|
Nord-10
Nord-10 was a medium-sized general-purpose 16-bit computing, 16-bit minicomputer designed for multilingual time-sharing applications and for real-time computing, real-time multi-program systems, produced by Norsk Data. It was introduced in 1973. The later follow up model, Nord-10/S, introduced in 1975, introduced CPU cache, paging, and other miscellaneous improvements. The CPU had a microprocessor, which was defined in the manual as a portmanteau of ''microcode processor'', not to be confused with the then nascent microprocessor. The CPU additionally contained instructions, operator communication, bootstrap loaders, and hardware test programs, that were implemented in a 1K read-only memory. The microprocessor also allowed for customer specified instructions to be built in. Nord-10 had a memory management system with hardware paging extending the memory size from 64 to 256K 16-bit words and two independent protecting systems, one acting on each page and one on the mode of instructi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Norsk Data
Norsk Data was a minicomputer manufacturer located in Oslo, Norway. Existing from 1967 to 1998, it had its most active period from the early 1970s to the late 1980s. At the company's peak in 1987, it was the second largest company in Norway and employed over 4,500 people. Throughout its history Norsk Data produced a long string of extremely innovative systems, with a disproportionately large number of world firsts. Some examples of this are the NORD-1, the first minicomputer to have memory paging as a standard option, and the first machine to have floating-point instructions standard, the NORD-5, the world's first 32-bit minicomputer (beating the VAX, often claimed the first, by 6 years). Historical overview The origins of Norsk Data go back to the development of digital computers at the Norwegian Defense Research Establishment at Kjeller, Norway, where several early computers had been designed, such as the Simulation for Automatic Machinery, SAM and the SAM 2, also known as the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Nord-100
The Nord-100 was a 16-bit minicomputer series made by Norsk Data, introduced in 1979. It shipped with the Sintran III operating system, and the architecture was based on, and backward compatible with, the Nord-10 line. The Nord-100 was originally named the Nord-10/M (''M'' for ''Micro'') as a bit sliced OEM processor. The board was laid out, finished, and tested when they realized that the central processing unit (CPU) was far faster than the Nord-10/S. The result was that all the marketing material for the new NORD-10/M was discarded, the board was rechristened the Nord-100, and extensively advertised as the successor of the Nord-10 line. Later, in an effort to internationalize their line, the machine was renamed ''ND-100''. Performance CPU The ND-100 line used a custom processor, and like the PDP-11 line, the CPU decided the name of the computer. *Nord-100/CE, Commercial Extended, with decimal arithmetic instructions (The decimal instruction set was later renamed CX) *ND- ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Punched Card
A punched card (also punch card or punched-card) is a piece of stiff paper that holds digital data represented by the presence or absence of holes in predefined positions. Punched cards were once common in data processing applications or to directly control automated machinery. Punched cards were widely used through much of the 20th century in the data processing industry, where specialized and increasingly complex unit record equipment, unit record machines, organized into semiautomatic data processing systems, used punched cards for data input, output, and storage. The IBM 12-row/80-column punched card format came to dominate the industry. Many early digital computers used punched cards as the primary medium for input of both computer programs and Data (computing), data. While punched cards are now obsolete as a storage medium, as of 2012, some voting machines still used punched cards to record votes. They also had a significant cultural impact. History The idea of contr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Bus
In computer architecture, a bus (shortened form of the Latin '' omnibus'', and historically also called data highway or databus) is a communication system that transfers data between components inside a computer, or between computers. This expression covers all related hardware components (wire, optical fiber, etc.) and software, including communication protocols. Early computer buses were parallel electrical wires with multiple hardware connections, but the term is now used for any physical arrangement that provides the same logical function as a parallel electrical busbar. Modern computer buses can use both parallel and bit serial connections, and can be wired in either a multidrop (electrical parallel) or daisy chain topology, or connected by switched hubs, as in the case of Universal Serial Bus (USB). Background and nomenclature Computer systems generally consist of three main parts: * The central processing unit (CPU) that processes data, * The memory that holds the p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Interrupt
In digital computers, an interrupt (sometimes referred to as a trap) is a request for the processor to ''interrupt'' currently executing code (when permitted), so that the event can be processed in a timely manner. If the request is accepted, the processor will suspend its current activities, save its state, and execute a function called an ''interrupt handler'' (or an ''interrupt service routine'', ISR) to deal with the event. This interruption is often temporary, allowing the software to resume normal activities after the interrupt handler finishes, although the interrupt could instead indicate a fatal error. Interrupts are commonly used by hardware devices to indicate electronic or physical state changes that require time-sensitive attention. Interrupts are also commonly used to implement computer multitasking, especially in real-time computing. Systems that use interrupts in these ways are said to be interrupt-driven. Types Interrupt signals may be issued in response to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ring (computer Security)
In computer science, hierarchical protection domains, often called protection rings, are mechanisms to protect data and functionality from faults (by improving fault tolerance) and malicious behavior (by providing computer security). Computer operating systems provide different levels of access to resources. A protection ring is one of two or more hierarchical ''levels'' or ''layers'' of privilege within the architecture of a computer system. This is generally hardware-enforced by some CPU architectures that provide different CPU modes at the hardware or microcode level. Rings are arranged in a hierarchy from most privileged (most trusted, usually numbered zero) to least privileged (least trusted, usually with the highest ring number). Ring 0 is the level with the most privileges and allows direct interaction with the physical hardware such as certain CPU functionality and chips on the motherboard. Special call gates between rings are provided to allow an outer ring to acces ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Physical Memory
Computer data storage is a technology consisting of computer components and recording media that are used to retain digital data. It is a core function and fundamental component of computers. The central processing unit (CPU) of a computer is what manipulates data by performing computations. In practice, almost all computers use a storage hierarchy, which puts fast but expensive and small storage options close to the CPU and slower but less expensive and larger options further away. Generally, the fast volatile technologies (which lose data when off power) are referred to as "memory", while slower persistent technologies are referred to as "storage". Even the first computer designs, Charles Babbage's Analytical Engine and Percy Ludgate's Analytical Machine, clearly distinguished between processing and memory (Babbage stored numbers as rotations of gears, while Ludgate stored numbers as displacements of rods in shuttles). This distinction was extended in the Von Neumann arch ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Physical Address
In computing, a physical address (also real address, or binary address), is a memory address that is represented in the form of a binary number on the address bus circuitry in order to enable the data bus to access a ''particular'' storage cell of main memory, or a register of memory-mapped I/O device. Use by central processing unit In a computer supporting virtual memory, the term ''physical address'' is used mostly to differentiate from a ''virtual address''. In particular, in computers utilizing a memory management unit (MMU) to translate memory addresses, the virtual and physical addresses refer to an address before and after translation performed by the MMU, respectively. Unaligned addressing Depending upon its underlying computer architecture, the performance of a computer may be hindered by ''unaligned'' access to memory. For example, a 16-bit computer with a 16-bit memory data bus, such as Intel 8086, generally has less overhead if the access is aligned to an even ad ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Virtual Address
In computing, a virtual address space (VAS) or address space is the set of ranges of virtual addresses that an operating system makes available to a process. The range of virtual addresses usually starts at a low address and can extend to the highest address allowed by the computer's instruction set architecture and supported by the operating system's pointer size implementation, which can be 4 bytes for 32-bit or 8 bytes for 64-bit OS versions. This provides several benefits, one of which is security through process isolation assuming each process is given a separate address space. Example :''In the following description, the terminology used will be particular to the Windows NT operating system, but the concepts are applicable to other virtual memory operating systems.'' When a new application on a 32-bit OS is executed, the process has a VAS: each one of the memory addresses (from 0 to 232 − 1) in that space can have a single byte as a value. Initially, none of them have ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
19-inch Rack
A 19-inch rack is a standardized frame or enclosure for mounting multiple electronic equipment modules. Each module has a front panel that is wide. The 19 inch dimension includes the edges or "ears" that protrude from each side of the equipment, allowing the module to be fastened to the rack frame with screws or bolts. Common uses include computer servers, telecommunications equipment and networking hardware, audiovisual production gear, and scientific equipment. Overview and history Equipment designed to be placed in a rack is typically described as rack-mount, rack-mount instrument, a rack-mounted system, a rack-mount chassis, subrack, rack cabinet, rack-mountable, or occasionally simply shelf. The height of the electronic modules is also standardized as multiples of or one rack unit or U (less commonly RU). The industry-standard rack cabinet is 42U tall; however, 45U racks are also common. The term ''relay rack'' appeared first in the world of telephony. By 1911, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
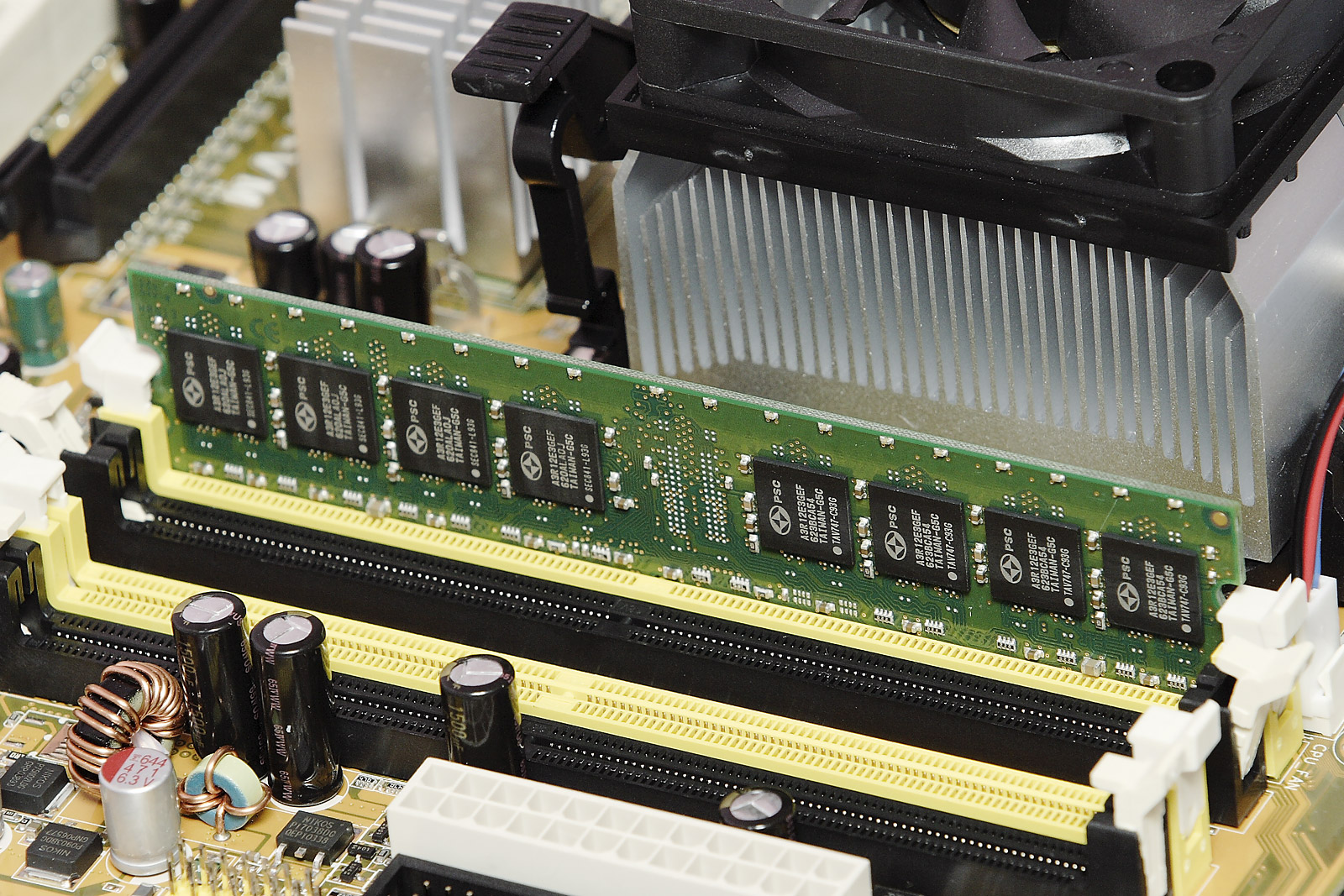
Random-access Memory
Random-access memory (RAM; ) is a form of computer memory that can be read and changed in any order, typically used to store working Data (computing), data and machine code. A Random access, random-access memory device allows data items to be read (computer), read or written in almost the same amount of time irrespective of the physical location of data inside the memory, in contrast with other direct-access data storage media (such as hard disks, CD-RWs, DVD-RWs and the older Magnetic tape data storage, magnetic tapes and drum memory), where the time required to read and write data items varies significantly depending on their physical locations on the recording medium, due to mechanical limitations such as media rotation speeds and arm movement. RAM contains multiplexer, multiplexing and demultiplexing circuitry, to connect the data lines to the addressed storage for reading or writing the entry. Usually more than one bit of storage is accessed by the same address, and RAM ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Byte
The byte is a unit of digital information that most commonly consists of eight bits. Historically, the byte was the number of bits used to encode a single character of text in a computer and for this reason it is the smallest addressable unit of memory in many computer architectures. To disambiguate arbitrarily sized bytes from the common 8-bit definition, network protocol documents such as The Internet Protocol () refer to an 8-bit byte as an octet. Those bits in an octet are usually counted with numbering from 0 to 7 or 7 to 0 depending on the bit endianness. The first bit is number 0, making the eighth bit number 7. The size of the byte has historically been hardware-dependent and no definitive standards existed that mandated the size. Sizes from 1 to 48 bits have been used. The six-bit character code was an often-used implementation in early encoding systems, and computers using six-bit and nine-bit bytes were common in the 1960s. These systems often had memory words ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |

.jpg)

.jpg)
