|
Log Management
Log management (LM) comprises an approach to dealing with large volumes of computer-generated log messages (also known as audit records, audit trails, event-logs, etc.). Log management generally covers: * Log collection * Centralized log aggregation * Long-term log storage and retention * Log rotation * Log analysis (in real-time and in bulk after storage) * Log search and reporting. Overview The primary drivers for log management implementations are concerns about security, system and network operations (such as system or network administration) and regulatory compliance. Logs are generated by nearly every computing device, and can often be directed to different locations both on a local file system or remote system. Effectively analyzing large volumes of diverse logs can pose many challenges, such as: * Volume: log data can reach hundreds of gigabytes of data per day for a large organization. Simply collecting, centralizing and storing data at this volume can be ch ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer
A computer is a machine that can be programmed to Execution (computing), carry out sequences of arithmetic or logical operations (computation) automatically. Modern digital electronic computers can perform generic sets of operations known as Computer program, programs. These programs enable computers to perform a wide range of tasks. A computer system is a nominally complete computer that includes the Computer hardware, hardware, operating system (main software), and peripheral equipment needed and used for full operation. This term may also refer to a group of computers that are linked and function together, such as a computer network or computer cluster. A broad range of Programmable logic controller, industrial and Consumer electronics, consumer products use computers as control systems. Simple special-purpose devices like microwave ovens and remote controls are included, as are factory devices like industrial robots and computer-aided design, as well as general-purpose devi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Value Proposition
In marketing, a company’s value proposition is the full mix of benefits or economic value which it promises to deliver to the current and future customers (i.e., a market segment) who will buy their products and/or services. It is part of a company's overall marketing strategy which differentiates its brand and fully positions it in the market. A value proposition can apply to an entire organization, or parts thereof, or customer accounts, or products or services. A value proposition can be written as a business or marketing statement (called a "positioning statement") which summarizes why a consumer should buy a product or use a service. A compellingly worded positioning statement has the potential to convince a prospective consumer that a particular product or service the company offers will add more value or better solve a problem (i.e. the "pain-point") for them than other similar offerings will, thus turning them into a paying client. The positioning statement usually co ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Web Counter
A web counter or hit counter is a publicly displayed running tally of the number of visits a webpage has received. Web counters are usually displayed as an inline digital image or in plain text. Image rendering of digits may use a variety of fonts and styles, with a classic design imitating the wheels of an odometer. Web counters were often accompanied by the date it was set up or last reset, to provide more context to readers on how to interpret the number shown. Although initially a way to publicly showcase a site's popularity to its visitors, some early web counters were simply web bugs used by webmasters to track hits and included no visible on-page elements. Counters were popular in the 1990s, but were later replaced by other web traffic measures such as self-hosted scripts like Analog, and later on by remote systems that used JavaScript, like Google Analytics. These systems typically do not include on-page elements displaying the count. Thus, seeing a web counter on a mo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
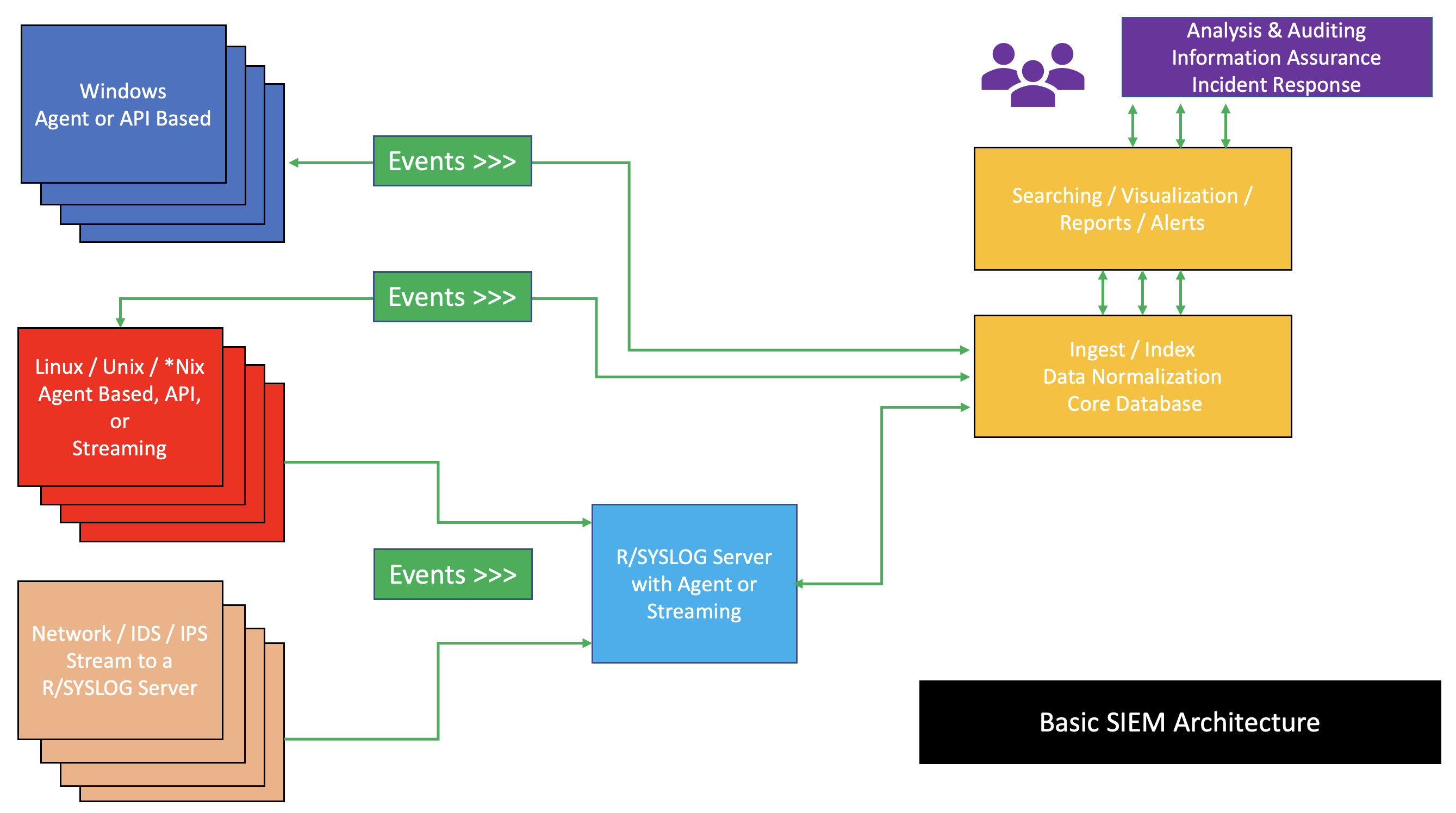
Syslog
In computing, syslog is a standard for message logging. It allows separation of the software that generates messages, the system that stores them, and the software that reports and analyzes them. Each message is labeled with a facility code, indicating the type of system generating the message, and is assigned a severity level. Computer system designers may use syslog for system management and security auditing as well as general informational, analysis, and debugging messages. A wide variety of devices, such as printers, routers, and message receivers across many platforms use the syslog standard. This permits the consolidation of logging data from different types of systems in a central repository. Implementations of syslog exist for many operating systems. When operating over a network, syslog uses a client-server architecture where a syslog server listens for and logs messages coming from clients. History Syslog was developed in the 1980s by Eric Allman as part of the Se ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Server Log
In computing, logging is the act of keeping a log of events that occur in a computer system, such as problems, errors or just information on current operations. These events may occur in the operating system or in other software. A message or log entry is recorded for each such event. These log messages can then be used to monitor and understand the operation of the system, to debug problems, or during an audit. Logging is particularly important in multi-user software, to have a central overview of the operation of the system. In the simplest case, messages are written to a file, called a log file. Alternatively, the messages may be written to a dedicated logging system or to a log management software, where it is stored in a database or on a different computer system. Specifically, a transaction log is a log of the communications between a system and the users of that system, or a data collection method that automatically captures the type, content, or time of transactions ma ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Information And Event Management
Security information and event management (SIEM) is a field within the field of computer security, where software products and services combine security information management (SIM) and security event management (SEM). They provide real-time analysis of security alerts generated by applications and network hardware. Vendors sell SIEM as software, as appliances, or as managed services; these products are also used to log security data and generate reports for compliance purposes. The term and the initialism SIEM was coined by Mark Nicolett and Amrit Williams of Gartner in 2005. History Monitoring system logs has grown more prevalent as complex cyber-attacks force compliance and regulatory mechanisms to mandate logging security controls within a Risk Management Framework. Logging levels of a system started with the primary function of troubleshooting system errors or debugging code compiled and run. As operating systems and networks have increased in complexity, so has the event ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Log Management Knowledge Base
The Log Management Knowledge Base is a free database of detailed descriptions on over 20,000 event logs generated by Windows systems, syslog devices and applications. Provided as a free service to the IT community by Prism Microsystems, the aim of the Knowledge Base is to help IT personnel make sense of the large amounts of cryptic and arcane log data generated by network systems and IT infrastructures. Log data provides a record of all corporate system activity and is critical for improving security, complying with requirements such as Sarbanes-Oxley, HIPAA and PCI-DSS, and optimizing IT operations. However, given the large number of logs produced by different devices, their inherent obscurity and the lack of a standard logging format, system-specific expertise is typically needed to extract any meaningful intelligence. The Knowledge Base provides this expertise free of charge via a searchable web repository with the aim of making log data readily understandable by all. The Knowled ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Log Monitor
Log monitors are a type of software that monitor log files. Servers, application, network and security devices generate log files. Errors, problems, and more information is constantly logged and saved for later log analysis. In order to detect problems automatically, system administrators and operations set up monitors on the generated logs. The log monitors scan the log files and search for known text patterns and rules that indicate important events. Once an event is detected, the monitoring system will send an alert, either to a person or to another software Software is a set of computer programs and associated documentation and data. This is in contrast to hardware, from which the system is built and which actually performs the work. At the lowest programming level, executable code consists .../ hardware system. Monitoring logs help to identify security events that occurred or might occur. System administration Website monitoring software {{software-stub ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Logging
A data logger (also datalogger or data recorder) is an electronic device that records data over time or about location either with a built-in instrument or sensor or via external instruments and sensors. Increasingly, but not entirely, they are based on a digital processor (or computer), and called digital data loggers (DDL). They generally are small, battery-powered, portable, and equipped with a microprocessor, internal memory for data storage, and sensors. Some data loggers interface with a personal computer and use software to activate the data logger and view and analyze the collected data, while others have a local interface device (keypad, LCD) and can be used as a stand-alone device. Data loggers vary from general-purpose types for a range of measurement applications to very specific devices for measuring in one environment or application type only. It is common for general purpose types to be programmable; however, many remain as static machines with only a limited nu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anomaly Detection At Multiple Scales
Anomaly Detection at Multiple Scales, or ADAMS, was a $35 million DARPA project designed to identify patterns and anomalies in very large data sets. It is under DARPA's DARPA#Current program offices, Information Innovation office and began in 2011 and ended in August 2014 The project was intended to detect and prevent insider threats such as "a soldier in good mental health becoming homicidal or suicidal", an "innocent insider becoming malicious", or "a government employee [who] abuses access privileges to share classified information". Specific cases mentioned are Nidal Malik Hasan and WikiLeaks source Chelsea Manning. Commercial applications may include finance. The intended recipients of the system output are operators in the counterintelligence agencies. The Proactive Discovery of Insider Threats Using Graph Analysis and Learning was part of the ADAMS project. The Georgia Tech team includes noted high-performance computing researcher David Bader (computer scientist). See als ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Proactive Discovery Of Insider Threats Using Graph Analysis And Learning
''The Prodigal'' is a 1955 epic biblical film. The Prodigal, Prodigal or Prodigals may also refer to: Arts, entertainment and media Film and television * ''The Prodigal'' (1931 film), an early talkie film * ''The Prodigal'' (1983 film), directed by James F. Collier * "The Prodigal" (''Angel''), a 2000 episode of the TV show * "The Prodigal", a 1985 episode of ''MacGyver'' TV series) * "The Prodigal", a 1996 episode of ''Xena: Warrior Princess'' (season 1) TV series * "The Prodigal", a 2008 episode of ''Stargate Atlantis'' (season 5) TV series * "Prodigal", a 2003 episode of ''Smallville'' (season 2) TV series Music * Prodigal (band), an American progressive contemporary Christian music band ** ''Prodigal'' (album), a 1982 album by the band * "Prodigal", a song by Porcupine Tree from the 2002 album ''In Absentia'' * "Prodigal", a song by OneRepublic from the 2007 album '' Dreaming Out Loud'' * "Prodigal", a song by Relient K from the 2016 album '' Air for Free'' * "The Pr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
DARPA
The Defense Advanced Research Projects Agency (DARPA) is a research and development agency of the United States Department of Defense responsible for the development of emerging technologies for use by the military. Originally known as the Advanced Research Projects Agency (ARPA), the agency was created on February 7, 1958, by President Dwight D. Eisenhower in response to the Soviet Union, Soviet launching of Sputnik 1 in 1957. By collaborating with academia, industry, and government partners, DARPA formulates and executes research and development projects to expand the frontiers of technology and science, often beyond immediate U.S. military requirements.Dwight D. Eisenhower and Science & Technology, (2008). Dwight D. Eisenhower Memorial CommissionSource ''The Economist'' has called DARPA the agency "that shaped the modern world," and pointed out that "Moderna COVID-19 vaccine, Moderna's COVID-19 vaccine sits alongside weather satellites, Global Positioning System, GPS, Unmann ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |