|
Neural Cryptography
Neural cryptography is a branch of cryptography dedicated to analyzing the application of stochastic algorithms, especially artificial neural network algorithms, for use in encryption and cryptanalysis. Definition Artificial neural networks are well known for their ability to selectively explore the solution space of a given problem. This feature finds a natural niche of application in the field of cryptanalysis. At the same time, neural networks offer a new approach to attack ciphering algorithms based on the principle that any function could be reproduced by a neural network, which is a powerful proven computational tool that can be used to find the inverse-function of any cryptographic algorithm. The ideas of mutual learning, self learning, and stochastic behavior of neural networks and similar algorithms can be used for different aspects of cryptography, like public-key cryptography, solving the key distribution problem using neural network mutual synchronization, hashing ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptography
Cryptography, or cryptology (from grc, , translit=kryptós "hidden, secret"; and ''graphein'', "to write", or ''-logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of adversarial behavior. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security ( data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, chip-based payment cards, digital currencies, computer passwords, and military communications. Cryptography prior to the modern age was effectively synonymo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Diffie–Hellman Key Exchange
Diffie–Hellman key exchangeSynonyms of Diffie–Hellman key exchange include: * Diffie–Hellman–Merkle key exchange * Diffie–Hellman key agreement * Diffie–Hellman key establishment * Diffie–Hellman key negotiation * Exponential key exchange * Diffie–Hellman protocol * Diffie–Hellman handshake is a mathematical method of securely exchanging cryptographic keys over a public channel and was one of the first public-key protocols as conceived by Ralph Merkle and named after Whitfield Diffie and Martin Hellman. DH is one of the earliest practical examples of public key exchange implemented within the field of cryptography. Published in 1976 by Diffie and Hellman, this is the earliest publicly known work that proposed the idea of a private key and a corresponding public key. Traditionally, secure encrypted communication between two parties required that they first exchange keys by some secure physical means, such as paper key lists transported by a trusted courier. The Di ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
University Of Würzburg
The Julius Maximilian University of Würzburg (also referred to as the University of Würzburg, in German ''Julius-Maximilians-Universität Würzburg'') is a public research university in Würzburg, Germany. The University of Würzburg is one of the oldest institutions of higher learning in Germany, having been founded in 1402. The university initially had a brief run and was closed in 1415. It was reopened in 1582 on the initiative of Julius Echter von Mespelbrunn. Today, the university is named for Julius Echter von Mespelbrunn and Maximilian Joseph. The University of Würzburg is part of the U15 group of research-intensive German universities. The university is also a member of the Coimbra Group. Name Its official name is Julius-Maximilians-Universität Würzburg (or "Julius-Maximilian University of Würzburg") but it is commonly referred to as the University of Würzburg. This name is taken from Julius Echter von Mespelbrunn, Prince-Bishop of Würzburg, who reestablishe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Shor's Algorithm
Shor's algorithm is a quantum algorithm, quantum computer algorithm for finding the prime factors of an integer. It was developed in 1994 by the American mathematician Peter Shor. On a quantum computer, to factor an integer N , Shor's algorithm runs in polynomial time, meaning the time taken is polynomial in \log N , the size of the integer given as input. Specifically, it takes quantum logic gate, quantum gates of order O \! \left((\log N)^ (\log \log N) (\log \log \log N) \right) using fast multiplication, or even O \! \left((\log N)^ (\log \log N) \right) utilizing the asymptotically fastest multiplication algorithm currently known due to Harvey and Van Der Hoven, thus demonstrating that the integer factorization problem can be efficiently solved on a quantum computer and is consequently in the complexity class BQP. This is almost exponentially faster than the most efficient known classical factoring algorithm, the ge ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Stochastic Neural Network
Artificial neural networks (ANNs), usually simply called neural networks (NNs) or neural nets, are computing systems inspired by the biological neural networks that constitute animal brains. An ANN is based on a collection of connected units or nodes called artificial neurons, which loosely model the neurons in a biological brain. Each connection, like the synapses in a biological brain, can transmit a signal to other neurons. An artificial neuron receives signals then processes them and can signal neurons connected to it. The "signal" at a connection is a real number, and the output of each neuron is computed by some non-linear function of the sum of its inputs. The connections are called ''edges''. Neurons and edges typically have a ''weight'' that adjusts as learning proceeds. The weight increases or decreases the strength of the signal at a connection. Neurons may have a threshold such that a signal is sent only if the aggregate signal crosses that threshold. Typically, n ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Neural Network
A neural network is a network or circuit of biological neurons, or, in a modern sense, an artificial neural network, composed of artificial neurons or nodes. Thus, a neural network is either a biological neural network, made up of biological neurons, or an artificial neural network, used for solving artificial intelligence (AI) problems. The connections of the biological neuron are modeled in artificial neural networks as weights between nodes. A positive weight reflects an excitatory connection, while negative values mean inhibitory connections. All inputs are modified by a weight and summed. This activity is referred to as a linear combination. Finally, an activation function controls the amplitude of the output. For example, an acceptable range of output is usually between 0 and 1, or it could be −1 and 1. These artificial networks may be used for predictive modeling, adaptive control and applications where they can be trained via a dataset. Self-learning resulting from e ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Quantum Computer
Quantum computing is a type of computation whose operations can harness the phenomena of quantum mechanics, such as superposition, interference, and entanglement. Devices that perform quantum computations are known as quantum computers. Though current quantum computers may be too small to outperform usual (classical) computers for practical applications, larger realizations are believed to be capable of solving certain computational problems, such as integer factorization (which underlies RSA encryption), substantially faster than classical computers. The study of quantum computing is a subfield of quantum information science. There are several models of quantum computation with the most widely used being quantum circuits. Other models include the quantum Turing machine, quantum annealing, and adiabatic quantum computation. Most models are based on the quantum bit, or "qubit", which is somewhat analogous to the bit in classical computation. A qubit can be in a 1 or 0 quantum ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Lecture Notes In Computer Science
''Lecture Notes in Computer Science'' is a series of computer science books published by Springer Science+Business Media since 1973. Overview The series contains proceedings, post-proceedings, monographs, and Festschrifts. In addition, tutorials, state-of-the-art surveys, and "hot topics" are increasingly being included. The series is indexed by DBLP. See also *''Monographiae Biologicae'', another monograph series published by Springer Science+Business Media *''Lecture Notes in Physics'' *''Lecture Notes in Mathematics'' *''Electronic Workshops in Computing ''Electronic Workshops in Computing'' (eWiC) is a publication series by the British Computer Society. The series provides free online access for conferences and workshops in the area of computing. For example, the EVA London Conference proceeding ...'', published by the British Computer Society References External links * Publications established in 1973 Computer science books Series of non-fiction books Springer ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Function (mathematics)
In mathematics, a function from a set to a set assigns to each element of exactly one element of .; the words map, mapping, transformation, correspondence, and operator are often used synonymously. The set is called the domain of the function and the set is called the codomain of the function.Codomain ''Encyclopedia of Mathematics'Codomain. ''Encyclopedia of Mathematics''/ref> The earliest known approach to the notion of function can be traced back to works of Persian mathematicians Al-Biruni and Sharaf al-Din al-Tusi. Functions were originally the idealization of how a varying quantity depends on another quantity. For example, the position of a planet is a ''function'' of time. Historically, the concept was elaborated with the infinitesimal calculus at the end of the 17th century, and, until the 19th century, the functions that were considered were differentiable (that is, they had a high degree of regularity). The concept of a function was formalized at the end of the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Feedforward Neural Network
A feedforward neural network (FNN) is an artificial neural network wherein connections between the nodes do ''not'' form a cycle. As such, it is different from its descendant: recurrent neural networks. The feedforward neural network was the first and simplest type of artificial neural network devised. In this network, the information moves in only one direction—forward—from the input nodes, through the hidden nodes (if any) and to the output nodes. There are no cycles or loops in the network. Single-layer perceptron The simplest kind of neural network is a ''single-layer perceptron'' network, which consists of a single layer of output nodes; the inputs are fed directly to the outputs via a series of weights. The sum of the products of the weights and the inputs is calculated in each node, and if the value is above some threshold (typically 0) the neuron fires and takes the activated value (typically 1); otherwise it takes the deactivated value (typically -1). Ne ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
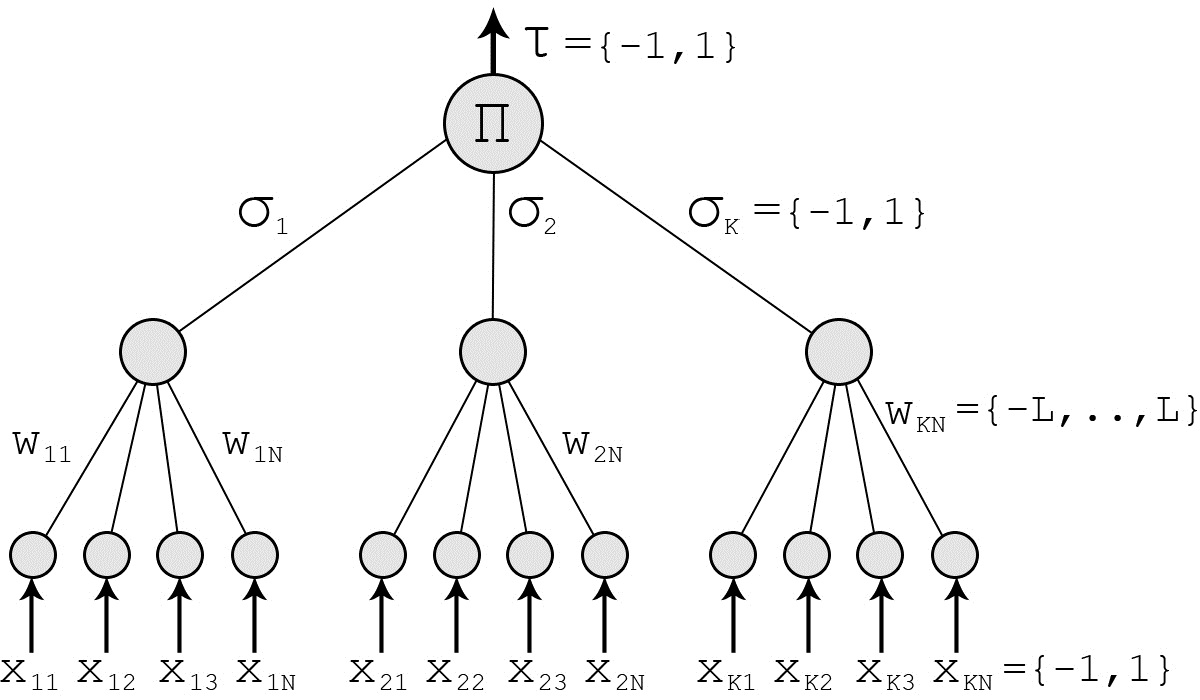
Tree Parity Machine
In botany, a tree is a perennial plant with an elongated stem, or trunk, usually supporting branches and leaves. In some usages, the definition of a tree may be narrower, including only woody plants with secondary growth, plants that are usable as lumber or plants above a specified height. In wider definitions, the taller palms, tree ferns, bananas, and bamboos are also trees. Trees are not a taxonomic group but include a variety of plant species that have independently evolved a trunk and branches as a way to tower above other plants to compete for sunlight. The majority of tree species are angiosperms or hardwoods; of the rest, many are gymnosperms or softwoods. Trees tend to be long-lived, some reaching several thousand years old. Trees have been in existence for 370 million years. It is estimated that there are some three trillion mature trees in the world. A tree typically has many secondary branches supported clear of the ground by the trunk. This trunk typically c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Chaos Communications
Chaos communications is an application of chaos theory which is aimed to provide security in the transmission of information performed through telecommunications technologies. By secure communications, one has to understand that the contents of the message transmitted are inaccessible to possible eavesdroppers. In chaos communications security (i.e., privacy) is based on the complex dynamic behaviors provided by chaotic systems. Some properties of chaotic dynamics, such as complex behaviour, noise-like dynamics ( pseudorandom noise) and spread spectrum, are used to encode data. On the other hand, chaos being a deterministic phenomenon, it is possible to decode data using this determinism. In practice, implementations of chaos communications devices resort to one of two chaotic phenomena: synchronization of chaos, or control of chaos. To implement chaos communications using such properties of chaos, two chaotic oscillators are required as a transmitter (or master) and receiver (o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |

.jpg)
