|
Log Management Software
Log management is the process for generating, transmitting, storing, accessing, and disposing of log data. A log data (or ''logs'') is composed of entries (records), and each entry contains information related to a specific event that occur within an organization's computing assets, including physical and virtual platforms, networks, services, and cloud environments. The process of log management generally breaks down into: * Log collection - a process of capturing actual data from log files, application standard output stream (stdout), network socket and other sources. * Logs aggregation (centralization) - a process of putting all the log data together in a single place for the sake of further analysis or/and retention. * Log storage and retention - a process of handling large volumes of log data according to corporate or regulatory policies (compliance). * Log analysis - a process that helps operations and security team to handle system performance issues and security incidents ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Standard Streams
In computer programming, standard streams are preconnected input and output communication channels between a computer program and its environment when it begins execution. The three input/output (I/O) connections are called standard input (stdin), standard output (stdout) and standard error (stderr). Originally I/O happened via a physically connected system console (input via keyboard, output via monitor), but standard streams abstract this. When a command is executed via an interactive shell, the streams are typically connected to the text terminal on which the shell is running, but can be changed with redirection or a pipeline. More generally, a child process inherits the standard streams of its parent process. Application Users generally know standard streams as input and output channels that handle data coming from an input device, or that write data from the application. The data may be text with any encoding, or binary data. When a program is run as a daemon, its stan ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Common Log Format
For computer log management, the Common Log Format, also known as the NCSA Common log format, (after NCSA HTTPd) is a standardized text file format used by web servers when generating server log files. Because the format is standardized, the files can be readily analyzed by a variety of web analysis programs, for example Webalizer and Analog. Each line in a file stored in the Common Log Format has the following syntax: host ident authuser timestamp request-line status bytes The format is extended by the Combined Log Format with referer and user-agent fields. Example 127.0.0.1 ident alice 1/May/2025:07:20:10 +0000"GET /index.html HTTP/1.1" 200 9481 A field set to dash () indicates missing data. * is the IP address of the client (remote host) which made the request to the server. * is the RFC 1413 identity of the client, if supplied. * is the userid of the person requesting the document. Missing unless HTTP authentication is used. * is the request timestamp. Her ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Management
Network management is the process of administering and managing computer networks. Services provided by this discipline include fault analysis, performance management, provisioning of networks and maintaining quality of service. Network management software is used by network administrators to help perform these functions. Technologies A small number of accessory methods exist to support network and network device management. Network management allows IT professionals to monitor network components within large network area. Access methods include the SNMP, command-line interface (CLI), custom XML, CMIP, Windows Management Instrumentation (WMI), Transaction Language 1 (TL1), CORBA, NETCONF, RESTCONF and the Java Management Extensions (JMX). Schemas include the Structure of Management Information (SMI), YANG, WBEM, the Common Information Model ( CIM Schema), and MTOSI amongst others. Value Effective network management can provide positive strategic impacts. For ex ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Web Log Analysis Software
Web log analysis software (also called a web log analyzer) is a kind of web analytics software that parses a server log file from a web server, and based on the values contained in the log file, derives indicators about when, how, and by whom a web server is visited. Reports are usually generated immediately, but data extracted from the log files can alternatively be stored in a database, allowing various reports to be generated on demand. Features supported by log analysis packages may include "hit filters", which use pattern matching to examine selected log data. Common indicators * Number of visits and number of unique visitors * Visit duration and last visits * Authenticated users, and last authenticated visits * Days of week and rush hours * Domains/countries of host's visitors. * Hosts list * Number of page views * Most viewed, entry, and exit pages * File types * OS used * Browsers used * Robots used * HTTP referrer * Search engines, key phrases and keywords used to fin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Web Counter
A web counter or hit counter is a publicly displayed running tally of the number of visits a webpage has received. Web counters are usually displayed as an inline digital image or in plain text. Image rendering of digits may use a variety of fonts and styles, with a classic design imitating the wheels of an odometer. Web counters were often accompanied by the date it was set up or last reset, to provide more context to readers on how to interpret the number shown. Although initially a way to publicly showcase a site's popularity to its visitors, some early web counters were simply web bugs used by webmasters to track hits and included no visible on-page elements. Counters were popular in the 1990s, but were later replaced by other web traffic measures such as self-hosted scripts like Analog, and later on by remote systems that used JavaScript, like Google Analytics. These systems typically do not include on-page elements displaying the count. Thus, seeing a web counter on a mo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Syslog
In computing, syslog () is a standard for message logging. It allows separation of the software that generates messages, the system that stores them, and the software that reports and analyzes them. Each message is labeled with a facility code, indicating the type of system generating the message, and is assigned a severity level. Computer system designers may use syslog for system management and security auditing as well as general informational, analysis, and debugging messages. A wide variety of devices, such as printers, routers, and message receivers across many platforms use the syslog standard. This permits the consolidation of logging data from different types of systems in a central repository. Implementations of syslog exist for many operating systems. When operating over a network, syslog uses a client-server architecture where a syslog server listens for and logs messages coming from clients. History Syslog was developed in the 1980s by Eric Allman as part of the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Server Log
In computing, logging is the act of keeping a log of events that occur in a computer system, such as problems, errors or broad information on current operations. These events may occur in the operating system or in other software. A message or ''log entry'' is recorded for each such event. These log messages can then be used to monitor and understand the operation of the system, to debug problems, or during an audit. Logging is particularly important in multi-user software, to have a central overview of the operation of the system. In the simplest case, messages are written to a file, called a ''log file''. Alternatively, the messages may be written to a dedicated logging system or to a log management software, where it is stored in a database or on a different computer system. Specifically, a ''transaction log'' is a log of the communications between a system and the users of that system, or a data collection method that automatically captures the type, content, or time of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
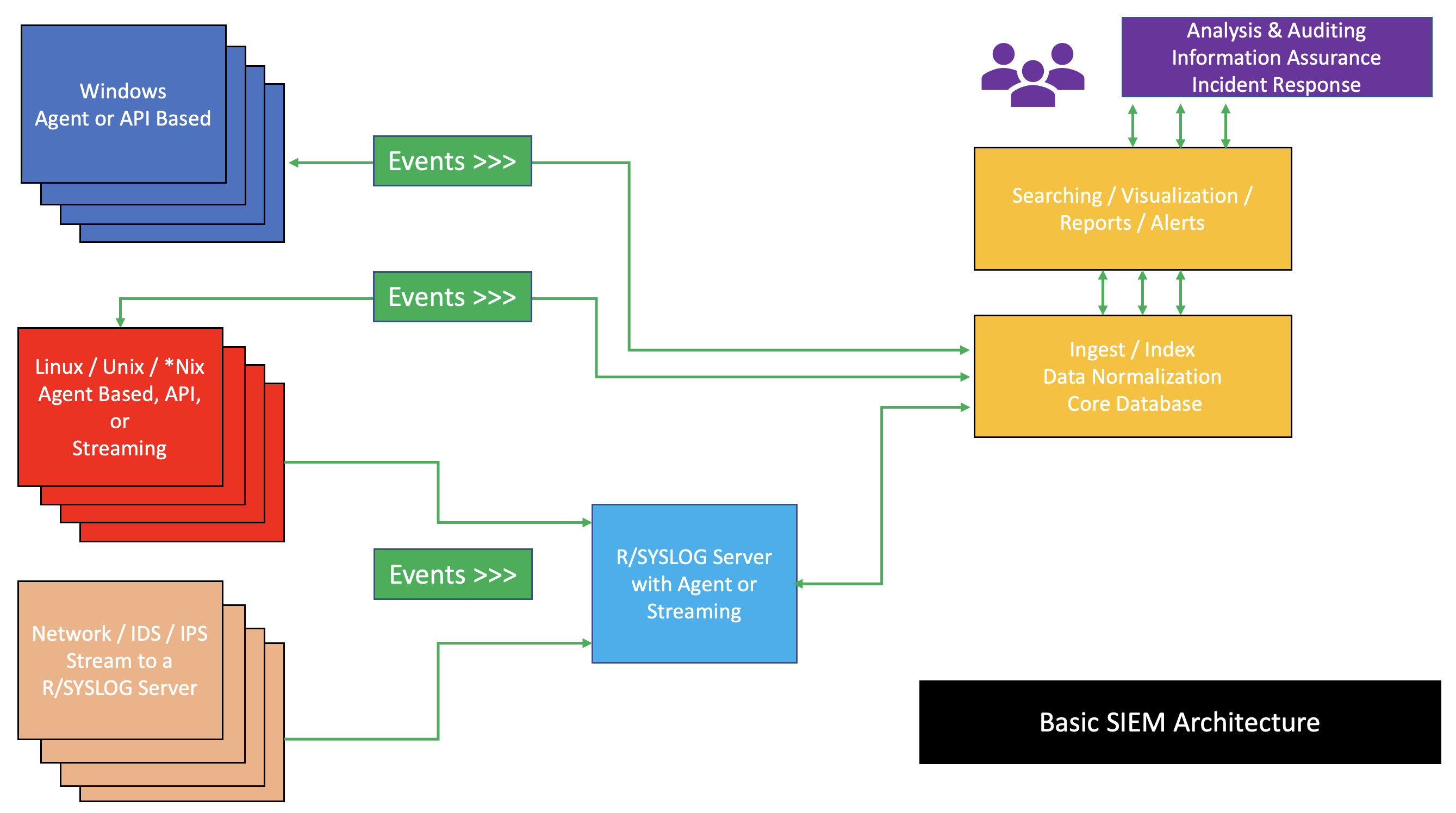
Security Information And Event Management
Security information and event management (SIEM) is a field within computer security that combines security information management (SIM) and security event management (SEM) to enable real-time analysis of security alerts generated by applications and network hardware. SIEM systems are central to Security operations center, security operations centers (SOCs), where they are employed to detect, investigate, and respond to security incidents. SIEM technology collects and aggregates data from various systems, allowing organizations to meet compliance requirements while safeguarding against Cyberattack, threats. National Institute of Standards and Technology (NIST) definition for SIEM tool is application that provides the ability to gather security data from information system components and present that data as actionable information via a single interface. SIEM tools can be implemented as software, hardware, or managed services. SIEM systems log security events and generating reports to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Log Management Knowledge Base
The Log Management Knowledge Base is a free database of detailed descriptions on over 20,000 event logs generated by Windows systems, syslog devices and applications. Provided as a free service to the IT community by Prism Microsystems, the aim of the Knowledge Base is to help IT personnel make sense of the large amounts of cryptic and arcane log data generated by network systems and IT infrastructures. Log data provides a record of all corporate system activity and is critical for improving security, complying with requirements such as Sarbanes-Oxley, HIPAA and PCI-DSS, and optimizing IT operations. However, given the large number of logs produced by different devices, their inherent obscurity and the lack of a standard logging format, system-specific expertise is typically needed to extract any meaningful intelligence. The Knowledge Base provides this expertise free of charge via a searchable web repository with the aim of making log data readily understandable by all. The Knowled ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Log Monitor
Log monitors are a type of software that monitor log files. Servers, application, network and security devices generate log files. Errors, problems, and more information is constantly logged and saved for later log analysis. In order to detect problems automatically, system administrators and operations set up monitors on the generated logs. The log monitors scan the log files and search for known text patterns and rules that indicate important events. Once an event is detected, the monitoring system will send an alert, either to a person or to another software Software consists of computer programs that instruct the Execution (computing), execution of a computer. Software also includes design documents and specifications. The history of software is closely tied to the development of digital comput .../ hardware system. Monitoring logs help to identify security events that occurred or might occur. References System administration Website monitoring software ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Logging
A data logger (also datalogger or data recorder) is an electronic device that records data over time or about location either with a built-in instrument or sensor or via external instruments and sensors. Increasingly, but not entirely, they are based on a digital processor (or computer), and called digital data loggers (DDL). They generally are small, battery-powered, portable, and equipped with a microprocessor, internal memory for data storage, and sensors. Some data loggers interface with a personal computer and use software to activate the data logger and view and analyze the collected data, while others have a local interface device (keypad, LCD) and can be used as a stand-alone device. Data loggers vary from general-purpose devices for various measurement applications to very specific devices for measuring in one environment or application type only. While it is common for general-purpose types to be programmable, many remain static machines with only a limited number o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anomaly Detection At Multiple Scales
Anomaly Detection at Multiple Scales, or ADAMS was a $35 million DARPA project designed to identify patterns and anomalies in very large data sets. It is under DARPA's Information Innovation office and began in 2011 and ended in August 2014 The project was intended to detect and prevent insider threats such as "a soldier in good mental health becoming homicidal or suicidal", an "innocent insider becoming malicious", or "a government employee who">/nowiki>who/nowiki> abuses access privileges to share classified information". Specific cases mentioned are Nadal Malik Hasan and WikiLeaks source Chelsea Manning. Commercial applications may include finance. The intended recipients of the system output are operators in the counterintelligence agencies. A final report was published on May 11, 2015, detailing a system known as Anomaly Detection Engine for Networks, or ADEN, developed by the University of Maryland, College Park, whose goal was to "identify malicious users within a networ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |