|
Netsukuku
Netsukuku is an experimental peer-to-peer routing system, developed by thFreakNet MediaLabin 2005, created to build up a distributed network, anonymous and censorship-free, fully independent but not necessarily separated from the Internet, without the support of any server, ISP and no central authority. Netsukuku is designed to handle up to 2128 nodes without any servers or central systems, with minimal CPU and memory resources. This mesh network can be built using existing network infrastructure components such as Wi-Fi. The project has been in slow development since 2005, never abandoning a beta state. It has also never been tested on large scale. Operation As of December 2011, the latest theoretical work on Netsukuku could be found in the author's master thesiScalable Mesh Networks and the Address Space Balancing problem The following description takes into account only the basic concepts of the theory. Netsukuku uses a custom routing protocol called QSPN (Quantum Shortes ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Netsukuku
Netsukuku is an experimental peer-to-peer routing system, developed by thFreakNet MediaLabin 2005, created to build up a distributed network, anonymous and censorship-free, fully independent but not necessarily separated from the Internet, without the support of any server, ISP and no central authority. Netsukuku is designed to handle up to 2128 nodes without any servers or central systems, with minimal CPU and memory resources. This mesh network can be built using existing network infrastructure components such as Wi-Fi. The project has been in slow development since 2005, never abandoning a beta state. It has also never been tested on large scale. Operation As of December 2011, the latest theoretical work on Netsukuku could be found in the author's master thesiScalable Mesh Networks and the Address Space Balancing problem The following description takes into account only the basic concepts of the theory. Netsukuku uses a custom routing protocol called QSPN (Quantum Shortes ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anonymous P2P
An anonymous P2P communication system is a peer-to-peer distributed application in which the nodes, which are used to share resources, or participants are anonymous or pseudonymous. Anonymity of participants is usually achieved by special routing overlay networks that hide the physical location of each node from other participants. Interest in anonymous P2P systems has increased in recent years for many reasons, ranging from the desire to share files without revealing one's network identity and risking litigationElectronic Frontier Foundation (2005)RIAA v. The People: Five Years Later. Retrieved March 5, 2008. to distrust in governments, concerns over mass surveillance and data retention, and lawsuits against bloggers. Motivation for anonymity There are many reasons to use anonymous P2P technology; most of them are generic to all forms of online anonymity. P2P users who desire anonymity usually do so as they do not wish to be identified as a publisher (sender), or reader (r ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Peer-to-peer
Peer-to-peer (P2P) computing or networking is a distributed application architecture that partitions tasks or workloads between peers. Peers are equally privileged, equipotent participants in the network. They are said to form a peer-to-peer network of nodes. Peers make a portion of their resources, such as processing power, disk storage or network bandwidth, directly available to other network participants, without the need for central coordination by servers or stable hosts. Peers are both suppliers and consumers of resources, in contrast to the traditional client–server model in which the consumption and supply of resources are divided. While P2P systems had previously been used in many application domains, the architecture was popularized by the file sharing system Napster, originally released in 1999. The concept has inspired new structures and philosophies in many areas of human interaction. In such social contexts, peer-to-peer as a meme refers to the egalitarian so ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wireless Community Network
Wireless community networks (WCNs) or wireless community projects or simply community networks, are non-centralized, self-managed and collaborative networks organized in a grassroots fashion by communities, NGO's and cooperatives in order to provide a viable alternative to municipal wireless networks for consumers. Many of these organizations set up wireless mesh networks which rely primarily on sharing of unmetered residential and business DSL and cable Internet. This sort of usage might be non-compliant with the terms of service of local internet service provider (ISPs) that deliver their service via the consumer phone and cable duopoly. Wireless community networks sometimes advocate complete freedom from censorship, and this position may be at odds with the acceptable use policies of some commercial services used. Some ISPs do allow sharing or reselling of bandwidth. The First Latin American Summit of Community Networks, held in Argentina in 2018, presented the following def ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Freifunk
Freifunk (German for: "free radio") is a non-commercial open grassroots initiative to support free computer networks in the German region. Freifunk is part of the international movement for a wireless community network. The initiative counts about 400 local communities with over 41,000 access points. Among them, Münster, Aachen, Munich, Hanover, Stuttgart, and Uelzen are the biggest communities, with more than 1,000 access points each. Aim The main goals of Freifunk are to build a large-scale free wireless Wi-Fi network that is decentralized, owned by those who run it and to support local communication. The initiative is based on the Picopeering Agreement. In this agreement, participants agree upon a network that is free from discrimination, in the sense of net neutrality. Similar grassroots initiatives in Austria and in Switzerland are FunkFeuer and Openwireless. Technology Like many other free community-driven networks, Freifunk uses mesh technology to bring up ad hoc ne ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mesh Network
A mesh network is a local area network topology in which the infrastructure nodes (i.e. bridges, switches, and other infrastructure devices) connect directly, dynamically and non-hierarchically to as many other nodes as possible and cooperate with one another to efficiently route data to and from clients. This lack of dependency on one node allows for every node to participate in the relay of information. Mesh networks dynamically self-organize and self-configure, which can reduce installation overhead. The ability to self-configure enables dynamic distribution of workloads, particularly in the event a few nodes should fail. This in turn contributes to fault-tolerance and reduced maintenance costs. Mesh topology may be contrasted with conventional star/tree local network topologies in which the bridges/switches are directly linked to only a small subset of other bridges/switches, and the links between these infrastructure neighbours are hierarchical. While star-and-tree topologi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
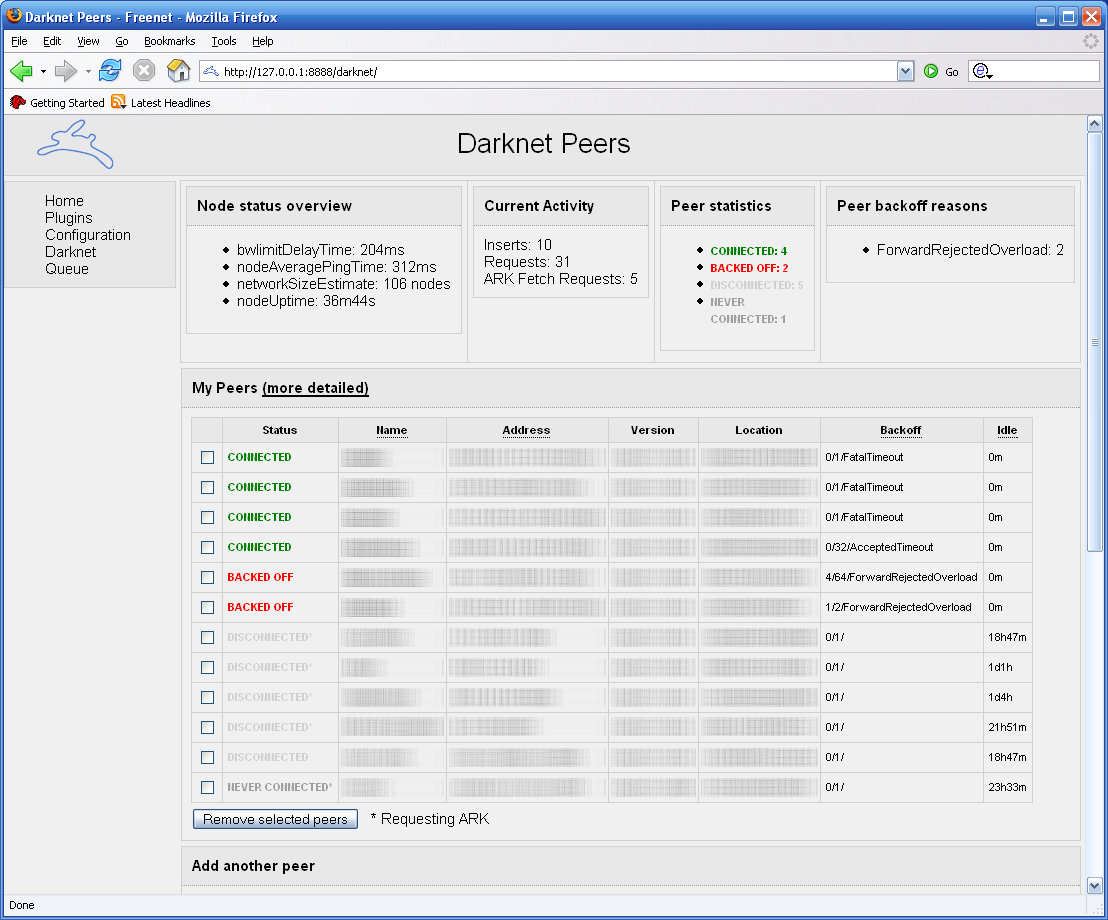
Freenet
Freenet is a peer-to-peer platform for censorship-resistant, anonymous communication. It uses a decentralized distributed data store to keep and deliver information, and has a suite of free software for publishing and communicating on the Web without fear of censorship.What is Freenet? , ''Freenet: The Free network official website''.Taylor, Ian J. ''From P2P to Web Services and Grids: Peers in a Client/Server World''. London: Springer, 2005. Both Freenet and some of its associated tools were originally designed by Ian Clarke, who defined Freenet's goal as providing |
Anonymity Networks
Anonymity describes situations where the acting person's identity is unknown. Some writers have argued that namelessness, though technically correct, does not capture what is more centrally at stake in contexts of anonymity. The important idea here is that a person be non-identifiable, unreachable, or untrackable. Anonymity is seen as a technique, or a way of realizing, a certain other values, such as privacy, or liberty. Over the past few years, anonymity tools used on the dark web by criminals and malicious users have drastically altered the ability of law enforcement to use conventional surveillance techniques. An important example for anonymity being not only protected, but enforced by law is the vote in free elections. In many other situations (like conversation between strangers, buying some product or service in a shop), anonymity is traditionally accepted as natural. There are also various situations in which a person might choose to withhold their identity. Acts of cha ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Server (computing)
In computing, a server is a piece of computer hardware or software (computer program) that provides functionality for other programs or devices, called " clients". This architecture is called the client–server model. Servers can provide various functionalities, often called "services", such as sharing data or resources among multiple clients, or performing computation for a client. A single server can serve multiple clients, and a single client can use multiple servers. A client process may run on the same device or may connect over a network to a server on a different device. Typical servers are database servers, file servers, mail servers, print servers, web servers, game servers, and application servers. Client–server systems are usually most frequently implemented by (and often identified with) the request–response model: a client sends a request to the server, which performs some action and sends a response back to the client, typically with a result or acknowledg ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Service Provider
An Internet service provider (ISP) is an organization that provides services for accessing, using, or participating in the Internet. ISPs can be organized in various forms, such as commercial, community-owned, non-profit, or otherwise privately owned. Internet services typically provided by ISPs can include Internet access, Internet transit, domain name registration, web hosting, Usenet service, and colocation. An ISP typically serves as the access point or the gateway that provides a user access to everything available on the Internet. Such a network can also be called as an eyeball network. History The Internet (originally ARPAnet) was developed as a network between government research laboratories and participating departments of universities. Other companies and organizations joined by direct connection to the backbone, or by arrangements through other connected companies, sometimes using dialup tools such as UUCP. By the late 1980s, a process was set in place towa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tor (anonymity Network)
Tor, short for The Onion Router, is free and open-source software for enabling anonymous communication. It directs Internet traffic through a free, worldwide, volunteer overlay network, consisting of more than seven thousand relays, to conceal a user's location and usage from anyone performing network surveillance or traffic analysis. Using Tor makes it more difficult to trace a user's Internet activity. Tor's intended use is to protect the personal privacy of its users, as well as their freedom and ability to communicate confidentially through IP address anonymity using Tor exit nodes. History The core principle of Tor, onion routing, was developed in the mid-1990s by United States Naval Research Laboratory employees, mathematician Paul Syverson, and computer scientists Michael G. Reed and David Goldschlag, to protect American intelligence communications online. Onion routing is implemented by means of encryption in the application layer of the communication protocol stack ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
I2P
The Invisible Internet Project (I2P) is an anonymous network layer (implemented as a mix network) that allows for Internet censorship circumvention, censorship-resistant, peer-to-peer communication. Anonymous connections are achieved by Encryption, encrypting the user's traffic (by using end-to-end encryption), and sending it through a volunteer-run network of roughly 55,000 computers distributed around the world. Given the high number of possible paths the traffic can transit, a third party watching a full connection is unlikely. The software that Implementation, implements this layer is called an "I2P Router (computing), router", and a computer running I2P is called an "I2P Node (networking), node". I2P is Free software, free and Open-source software, open sourced, and is published under multiple software license, licenses. Technical design I2P is Development stage#Beta, beta software since 2003, when it started as a fork of Freenet. The software's developers emphasize ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |