|
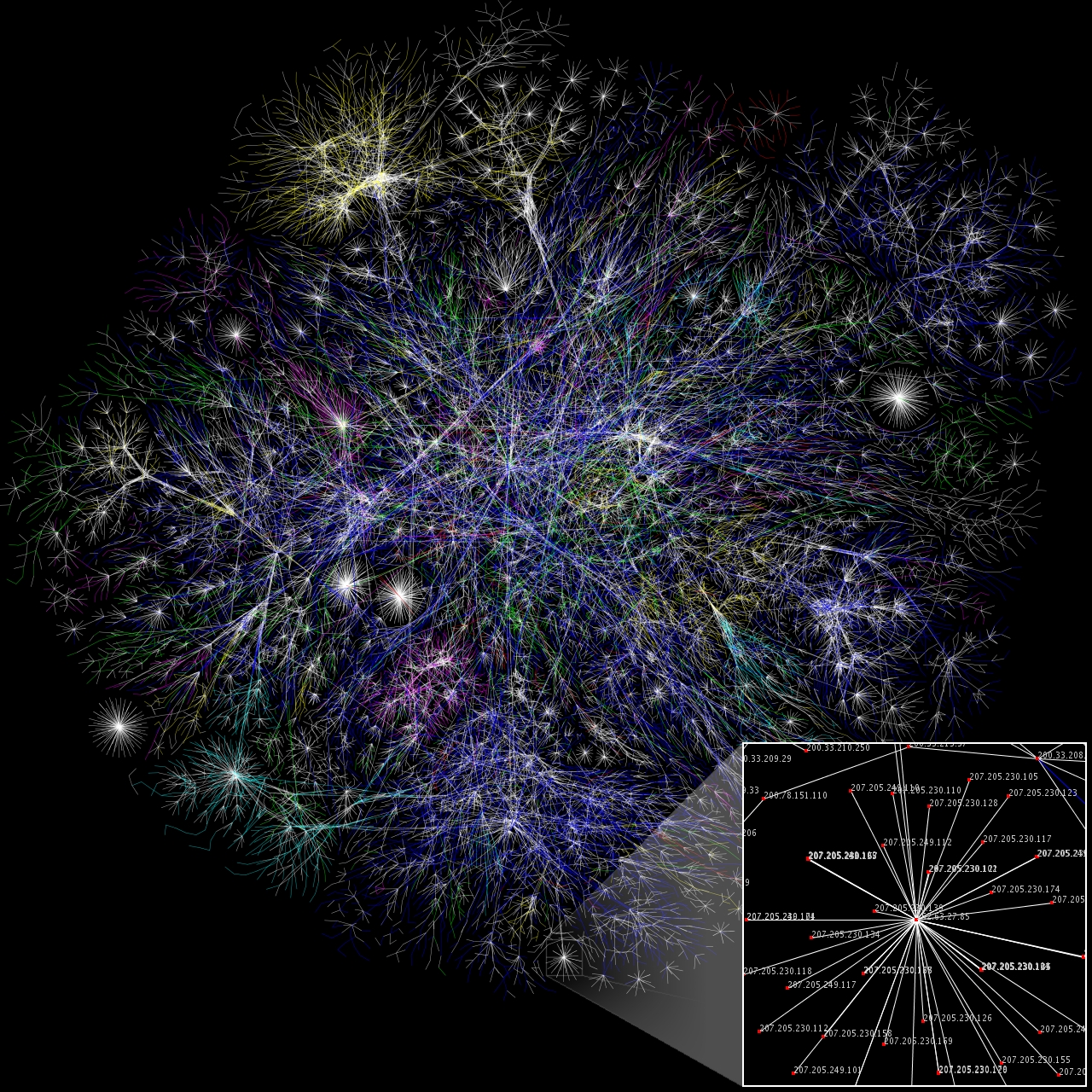
Internet Mapping Project
The Internet Mapping Project was started by William Cheswick and Hal Burch at Bell Labs in 1997. It has collected and preserved traceroute-style paths to some hundreds of thousands of networks almost daily since 1998. The project included visualization of the Internet data, and the Internet maps were widely disseminated. The technology is now used by Lumeta, a spinoff of Bell Labs, to map corporate and government networks. Although Cheswick left Lumeta in September 2006, Lumeta continues to map both the IPv4 and IPv6 Internet. The data allows for both a snapshot and view over time of the routed infrastructure of a particular geographical area, company, organization, etc. Cheswick continues to collect and preserve the data, and it is available for research purposes. According to Cheswick, a main goal of the project was to collect the data over time, and make a time-lapse movie of the growth of the Internet. Techniques The techniques available for network discovery rely on h ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Map 1024
The Internet (or internet) is the global system of interconnected computer networks that uses the Internet protocol suite (TCP/IP) to communicate between networks and devices. It is a '' network of networks'' that consists of private, public, academic, business, and government networks of local to global scope, linked by a broad array of electronic, wireless, and optical networking technologies. The Internet carries a vast range of information resources and services, such as the inter-linked hypertext documents and applications of the World Wide Web (WWW), electronic mail, telephony, and file sharing. The origins of the Internet date back to the development of packet switching and research commissioned by the United States Department of Defense in the 1960s to enable time-sharing of computers. The primary precursor network, the ARPANET, initially served as a backbone for interconnection of regional academic and military networks in the 1970s to enable resource sharing. T ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Control Message Protocol
The Internet Control Message Protocol (ICMP) is a supporting protocol in the Internet protocol suite. It is used by network devices, including routers, to send error messages and operational information indicating success or failure when communicating with another IP address, for example, an error is indicated when a requested service is not available or that a host or router could not be reached. ICMP differs from transport protocols such as TCP and UDP in that it is not typically used to exchange data between systems, nor is it regularly employed by end-user network applications (with the exception of some diagnostic tools like ping and traceroute). ICMP for IPv4 is defined in RFC 792. A separate ICMPv6, defined by RFC 4443, is used with IPv6. Technical details ICMP is part of the Internet protocol suite as defined in RFC 792. ICMP messages are typically used for diagnostic or control purposes or generated in response to errors in IP operations (as specified in RFC 1122 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Route Analytics
Network monitoring is the use of a system that constantly monitors a computer network for slow or failing components and that notifies the network administrator (via email, SMS or other alarms) in case of outages or other trouble. Network monitoring is part of network management. Details While an intrusion detection system monitors a network threats from the outside, a network monitoring system monitors the network for problems caused by overloaded or crashed servers, network connections or other devices. For example, to determine the status of a web server, monitoring software may periodically send an HTTP request to fetch a page. For email servers, a test message might be sent through SMTP and retrieved by IMAP or POP3. Commonly measured metrics are response time, availability and uptime, although both consistency and reliability metrics are starting to gain popularity. The widespread addition of WAN optimization devices is having an adverse effect on most network monitoring to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Mapping
Network mapping is the study of the physical connectivity of networks e.g. the Internet. Network mapping discovers the devices on the network and their connectivity. It is not to be confused with network discovery or Network enumeration, network enumerating which discovers devices on the network and their characteristics such as (operating system, open Computer port (software), ports, listening network services, etc.). The field of automated network mapping has taken on greater importance as networks become more dynamic and complex in nature. Large-scale mapping project Images of some of the first attempts at a large scale map of the internet were produced by the Internet Mapping Project and appeared in ''Wired (magazine), Wired'' magazine. The maps produced by this project were based on the Network Layer, layer 3 or Internet Protocol, IP level connectivity of the Internet (see OSI model), but there are different aspects of internet structure that have also been mapped. More rec ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wired Magazine
''Wired'' (stylized as ''WIRED'') is a monthly American magazine, published in print and online magazine, online editions, that focuses on how emerging technologies affect culture, the economy, and politics. Owned by Condé Nast, it is headquartered in San Francisco, California, and has been in publication since March/April 1993. Several spin-offs have been launched, including ''Wired UK'', ''Wired Italia'', ''Wired Japan'', and ''Wired Germany''. From its beginning, the strongest influence on the magazine's editorial outlook came from founding editor and publisher Louis Rossetto. With founding creative director John Plunkett, Rossetto in 1991 assembled a 12-page prototype, nearly all of whose ideas were realized in the magazine's first several issues. In its earliest colophon (publishing), colophons, ''Wired'' credited Canadian media theorist Marshall McLuhan as its "patron saint". ''Wired'' went on to chronicle the evolution of digital technology and its impact on society. ' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Kevin Kelly (editor)
Kevin Kelly (born 1952) is the founding executive editor of ''Wired'' magazine, and a former editor/publisher of the ''Whole Earth Review''. He has also been a writer, photographer, conservationist, and student of Asian and digital culture. Life Kelly was born in Pennsylvania in 1952, and graduated from Westfield High School, Westfield, New Jersey, in 1970. Through his father, an executive for ''Time'' who used systems analysis in his work, Kelly developed an early interest in cybernetics. He attended the University of Rhode Island for one year, studying geology. Kelly has traveled extensively, backpacking in Asia. While travelling in the Middle East, he had a conversion experience and became a born-again Christian. He was raised Catholic. He lives in Pacifica, California, a small coastal town just south of San Francisco. He is married to the biochemist Gia-Miin Fuh and has three children: Kaileen, Ting, and Tywen. He regrets not having a fourth child. Among Kelly's perso ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Border Gateway Protocol
Border Gateway Protocol (BGP) is a standardized exterior gateway protocol designed to exchange routing and reachability information among autonomous systems (AS) on the Internet. BGP is classified as a path-vector routing protocol, and it makes routing decisions based on paths, network policies, or rule-sets configured by a network administrator. BGP used for routing within an autonomous system is called Interior Border Gateway Protocol, Internal BGP (iBGP). In contrast, the Internet application of the protocol is called Exterior Border Gateway Protocol, External BGP (eBGP). History The Border Gateway Protocol was sketched out in 1989 by engineers on the back of "three ketchup-stained napkins", and is still known as the ''three-napkin protocol''. It was first described in 1989 in RFC 1105, and has been in use on the Internet since 1994. IPv6 BGP was first defined in in 1994, and it was improved to in 1998. The current version of BGP is version 4 (BGP4), which was publishe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Opte Project
The Opte Project, created in 2003 by Barrett Lyon, seeks to generate an accurate representation of the breadth of the Internet using visual graphics. Lyon believes that his network mapping can help teach students more about the Internet while also acting as a gauge illustrating both overall Internet growth and the specific areas where that growth occurs. It was not the first such project; others predated it, such as the Bell Labs Internet Mapping Project. Lyon has been generating image maps using traceroute, and later switched to mapping using BGP routes. The generated images were published on the Opte Project website. In 2021, Lyon created different vdeo animations, using his mapping technique: shedding light on internet growth between 1997 and 2021, the Iranian internet shutdown of 2019, the United States Department of Defense's place on the internet as well as the few entry points into the Chinese internet. The project has gathered notice worldwide having been featured by ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Topology
Network topology is the arrangement of the elements ( links, nodes, etc.) of a communication network. Network topology can be used to define or describe the arrangement of various types of telecommunication networks, including command and control radio networks, industrial fieldbusses and computer networks. Network topology is the topological structure of a network and may be depicted physically or logically. It is an application of graph theory wherein communicating devices are modeled as nodes and the connections between the devices are modeled as links or lines between the nodes. Physical topology is the placement of the various components of a network (e.g., device location and cable installation), while logical topology illustrates how data flows within a network. Distances between nodes, physical interconnections, transmission rates, or signal types may differ between two different networks, yet their logical topologies may be identical. A network’s physical topology is ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Center For Applied Internet Data Analysis
The San Diego Supercomputer Center (SDSC) is an organized research unit of the University of California, San Diego (UCSD). SDSC is located at the UCSD campus' Eleanor Roosevelt College east end, immediately north the Hopkins Parking Structure. The current SDSC director is Michael L. Norman, UCSD physics professor, who succeeded noted grid computing pioneer Francine Berman. He was named director September 2010, having been interim director more than a year. SDSC was founded in 1985 and describes its mission as "developing and using technology to advance science." The SDSC was one of the five original NSF Supercomputing Centers and the National Science Foundation (NSF) continues to be a primary funder of the SDSC. Its research pursuits are high performance computing, grid computing, computational biology, geoinformatics, computational physics, computational chemistry, data management, scientific visualization, and computer networking. SDSC computational biosciences contribu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Time To Live
Time to live (TTL) or hop limit is a mechanism which limits the lifespan or lifetime of data in a computer or network. TTL may be implemented as a counter or timestamp attached to or embedded in the data. Once the prescribed event count or timespan has elapsed, data is discarded or revalidated. In computer networking, TTL prevents a data packet from circulating indefinitely. In computing applications, TTL is commonly used to improve the performance and manage the caching of data. Description The original DARPA Internet Protocol's RFC document describes TTL as: IP packets Under the Internet Protocol, TTL is an 8-bit field. In the IPv4 header, TTL is the 9th octet of 20. In the IPv6 header, it is the 8th octet of 40. The maximum TTL value is 255, the maximum value of a single octet. A recommended initial value is 64. The time-to-live value can be thought of as an upper bound on the time that an IP datagram can exist in an Internet system. The TTL field is set by the sender ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
William Cheswick
William R. "Bill" Cheswick (also known as "Ches") is a computer security and networking researcher. Education Cheswick graduated from Lawrenceville School in 1970 and received a B.S. in Fundamental Science in 1975 from Lehigh University. While at Lehigh, working with Doug Price and Steve Lidie, Cheswick co-authored the Senator line-oriented text editor. Career Cheswick's early career included contracting in Bethlehem, PA between 1975 and 1977. He was a Programmer for American Newspaper Publishers Association / Research Institute in Easton, PA between 1976 and 1977 and a Systems Programmer for Computer Sciences Corporation in Warminster, PA between 1977 and 1978. Following this, Cheswick joined Systems and Computer Technology Corporation where he served as a Systems Programmer and Consultant between 1978 and 1987. Much of Cheswick's early career was related to his expertise with Control Data Corporation (CDC) mainframes, their operating systems such as SCOPE and NOS, and the rela ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |