|
Lions' Commentary On UNIX 6th Edition, With Source Code
''A Commentary on the UNIX Operating System'' by John Lions (later reissued as ''Lions' Commentary on UNIX 6th Edition'') is a highly influential 1976 publication containing analytical commentary on the source code of the 6th Edition Unix computer operating system "resident nucleus" (i.e., kernel) software, plus copy formatted and indexed by Lions, of said source code obtained from the authors at AT&T Bell Labs. It is also commonly referred to as the Lions Book. Itself an exemplar of the early success of UNIX as portable code for a publishing platform, Lions's work was typeset using UNIX tools, on systems running code ported at the University, similar to that which it documented, see ''page vi''. It was commonly held to be the most copied book in computer science. Despite its age, Lions's book is still considered an excellent commentary on simple, high quality code. Lions's work was most recently reprinted in 1996 by Peer-To-Peer Communications, and has been circulated, recr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Brian Kernighan
Brian Wilson Kernighan (; born 1942) is a Canadian computer scientist. He worked at Bell Labs and contributed to the development of Unix alongside Unix creators Ken Thompson and Dennis Ritchie. Kernighan's name became widely known through co-authorship of the first book on the C programming language (''The C Programming Language'') with Dennis Ritchie. Kernighan affirmed that he had no part in the design of the C language ("it's entirely Dennis Ritchie's work"). He authored many Unix programs, including ditroff. Kernighan is coauthor of the AWK and AMPL programming languages. The "K" of K&R C and of AWK both stand for "Kernighan". In collaboration with Shen Lin he devised well-known heuristics for two NP-complete optimization problems: graph partitioning and the travelling salesman problem. In a display of authorial equity, the former is usually called the Kernighan–Lin algorithm, while the latter is known as the Lin–Kernighan heuristic. Kernighan has been a P ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
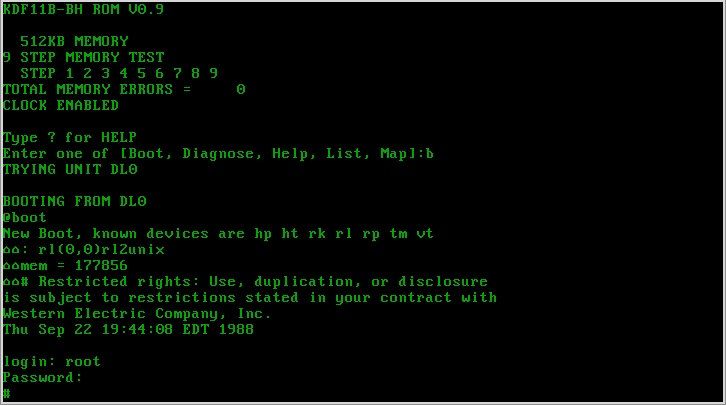
SIMH
SIMH is a free and open source, multi-platform multi-system emulator. It is maintained by Bob Supnik, a former DEC engineer and DEC vice president, and has been in development in one form or another since the 1960s. History SIMH was based on a much older systems emulator called MIMIC, which was written in the late 1960s at Applied Data Research."Preserving Computing's Past: Restoration and Simulation" Max Burnet and Bob Supnik, Digital Technical Journal, Volume 8, Number 3, 1996. SIMH was started in 1993 with the purpose of preserving hardware and software that was fading into obscurity. In May 2022, the |
Andrew S
Andrew is the English form of a given name common in many countries. In the 1990s, it was among the top ten most popular names given to boys in English-speaking countries. "Andrew" is frequently shortened to "Andy" or "Drew". The word is derived from the el, Ἀνδρέας, ''Andreas'', itself related to grc, ἀνήρ/ἀνδρός ''aner/andros'', "man" (as opposed to "woman"), thus meaning "manly" and, as consequence, "brave", "strong", "courageous", and "warrior". In the King James Bible, the Greek "Ἀνδρέας" is translated as Andrew. Popularity Australia In 2000, the name Andrew was the second most popular name in Australia. In 1999, it was the 19th most common name, while in 1940, it was the 31st most common name. Andrew was the first most popular name given to boys in the Northern Territory in 2003 to 2015 and continuing. In Victoria, Andrew was the first most popular name for a boy in the 1970s. Canada Andrew was the 20th most popular name chosen for mal ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Jargon File
The Jargon File is a glossary and usage dictionary of slang used by computer programmers. The original Jargon File was a collection of terms from technical cultures such as the MIT AI Lab, the Stanford AI Lab (SAIL) and others of the old ARPANET AI/LISP/ PDP-10 communities, including Bolt, Beranek and Newman, Carnegie Mellon University, and Worcester Polytechnic Institute. It was published in paperback form in 1983 as ''The Hacker's Dictionary'' (edited by Guy Steele), revised in 1991 as ''The New Hacker's Dictionary'' (ed. Eric S. Raymond; third edition published 1996). The concept of the file began with the Tech Model Railroad Club (TMRC) that came out of early TX-0 and PDP-1 hackers in the 1950s, where the term hacker emerged and the ethic, philosophies and some of the nomenclature emerged. 1975 to 1983 The Jargon File (referred to here as "Jargon-1" or "the File") was made by Raphael Finkel at Stanford in 1975. From that time until the plug was finally pulled o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Open-source Software
Open-source software (OSS) is computer software that is released under a license in which the copyright holder grants users the rights to use, study, change, and distribute the software and its source code to anyone and for any purpose. Open-source software may be developed in a collaborative public manner. Open-source software is a prominent example of open collaboration, meaning any capable user is able to participate online in development, making the number of possible contributors indefinite. The ability to examine the code facilitates public trust in the software. Open-source software development can bring in diverse perspectives beyond those of a single company. A 2008 report by the Standish Group stated that adoption of open-source software models has resulted in savings of about $60 billion per year for consumers. Open source code can be used for studying and allows capable end users to adapt software to their personal needs in a similar way user scripts ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Copyright Law Of Australia
The copyright law of Australia defines the legally enforceable rights of creators of creative and artistic works under Australian law. The scope of copyright in Australia is defined in the '' Copyright Act 1968'' (as amended), which applies the national law throughout Australia. Designs may be covered by the ''Copyright Act'' (as sculptures or drawings) as well as by the '' Design Act''. Since 2007, performers have moral rights in recordings of their work. Until 2004, copyright in Australia was based on the "plus 50" law which restricts works until 50 years after the author's death. In 2004 this was changed to a "plus 70" law in line with the USA and European Union, but this change was not made retroactive (unlike the 1995 change in the European Union which brought some, e.g. British authors, back into copyright). The consequence is that the work of an Australian author who died before 1955 is normally in the public domain in Australia. However the copyright of authors was exte ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
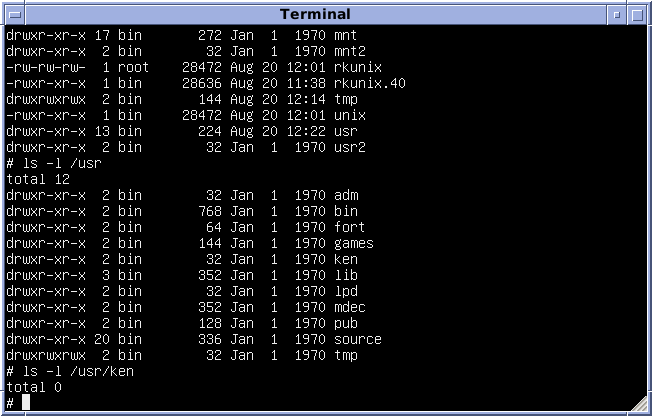
Version 7 Unix
Seventh Edition Unix, also called Version 7 Unix, Version 7 or just V7, was an important early release of the Unix operating system. V7, released in 1979, was the last Bell Laboratories release to see widespread distribution before the commercialization of Unix by AT&T Corporation in the early 1980s. V7 was originally developed for Digital Equipment Corporation's PDP-11 minicomputers and was later ported to other platforms. Overview Unix versions from Bell Labs were designated by the edition of the user's manual with which they were accompanied. Released in 1979, the Seventh Edition was preceded by Sixth Edition, which was the first version licensed to commercial users. Development of the Research Unix line continued with the Eighth Edition, which incorporated development from 4.1BSD, through the Tenth Edition, after which the Bell Labs researchers concentrated on developing Plan 9. V7 was the first readily portable version of Unix. As this was the era of minicomputers, w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Top Secret
Classified information is material that a government body deems to be sensitive information that must be protected. Access is restricted by law or regulation to particular groups of people with the necessary security clearance and need to know, and mishandling of the material can incur criminal penalties. A formal security clearance is required to view or handle classified material. The clearance process requires a satisfactory background investigation. Documents and other information must be properly marked "by the author" with one of several (hierarchical) levels of sensitivity—e.g. restricted, confidential, secret, and top secret. The choice of level is based on an impact assessment; governments have their own criteria, including how to determine the classification of an information asset and rules on how to protect information classified at each level. This process often includes security clearances for personnel handling the information. Some corporations and non-gove ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Western Electric
The Western Electric Company was an American electrical engineering and manufacturing company officially founded in 1869. A wholly owned subsidiary of American Telephone & Telegraph for most of its lifespan, it served as the primary equipment manufacturer, supplier, and purchasing agent for the Bell System from 1881 to 1984 when it was dismantled. The company was responsible for many technological innovations as well as developments in industrial management. History In 1856, George Shawk, a craftsman and telegraph maker, purchased an electrical engineering business in Cleveland, Ohio. In January, 1869, Shawk had partnered with Enos M. Barton in the former Western Union repair shop of Cleveland, to manufacture burglar, fire alarms, and other electrical items. Both men were former Western Union employees. Shawk, was the Cleveland shop foreman and Barton, was a Rochester, New York telegrapher. During this Shawk and Barton partnership, one customer was an inventor sourcing parts and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
History Of Unix
The history of Unix dates back to the mid-1960s, when the Massachusetts Institute of Technology, AT&T Bell Labs, and General Electric were jointly developing an experimental time-sharing operating system called Multics for the GE-645 mainframe. Multics introduced many innovations, but also had many problems. Bell Labs, frustrated by the size and complexity of Multics but not its aims, slowly pulled out of the project. Their last researchers to leave Multics – among them Ken Thompson, Dennis Ritchie, Doug McIlroy, and Joe Ossanna – decided to redo the work, but on a much smaller scale. APDF/ref> In 1979, Ritchie described the group's vision for Unix: 1960s In the late 1960s, Bell Labs was involved in a project with MIT and General Electric to develop a time-sharing system, called Multiplexed Information and Computing Service (Multics), allowing multiple users to access a mainframe simultaneously. Dissatisfied with the project's progress, Bell Labs management ultimatel ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Lions Commentary Unix
The lion (''Panthera leo'') is a large cat of the genus ''Panthera'' native to Africa and India. It has a muscular, broad-chested body; short, rounded head; round ears; and a hairy tuft at the end of its tail. It is sexually dimorphic; adult male lions are larger than females and have a prominent mane. It is a social species, forming groups called ''prides''. A lion's pride consists of a few adult males, related females, and cubs. Groups of female lions usually hunt together, preying mostly on large ungulates. The lion is an apex and keystone predator; although some lions scavenge when opportunities occur and have been known to hunt humans, lions typically don't actively seek out and prey on humans. The lion inhabits grasslands, savannas and shrublands. It is usually more diurnal than other wild cats, but when persecuted, it adapts to being active at night and at twilight. During the Neolithic period, the lion ranged throughout Africa and Eurasia from Southeast Europe to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |