|
One-time Password
A one-time password (OTP), also known as a one-time PIN, one-time authorization code (OTAC) or dynamic password, is a password that is valid for only one login session or transaction, on a computer system or other digital device. OTPs avoid several shortcomings that are associated with traditional (static) password-based authentication; a number of implementations also incorporate two-factor authentication by ensuring that the one-time password requires access to ''something a person has'' (such as a small keyring fob device with the OTP calculator built into it, or a smartcard or specific cellphone) as well as ''something a person knows'' (such as a PIN). OTP generation algorithms typically make use of pseudorandomness or randomness to generate a shared key or seed, and cryptographic hash functions, which can be used to derive a value but are hard to reverse and therefore difficult for an attacker to obtain the data that was used for the hash. This is necessary because otherwise ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
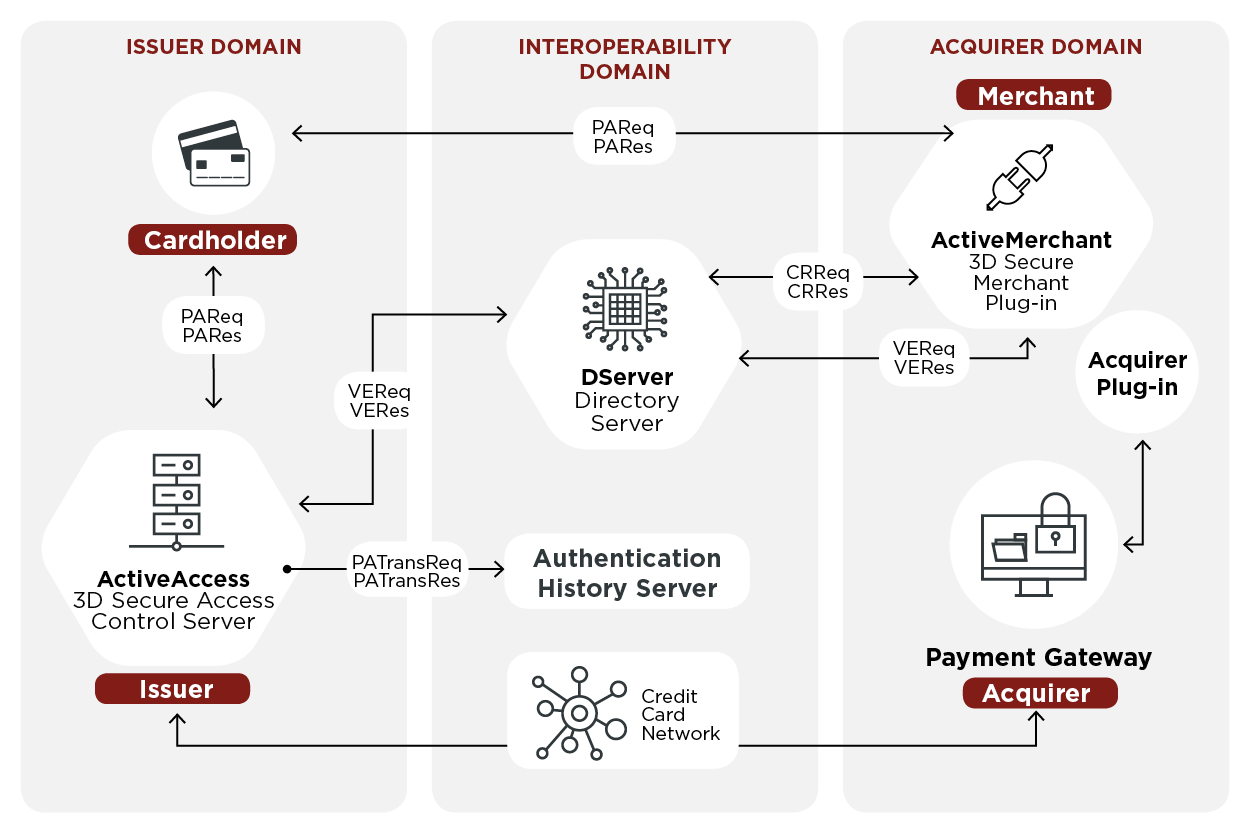
MasterCard SecureCode
3-D Secure is a protocol designed to be an additional security layer for online credit and debit card transactions. The name refers to the "three domains" which interact using the protocol: the merchant/acquirer domain, the issuer domain, and the interoperability domain. Originally developed in the autumn of 1999 by Celo Communications AB (later Gemplus, Gemalto and now Thales Group) for Visa Inc. in a project named "p42" ("p" from Pole vault as the project was a big challenge and "42" as the answer from the book ''The Hitchhiker's Guide to the Galaxy''). A new updated version was developed by Gemplus between 2000-2001. In 2001 Arcot Systems (now CA Technologies) and Visa Inc. with the intention of improving the security of Internet payments, and offered to customers under the Verified by Visa brand (later rebranded as Visa Secure). Services based on the protocol have also been adopted by Mastercard as SecureCode, by Discover as ProtectBuy, by JCB International as J/Secure, and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Freeware
Freeware is software, most often proprietary, that is distributed at no monetary cost to the end user. There is no agreed-upon set of rights, license, or EULA that defines ''freeware'' unambiguously; every publisher defines its own rules for the freeware it offers. For instance, modification, redistribution by third parties, and reverse engineering are permitted by some publishers but prohibited by others. Unlike with free and open-source software, which are also often distributed free of charge, the source code for freeware is typically not made available. Freeware may be intended to benefit its producer by, for example, encouraging sales of a more capable version, as in the freemium and shareware business models. History The term ''freeware'' was coined in 1982 by Andrew Fluegelman, who wanted to sell PC-Talk, the communications application he had created, outside of commercial distribution channels. Fluegelman distributed the program via a process now termed '' shareware''. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Text Messaging
Text messaging, or texting, is the act of composing and sending electronic messages, typically consisting of alphabetic and numeric characters, between two or more users of mobile devices, desktops/laptops, or another type of compatible computer. Text messages may be sent over a cellular network, or may also be sent via an Internet connection. The term originally referred to messages sent using the Short Message Service (SMS). It has grown beyond alphanumeric text to include multimedia messages using the Multimedia Messaging Service (MMS) containing digital images, videos, and sound content, as well as ideograms known as emoji ( happy faces, sad faces, and other icons), and instant messenger applications (usually the term is used when on mobile devices). Text messages are used for personal, family, business and social purposes. Governmental and non-governmental organizations use text messaging for communication between colleagues. In the 2010s, the sending of short informal mes ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
S/KEY
S/KEY is a one-time password system developed for authentication to Unix-like operating systems, especially from dumb terminals or untrusted public computers on which one does not want to type a long-term password. A user's real password is combined in an offline device with a short set of characters and a decrementing counter to form a single-use password. Because each password is only used once, they are useless to password sniffers. Because the short set of characters does not change until the counter reaches zero, it is possible to prepare a list of single-use passwords, in order, that can be carried by the user. Alternatively, the user can present the password, characters, and desired counter value to a local calculator to generate the appropriate one-time password that can then be transmitted over the network in the clear. The latter form is more common and practically amounts to challenge–response authentication. S/KEY is supported in Linux (via pluggable authentication mo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computationally Intractable
In theoretical computer science and mathematics, computational complexity theory focuses on classifying computational problems according to their resource usage, and relating these classes to each other. A computational problem is a task solved by a computer. A computation problem is solvable by mechanical application of mathematical steps, such as an algorithm. A problem is regarded as inherently difficult if its solution requires significant resources, whatever the algorithm used. The theory formalizes this intuition, by introducing mathematical models of computation to study these problems and quantifying their computational complexity, i.e., the amount of resources needed to solve them, such as time and storage. Other measures of complexity are also used, such as the amount of communication (used in communication complexity), the number of gates in a circuit (used in circuit complexity) and the number of processors (used in parallel computing). One of the roles of computati ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Inverse Function
In mathematics, the inverse function of a function (also called the inverse of ) is a function that undoes the operation of . The inverse of exists if and only if is bijective, and if it exists, is denoted by f^ . For a function f\colon X\to Y, its inverse f^\colon Y\to X admits an explicit description: it sends each element y\in Y to the unique element x\in X such that . As an example, consider the real-valued function of a real variable given by . One can think of as the function which multiplies its input by 5 then subtracts 7 from the result. To undo this, one adds 7 to the input, then divides the result by 5. Therefore, the inverse of is the function f^\colon \R\to\R defined by f^(y) = \frac . Definitions Let be a function whose domain is the set , and whose codomain is the set . Then is ''invertible'' if there exists a function from to such that g(f(x))=x for all x\in X and f(g(y))=y for all y\in Y. If is invertible, then there is exactly one function sat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hash Function
A hash function is any function that can be used to map data of arbitrary size to fixed-size values. The values returned by a hash function are called ''hash values'', ''hash codes'', ''digests'', or simply ''hashes''. The values are usually used to index a fixed-size table called a ''hash table''. Use of a hash function to index a hash table is called ''hashing'' or ''scatter storage addressing''. Hash functions and their associated hash tables are used in data storage and retrieval applications to access data in a small and nearly constant time per retrieval. They require an amount of storage space only fractionally greater than the total space required for the data or records themselves. Hashing is a computationally and storage space-efficient form of data access that avoids the non-constant access time of ordered and unordered lists and structured trees, and the often exponential storage requirements of direct access of state spaces of large or variable-length keys. Use of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Random Seed
A random seed (or seed state, or just seed) is a number (or vector) used to initialize a pseudorandom number generator. For a seed to be used in a pseudorandom number generator, it does not need to be random. Because of the nature of number generating algorithms, so long as the original seed is ignored, the rest of the values that the algorithm generates will follow probability distribution in a pseudorandom manner. A pseudorandom number generator's number sequence is completely determined by the seed: thus, if a pseudorandom number generator is reinitialized with the same seed, it will produce the same sequence of numbers. The choice of a good random seed is crucial in the field of computer security. When a secret encryption key is pseudorandomly generated, having the seed will allow one to obtain the key. High entropy is important for selecting good random seed data. If the same ''random'' seed is deliberately shared, it becomes a secret key, so two or more systems using mat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
One-way Function
In computer science, a one-way function is a function that is easy to compute on every input, but hard to invert given the image of a random input. Here, "easy" and "hard" are to be understood in the sense of computational complexity theory, specifically the theory of polynomial time problems. Not being one-to-one is not considered sufficient for a function to be called one-way (see Theoretical definition, below). The existence of such one-way functions is still an open conjecture. Their existence would prove that the complexity classes P and NP are not equal, thus resolving the foremost unsolved question of theoretical computer science.Oded Goldreich (2001). Foundations of Cryptography: Volume 1, Basic Tools,draft availablefrom author's site). Cambridge University Press. . (see als The converse is not known to be true, i.e. the existence of a proof that P≠NP would not directly imply the existence of one-way functions. In applied contexts, the terms "easy" and "hard" are usu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Leslie Lamport
Leslie B. Lamport (born February 7, 1941 in Brooklyn) is an American computer scientist and mathematician. Lamport is best known for his seminal work in distributed systems, and as the initial developer of the document preparation system LaTeX and the author of its first manual. Lamport was the winner of the 2013 Turing Award for imposing clear, well-defined coherence on the seemingly chaotic behavior of distributed computing systems, in which several autonomous computers communicate with each other by passing messages. He devised important algorithms and developed formal modeling and verification protocols that improve the quality of real distributed systems. These contributions have resulted in improved correctness, performance, and reliability of computer systems. Early life and education Lamport was born into a Jewish family in Brooklyn, New York, the son of Benjamin and Hannah Lamport (née Lasser). His father was an immigrant from Volkovisk in the Russian Empire (now Vawkav ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Password Manager
A password manager is a computer program that allows users to store and manage their passwords for local applications and online services. In many cases software used to manage passwords allow also generate strong passwords and fill forms. Password manager can be delivered as a one of or mixed of: computer application, mobile application, web browser extension, web based service, portable software for USB units. A password manager assists in generating and retrieving complex passwords, storing such passwords in an encrypted database, or calculating them on demand. Depending on the type of password manager used and on the functionality offered by its developers, the encrypted database is either stored locally on the user's device or stored remotely through an online cloud storage. Password managers typically require a user to generate and remember one "master" password to unlock and access information stored in their databases. Modern password managers increase security usi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |