|
Internet Censorship In Switzerland
Internet censorship in Switzerland is regulated by the Federal Supreme Court of Switzerland on a case by case basis. Internet services provided by the registered with BAKOM Internet service providers (ISPs) are subject to a "voluntary recommendation" by the Federal Supreme Court of Switzerland, which requires blocking of websites just after 18 December 2007. , this might change soon and additional topics like Online gambling are on the focus now. History There were no government restrictions on access to the Internet or credible reports that the government monitored e-mail or Internet chat rooms without appropriate legal authority."Switzerland" ''Country Reports on Human Rights Practices for 2012'', Bureau of Democracy, Human Rights and Labor, U.S. Department of State. Retrie ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Federal Supreme Court Of Switzerland
The Federal Supreme Court of Switzerland (german: Bundesgericht, french: Tribunal fédéral, it, Tribunale federale, rm, ) is the supreme court of the Swiss Confederation and at the head of the Swiss judiciary. The Federal Supreme Court is headquartered in the Federal Courthouse in Lausanne in the canton of Vaud. The two social security divisions of the Federal Supreme Court (formerly Federal Insurance Court, as an organizationally independent unit of the Federal Supreme Court), are located in Lucerne. The Federal Assembly elects 38 justices to the Federal Supreme Court. The current president of the court is Martha Niquille. Functions The Federal Supreme Court is the final arbiter on disputes in the field of civil law (citizens-citizens), the public arena (citizen-state), as well as in disputes between cantons or between cantons and the Confederation. The Supreme Court's decisions in the field of human rights violations can be appealed to the European Court of Human Rig ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Vidalia Project
Vidalia is a discontinued cross-platform GUI for controlling Tor, built using Qt. The name comes from the Vidalia onion since Tor uses onion routing. It allows the user to start, stop or view the status of Tor, view, filter or search log messages, monitor bandwidth usage, and configure some aspects of Tor. Vidalia also makes it easier to contribute to the Tor network by optionally helping the user set up a Tor relay. Another prominent feature of Vidalia is its Tor network map, which lets the user see the geographic location of relays on the Tor network, as well as where the user's application traffic is going. Vidalia is released under the GNU General Public License. It runs on any platform supported by Qt 4.2, including Windows, Mac OS X, and Linux or other Unix-like variants using the X11 window system. Vidalia is no longer maintained or supported, and Tor developers do not recommend its use anymore. In 2013 it was replaced with a Firefox Mozilla Firefox, or simply Fire ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Censorship By Country
This list of Internet censorship and surveillance by country provides information on the types and levels of Internet censorship and surveillance that is occurring in countries around the world. Classifications Detailed country by country information on Internet censorship and surveillance is provided in the ''Freedom on the Net'' reports from Freedom House, by the OpenNet Initiative, by Reporters Without Borders, and in the ''Country Reports on Human Rights Practices'' from the U.S. State Department Bureau of Democracy, Human Rights, and Labor. The ratings produced by several of these organizations are summarized below as well as in the Censorship by country article. ''Freedom on the Net'' reports The ''Freedom on the Net'' reports provide analytical reports and numerical ratings regarding the state of Internet freedom for countries worldwide. The countries surveyed represent a sample with a broad range of geographical diversity and levels of economic development, as well as var ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer And Network Surveillance
Computer and network surveillance is the monitoring of computer activity and data stored locally on a computer or data being transferred over computer networks such as the Internet. This monitoring is often carried out covertly and may be completed by governments, corporations, criminal organizations, or individuals. It may or may not be legal and may or may not require authorization from a court or other independent government agencies. Computer and network surveillance programs are widespread today and almost all Internet traffic can be monitored. Surveillance allows governments and other agencies to maintain social control, recognize and monitor threats or any suspicious or abnormal activity, and prevent and investigate criminal activities. With the advent of programs such as the Total Information Awareness program, technologies such as high-speed surveillance computers and biometrics software, and laws such as the Communications Assistance For Law Enforcement Act, governmen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Content-control Software
An Internet filter is software that restricts or controls the content an Internet user is capable to access, especially when utilized to restrict material delivered over the Internet via the Web, Email, or other means. Content-control software determines what content will be available or be blocked. Such restrictions can be applied at various levels: a government can attempt to apply them nationwide (see Internet censorship), or they can, for example, be applied by an Internet service provider to its clients, by an employer to its personnel, by a school to its students, by a library to its visitors, by a parent to a child's computer, or by an individual users to their own computers. The motive is often to prevent access to content which the computer's owner(s) or other authorities may consider objectionable. When imposed without the consent of the user, content control can be characterised as a form of internet censorship. Some content-control software includes time control func ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Global Internet Freedom Consortium
The Global Internet Freedom Consortium is a consortium of organizations that develop and deploy anti-censorship technologies for use by Internet users in countries whose governments restrict Web-based information access. The organization was reportedly begun in 2001 by Chinese-born scientists living in the United States reacting against Chinese government oppression of the Falun Gong. Products The main products are Freegate and Ultrasurf. Funding The organization states that the majority of its funding comes from its members. In May 2010, the group was offered a $1.5 million (USD) grant from the United States Department of State. This move received criticism from representatives of the Chinese government. See also *Human rights in the People's Republic of China *Internet censorship *Internet censorship in the People's Republic of China *Political repression of cyber-dissidents Political repression of cyber-dissidents is the oppression or persecution of people for expres ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Privacy
Internet privacy involves the right or mandate of personal privacy concerning the storing, re-purposing, provision to third parties, and displaying of information pertaining to oneself via Internet. Internet privacy is a subset of data privacy. Privacy concerns have been articulated from the beginnings of large-scale computer sharing. Privacy can entail either personally identifiable information (PII) or non-PII information such as a site visitor's behavior on a website. PII refers to any information that can be used to identify an individual. For example, age and physical address alone could identify who an individual is without explicitly disclosing their name, as these two factors are unique enough to identify a specific person typically. Other forms of PII may soon include GPS tracking data used by apps, as the daily commute and routine information can be enough to identify an individual. It has been suggested that the "appeal of online services is to broadcast personal infor ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
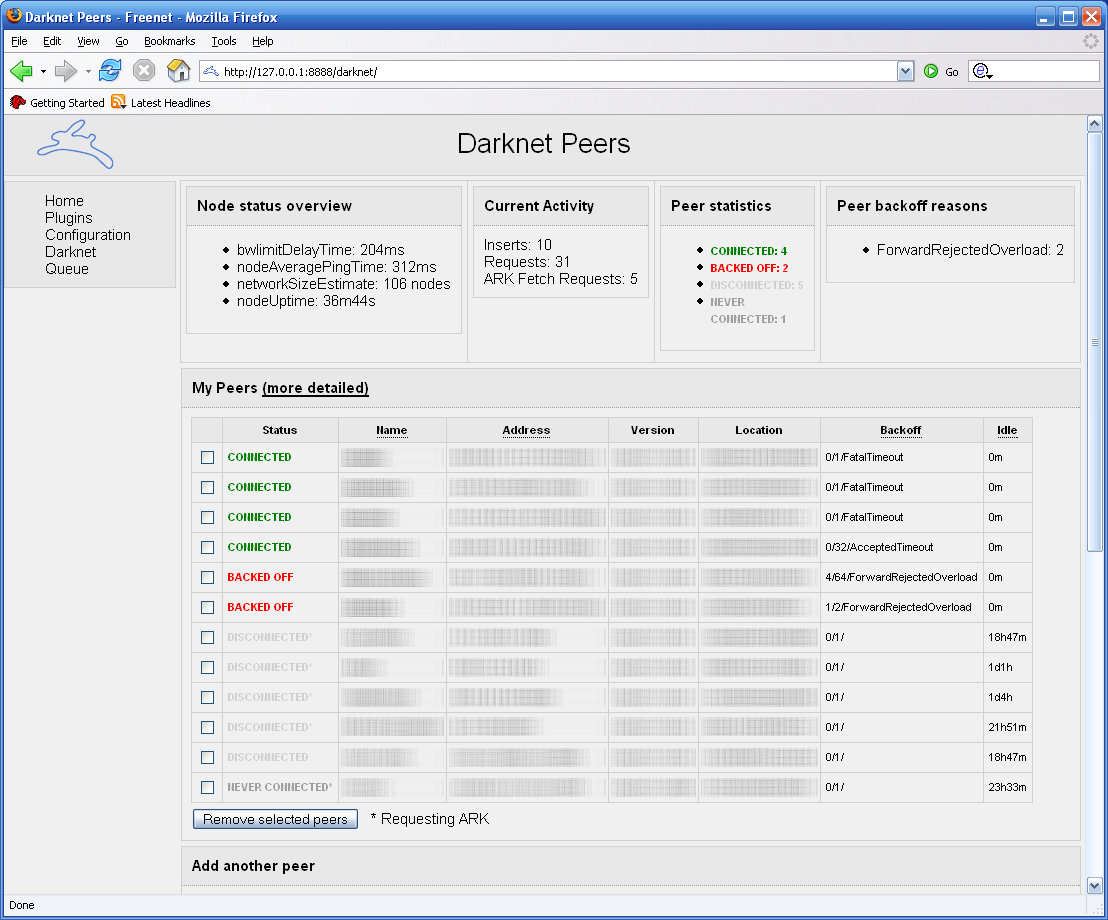
Freenet
Freenet is a peer-to-peer platform for censorship-resistant, anonymous communication. It uses a decentralized distributed data store to keep and deliver information, and has a suite of free software for publishing and communicating on the Web without fear of censorship.What is Freenet? , ''Freenet: The Free network official website''.Taylor, Ian J. ''From P2P to Web Services and Grids: Peers in a Client/Server World''. London: Springer, 2005. Both Freenet and some of its associated tools were originally designed by Ian Clarke, who defined Freenet's goal as providing |
Proxify
If you are looking for Proxify (Company) Proxify is a partly free, single-serving website that enables users to communicate more anonymously on the Internet. An example of this is to have Proxify use an SSH tunnel, already created and listening in on the localhost. This can be done using PuTTy to dynamically listen in to the host and redirecting traffic through the tunnel. Proxify is then used to hook applications into using the tunnel without configuring the different applications itself. Proxify matches its registration information with a WHOIS database, as reassurance. There are three general pre-configured options (max speed, max security, or compatibility) with users able to tweak the settings otherwise. Although free searches are offered, a message may appear: "Proxify is experiencing higher than normal traffic volume. We must restrict access to our free service during peak usage times to ensure the best possible experience for paid subscribers. Please login to your accoun ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
XB Browser
xB Browser (formerly known as TorPark and Xerobank browser) was a web browser designed to run on both the Tor and XeroBank anonymity networks, and is available as component of the xB Machine and the xB Installer. It is designed for use on portable media such as a USB flash drive, but it can also be used on any hard disk drive. As such, a secure and encrypted connection to any of the Tor or XeroBank routers can be created from any computer with a suitable Internet connection, and the browser clears all data that was created on the portable drive upon exit or on demand. In March 2007 it was reported that the xB Browser was downloaded 4 million times and in February 2008 over 6.5 million downloads making xB Browser the most popular anonymous browser on the Internet. History Steve Topletz co-released Torpark v.1.5.0.7 with CULT OF THE DEAD COW/Hacktivismo on 19 September 2006 after more than one year of development based on Portable Firefox web browser with built in support f ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tor (anonymity Network)
Tor, short for The Onion Router, is free and open-source software for enabling anonymous communication. It directs Internet traffic through a free, worldwide, volunteer overlay network, consisting of more than seven thousand relays, to conceal a user's location and usage from anyone performing network surveillance or traffic analysis. Using Tor makes it more difficult to trace a user's Internet activity. Tor's intended use is to protect the personal privacy of its users, as well as their freedom and ability to communicate confidentially through IP address anonymity using Tor exit nodes. History The core principle of Tor, onion routing, was developed in the mid-1990s by United States Naval Research Laboratory employees, mathematician Paul Syverson, and computer scientists Michael G. Reed and David Goldschlag, to protect American intelligence communications online. Onion routing is implemented by means of encryption in the application layer of the communication protocol stack ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |

.jpg)