|
Lawrence A. Gordon
Lawrence A. Gordon is the Ernst & Young, EY Alumni Professor of Managerial Accounting and Information Assurance at the University of Maryland’s Robert H. Smith School of Business. He is also an Affiliate Professor in the University of Maryland Institute for Advanced Computer Studies.Maryland Cybersecurity Center at http://www.cyber.umd.edu/faculty Gordon earned his Ph.D. in Managerial Economics from Rensselaer Polytechnic Institute. Gordon's research focuses on such issues as economic aspects of information security (including cybersecurity or computer security), corporate performance measures, cost management systems, and capital investments. He is the author of approximately 100 articles. He is the namesake of the Gordon–Loeb model, Gordon-Loeb model. Bibliography * ''Managerial Accounting: Concepts and Empirical Evidence'' () * ''Managing Cybersecurity Resources: A Cost-Benefit Analysis'' () * ''Improving Capital Budgeting: A Decision Support System Approach'' () Referen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Rensselaer Polytechnic Institute
Rensselaer Polytechnic Institute () (RPI) is a private research university in Troy, New York, with an additional campus in Hartford, Connecticut. A third campus in Groton, Connecticut closed in 2018. RPI was established in 1824 by Stephen Van Rensselaer and Amos Eaton for the "application of science to the common purposes of life" and is the oldest technological university in the English-speaking world and the Western Hemisphere. Built on a hillside, RPI's campus overlooks the city of Troy and the Hudson River, and is a blend of traditional and modern architecture. The institute operates an on‑campus business incubator and the Rensselaer Technology Park. RPI is organized into six main schools which contain 37 departments, with emphasis on science and technology. It is classified among "R1: Doctoral Universities: Very High Research Activity" and many of its engineering programs are highly ranked. As of 2017, RPI's faculty and alumni included 6 members of the National Inve ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ernst & Young
Ernst & Young Global Limited, trade name EY, is a multinational professional services partnership headquartered in London, England. EY is one of the largest professional services networks in the world. Along with Deloitte, KPMG and PricewaterhouseCoopers (PwC), it is considered one of the Big Four accounting firms. It primarily provides assurance (which includes financial audit), tax, consulting and advisory services to its clients. Like many of the larger accounting firms in recent years, EY has expanded into markets adjacent to accounting, including strategy, operations, HR, technology, and financial services consulting. EY operates as a network of member firms which are structured as separate legal entities in a partnership, which has 312,250 employees in over 700 offices in more than 150 countries around the world. The firm's current partnership was formed in 1989 by a merger of two accounting firms; Ernst & Whinney and Arthur Young & Co. It was named Ernst & Young until ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Assurance
Information assurance (IA) is the practice of assuring information and managing risks related to the use, processing, storage, and transmission of information. Information assurance includes protection of the integrity, availability, authenticity, non-repudiation and confidentiality of user data. IA encompasses not only digital protections but also physical techniques. These protections apply to data in transit, both physical and electronic forms, as well as data at rest . IA is best thought of as a superset of information security (i.e. umbrella term), and as the business outcome of information risk management. Overview Information assurance (IA) is the process of processing, storing, and transmitting the right information to the right people at the right time. IA relates to the business level and strategic risk management of information and related systems, rather than the creation and application of security controls. IA is used to benefit business through the use of information ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
University Of Maryland
The University of Maryland, College Park (University of Maryland, UMD, or simply Maryland) is a public land-grant research university in College Park, Maryland. Founded in 1856, UMD is the flagship institution of the University System of Maryland. It is also the largest university in both the state and the Washington metropolitan area, with more than 41,000 students representing all fifty states and 123 countries, and a global alumni network of over 388,000. Together, its 12 schools and colleges offer over 200 degree-granting programs, including 92 undergraduate majors, 107 master's programs, and 83 doctoral programs. UMD is a member of the Association of American Universities and competes in intercollegiate athletics as a member of the Big Ten Conference. The University of Maryland's proximity to the nation's capital has resulted in many research partnerships with the federal government; faculty receive research funding and institutional support from many agencies, such ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Robert H
The name Robert is an ancient Germanic given name, from Proto-Germanic "fame" and "bright" (''Hrōþiberhtaz''). Compare Old Dutch ''Robrecht'' and Old High German ''Hrodebert'' (a compound of '' Hruod'' ( non, Hróðr) "fame, glory, honour, praise, renown" and ''berht'' "bright, light, shining"). It is the second most frequently used given name of ancient Germanic origin. It is also in use as a surname. Another commonly used form of the name is Rupert. After becoming widely used in Continental Europe it entered England in its Old French form ''Robert'', where an Old English cognate form (''Hrēodbēorht'', ''Hrodberht'', ''Hrēodbēorð'', ''Hrœdbœrð'', ''Hrœdberð'', ''Hrōðberχtŕ'') had existed before the Norman Conquest. The feminine version is Roberta. The Italian, Portuguese, and Spanish form is Roberto. Robert is also a common name in many Germanic languages, including English, German, Dutch, Norwegian, Swedish, Scots, Danish, and Icelandic. It can be use ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Security
Information security, sometimes shortened to InfoSec, is the practice of protecting information by mitigating information risks. It is part of information risk management. It typically involves preventing or reducing the probability of unauthorized/inappropriate access to data, or the unlawful use, disclosure, disruption, deletion, corruption, modification, inspection, recording, or devaluation of information. It also involves actions intended to reduce the adverse impacts of such incidents. Protected information may take any form, e.g. electronic or physical, tangible (e.g. paperwork) or intangible (e.g. knowledge). Information security's primary focus is the balanced protection of the confidentiality, integrity, and availability of data (also known as the CIA triad) while maintaining a focus on efficient policy implementation, all without hampering organization productivity. This is largely achieved through a structured risk management process that involves: * identifying inform ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cybersecurity
Computer security, cybersecurity (cyber security), or information technology security (IT security) is the protection of computer systems and networks from attack by malicious actors that may result in unauthorized information disclosure, theft of, or damage to hardware, software, or data, as well as from the disruption or misdirection of the services they provide. The field has become of significance due to the expanded reliance on computer systems, the Internet, and wireless network standards such as Bluetooth and Wi-Fi, and due to the growth of smart devices, including smartphones, televisions, and the various devices that constitute the Internet of things (IoT). Cybersecurity is one of the most significant challenges of the contemporary world, due to both the complexity of information systems and the societies they support. Security is of especially high importance for systems that govern large-scale systems with far-reaching physical effects, such as power distribution, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Security
Computer security, cybersecurity (cyber security), or information technology security (IT security) is the protection of computer systems and networks from attack by malicious actors that may result in unauthorized information disclosure, theft of, or damage to hardware, software, or data, as well as from the disruption or misdirection of the services they provide. The field has become of significance due to the expanded reliance on computer systems, the Internet, and wireless network standards such as Bluetooth and Wi-Fi, and due to the growth of smart devices, including smartphones, televisions, and the various devices that constitute the Internet of things (IoT). Cybersecurity is one of the most significant challenges of the contemporary world, due to both the complexity of information systems and the societies they support. Security is of especially high importance for systems that govern large-scale systems with far-reaching physical effects, such as power distribution, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
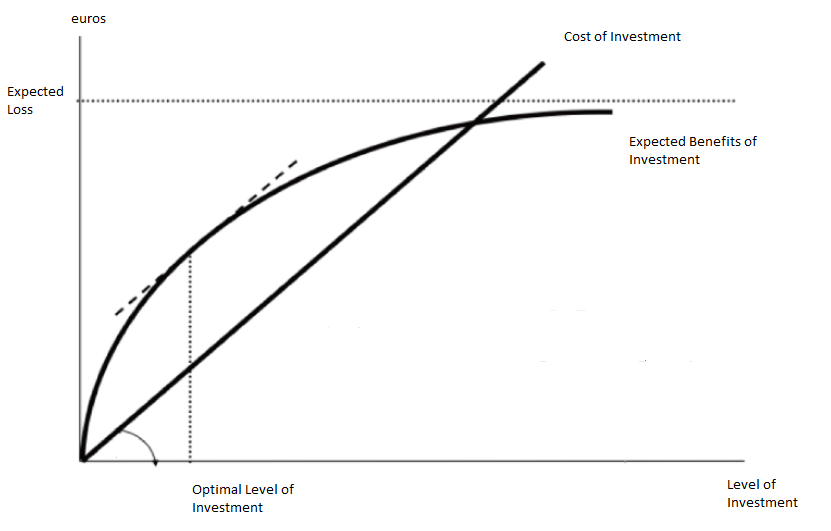
Gordon–Loeb Model
The Gordon–Loeb model is a mathematical economic model analyzing the optimal investment level in information security. The primary benefits from cybersecurity investments result from the cost savings associated with Data breach, cyber breaches that are prevented due to the investment. However, as with any investment, it is important to cost benefit analysis, compare the benefits to the costs when deciding how to invest. The Gordon-Loeb model provides a valuable framework for deriving, on a cost-benefit basis, the appropriate amount to invest in cybersecurity related activities. The basic components of the Gordon-Loeb model are as follows: # Data (information) sets of organizations that are vulnerable to cyber-attacks. This vulnerability, denoted as (), represents the probability that a breach to a specific information set will occur under current conditions. # If an information set is breached, the value of the information set represents the potential loss (i.e., the cost of t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Year Of Birth Missing (living People)
A year or annus is the orbital period of a planetary body, for example, the Earth, moving in its orbit around the Sun. Due to the Earth's axial tilt, the course of a year sees the passing of the seasons, marked by change in weather, the hours of daylight, and, consequently, vegetation and soil fertility. In temperate and subpolar regions around the planet, four seasons are generally recognized: spring, summer, autumn and winter. In tropical and subtropical regions, several geographical sectors do not present defined seasons; but in the seasonal tropics, the annual wet and dry seasons are recognized and tracked. A calendar year is an approximation of the number of days of the Earth's orbital period, as counted in a given calendar. The Gregorian calendar, or modern calendar, presents its calendar year to be either a common year of 365 days or a leap year of 366 days, as do the Julian calendars. For the Gregorian calendar, the average length of the calendar year (the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Living People
Related categories * :Year of birth missing (living people) / :Year of birth unknown * :Date of birth missing (living people) / :Date of birth unknown * :Place of birth missing (living people) / :Place of birth unknown * :Year of death missing / :Year of death unknown * :Date of death missing / :Date of death unknown * :Place of death missing / :Place of death unknown * :Missing middle or first names See also * :Dead people * :Template:L, which generates this category or death years, and birth year and sort keys. : {{DEFAULTSORT:Living people 21st-century people People by status ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Rensselaer Polytechnic Institute Alumni
Rensselaer may refer to: Places *Rensselaer, Indiana, a city ** Rensselaer (Amtrak station), serving the city * Rensselaer, Missouri, a village *Rensselaer County, New York * Rensselaer, New York, a city in Rensselaer County * Rensselaer Falls, New York, a village in St. Lawrence County * Rensselaerville, New York, a town in Albany County *Manor of Rensselaerswyck, the Van Rensselaer family's estate during colonial times People * Van Rensselaer (surname) * Rensselaer Morse Lewis (1820-1888), Wisconsin state legislator * Rensselaer Nelson (1826-1904), U.S. federal judge * Rensselaer Westerlo (1776–1851), U.S. Congressman from New York * Bret Rensselaer, an American-born, British spy in the Bernard Samson novels Other * Rensselaer Polytechnic Institute, a university in Troy, New York See also * Van Rensselaer (other) Van Rensselaer may refer to: *Van Rensselaer family, a prominent Dutch American family *Van Rensselaer (surname), a surname (including a list of people ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |