|
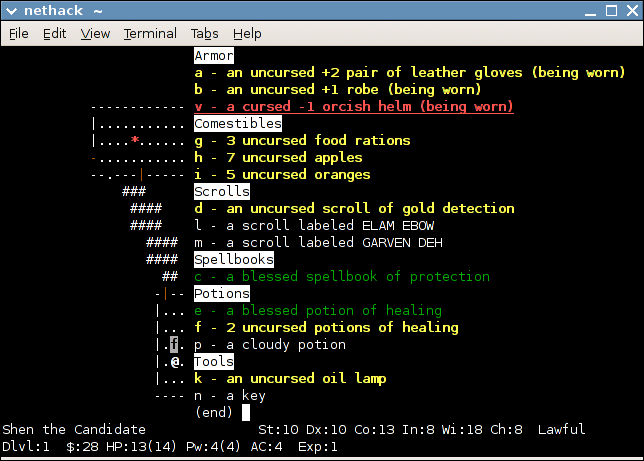
NetHack
''NetHack'' is an open source single-player roguelike video game, first released in 1987 and maintained by the NetHack DevTeam. The game is a fork of the 1982 game ''Hack'', itself inspired by the 1980 game '' Rogue''. The player takes the role as one of several pre-defined character classes to descend through multiple dungeon floors, fighting monsters and collecting treasure, to recover the "Amulet of Yendor" at the lowest floor and then escape. As an exemplar of the traditional "roguelike" game, ''NetHack'' features turn-based, grid-based hack and slash dungeon crawling gameplay, procedurally generated dungeons and treasure, and permadeath, requiring the player to restart the game anew should the player character die. The game uses simple ASCII graphics by default so as to display readily on a wide variety of computer displays, but can use curses with box-drawing characters, as well as substitute graphical tilesets on machines with graphics. While ''Rogue'', ''Hack'' and other e ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Roguelike
Roguelike (or rogue-like) is a subgenre of role-playing computer games traditionally characterized by a dungeon crawl through procedurally generated levels, turn-based gameplay, grid-based movement, and permanent death of the player character. Most roguelikes are based on a high fantasy narrative, reflecting their influence from tabletop role playing games such as ''Dungeons & Dragons''. Though '' Beneath Apple Manor'' predates it, the 1980 game '' Rogue'', which is an ASCII based game that runs in terminal or terminal emulator, is considered the forerunner and the namesake of the genre, with derivative games mirroring ''Rogue''s character- or sprite-based graphics. These games were popularized among college students and computer programmers of the 1980s and 1990s, leading to hundreds of variants. Some of the better-known variants include ''Hack'', ''NetHack'', ''Ancient Domains of Mystery'', '' Moria'', '' Angband'', ''Tales of Maj'Eyal'', and ''Dungeon Crawl Stone Soup''. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Roguelike
Roguelike (or rogue-like) is a subgenre of role-playing computer games traditionally characterized by a dungeon crawl through procedurally generated levels, turn-based gameplay, grid-based movement, and permanent death of the player character. Most roguelikes are based on a high fantasy narrative, reflecting their influence from tabletop role playing games such as ''Dungeons & Dragons''. Though '' Beneath Apple Manor'' predates it, the 1980 game '' Rogue'', which is an ASCII based game that runs in terminal or terminal emulator, is considered the forerunner and the namesake of the genre, with derivative games mirroring ''Rogue''s character- or sprite-based graphics. These games were popularized among college students and computer programmers of the 1980s and 1990s, leading to hundreds of variants. Some of the better-known variants include ''Hack'', ''NetHack'', ''Ancient Domains of Mystery'', '' Moria'', '' Angband'', ''Tales of Maj'Eyal'', and ''Dungeon Crawl Stone Soup''. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hack (Unix Video Game)
''Hack'' is a 1984 roguelike video game that introduced shops as gameplay elements and expanded available monsters, items, and spells. It later became the basis for ''NetHack''. History and development ''Hack'' was created in 1982 by Jay Fenlason with the assistance of Kenny Woodland, Mike Thome, and Jonathan Payne, while students at Lincoln-Sudbury Regional High School. A greatly extended version was first released on Usenet in 1984 by Andries Brouwer. Brouwer continued to work on ''Hack'' until July 1985. Don Kneller ported the game to MS-DOS and continued development there. Development on all ''Hack'' versions ended within a few years. ''Hack'' descendant ''NetHack'' was released in 1987. ''Hack'' is still available for Unix, and is distributed alongside many modern Unix-like OSes, including Debian, Ubuntu, the BSDs, Fedora, and others. ''Hack'' has also been ported to a variety of non-Unix-based platforms. ''NetHack'' is available for almost all platforms which run ''Hack' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Rogue (video Game)
''Rogue'' (also known as ''Rogue: Exploring the Dungeons of Doom'') is a dungeon crawling video game by Michael Toy and Glenn Wichman with later contributions by Ken Arnold. ''Rogue'' was originally developed around 1980 for Unix-based mainframe systems as a freely distributed executable. It was later included in the official Berkeley Software Distribution 4.2 operating system (4.2BSD). Commercial ports of the game for a range of personal computers were made by Toy, Wichman, and Jon Lane under the company A.I. Design and financially supported by the Epyx software publishers. Additional ports to modern systems have been made since by other parties using the game's now-open source code. In ''Rogue'', players control a character as they explore several levels of a dungeon seeking the Amulet of Yendor located in the dungeon's lowest level. The player-character must fend off an array of monsters that roam the dungeons. Along the way, players can collect treasures that can help them of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Permadeath
Permadeath or permanent death is a game mechanic in both tabletop games and video games in which player characters who lose all of their health are considered dead and cannot be used anymore. Depending on the situation, this could require the player to create a new character to continue, or completely restart the game potentially losing nearly all progress made. Other terms include persona death and player death. Some video games offer a hardcore mode that features this mechanic, rather than making it part of the core game. Permadeath contrasts with games that allow the player to continue in some manner, such as their character respawning at a checkpoint on "death", resurrection of their character by a magic item or spell, or being able to load and restore a saved game state to avoid the death situation. The mechanic is frequently associated with both tabletop and computer-based role-playing games, and is considered an essential element of the roguelike genre of video games. Th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Procedural Generation
In computing, procedural generation is a method of creating data algorithmically as opposed to manually, typically through a combination of human-generated assets and algorithms coupled with computer-generated randomness and processing power. In computer graphics, it is commonly used to create textures and 3D models. In video games, it is used to automatically create large amounts of content in a game. Depending on the implementation, advantages of procedural generation can include smaller file sizes, larger amounts of content, and randomness for less predictable gameplay. Procedural generation is a branch of media synthesis. Overview The term ''procedural'' refers to the process that computes a particular function. Fractals are geometric patterns which can often be generated procedurally. Commonplace procedural content includes textures and meshes. Sound is often also procedurally generated, and has applications in both speech synthesis as well as music. It has been used to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Genie
Jinn ( ar, , ') – also romanized as djinn or anglicized as genies (with the broader meaning of spirit or demon, depending on sources) – are invisible creatures in early pre-Islamic Arabian religious systems and later in Islamic mythology and theology. Like humans, they are accountable for their deeds, can be either believers (''Muslim'') or unbelievers (''kafir''); depending on whether they accept God's guidance. Since jinn are neither innately evil nor innately good, Islam acknowledged spirits from other religions and was able to adapt spirits from other religions during its expansion. Jinn are not a strictly Islamic concept; they may represent several pagan beliefs integrated into Islam. To assert a strict monotheism and the Islamic concept of ''Tauhid'', Islam denies all affinities between the jinn and God, thus placing the jinn parallel to humans, also subject to God's judgment and afterlife. The Quran condemns the pre-Islamic Arabian practise of worshipping the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Curses (programming Library)
curses is a terminal control library for Unix-like systems, enabling the construction of text user interface (TUI) applications. The name is a pun on the term " cursor optimization". It is a library of functions that manage an application's display on character-cell terminals (e.g., VT100). Overview Using curses, programmers are able to write text-based applications without writing directly for any specific terminal type. The curses library on the executing system sends the correct control characters based on the terminal type. It provides an abstraction of one or more windows that maps onto the terminal screen. Each window is represented by a character matrix. The programmer sets up the desired appearance of each window, then tells the curses package to update the screen. The library determines a minimal set of changes that are needed to update the display and then executes these using the terminal's specific capabilities and control sequences. In short, this means that the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Terminal
A computer terminal is an electronic or electromechanical hardware device that can be used for entering data into, and transcribing data from, a computer or a computing system. The teletype was an example of an early-day hard-copy terminal and predated the use of a computer screen by decades. Early terminals were inexpensive devices but very slow compared to punched cards or paper tape for input, yet as the technology improved and video displays were introduced, terminals pushed these older forms of interaction from the industry. A related development was time-sharing systems, which evolved in parallel and made up for any inefficiencies in the user's typing ability with the ability to support multiple users on the same machine, each at their own terminal or terminals. The function of a terminal is typically confined to transcription and input of data; a device with significant local, programmable data-processing capability may be called a "smart terminal" or fat client. A ter ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ASCII
ASCII ( ), abbreviated from American Standard Code for Information Interchange, is a character encoding standard for electronic communication. ASCII codes represent text in computers, telecommunications equipment, and other devices. Because of technical limitations of computer systems at the time it was invented, ASCII has just 128 code points, of which only 95 are , which severely limited its scope. All modern computer systems instead use Unicode, which has millions of code points, but the first 128 of these are the same as the ASCII set. The Internet Assigned Numbers Authority (IANA) prefers the name US-ASCII for this character encoding. ASCII is one of the List of IEEE milestones, IEEE milestones. Overview ASCII was developed from telegraph code. Its first commercial use was as a seven-bit teleprinter code promoted by Bell data services. Work on the ASCII standard began in May 1961, with the first meeting of the American Standards Association's (ASA) (now the American Nat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|