|
Pastry (DHT)
:''This article describes the Pastry Distributed Hash Table. For the food, see Pastry.'' Pastry is an overlay network and routing network for the implementation of a distributed hash table (DHT) similar to Chord. The key–value pairs are stored in a redundant peer-to-peer network of connected Internet hosts. The protocol is bootstrapped by supplying it with the IP address of a peer already in the network and from then on via the routing table which is dynamically built and repaired. It is claimed that because of its redundant and decentralized nature there is no single point of failure and any single node can leave the network at any time without warning and with little or no chance of data loss. The protocol is also capable of using a routing metric supplied by an outside program, such as ping or traceroute, to determine the best routes to store in its routing table. Overview Although the distributed hash table functionality of Pastry is almost identical to other DHTs, what se ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pastry
Pastry is baked food made with a dough of flour, water and shortening (solid fats, including butter or lard) that may be savoury or sweetened. Sweetened pastries are often described as '' bakers' confectionery''. The word "pastries" suggests many kinds of baked products made from ingredients such as flour, sugar, milk, butter, shortening, baking powder, and eggs. Small tarts and other sweet baked products are called pastries as a synecdoche. Common pastry dishes include pies, tarts, quiches, croissants, and pasties. The French word pâtisserie is also used in English (with or without the accent) for the same foods. Originally, the French word referred to anything, such as a meat pie, made in dough (''paste'', later ''pâte'') and not typically a luxurious or sweet product. This meaning still persisted in the nineteenth century, though by then the term more often referred to the sweet and often ornate confections implied today. Pastry can also refer to the pastry dough, from w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
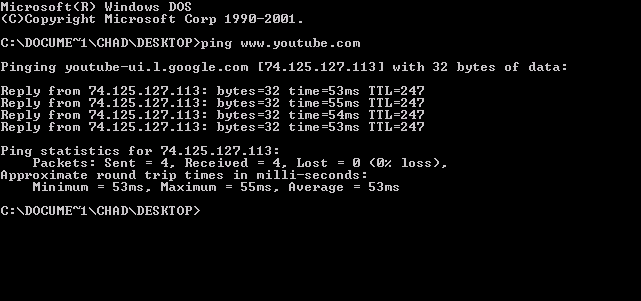
Traceroute
In computing, traceroute and tracert are computer network diagnostic commands for displaying possible routes (paths) and measuring transit delays of packets across an Internet Protocol (IP) network. The history of the route is recorded as the round-trip times of the packets received from each successive host (remote node) in the route (path); the sum of the mean times in each hop is a measure of the total time spent to establish the connection. Traceroute proceeds unless all (usually three) sent packets are lost more than twice; then the connection is lost and the route cannot be evaluated. Ping, on the other hand, only computes the final round-trip times from the destination point. For Internet Protocol Version 6 (IPv6) the tool sometimes has the name traceroute6 and tracert6. Implementations The command traceroute is available on many modern operating systems. On Unix-like systems such as FreeBSD, macOS, and Linux it is available as a command line tool. Traceroute is al ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tapestry (DHT)
Tapestry is a peer-to-peer overlay network which provides a distributed hash table, routing, and multicasting infrastructure for distributed applications.{{cite journal , last=Zhao , first=Ben Y. , last2=Huang , first2=Ling , last3=Stribling , first3=Jeremy , last4=Rhea , first4=Sean C. , last5=Joseph , first5=Anthony D. , last6=Kubiatowicz , first6=John D., date=2004 , title=Tapestry: A Resilient Global-scale Overlay for Service Deployment , url=http://pdos.csail.mit.edu/~strib/docs/tapestry/tapestry_jsac03.pdf , journal=IEEE Journal on Selected Areas in Communications , volume=22 , issue=1 , pages=41–53 , doi=10.1109/JSAC.2003.818784 , access-date=13 January 2015, citeseerx=10.1.1.71.2718 The Tapestry peer-to-peer system offers efficient, scalable, self-repairing, location-aware routing to nearby resources. Introduction The first generation of peer-to-peer applications, including Napster, Gnutella, had restricting limitations such as a central directory for Napster and scoped ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Kademlia
Kademlia is a distributed hash table for decentralized peer-to-peer computer networks designed by Petar Maymounkov and David Mazières in 2002. It specifies the structure of the network and the exchange of information through node lookups. Kademlia nodes communicate among themselves using UDP. A virtual or overlay network is formed by the participant nodes. Each node is identified by a number or ''node ID''. The ''node ID'' serves not only as identification, but the Kademlia algorithm uses the ''node ID'' to locate values (usually file hashes or keywords). In order to look up the value associated with a given key, the algorithm explores the network in several steps. Each step will find nodes that are closer to the key until the contacted node returns the value or no more closer nodes are found. This is very efficient: like many other s, Kademlia contacts only O(\log n) nodes during the search out of a total of n nodes in the system. Further advantages are found particularly in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Content Addressable Network
The content-addressable network (CAN) is a distributed, decentralized P2P infrastructure that provides hash table functionality on an Internet-like scale. CAN was one of the original four distributed hash table proposals, introduced concurrently with Chord, Pastry, and Tapestry. Overview Like other distributed hash tables, CAN is designed to be scalable, fault tolerant, and self-organizing. The architectural design is a virtual multi-dimensional Cartesian coordinate space, a type of overlay network, on a multi-torus. This n-dimensional coordinate space is a Virtuality, virtual logical address, completely independent of the physical location and physical connectivity of the nodes. Point (geometry), Points within the space are identified with coordinates. The entire coordinate space is dynamically partitioned among all the nodes in the system such that every node possesses at least one distinct zone within the overall space. Routing A CAN node maintains a routing table that holds ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Multicast
In computer networking, multicast is group communication where data transmission is addressed to a group of destination computers simultaneously. Multicast can be one-to-many or many-to-many distribution. Multicast should not be confused with physical layer point-to-multipoint communication. Group communication may either be application layer multicast or network-assisted multicast, where the latter makes it possible for the source to efficiently send to the group in a single transmission. Copies are automatically created in other network elements, such as routers, switches and cellular network base stations, but only to network segments that currently contain members of the group. Network assisted multicast may be implemented at the data link layer using one-to-many addressing and switching such as Ethernet multicast addressing, Asynchronous Transfer Mode (ATM), point-to-multipoint virtual circuits (P2MP) or InfiniBand multicast. Network-assisted multicast may also be impl ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Communications Protocol
A communication protocol is a system of rules that allows two or more entities of a communications system to transmit information via any kind of variation of a physical quantity. The protocol defines the rules, syntax, semantics and synchronization of communication and possible error recovery methods. Protocols may be implemented by hardware, software, or a combination of both. Communicating systems use well-defined formats for exchanging various messages. Each message has an exact meaning intended to elicit a response from a range of possible responses pre-determined for that particular situation. The specified behavior is typically independent of how it is to be implemented. Communication protocols have to be agreed upon by the parties involved. To reach an agreement, a protocol may be developed into a technical standard. A programming language describes the same for computations, so there is a close analogy between protocols and programming languages: ''protocols ar ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fault Tolerance
Fault tolerance is the property that enables a system to continue operating properly in the event of the failure of one or more faults within some of its components. If its operating quality decreases at all, the decrease is proportional to the severity of the failure, as compared to a naively designed system, in which even a small failure can cause total breakdown. Fault tolerance is particularly sought after in high-availability, mission-critical, or even life-critical systems. The ability of maintaining functionality when portions of a system break down is referred to as graceful degradation. A fault-tolerant design enables a system to continue its intended operation, possibly at a reduced level, rather than failing completely, when some part of the system fails. The term is most commonly used to describe computer systems designed to continue more or less fully operational with, perhaps, a reduction in throughput or an increase in response time in the event of some partial fa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Scalability
Scalability is the property of a system to handle a growing amount of work by adding resources to the system. In an economic context, a scalable business model implies that a company can increase sales given increased resources. For example, a package delivery system is scalable because more packages can be delivered by adding more delivery vehicles. However, if all packages had to first pass through a single warehouse for sorting, the system would not be as scalable, because one warehouse can handle only a limited number of packages. In computing, scalability is a characteristic of computers, networks, algorithms, networking protocols, programs and applications. An example is a search engine, which must support increasing numbers of users, and the number of topics it indexes. Webscale is a computer architectural approach that brings the capabilities of large-scale cloud computing companies into enterprise data centers. In mathematics, scalability mostly refers to closure u ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Distributed Hash Table
A distributed hash table (DHT) is a distributed system that provides a lookup service similar to a hash table: key–value pairs are stored in a DHT, and any participating node can efficiently retrieve the value associated with a given key. The main advantage of a DHT is that nodes can be added or removed with minimum work around re-distributing keys. ''Keys'' are unique identifiers which map to particular ''values'', which in turn can be anything from addresses, to documents, to arbitrary data. Responsibility for maintaining the mapping from keys to values is distributed among the nodes, in such a way that a change in the set of participants causes a minimal amount of disruption. This allows a DHT to scale to extremely large numbers of nodes and to handle continual node arrivals, departures, and failures. DHTs form an infrastructure that can be used to build more complex services, such as anycast, cooperative web caching, distributed file systems, domain name services, instant ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ping (networking Utility)
ping is a computer network administration software utility used to test the reachability of a host on an Internet Protocol (IP) network. It is available for virtually all operating systems that have networking capability, including most embedded network administration software. Ping measures the round-trip time for messages sent from the originating host to a destination computer that are echoed back to the source. The name comes from active sonar terminology that sends a pulse of sound and listens for the echo to detect objects under water. Ping operates by means of Internet Control Message Protocol (ICMP) packets. ''Pinging'' involves sending an ICMP echo request to the target host and waiting for an ICMP echo reply. The program reports errors, packet loss, and a statistical summary of the results, typically including the minimum, maximum, the mean round-trip times, and standard deviation of the mean. The command-line options of the ping utility and its output vary between t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Overlay Network
An overlay network is a computer network that is layered on top of another network. Structure Nodes in the overlay network can be thought of as being connected by virtual or logical links, each of which corresponds to a path, perhaps through many physical links, in the underlying network. For example, distributed systems such as peer-to-peer networks and client–server applications are overlay networks because their nodes run on top of the Internet. The Internet was originally built as an overlay upon the telephone network, while today (through the advent of VoIP), the telephone network is increasingly turning into an overlay network built on top of the Internet. Uses Enterprise networks Enterprise private networks were first overlaid on telecommunication networks such as Frame Relay and Asynchronous Transfer Mode packet switching infrastructures but migration from these (now legacy) infrastructures to IP based MPLS networks and virtual private networks started (2001~ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |