|
Policy Appliances
Policy appliances are technical control and logging mechanisms to enforce or reconcile policy rules (information use rules) and to ensure accountability in information systems. Policy appliances can be used to enforce policy or other systems constraints within and among trusted systems. The emerging global information society consists of many heterogeneous but interconnected systems that are governed or managed according to different policies, rules, or principles that meet local information management needs. For example, systems may be subject to different international, national or other political subdivision information disclosure or privacy laws; or different information management or security policies among or between government agencies, government and private sector information systems, or producers and consumers of proprietary information or intellectual property, etc. This interconnected network of systems (for which the Internet as we currently know it serves as t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Policy
Policy is a deliberate system of guidelines to guide decisions and achieve rational outcomes. A policy is a statement of intent and is implemented as a procedure or protocol. Policies are generally adopted by a governance body within an organization. Policies can assist in both ''subjective'' and ''objective'' decision making. Policies used in subjective decision-making usually assist senior management with decisions that must be based on the relative merits of a number of factors, and as a result, are often hard to test objectively, e.g. work–life balance policy... Moreover, Governments and other institutions have policies in the form of laws, regulations, procedures, administrative actions, incentives and voluntary practices. Frequently, resource allocations mirror policy decisions. Policy is a blueprint of the organizational activities which are repetitive/routine in nature. In contrast, policies to assist in objective decision-making are usually operational in nature an ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Process Management (Project Management)
In civil engineering and project management, process management is the management of "systematic series of activities directed towards causing an end result such that one or more inputs will be acted upon to create one or more outputs".PMI (2012), "Process" definition, in: ''A Guide to the Project Management Body of Knowledge'', 5th Ed. Process management offers project organizations a means of applying the same quality improvement and defect reduction techniques used in business and manufacturing processes by taking a process view of project activity; modeling discrete activities and high-level processes.Mitchell (2016). See Chapter 3 Process Management—Evolution and Definition. Overview The term ''process management'' usually refers to the management of engineering processes and project management processes where a ''process'' is a collection of related, structured tasks that produce a specific service or product to address a certain goal for a particular actor or set of act ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
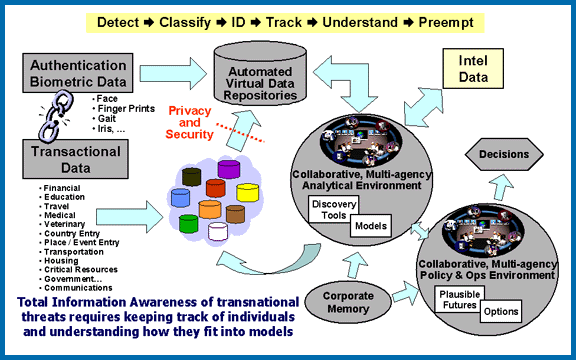
Information Awareness Office
The Information Awareness Office (IAO) was established by the United States Defense Advanced Research Projects Agency (DARPA) in January 2002 to bring together several DARPA projects focused on applying surveillance and information technology to track and monitor terrorists and other asymmetric threats to U.S. national security by achieving "Total Information Awareness" (TIA). It was achieved by creating enormous computer databases to gather and store the personal information of everyone in the United States, including personal e-mails, social networks, credit card records, phone calls, medical records, and numerous other sources, without any requirement for a search warrant. The information was then analyzed for suspicious activities, connections between individuals, and "threats".Total Information Awareness (TIA) ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Civil Liberties
Civil liberties are guarantees and freedoms that governments commit not to abridge, either by constitution, legislation, or judicial interpretation, without due process. Though the scope of the term differs between countries, civil liberties may include the Freedom of thought, freedom of conscience, Freedom of the press, freedom of press, freedom of religion, Freedom of speech, freedom of expression, freedom of assembly, the right to security and liberty, freedom of speech, the right to privacy, the right to Equality before the law, equal treatment under the law and due process, the right to a fair trial, and the right to life. Other civil liberties include the Right to property, right to own property, the Self-defense, right to defend oneself, and the right to bodily integrity. Within the distinctions between civil liberties and other types of liberty, distinctions exist between positive liberty/Negative and positive rights, positive rights and negative liberty/Negative and positi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Authentication
Authentication (from ''authentikos'', "real, genuine", from αὐθέντης ''authentes'', "author") is the act of proving an assertion, such as the identity of a computer system user. In contrast with identification, the act of indicating a person or thing's identity, authentication is the process of verifying that identity. It might involve validating personal identity documents, verifying the authenticity of a website with a digital certificate, determining the age of an artifact by carbon dating, or ensuring that a product or document is not counterfeit. Methods Authentication is relevant to multiple fields. In art, antiques, and anthropology, a common problem is verifying that a given artifact was produced by a certain person or in a certain place or period of history. In computer science, verifying a user's identity is often required to allow access to confidential data or systems. Authentication can be considered to be of three types: The first type of au ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Digital Rights Management
Digital rights management (DRM) is the management of legal access to digital content. Various tools or technological protection measures (TPM) such as access control technologies can restrict the use of proprietary hardware and copyrighted works. DRM technologies govern the use, modification, and distribution of copyrighted works (such as software and multimedia content), as well as systems that enforce these policies within devices. Laws in many countries criminalize the circumvention of DRM, communication about such circumvention, and the creation and distribution of tools used for such circumvention. Such laws are part of the United States' Digital Millennium Copyright Act (DMCA), and the European Union's Information Society Directive (the French DADVSI is an example of a member state of the European Union implementing the directive). DRM techniques include licensing agreements and encryption. The industry has expanded the usage of DRM to various hardware products, such as K ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Context Awareness
Context awareness refers, in information and communication technologies, to a capability to take into account the ''situation'' of ''entities'', which may be users or devices, but are not limited to those. ''Location'' is only the most obvious element of this ''situation''. Narrowly defined for mobile devices, context awareness does thus generalize location awareness. Whereas location may determine how certain processes around a contributing device operate, context may be applied more flexibly with mobile users, especially with users of smart phones. Context awareness originated as a term from ubiquitous computing or as so-called pervasive computing which sought to deal with linking changes in the environment with computer systems, which are otherwise static. The term has also been applied to business theory in relation to contextual application design and business process management issues. Qualities of context Various categorizations of context have been proposed in the past. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intelligent Agent
In artificial intelligence, an intelligent agent (IA) is anything which perceives its environment, takes actions autonomously in order to achieve goals, and may improve its performance with learning or may use knowledge. They may be simple or complex — a thermostat is considered an example of an intelligent agent, as is a human being, as is any system that meets the definition, such as a firm, a state, or a biome. Leading AI textbooks define "artificial intelligence" as the "study and design of intelligent agents", a definition that considers goal-directed behavior to be the essence of intelligence. Goal-directed agents are also described using a term borrowed from economics, "rational agent". An agent has an "objective function" that encapsulates all the IA's goals. Such an agent is designed to create and execute whatever plan will, upon completion, maximize the expected value of the objective function. For example, a reinforcement learning agent has a "reward function ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Middleware
Middleware is a type of computer software that provides services to software applications beyond those available from the operating system. It can be described as "software glue". Middleware makes it easier for software developers to implement communication and input/output, so they can focus on the specific purpose of their application. It gained popularity in the 1980s as a solution to the problem of how to link newer applications to older legacy systems, although the term had been in use since 1968. In distributed applications The term is most commonly used for software that enables communication and management of data in distributed applications. An IETF workshop in 2000 defined middleware as "those services found above the transport (i.e. over TCP/IP) layer set of services but below the application environment" (i.e. below application-level APIs). In this more specific sense ''middleware'' can be described as the dash ("-") in '' client-server'', or the ''-to-'' in ''peer ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
End-to-end Principle
The end-to-end principle is a design framework in computer networking. In networks designed according to this principle, guaranteeing certain application-specific features, such as reliability and security, requires that they reside in the communicating end nodes of the network. Intermediary nodes, such as gateways and routers, that exist to establish the network, may implement these to improve efficiency but cannot guarantee end-to-end correctness. The essence of what would later be called the end-to-end principle was contained in the work of Paul Baran and Donald Davies on packet-switched networks in the 1960s. Louis Pouzin pioneered the use of the end-to-end strategy in the CYCLADES network in the 1970s. The principle was first articulated explicitly in 1981 by Saltzer, Reed, and Clark. The meaning of the end-to-end principle has been continuously reinterpreted ever since its initial articulation. Also, noteworthy formulations of the end-to-end principle can be found befor ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Management Information Systems
A management information system (MIS) is an information system used for decision-making, and for the coordination, control, analysis, and visualization of information in an organization. The study of the management information systems involves people, processes and technology in an organizational context. In a corporate setting, the ultimate goal of using management information system is to increase the value and profits of the business. History While it can be contested that the history of management information system dates as far back as companies using ledgers to keep track of accounting, the modern history of MIS can be divided into five ''eras'' originally identified by Kenneth C. Laudon and Jane Laudon in their seminal textbook ''Management Information Systems.'' * First Era – Mainframe and minicomputer computing * Second Era – Personal computers * Third Era – Client/server networks * Fourth Era – Enterprise computing * Fifth Era – Cloud computing The ''fi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Access Control
In the fields of physical security and information security, access control (AC) is the selective restriction of access to a place or other resource, while access management describes the process. The act of ''accessing'' may mean consuming, entering, or using. Permission to access a resource is called ''authorization''. Locks and login credentials are two analogous mechanisms of access control. Physical security Geographical access control may be enforced by personnel (e.g. border guard, bouncer, ticket checker), or with a device such as a turnstile. There may be fences to avoid circumventing this access control. An alternative of access control in the strict sense (physically controlling access itself) is a system of checking authorized presence, see e.g. Ticket controller (transportation). A variant is exit control, e.g. of a shop (checkout) or a country. The term access control refers to the practice of restricting entrance to a property, a building, or a room to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |