|
Mac OS 8.6
Mac OS 8 is an operating system that was released by Apple Computer on July 26, 1997. It includes the largest overhaul of the classic Mac OS experience since the release of System 7, approximately six years before. It places a greater emphasis on color than prior versions. Released over a series of updates, Mac OS 8 represents an incremental integration of many of the technologies which had been developed from 1988 to 1996 for Apple's overly ambitious OS named Copland. Mac OS 8 helped modernize the Mac OS while Apple developed its next-generation operating system, Mac OS X (renamed in 2012 to OS X and then in 2016 to macOS). Mac OS 8 is one of Apple's most commercially successful software releases, selling over 1.2 million copies in the first two weeks. As it came at a difficult time in Apple's history, many pirate groups refused to traffic in the new OS, encouraging people to buy it instead. Mac OS 8.0 introduces the most visible changes in the lineup, including the Platinum ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Macintosh Operating Systems
Two major famlies of Mac operating systems were developed by Apple Inc. In 1984, Apple debuted the operating system that is now known as the "Classic" Mac OS with its release of the original Macintosh System Software. The system, rebranded "Mac OS" in 1997, was preinstalled on every Macintosh until 2002 and offered on Macintosh clones for a short time in the 1990s. Noted for its ease of use, it was also criticized for its lack of modern technologies compared to its competitors. The current Mac operating system is macOS, originally named "Mac OS X" until 2012 and then "OS X" until 2016. Developed between 1997 and 2001 after Apple's purchase of NeXT, Mac OS X brought an entirely new architecture based on NeXTSTEP, a Unix system, that eliminated many of the technical challenges that the classic Mac OS faced. The current macOS is preinstalled with every Mac and receives a major update annually. It is the basis of Apple's current system software for its other devices – iOS ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Copyright Infringement
Copyright infringement (at times referred to as piracy) is the use of works protected by copyright without permission for a usage where such permission is required, thereby infringing certain exclusive rights granted to the copyright holder, such as the right to reproduce, distribute, display or perform the protected work, or to make derivative works. The copyright holder is typically the work's creator, or a publisher or other business to whom copyright has been assigned. Copyright holders routinely invoke legal and technological measures to prevent and penalize copyright infringement. Copyright infringement disputes are usually resolved through direct negotiation, a notice and take down process, or litigation in civil court. Egregious or large-scale commercial infringement, especially when it involves counterfeiting, is sometimes prosecuted via the criminal justice system. Shifting public expectations, advances in digital technology and the increasing reach of the Internet ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Preemption (computing)
In computing, preemption is the act of temporarily interrupting an executing task, with the intention of resuming it at a later time. This interrupt is done by an external scheduler with no assistance or cooperation from the task. This preemptive scheduler usually runs in the most privileged protection ring, meaning that interruption and resuming are considered highly secure actions. Such a change in the currently executing task of a processor is known as context switching. User mode and kernel mode In any given system design, some operations performed by the system may not be preemptable. This usually applies to kernel functions and service interrupts which, if not permitted to run to completion, would tend to produce race conditions resulting in deadlock. Barring the scheduler from preempting tasks while they are processing kernel functions simplifies the kernel design at the expense of system responsiveness. The distinction between user mode and kernel mode, which det ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Memory Protection
Memory protection is a way to control memory access rights on a computer, and is a part of most modern instruction set architectures and operating systems. The main purpose of memory protection is to prevent a process from accessing memory that has not been allocated to it. This prevents a bug or malware within a process from affecting other processes, or the operating system itself. Protection may encompass all accesses to a specified area of memory, write accesses, or attempts to execute the contents of the area. An attempt to access unauthorized memory results in a hardware fault, e.g., a segmentation fault, storage violation exception, generally causing abnormal termination of the offending process. Memory protection for computer security includes additional techniques such as address space layout randomization and executable space protection. Methods Segmentation Segmentation refers to dividing a computer's memory into segments. A reference to a memory location incl ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
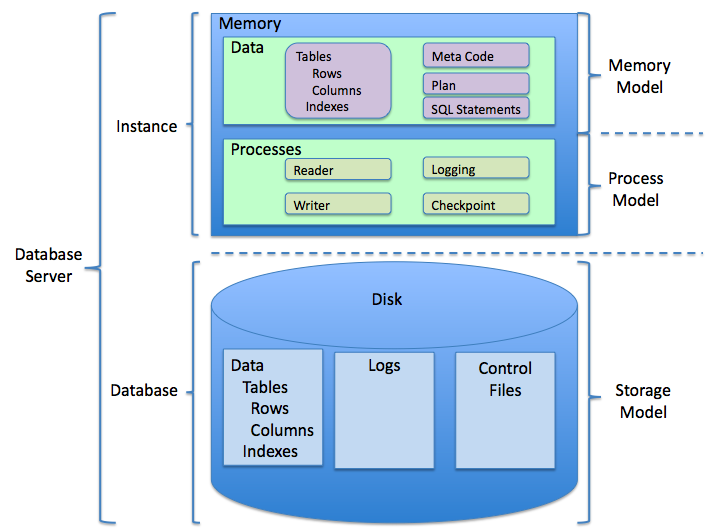
Relational Database
A relational database is a (most commonly digital) database based on the relational model of data, as proposed by E. F. Codd in 1970. A system used to maintain relational databases is a relational database management system (RDBMS). Many relational database systems are equipped with the option of using the SQL (Structured Query Language) for querying and maintaining the database. History The term "relational database" was first defined by E. F. Codd at IBM in 1970. Codd introduced the term in his research paper "A Relational Model of Data for Large Shared Data Banks". In this paper and later papers, he defined what he meant by "relational". One well-known definition of what constitutes a relational database system is composed of Codd's 12 rules. However, no commercial implementations of the relational model conform to all of Codd's rules, so the term has gradually come to describe a broader class of database systems, which at a minimum: # Present the data to the user as relati ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hardware Abstraction Layer
Hardware abstractions are sets of routines in software that provide programs with access to hardware resources through programming interfaces. The programming interface allows all devices in a particular class ''C'' of hardware devices to be accessed through identical interfaces even though ''C'' may contain different subclasses of devices that each provide a different hardware interface. Hardware abstractions often allow programmers to write device-independent, high performance applications by providing standard operating system (OS) calls to hardware. The process of abstracting pieces of hardware is often done from the perspective of a CPU. Each type of CPU has a specific instruction set architecture or ISA. The ISA represents the primitive operations of the machine that are available for use by assembly programmers and compiler writers. One of the main functions of a compiler is to allow a programmer to write an algorithm in a high-level language without having to care a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microkernel
In computer science, a microkernel (often abbreviated as μ-kernel) is the near-minimum amount of software that can provide the mechanisms needed to implement an operating system (OS). These mechanisms include low-level address space management, thread management, and inter-process communication (IPC). If the hardware provides multiple rings or CPU modes, the microkernel may be the only software executing at the most privileged level, which is generally referred to as supervisor or kernel mode. Traditional operating system functions, such as device drivers, protocol stacks and file systems, are typically removed from the microkernel itself and are instead run in user space. In terms of the source code size, microkernels are often smaller than monolithic kernels. The MINIX 3 microkernel, for example, has only approximately 12,000 lines of code. History Microkernels trace their roots back to Danish computer pioneer Per Brinch Hansen and his tenure in Danish computer compan ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intelligent Agent
In artificial intelligence, an intelligent agent (IA) is anything which perceives its environment, takes actions autonomously in order to achieve goals, and may improve its performance with learning or may use knowledge. They may be simple or complex — a thermostat is considered an example of an intelligent agent, as is a human being, as is any system that meets the definition, such as a firm, a state, or a biome. Leading AI textbooks define "artificial intelligence" as the "study and design of intelligent agents", a definition that considers goal-directed behavior to be the essence of intelligence. Goal-directed agents are also described using a term borrowed from economics, "rational agent". An agent has an "objective function" that encapsulates all the IA's goals. Such an agent is designed to create and execute whatever plan will, upon completion, maximize the expected value of the objective function. For example, a reinforcement learning agent has a "reward function ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Sherlock (software)
Sherlock, named after fictional detective Sherlock Holmes, was a file and web search tool created by Apple Inc. for the PowerPC-based "classic" Mac OS, introduced with Mac OS 8 as an extension of the Mac OS Finder's file searching capabilities. Like its predecessor (System 7.5’s totally revamped 'Find File' app, adapted by Bill Monk from his 'Find Pro' shareware find program), Sherlock searched for local files and file contents, using the same basic indexing code and search logic found in AppleSearch. Sherlock extended the system by enabling the user to search for items through the World Wide Web through a set of plugins which employed existing web search engines. These plugins were written as plain text files, so that it was a simple task for a user to write a Sherlock plugin. Sherlock was replaced by Spotlight and Dashboard in Mac OS X 10.4 Tiger, although Apple continued to include it with the default installation. Since most of the standard plug-ins for Sherlock provided ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
AppleScript
AppleScript is a scripting language created by Apple Inc. that facilitates automated control over scriptable Mac applications. First introduced in System 7, it is currently included in all versions of macOS as part of a package of system automation tools. The term "AppleScript" may refer to the language itself, to an individual script written in the language, or, informally, to the macOS Open Scripting Architecture that underlies the language. Overview AppleScript is primarily a scripting language developed by Apple to do inter-application communication (IAC) using Apple events. AppleScript is related to, but different from, Apple events. Apple events are designed to exchange data between and control other applications in order to automate repetitive tasks. AppleScript has some processing abilities of its own, in addition to sending and receiving Apple events to applications. AppleScript can do basic calculations and text processing, and is extensible, allowing the use of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
QuickDraw
A quickdraw (also known as an extender) is a piece of climbing equipment used by rock and ice climbers to allow the climbing rope to run freely through protection such as a bolt anchors or other traditional gear while leading. A quickdraw consists of two carabiner A carabiner or karabiner () is a specialized type of shackle, a metal loop with a spring-loaded gate used to quickly and reversibly connect components, most notably in safety-critical systems. The word is a shortened form of ''Karabinerhaken'' ...s connected by a semi-rigid material (sometimes called the "dogbone"). One carabiner has a straight gate and connects to an anchoring device. The other carabiner is for the climbing rope, and uses a bent gate. Quickdraws are manufactured with either a solid carabiner gate or a wire carabiner gate for its lighter weight. Use A quickdraw is a specific type of runner. Runners are used by rock and ice climbers to extend the distance between an anchoring device and the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
HFS Plus
HFS Plus or HFS+ (also known as Mac OS Extended or HFS Extended) is a journaling file system developed by Apple Inc. It replaced the Hierarchical File System (HFS) as the primary file system of Apple computers with the 1998 release of Mac OS 8.1. HFS+ continued as the primary Mac OS X file system until it was itself replaced with the Apple File System (APFS), released with macOS High Sierra in 2017. HFS+ is also one of the formats supported by the iPod digital music player. Compared to its predecessor HFS, also called ''Mac OS Standard'' or ''HFS Standard,'' HFS Plus supports much larger files (block addresses are 32-bit length instead of 16-bit) and using Unicode (instead of Mac OS Roman or any of several other character sets) for naming items. Like HFS, HFS Plus uses B-trees to store most volume metadata, but unlike most file systems that support hard links, HFS Plus supports hard links to directories. HFS Plus permits filenames up to 255 characters in length, and n-fork ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |