|
National Security Agency Academic Publications
The United States' National Security Agency (NSA), an intelligence agency of the federal government, publishes many documents on the history and technology of cryptology, cryptography, and cryptanalysis through various publications. * ''Cryptolog'' is published monthly by PI, Techniques and Standards, for the Personnel of Operations". Declassified issues are available online. * The ''Cryptologic Almanac'' is a cryptology academic journal published internally by the NSA. It publishes short vignettes about NSA or NSA-related topics. A selection of articles published are available to the public online. * ''Cryptologic Quarterly'' was the combined result of the merger of ''NSA Technical Journal'' and ''Cryptologic Spectrum'' in 1981. It expanded its coverage to cover a larger segment of NSA readership. * ''Cryptologic Spectrum'' was a cryptology journal published internally by the NSA. It was established in 1969, until consolidation with the ''NSA Technical Journal'' in 1981. A selecti ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
United States
The United States of America (U.S.A. or USA), commonly known as the United States (U.S. or US) or America, is a country primarily located in North America. It consists of 50 states, a federal district, five major unincorporated territories, nine Minor Outlying Islands, and 326 Indian reservations. The United States is also in free association with three Pacific Island sovereign states: the Federated States of Micronesia, the Marshall Islands, and the Republic of Palau. It is the world's third-largest country by both land and total area. It shares land borders with Canada to its north and with Mexico to its south and has maritime borders with the Bahamas, Cuba, Russia, and other nations. With a population of over 333 million, it is the most populous country in the Americas and the third most populous in the world. The national capital of the United States is Washington, D.C. and its most populous city and principal financial center is New York City. Paleo-Americ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
National Security Agency
The National Security Agency (NSA) is a national-level intelligence agency of the United States Department of Defense, under the authority of the Director of National Intelligence (DNI). The NSA is responsible for global monitoring, collection, and processing of information and data for foreign and domestic intelligence and counterintelligence purposes, specializing in a discipline known as signals intelligence (SIGINT). The NSA is also tasked with the protection of U.S. communications networks and information systems. The NSA relies on a variety of measures to accomplish its mission, the majority of which are clandestine. The existence of the NSA was not revealed until 1975. The NSA has roughly 32,000 employees. Originating as a unit to decipher coded communications in World War II, it was officially formed as the NSA by President Harry S. Truman in 1952. Between then and the end of the Cold War, it became the largest of the U.S. intelligence organizations in terms of pers ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
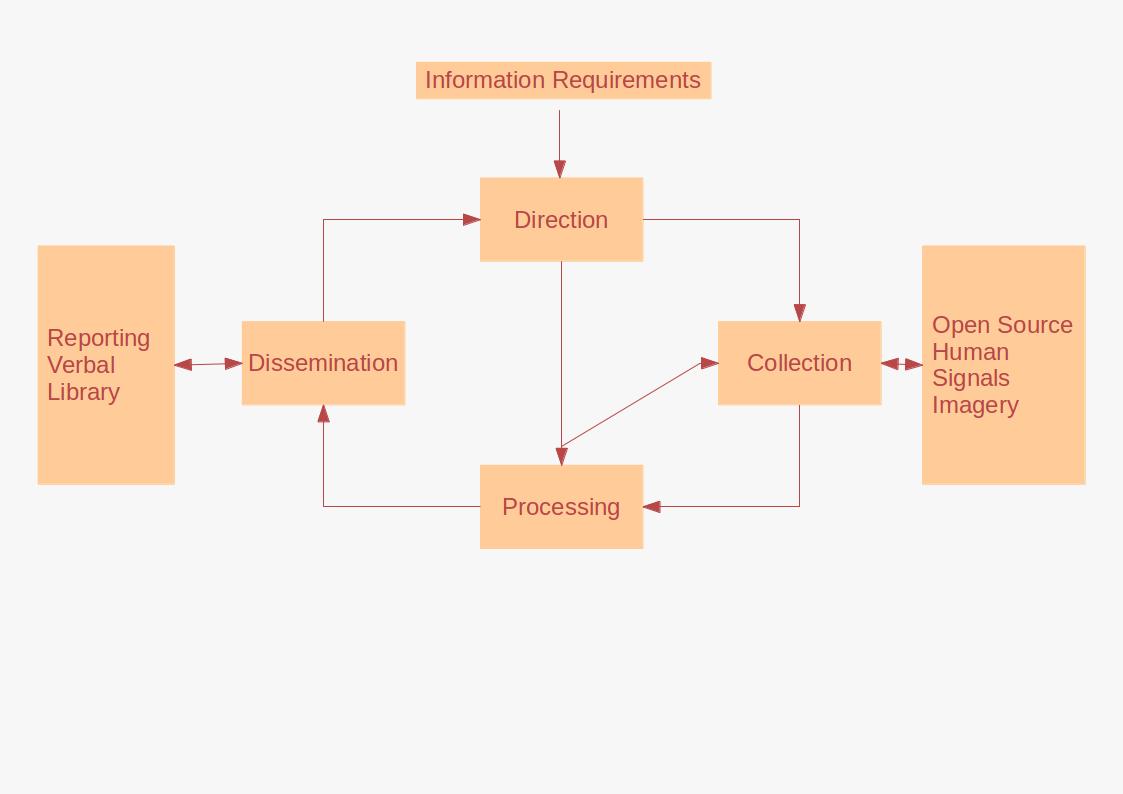
Intelligence (information Gathering)
Intelligence assessment, or simply intel, is the development of behavior forecasts or recommended courses of action to the leadership of an organisation, based on wide ranges of available overt and covert information (intelligence). Assessments develop in response to leadership declaration requirements to inform decision-making. Assessment may be executed on behalf of a state, military or commercial organisation with ranges of information sources available to each. An intelligence assessment reviews available information and previous assessments for relevance and currency. Where there requires additional information, the analyst may direct some collection. Intelligence studies is the academic field concerning intelligence assessment, especially relating to international relations and military science. Process Intelligence assessment is based on a customer requirement or need, which may be a standing requirement or tailored to a specific circumstance or a Request for Inform ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Federal Government Of The United States
The federal government of the United States (U.S. federal government or U.S. government) is the national government of the United States, a federal republic located primarily in North America, composed of 50 states, a city within a federal district (the city of Washington in the District of Columbia, where most of the federal government is based), five major self-governing territories and several island possessions. The federal government, sometimes simply referred to as Washington, is composed of three distinct branches: legislative, executive, and judicial, whose powers are vested by the U.S. Constitution in the Congress, the president and the federal courts, respectively. The powers and duties of these branches are further defined by acts of Congress, including the creation of executive departments and courts inferior to the Supreme Court. Naming The full name of the republic is "United States of America". No other name appears in the Constitution, and this i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptology
Cryptography, or cryptology (from grc, , translit=kryptós "hidden, secret"; and ''graphein'', "to write", or '' -logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of adversarial behavior. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security ( data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, chip-based payment cards, digital currencies, computer passwords, and military communications. Cryptography prior to the modern age was effectively synonymous wit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptography
Cryptography, or cryptology (from grc, , translit=kryptós "hidden, secret"; and ''graphein'', "to write", or ''-logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of adversarial behavior. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security ( data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, chip-based payment cards, digital currencies, computer passwords, and military communications. Cryptography prior to the modern age was effectively synonymo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptanalysis
Cryptanalysis (from the Greek ''kryptós'', "hidden", and ''analýein'', "to analyze") refers to the process of analyzing information systems in order to understand hidden aspects of the systems. Cryptanalysis is used to breach cryptographic security systems and gain access to the contents of encrypted messages, even if the cryptographic key is unknown. In addition to mathematical analysis of cryptographic algorithms, cryptanalysis includes the study of side-channel attacks that do not target weaknesses in the cryptographic algorithms themselves, but instead exploit weaknesses in their implementation. Even though the goal has been the same, the methods and techniques of cryptanalysis have changed drastically through the history of cryptography, adapting to increasing cryptographic complexity, ranging from the pen-and-paper methods of the past, through machines like the British Bombes and Colossus computers at Bletchley Park in World War II, to the mathematically advanced comput ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Academic Journal
An academic journal or scholarly journal is a periodical publication in which scholarship relating to a particular academic discipline is published. Academic journals serve as permanent and transparent forums for the presentation, scrutiny, and discussion of research. They nearly-universally require peer-review or other scrutiny from contemporaries competent and established in their respective fields. Content typically takes the form of articles presenting original research, review articles, or book reviews. The purpose of an academic journal, according to Henry Oldenburg (the first editor of ''Philosophical Transactions of the Royal Society''), is to give researchers a venue to "impart their knowledge to one another, and contribute what they can to the Grand design of improving natural knowledge, and perfecting all Philosophical Arts, and Sciences." The term ''academic journal'' applies to scholarly publications in all fields; this article discusses the aspects common to all ac ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Classified Information In The United States
The United States government classification system is established under Executive Order 13526, the latest in a long series of executive orders on the topic beginning in 1951. Issued by President Barack Obama in 2009, Executive Order 13526 replaced earlier executive orders on the topic and modified the regulations codified to 32 C.F.R. 2001. It lays out the system of classification, declassification, and handling of national security information generated by the U.S. government and its employees and contractors, as well as information received from other governments. The desired degree of secrecy about such information is known as its sensitivity. Sensitivity is based upon a calculation of the damage to national security that the release of the information would cause. The United States has three levels of classification: Confidential, Secret, and Top Secret. Each level of classification indicates an increasing degree of sensitivity. Thus, if one holds a Top Secret security cle ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Freedom Of Information Act (United States)
The Freedom of Information Act (FOIA), , is the U.S. federal freedom of information law that requires the full or partial disclosure of previously unreleased or uncirculated information and documents controlled by the United States government, state, or other public authority upon request. The act defines agency records subject to disclosure, outlines mandatory disclosure procedures, and includes nine exemptions that define categories of information not subject to disclosure. The act was intended to make U.S. government agencies' functions more transparent so that the American public could more easily identify problems in government functioning and put pressure on Congress, agency officials, and the president to address them. The FOIA has been changed repeatedly by both the legislative and executive branches. Apart from the U.S. federal government's Freedom of Information Act, the U.S. states have their own varying freedom of information laws. The Freedom of Information Act is c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ralph J
Ralph (pronounced ; or ,) is a male given name of English, Scottish and Irish origin, derived from the Old English ''Rædwulf'' and Radulf, cognate with the Old Norse ''Raðulfr'' (''rað'' "counsel" and ''ulfr'' "wolf"). The most common forms are: * Ralph, the common variant form in English, which takes either of the given pronunciations. * Rafe, variant form which is less common; this spelling is always pronounced , as are all other English spellings without "l". * Raife, a very rare variant. * Raif, a very rare variant. Raif Rackstraw from H.M.S. Pinafore * Ralf, the traditional variant form in Dutch, German, Swedish, and Polish. * Ralfs, the traditional variant form in Latvian. * Raoul, the traditional variant form in French. * Raúl, the traditional variant form in Spanish. * Raul, the traditional variant form in Portuguese and Italian. * Raül, the traditional variant form in Catalan. * Rádhulbh, the traditional variant form in Irish. Given name Middle Ages * Ralp ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |