|
Kerckhoffs's Principle
Kerckhoffs's principle (also called Kerckhoffs's desideratum, assumption, axiom, doctrine or law) of cryptography was stated by Dutch-born cryptographer Auguste Kerckhoffs in the 19th century. The principle holds that a cryptosystem should be secure, even if everything about the system, except the key, is public knowledge. This concept is widely embraced by cryptographers, in contrast to security through obscurity, which is not. Kerckhoffs's principle was phrased by American mathematician Claude Shannon as "the enemy knows the system", i.e., "one ought to design systems under the assumption that the enemy will immediately gain full familiarity with them". In that form, it is called Shannon's maxim. Another formulation by American researcher and professor Steven M. Bellovin is: In other words — design your system assuming that your opponents know it in detail. (A former official at NSA's National Computer Security Center told me that the standard assumption there was that ser ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptography
Cryptography, or cryptology (from grc, , translit=kryptós "hidden, secret"; and ''graphein'', "to write", or ''-logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of adversarial behavior. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security ( data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, chip-based payment cards, digital currencies, computer passwords, and military communications. Cryptography prior to the modern age was effectively synonymo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Memory Dump
In computing, a core dump, memory dump, crash dump, storage dump, system dump, or ABEND dump consists of the recorded state of the working memory of a computer program at a specific time, generally when the program has crashed or otherwise terminated abnormally. In practice, other key pieces of program state are usually dumped at the same time, including the processor registers, which may include the program counter The program counter (PC), commonly called the instruction pointer (IP) in Intel x86 and Itanium microprocessors, and sometimes called the instruction address register (IAR), the instruction counter, or just part of the instruction sequencer, is ... and stack pointer, memory management information, and other processor and operating system flags and information. A snapshot dump (or snap dump) is a memory dump requested by the computer operator or by the running program, after which the program is able to continue. Core dumps are often used to assist in diagnosing and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Engineering Task Force
The Internet Engineering Task Force (IETF) is a standards organization for the Internet and is responsible for the technical standards that make up the Internet protocol suite (TCP/IP). It has no formal membership roster or requirements and all its participants are volunteers. Their work is usually funded by employers or other sponsors. The IETF was initially supported by the federal government of the United States but since 1993 has operated under the auspices of the Internet Society, an international non-profit organization. Organization The IETF is organized into a large number of working groups and birds of a feather informal discussion groups, each dealing with a specific topic. The IETF operates in a bottom-up task creation mode, largely driven by these working groups. Each working group has an appointed chairperson (or sometimes several co-chairs); a charter that describes its focus; and what it is expected to produce, and when. It is open to all who want to particip ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Randy Bush (scientist)
Randy Bush is a member of technical staff at Arrcus and a research fellow at Internet Initiative Japan. He was among the inaugural inductees into the Internet Hall of Fame in 2012, given by the Internet Society. Career Bush has been working in the computer industry since 1966. He began with Languages and Compilers but for the past few decades has been working in the Internet industry. Bush was the senior engineer of the Verio founding team in the late 1990s, and worked there for five years as the Vice President of IP Networking. He was the Principal Engineer at RAINet in the early 90s, which was later acquired by Verio at which time he joined Verio. He was the founder of the Network Startup Resource Center and worked there as a PI. Bush has served as a member of the IESG. At APNIC, he has been the Routing SIG Co-Chair, Policy SIG Co-Chair, and the Fees Working Group Chair. He was on the founding board of ARIN, helped start AFRINIC, NANOG, etc. He was the chair of the ACM Inter ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Content Scramble System
The Content Scramble System (CSS) is a digital rights management (DRM) and encryption system employed on many commercially produced DVD-Video discs. CSS utilizes a proprietary 40-bit stream cipher algorithm. The system was introduced around 1996 and was first compromised in 1999. CSS is one of several complementary systems designed to restrict DVD-Video access. It has been superseded by newer DRM schemes such as Content Protection for Recordable Media (CPRM), or by Advanced Encryption Standard (AES) in the Advanced Access Content System (AACS) DRM scheme used by HD DVD and Blu-ray Disc, which have 56-bit and 128-bit key sizes, respectively, providing a much higher level of security than the less secure 40-bit key size of CSS. Preliminary note The content scramble system (CSS) is a collection of proprietary protection mechanisms for DVD-Video discs. CSS attempts to restrict access to the content only for licensed applications. According to the DVD Copy Control Association (CCA ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Type 1 Encryption
The U.S. National Security Agency (NSA) used to rank cryptographic products or algorithms by a certification called product types. Product types were defined in the National Information Assurance Glossary (CNSSI No. 4009, 2010) which used to define Type 1, 2, 3, and 4 products. The definitions of numeric type products have been removed from the government lexicon and are no longer used in government procurement efforts. Type 1 product A Type 1 product was a device or system certified by NSA for use in cryptographically securing classified U.S. Government information. A Type 1 product was defined as: Cryptographic equipment, assembly or component classified or certified by NSA for encrypting and decrypting classified and sensitive national security information when appropriately keyed. Developed using established NSA business processes and containing NSA approved algorithms. Used to protect systems requiring the most stringent protection mechanisms. They were available to U.S. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
The Atlantic Monthly
''The Atlantic'' is an American magazine and multi-platform publisher. It features articles in the fields of politics, foreign affairs, business and the economy, culture and the arts, technology, and science. It was founded in 1857 in Boston, as ''The Atlantic Monthly'', a literary and cultural magazine that published leading writers' commentary on education, the abolition of slavery, and other major political issues of that time. Its founders included Francis H. Underwood and prominent writers Ralph Waldo Emerson, Oliver Wendell Holmes Sr., Henry Wadsworth Longfellow, Harriet Beecher Stowe, and John Greenleaf Whittier. James Russell Lowell was its first editor. In addition, ''The Atlantic Monthly Almanac'' was an annual almanac published for ''Atlantic Monthly'' readers during the 19th and 20th centuries. A change of name was not officially announced when the format first changed from a strict monthly (appearing 12 times a year) to a slightly lower frequency. It was a monthly ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
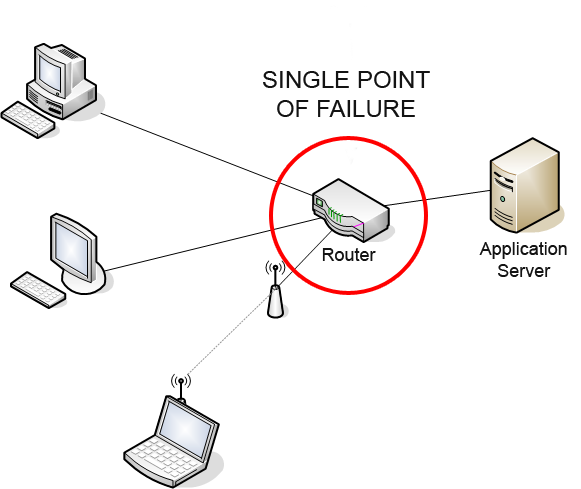
Single Point Of Failure
A single point of failure (SPOF) is a part of a system that, if it fails, will stop the entire system from working. SPOFs are undesirable in any system with a goal of high availability or reliability, be it a business practice, software application, or other industrial system. Overview Systems can be made robust by adding redundancy in all potential SPOFs. Redundancy can be achieved at various levels. The assessment of a potential SPOF involves identifying the critical components of a complex system that would provoke a total systems failure in case of malfunction. Highly reliable systems should not rely on any such individual component. For instance, the owner of a small tree care company may only own one woodchipper. If the chipper breaks, he may be unable to complete his current job and may have to cancel future jobs until he can obtain a replacement. The owner of the tree care company may have spare parts ready for the repair of the wood chipper, in case it fails. At ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Graceful Exit
A graceful exit (or graceful handling) is a simple programming idiom wherein a program detects a serious error condition and "exits gracefully" in a controlled manner as a result. Often the program prints a descriptive error message to a terminal or log as part of the graceful exit. Usually, code for a graceful exit exists when the alternative — allowing the error to go undetected and unhandled — would produce spurious errors or later anomalous behavior that would be more difficult for the programmer to debug. The code associated with a graceful exit may also take additional steps, such as closing files, to ensure that the program leaves data in a consistent, recoverable state. Graceful exits are not always desired. In many cases, an outright crash can give the software developer the opportunity to attach a debugger or collect important information, such as a core dump or stack trace, to diagnose the root cause of the error. In a language that supports formal exception hand ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bruce Schneier
Bruce Schneier (; born January 15, 1963) is an American cryptographer, computer security professional, privacy specialist, and writer. Schneier is a Lecturer in Public Policy at the Harvard Kennedy School and a Fellow at the Berkman Klein Center for Internet & Society as of November, 2013. He is a board member of the Electronic Frontier Foundation, Access Now, and The Tor Project; and an advisory board member of Electronic Privacy Information Center and VerifiedVoting.org. He is the author of several books on general security topics, computer security and cryptography and is a squid enthusiast. In 2015, Schneier received the EPIC Lifetime Achievement Award from Electronic Privacy Information Center. Early life Bruce Schneier is the son of Martin Schneier, a Brooklyn Supreme Court judge. He grew up in the Flatbush neighborhood of Brooklyn, New York, attending P.S. 139 and Hunter College High School. After receiving a physics bachelor's degree from the University of Roche ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Steganographic
Steganography ( ) is the practice of representing information within another message or physical object, in such a manner that the presence of the information is not evident to human inspection. In computing/electronic contexts, a computer file, message, image, or video is concealed within another file, message, image, or video. The word ''steganography'' comes from Greek ''steganographia'', which combines the words ''steganós'' (), meaning "covered or concealed", and ''-graphia'' () meaning "writing". The first recorded use of the term was in 1499 by Johannes Trithemius in his '' Steganographia'', a treatise on cryptography and steganography, disguised as a book on magic. Generally, the hidden messages appear to be (or to be part of) something else: images, articles, shopping lists, or some other cover text. For example, the hidden message may be in invisible ink between the visible lines of a private letter. Some implementations of steganography that lack a shared secret are f ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Dutch People
The Dutch (Dutch: ) are an ethnic group and nation native to the Netherlands. They share a common history and culture and speak the Dutch language. Dutch people and their descendants are found in migrant communities worldwide, notably in Aruba, Suriname, Guyana, Curaçao, Argentina, Brazil, Canada,Based on Statistics Canada, Canada 2001 Censusbr>Linkto Canadian statistics. Australia, South Africa, New Zealand and the United States.According tFactfinder.census.gov The Low Countries were situated around the border of France and the Holy Roman Empire, forming a part of their respective peripheries and the various territories of which they consisted had become virtually autonomous by the 13th century. Under the Habsburgs, the Netherlands were organised into a single administrative unit, and in the 16th and 17th centuries the Northern Netherlands gained independence from Spain as the Dutch Republic. The high degree of urbanization characteristic of Dutch society was attained at a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |

.jpg)