|
Profiling (information Science)
In information science, profiling refers to the process of construction and application of user profiles generated by computerized data analysis. This is the use of algorithms or other mathematical techniques that allow the discovery of patterns or correlations in large quantities of data, aggregated in databases. When these patterns or correlations are used to identify or represent people, they can be called ''profiles''. Other than a discussion of profiling ''technologies'' or ''population profiling'', the notion of profiling in this sense is not just about the construction of profiles, but also concerns the ''application'' of group profiles to individuals, e. g., in the cases of credit scoring, price discrimination, or identification of security risks . Profiling is being used in fraud prevention, ambient intelligence, and consumer analytics. Statistical methods of profiling include Knowledge Discovery in Databases (KDD). The profiling process The technical proces ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Science
Information science (also known as information studies) is an academic field which is primarily concerned with analysis, collection, classification, manipulation, storage, retrieval, movement, dissemination, and protection of information. Practitioners within and outside the field study the application and the usage of knowledge in organizations in addition to the interaction between people, organizations, and any existing information systems with the aim of creating, replacing, improving, or understanding the information systems. Historically, information science (informatics) is associated with computer science, data science, psychology, technology, library science, healthcare, and intelligence agencies. However, information science also incorporates aspects of diverse fields such as archival science, cognitive science, commerce, law, linguistics, museology, management, mathematics, philosophy, public policy, and social sciences. Foundations Scope and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
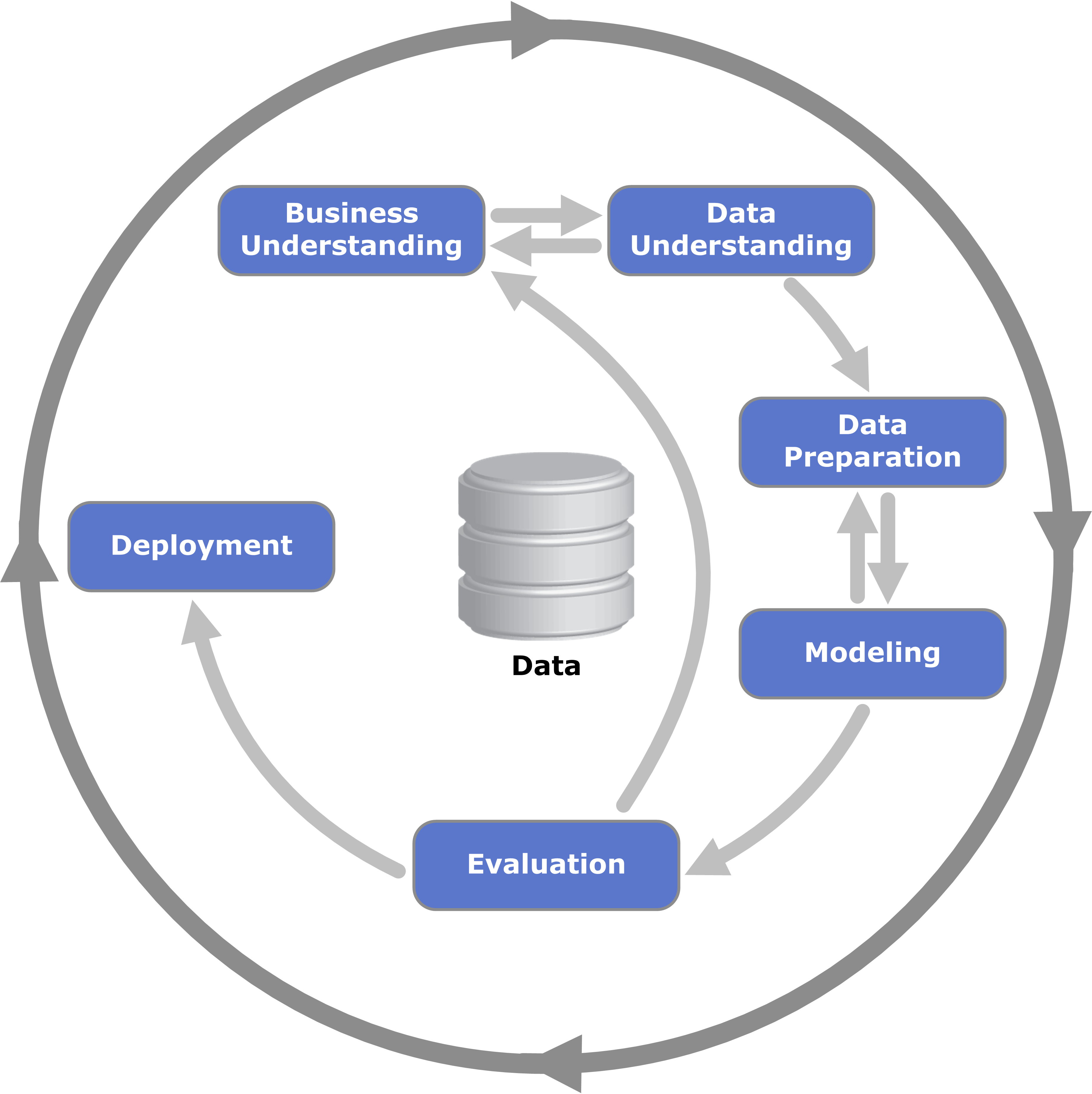
CRISP-DM
Cross-industry standard process for data mining, known as CRISP-DM,Shearer C., ''The CRISP-DM model: the new blueprint for data mining'', J Data Warehousing (2000); 5:13—22. is an open standard process model that describes common approaches used by data mining experts. It is the most widely-used analytics model. In 2015, IBM released a new methodology called ''Analytics Solutions Unified Method for Data Mining/Predictive Analytics'' (also known as ASUM-DM) which refines and extends CRISP-DM. History CRISP-DM was conceived in 1996 and became a European Union project under the ESPRIT funding initiative in 1997. The project was led by five companies: Integral Solutions Ltd (ISL), Teradata, Daimler AG, NCR Corporation and OHRA, an insurance company. This core consortium brought different experiences to the project: ISL, later acquired and merged into SPSS. The computer giant NCR Corporation produced the Teradata data warehouse and its own data mining software. Daimler-Benz h ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pricing
Pricing is the process whereby a business sets the price at which it will sell its products and services, and may be part of the business's marketing plan. In setting prices, the business will take into account the price at which it could acquire the goods, the manufacturing cost, the marketplace, competition, market condition, brand, and quality of product. Pricing is a fundamental aspect of product management and is one of the four Ps of the marketing mix, the other three aspects being product, promotion, and place. Price is the only revenue generating element amongst the four Ps, the rest being cost centers. However, the other Ps of marketing will contribute to decreasing price elasticity and so enable price increases to drive greater revenue and profits. Pricing can be a manual or automatic process of applying prices to purchase and sales orders, based on factors such as: a fixed amount, quantity break, promotion or sales campaign, specific vendor quote, price pre ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Product Promotion
In marketing, promotion refers to any type of marketing communication used to inform target audiences of the relative merits of a product, service, brand or issue, most of the time persuasive in nature. It helps marketers to create a distinctive place in customers' mind, it can be either a cognitive or emotional route. The aim of promotion is to increase brand awareness, create interest, generate sales or create brand loyalty. It is one of the basic elements of the market mix, which includes the four Ps, i.e., product, price, place, and promotion. Promotion is also one of the elements in the promotional mix or promotional plan. These are personal selling, advertising, sales promotion, direct marketing, publicity, word of mouth and may also include event marketing, exhibitions and trade shows. A promotional plan specifies how much attention to pay to each of the elements in the promotional mix, and what proportion of the budget should be allocated to each element. Promotion cover ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Customer Analytics
In sales, commerce, and economics, a customer (sometimes known as a client, buyer, or purchaser) is the recipient of a good, service, product or an idea - obtained from a seller, vendor, or supplier via a financial transaction or exchange for money or some other valuable consideration. Etymology and terminology Early societies relied on a gift economy based on favours. Later, as commerce developed, less permanent human relations were formed, depending more on transitory needs rather than enduring social desires. Customers are generally said to be the purchasers of goods and services, while clients are those who receive personalized advice and solutions. Although such distinctions have no contemporary semantic weight, agencies such as law firms, film studios, and health care providers tend to prefer '' client'', while grocery stores, banks, and restaurants tend to prefer ''customer'' instead. Clients The term client is derived from Latin ''clients'' or ''care'' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Forensic Science
Forensic science, also known as criminalistics, is the application of science to Criminal law, criminal and Civil law (legal system), civil laws, mainly—on the criminal side—during criminal investigation, as governed by the legal standards of admissible evidence and criminal procedure. Forensic science is a broad field that includes; DNA analysis, fingerprint analysis, blood stain pattern analysis, firearms examination and ballistics, tool mark analysis, serology, toxicology, hair and fiber analysis, entomology, questioned documents, anthropology, odontology, pathology, epidemiology, footwear and tire tread analysis, drug chemistry, paint and glass analysis, digital audio video and photo analysis. Forensic scientists collect, preserve, and analyze scientific evidence during the course of an investigation. While some forensic scientists travel to the scene of the crime to collect the evidence themselves, others occupy a laboratory role, performing analysis on objects brough ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Attention Management
Attention management refers to models and tools for supporting the management of attention at the individual or at the collective level (cf. attention economy), and at the short-term (quasi real time) or at a longer term (over periods of weeks or months). The ability to control distractions and stay focused is essential to produce higher quality results. A research conducted by Stanford shows that single-tasking is more effective and productive than multi-tasking. Different studies have been conducted in using Information and Communications Technology (ICT) for supporting attention, and in particular, models have been elaborated for supporting attention. Background The scarcity of attention is the underlying assumption for attention management; the researcher Herbert A. Simon pointed out that when there is a vast availability of information, attention becomes the more scarce resource as human beings cannot digest all the information. Fundamentally, attention is limited by the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Adaptive Hypermedia
Adaptive hypermedia (AH) uses hypermedia which is adaptive according to a ''user model''. In contrast to linear media, where all users are offered a standard series of hyperlinks, adaptive hypermedia (AH) tailors what the user is offered based on a model of the user's goals, preferences and knowledge, thus providing links or content most appropriate to the current user. Background Adaptive hypermedia is used in educational hypermedia, on-line information and help systems, as well as institutional information systems. Adaptive educational hypermedia tailors what the learner sees to that learner's goals, abilities, needs, interests, and knowledge of the subject, by providing hyperlinks that are most relevant to the user in an effort to shape the user's cognitive load. The teaching tools "adapt" to the learner. On-line information systems provide reference access to information for users with a different knowledge level of the subject. An adaptive hypermedia system should satisfy thre ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Employee Monitoring
Employee monitoring is the (often automated) surveillance of workers' activity. Organizations engage in employee monitoring for different reasons such as to track performance, to avoid legal liability, to protect trade secrets, and to address other security concerns. This practice may impact employee satisfaction due to its impact on the employee's privacy. Among organizations, the extent and methods of employee monitoring differ. Surveillance Methods A company can use its everyday electronic devices to monitor its employees almost continuously. Common methods include software monitoring, telephone tapping, video surveillance, email monitoring, and location monitoring. Software monitoring. Companies often use employee monitoring software to track what their employees are doing on their computers. Tracking data may include typing speed, mistakes, applications used, and what specific keys are pressed. Telephone tapping can be used to record employees' phone call details and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Money-laundering
Money laundering is the process of concealing the origin of money, obtained from illicit activities such as drug trafficking, corruption, embezzlement or gambling, by converting it into a legitimate source. It is a crime in many jurisdictions with varying definitions. It is usually a key operation of organized crime. In US law, money laundering is the practice of engaging in financial transactions to conceal the identity, source, or destination of illegally gained money. In UK law the common law definition is wider. The act is defined as "taking any action with property of any form which is either wholly or in part the proceeds of a crime that will disguise the fact that that property is the proceeds of a crime or obscure the beneficial ownership of said property". In the past, the term "money laundering" was applied only to financial transactions related to organized crime. Today its definition is often expanded by government and international regulators such as the US Offic ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fraud Prevention
In law, fraud is intentional deception to secure unfair or unlawful gain, or to deprive a victim of a legal right. Fraud can violate civil law (e.g., a fraud victim may sue the fraud perpetrator to avoid the fraud or recover monetary compensation) or criminal law (e.g., a fraud perpetrator may be prosecuted and imprisoned by governmental authorities), or it may cause no loss of money, property, or legal right but still be an element of another civil or criminal wrong. The purpose of fraud may be monetary gain or other benefits, for example by obtaining a passport, travel document, or driver's license, or mortgage fraud, where the perpetrator may attempt to qualify for a mortgage by way of false statements. Internal fraud, also known as "insider fraud", is fraud committed or attempted by someone within an organisation such as an employee. A hoax is a distinct concept that involves deliberate deception without the intention of gain or of materially damaging or depriving a vi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Machine-readable Data
Machine-readable data, or computer-readable data, is data in a format that can be processed by a computer. Machine-readable data must be structured data. Attempts to create machine-readable data occurred as early as the 1960s. At the same time that seminal developments in machine-reading and natural-language processing were releasing (like Weizenbaum's ELIZA), people were anticipating the success of machine-readable functionality and attempting to create machine-readable documents. One such example was musicologist Nancy B. Reich's creation of a machine-readable catalog of composer William Jay Sydeman's works in 1966. In the United States, the OPEN Government Data Act of 14 January 2019 defines machine-readable data as "data in a format that can be easily processed by a computer without human intervention while ensuring no semantic meaning is lost." The law directs U.S. federal agencies to publish public data in such a manner, ensuring that "any public data asset of the agenc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |