchange implemented within the field of cryptography. Published in 1976 by Diffie and Hellman, this is the earliest publicly known work that proposed the idea of a private key and a corresponding public key. Traditionally, secure encrypted communication between two parties required that they first exchange keys by some secure physical means, such as paper key lists transported by a trusted courier. The Di ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Streisand Effect
Attempts to hide, remove, or censor information often have the unintended consequence of increasing awareness of that information via the Internet. This is called the Streisand effect. It is named after American singer and actress Barbra Streisand, whose attempt to suppress the California Coastal Records Project's photograph of her cliff-top residence in Malibu, California, taken to document California coastal erosion, inadvertently drew greater attention to the photograph in 2003. Attempts to suppress information are often made through cease-and-desist letters, but instead of being suppressed, the information receives extensive publicity, as well as media extensions such as videos and spoof songs, which can be mirrored on the Internet or distributed on file-sharing networks. In addition, seeking or obtaining an injunction to prohibit something from being published or remove something that is already published can lead to increased publicity of the published work. The Streisa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
DMCA Takedown
The Online Copyright Infringement Liability Limitation Act (OCILLA) is United States federal law that creates a conditional 'safe harbor' for online service providers (OSP) (a group which includes internet service providers (ISP) and other Internet intermediaries) by shielding them for their own acts of direct copyright infringement (when they make unauthorized copies) as well as shielding them from potential secondary liability for the infringing acts of others. OCILLA was passed as a part of the 1998 Digital Millennium Copyright Act (DMCA) and is sometimes referred to as the " Safe Harbor" provision or as "DMCA 512" because it addeSection 512to Title 17 of the United States Code. By exempting Internet intermediaries from copyright infringement liability provided they follow certain rules, OCILLA attempts to strike a balance between the competing interests of copyright owners and digital users. Overview The 1998 DMCA was the U.S. implementation of the 1996 WIPO Copyright Treat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Trusted Client
In computing, a trusted client is a device or program controlled by the user of a service, but with restrictions designed to prevent its use in ways not authorized by the provider of the service. That is, the client is a device that vendors trust and then sell to the consumers, whom they do not trust. Examples include video games played over a computer network or the Content Scramble System (CSS) in DVDs. Trusted client software is considered fundamentally insecure: once the security is broken by one user, the break is trivially copyable and available to others. As computer security specialist Bruce Schneier states, "Against the average user, anything works; there's no need for complex security software. Against the skilled attacker, on the other hand, nothing works." Trusted client hardware is somewhat more secure, but not a complete solution. Trusted clients are attractive to business as a form of vendor lock-in: sell the trusted client at a loss and charge more than would be ot ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Adobe Flash Player
Adobe Flash Player (known in Internet Explorer, Firefox, and Google Chrome as Shockwave Flash) is Software, computer software for viewing multimedia contents, executing rich Internet applications, and streaming media, streaming audio and video content created on the Adobe Flash platform. It can run from a web browser as a browser plug-in (computing), plug-in or independently on supported devices. Originally created by FutureWave under the name FutureSplash Player, it was renamed to Macromedia Flash Player after Macromedia acquired FutureWave in 1996. It was then developed and distributed by Adobe Systems as Flash Player after Adobe acquired Macromedia in 2005. It is currently developed and distributed by Zhongcheng for users in China, and by Harman International for enterprise users outside of China, in collaboration with Adobe. Flash Player runs SWF files that can be created by Adobe Flash Professional, Adobe Flash Builder or by third-party tools such as FlashDevelop. Flash P ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Man-in-the-middle Attack
In cryptography and computer security, a man-in-the-middle, monster-in-the-middle, machine-in-the-middle, monkey-in-the-middle, meddler-in-the-middle, manipulator-in-the-middle (MITM), person-in-the-middle (PITM) or adversary-in-the-middle (AiTM) attack is a cyberattack where the attacker secretly relays and possibly alters the communications between two parties who believe that they are directly communicating with each other, as the attacker has inserted themselves between the two parties. One example of a MITM attack is active eavesdropping, in which the attacker makes independent connections with the victims and relays messages between them to make them believe they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. The attacker must be able to intercept all relevant messages passing between the two victims and inject new ones. This is straightforward in many circumstances; for example, an attacker wit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Through Obscurity
Security through obscurity (or security by obscurity) is the reliance in security engineering on design or implementation secrecy as the main method of providing security to a system or component. History An early opponent of security through obscurity was the locksmith Alfred Charles Hobbs, who in 1851 demonstrated to the public how state-of-the-art locks could be picked. In response to concerns that exposing security flaws in the design of locks could make them more vulnerable to criminals, he said: "Rogues are very keen in their profession, and know already much more than we can teach them." There is scant formal literature on the issue of security through obscurity. Books on security engineering cite Kerckhoffs' doctrine from 1883, if they cite anything at all. For example, in a discussion about secrecy and openness in Nuclear Command and Control: e benefits of reducing the likelihood of an accidental war were considered to outweigh the possible benefits of secrecy. This ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Transport Layer Security
Transport Layer Security (TLS) is a cryptographic protocol designed to provide communications security over a computer network. The protocol is widely used in applications such as email, instant messaging, and voice over IP, but its use in securing HTTPS remains the most publicly visible. The TLS protocol aims primarily to provide security, including privacy (confidentiality), integrity, and authenticity through the use of cryptography, such as the use of certificates, between two or more communicating computer applications. It runs in the presentation layer and is itself composed of two layers: the TLS record and the TLS handshake protocols. The closely related Datagram Transport Layer Security (DTLS) is a communications protocol providing security to datagram-based applications. In technical writing you often you will see references to (D)TLS when it applies to both versions. TLS is a proposed Internet Engineering Task Force (IETF) standard, first defined in 1999, and the c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Adobe Systems
Adobe Inc. ( ), originally called Adobe Systems Incorporated, is an American multinational computer software company incorporated in Delaware and headquartered in San Jose, California. It has historically specialized in software for the creation and publication of a wide range of content, including graphics, photography, illustration, animation, multimedia/video, motion pictures, and print. Its flagship products include Adobe Photoshop image editing software; Adobe Illustrator vector-based illustration software; Adobe Acrobat Reader and the Portable Document Format (PDF); and a host of tools primarily for audio-visual content creation, editing and publishing. Adobe offered a bundled solution of its products named Adobe Creative Suite, which evolved into a subscription software as a service (SaaS) offering named Adobe Creative Cloud. The company also expanded into digital marketing software and in 2021 was considered one of the top global leaders in Customer Experience Manageme ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
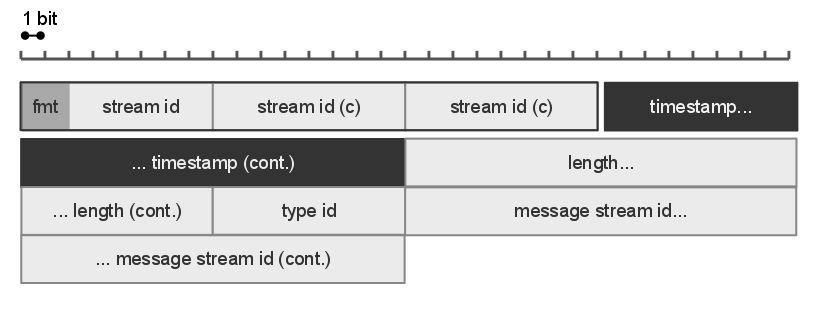
RTMPS
Real-Time Messaging Protocol (RTMP) is a communication protocol for streaming audio, video, and data over the Internet. Originally developed as a proprietary protocol by Macromedia for streaming between Flash Player and the Flash Communication Server, Adobe (which acquired Macromedia) has released an incomplete version of the specification of the protocol for public use. The RTMP protocol has multiple variations: # RTMP proper, the "plain" protocol which works on top of Transmission Control Protocol (TCP) and uses port number 1935 by default. # RTMPS, which is RTMP over a Transport Layer Security (TLS/SSL) connection. # RTMPE, which is RTMP encrypted using Adobe's own security mechanism. While the details of the implementation are proprietary, the mechanism uses industry standard cryptographic primitives. # RTMPT, which is encapsulated within HTTP requests to traverse firewalls. RTMPT is frequently found utilizing cleartext requests on TCP ports 80 and 443 to bypass most corpor ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |