|
Mission-critical
A mission critical factor of a system is any factor (component, equipment, personnel, process, procedure, software, etc.) that is essential to business operation or to an organization. Failure or disruption of mission critical factors will result in serious impact on business operations or upon an organization, and even can cause social turmoil and catastrophes. Mission critical systems A mission critical system is a system that is essential to the survival of a business or organization. When a mission critical system fails or is interrupted, business operations are significantly impacted. Mission essential equipment and mission critical application are also known as mission critical system. Examples of mission critical systems are: an online banking system, railway/aircraft operating and control systems, electric power systems, and many other computer systems that will adversely affect business and society when they fail. A good example of a mission critical system is a na ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
System
A system is a group of Interaction, interacting or interrelated elements that act according to a set of rules to form a unified whole. A system, surrounded and influenced by its environment (systems), environment, is described by its boundaries, structure and purpose and expressed in its functioning. Systems are the subjects of study of systems theory and other systems sciences. Systems have several common properties and characteristics, including structure, function(s), behavior and interconnectivity. Etymology The term ''system'' comes from the Latin word ''systēma'', in turn from Greek language, Greek ''systēma'': "whole concept made of several parts or members, system", literary "composition"."σύστημα" Henry George Liddell, Robert Scott, ''A Greek–English Lexicon'', on Per ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Amazon
Amazon most often refers to: * Amazons, a tribe of female warriors in Greek mythology * Amazon rainforest, a rainforest covering most of the Amazon basin * Amazon River, in South America * Amazon (company), an American multinational technology company Amazon or Amazone may also refer to: Places South America * Amazon Basin (sedimentary basin), a sedimentary basin at the middle and lower course of the river * Amazon basin, the part of South America drained by the river and its tributaries * Amazon Reef, at the mouth of the Amazon basin Elsewhere * 1042 Amazone, an asteroid * Amazon Creek, a stream in Oregon, US People * Amazon Eve (born 1979), American model, fitness trainer, and actress * Lesa Lewis (born 1967), American professional bodybuilder nicknamed "Amazon" Art and entertainment Fictional characters * Amazon (Amalgam Comics) * Amazon, an alias of the Marvel supervillain Man-Killer * Amazons (DC Comics), a group of superhuman characters * The Amazon, a ' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Real-time Computing
Real-time computing (RTC) is the computer science term for hardware and software systems subject to a "real-time constraint", for example from event to system response. Real-time programs must guarantee response within specified time constraints, often referred to as "deadlines". Ben-Ari, Mordechai; "Principles of Concurrent and Distributed Programming", ch. 16, Prentice Hall, 1990, , page 164 Real-time responses are often understood to be in the order of milliseconds, and sometimes microseconds. A system not specified as operating in real time cannot usually ''guarantee'' a response within any timeframe, although ''typical'' or ''expected'' response times may be given. Real-time processing ''fails'' if not completed within a specified deadline relative to an event; deadlines must always be met, regardless of system load. A real-time system has been described as one which "controls an environment by receiving data, processing them, and returning the results sufficiently quic ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pu-239
Plutonium-239 (239Pu or Pu-239) is an isotope of plutonium. Plutonium-239 is the primary fissile isotope used for the production of nuclear weapons, although uranium-235 is also used for that purpose. Plutonium-239 is also one of the three main isotopes demonstrated usable as fuel in thermal spectrum nuclear reactors, along with uranium-235 and uranium-233. Plutonium-239 has a half-life of 24,110 years. Nuclear properties The nuclear properties of plutonium-239, as well as the ability to produce large amounts of nearly pure 239Pu more cheaply than highly enriched weapons-grade uranium-235, led to its use in nuclear weapons and nuclear power plants. The fissioning of an atom of uranium-235 in the reactor of a nuclear power plant produces two to three neutrons, and these neutrons can be absorbed by uranium-238 to produce plutonium-239 and other isotopes. Plutonium-239 can also absorb neutrons and fission along with the uranium-235 in a reactor. Of all the common nuclear fuels ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
U-235
Uranium-235 (235U or U-235) is an isotope of uranium making up about 0.72% of natural uranium. Unlike the predominant isotope uranium-238, it is fissile, i.e., it can sustain a nuclear chain reaction. It is the only fissile isotope that exists in nature as a primordial nuclide. Uranium-235 has a half-life of 703.8 million years. It was discovered in 1935 by Arthur Jeffrey Dempster. Its fission cross section for slow thermal neutrons is about 584.3±1 barns. For fast neutrons it is on the order of 1 barn. Most but not all neutron absorptions result in fission; a minority result in neutron capture forming uranium-236. Natural decay chain :\begin \ce \begin \ce \\ \ce \end \ce \\ \ce \begin \ce \\ \ce \end \ce \end Fission properties The fission of one atom of uranium-235 releases () inside the reactor. That corresponds to 19.54 TJ/ mol, or 83.14 TJ/kg. [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptographic Keys
A key in cryptography is a piece of information, usually a string of numbers or letters that are stored in a file, which, when processed through a cryptographic algorithm, can encode or decode cryptographic data. Based on the used method, the key can be different sizes and varieties, but in all cases, the strength of the encryption relies on the security of the key being maintained. A key’s security strength is dependent on its algorithm, the size of the key, the generation of the key, and the process of key exchange. Scope The key is what is used to encrypt data from plaintext to ciphertext. There are different methods for utilizing keys and encryption. Symmetric cryptography Symmetric cryptography refers to the practice of the same key being used for both encryption and decryption. Asymmetric cryptography Asymmetric cryptography has separate keys for encrypting and decrypting. These keys are known as the public and private keys, respectively. Purpose Since the key pro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Digital Certificate
In cryptography, a public key certificate, also known as a digital certificate or identity certificate, is an electronic document used to prove the validity of a Key authentication, public key. The certificate includes information about the key, information about the identity of its owner (called the subject), and the digital signature of an entity that has verified the certificate's contents (called the issuer). If the signature is valid, and the software examining the certificate trusts the issuer, then it can use that key to communicate securely with the certificate's subject. In email encryption, code signing, and Electronic signature, e-signature systems, a certificate's subject is typically a person or organization. However, in Transport Layer Security (TLS) a certificate's subject is typically a computer or other device, though TLS certificates may identify organizations or individuals in addition to their core role in identifying devices. TLS, sometimes called by its older n ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Encryption
In cryptography, encryption is the process of encoding information. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can decipher a ciphertext back to plaintext and access the original information. Encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. For technical reasons, an encryption scheme usually uses a pseudo-random encryption key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users. Historically, various forms of encryption have been used to aid in cryptography. Early encryption techniques were often used in military ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bank Of America
The Bank of America Corporation (often abbreviated BofA or BoA) is an American multinational investment bank and financial services holding company headquartered at the Bank of America Corporate Center in Charlotte, North Carolina. The bank was founded in San Francisco. It is the second-largest banking institution in the United States, after JPMorgan Chase, and the second largest bank in the world by market capitalization. Bank of America is one of the Big Four banking institutions of the United States. It serves approximately 10.73% of all American bank deposits, in direct competition with JPMorgan Chase, Citigroup, and Wells Fargo. Its primary financial services revolve around commercial banking, wealth management, and investment banking. One branch of its history stretches back to the U.S.-based Bank of Italy, founded by Amadeo Pietro Giannini in 1904, which provided various banking options to Italian immigrants who faced service discrimination. Originally headquartered ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
PayPal
PayPal Holdings, Inc. is an American multinational financial technology company operating an online payments system in the majority of countries that support online money transfers, and serves as an electronic alternative to traditional paper methods such as checks and money orders. The company operates as a payment processor for online vendors, auction sites and many other commercial users, for which it charges a fee. Established in 1998 as Confinity, PayPal went public through an IPO in 2002. It became a wholly owned subsidiary of eBay later that year, valued at $1.5 billion. In 2015 eBay spun off PayPal to its shareholders, and PayPal became an independent company again. The company was ranked 143rd on the 2022 Fortune 500 of the largest United States corporations by revenue. History Early history PayPal was originally established by Max Levchin, Peter Thiel, and Luke Nosek in December 1998 as Confinity, a company that developed security software for hand-held de ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Encrypt
In cryptography, encryption is the process of encoding information. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can decipher a ciphertext back to plaintext and access the original information. Encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. For technical reasons, an encryption scheme usually uses a pseudo-random A pseudorandom sequence of numbers is one that appears to be statistically random, despite having been produced by a completely deterministic and repeatable process. Background The generation of random numbers has many uses, such as for rando ... encryption Key (cryptography), key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An au ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
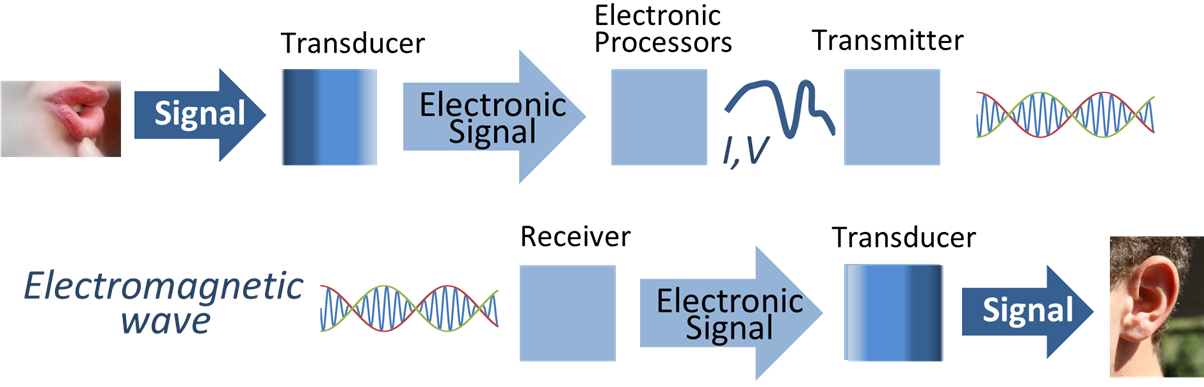
Communication System
A communications system or communication system is a collection of individual telecommunications networks, transmission systems, relay stations, tributary stations, and terminal equipment usually capable of interconnection and interoperation to form an integrated whole. The components of a communications system serve a common purpose, are technically compatible, use common procedures, respond to controls, and operate in union. Telecommunications is a method of communication (e.g., for sports broadcasting, mass media, journalism, etc.). Communication is the act of conveying intended meanings from one entity or group to another through the use of mutually understood signs and semiotic rules. Types By media An optical communication system is any form of telecommunication that uses light as the transmission medium. Equipment consists of a transmitter, which encodes a ''message'' into an optical ''signal'', a ''communication channel'', which carries the signal to its dest ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |