|
Infrastructure Security
Infrastructure security is the security provided to protect infrastructure, especially critical infrastructure, such as airports, highways rail transport, hospitals, bridges, transport hubs, network communications, media, the electricity grid, dams, power plants, seaports, oil refineries, and water systems. Infrastructure security seeks to limit vulnerability of these structures and systems to sabotage, terrorism, and contamination. Critical infrastructures naturally utilize information technology as this capability has become more and more available. As a result, they have become highly interconnected, and interdependent. Intrusions and disruptions in one infrastructure might provoke unexpected failures in others, which makes handing interdependencies a key concern. There are several examples where an incident at one critical infrastructure site affects others. For example, in 2003, the Northeastern American areas experienced a power outage that appears to have or ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security
" \n\n\nsecurity.txt is a proposed standard for websites' security information that is meant to allow security researchers to easily report security vulnerabilities. The standard prescribes a text file called \"security.txt\" in the well known location, similar in syntax to robots.txt but intended to be machine- and human-readable, for those wishing to contact a website's owner about security issues. security.txt files have been adopted by Google, GitHub, LinkedIn, and Facebook.\n History \n\nThe Internet Draft was first submitted by Edwin Foudil in September 2017. At that time it covered four directives, \"Contact\", \"Encryption\", \"Disclosure\" and \"Acknowledgement\". Foudil expected to add further directives based on feedback. In addition, web security expert Scott Helme said he had seen positive feedback from the security community while use among the top 1 million websites was \"as low as expected right now\".\n\nIn 2019, the Cybersecurity and Infrastructure Security Agenc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Contamination
Contamination is the presence of a constituent, impurity, or some other undesirable element that spoils, corrupts, infects, makes unfit, or makes inferior a material, physical body, natural environment, workplace, etc. Types of contamination Within the sciences, the word "contamination" can take on a variety of subtle differences in meaning, whether the contaminant is a solid or a liquid, as well as the variance of environment the contaminant is found to be in. A contaminant may even be more abstract, as in the case of an unwanted energy source that may interfere with a process. The following represent examples of different types of contamination based on these and other variances. Chemical contamination In chemistry, the term "contamination" usually describes a single constituent, but in specialized fields the term can also mean chemical mixtures, even up to the level of cellular materials. All chemicals contain some level of impurity. Contamination may be recognized or no ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hurricane Ike
Hurricane Ike () was a powerful tropical cyclone that swept through portions of the Greater Antilles and Northern America in September 2008, wreaking havoc on infrastructure and agriculture, particularly in Cuba and Texas. Ike took a similar track to the 1900 Galveston hurricane. The ninth tropical storm, fifth hurricane, and third major hurricane of the 2008 Atlantic hurricane season, Ike developed from a tropical wave west of Cape Verde on September 1 and strengthened to a peak intensity as a List of Category 4 Atlantic hurricanes, Category 4 hurricane over the open waters of the central Atlantic on September 4 as it tracked westward. Several fluctuations in strength occurred before Ike made landfall (meteorology), landfall on eastern Cuba on September 8. The hurricane weakened prior to continuing into the Gulf of Mexico, but increased its intensity by the time of its final landfall in Galveston, Texas, on September 13 before becoming an ext ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
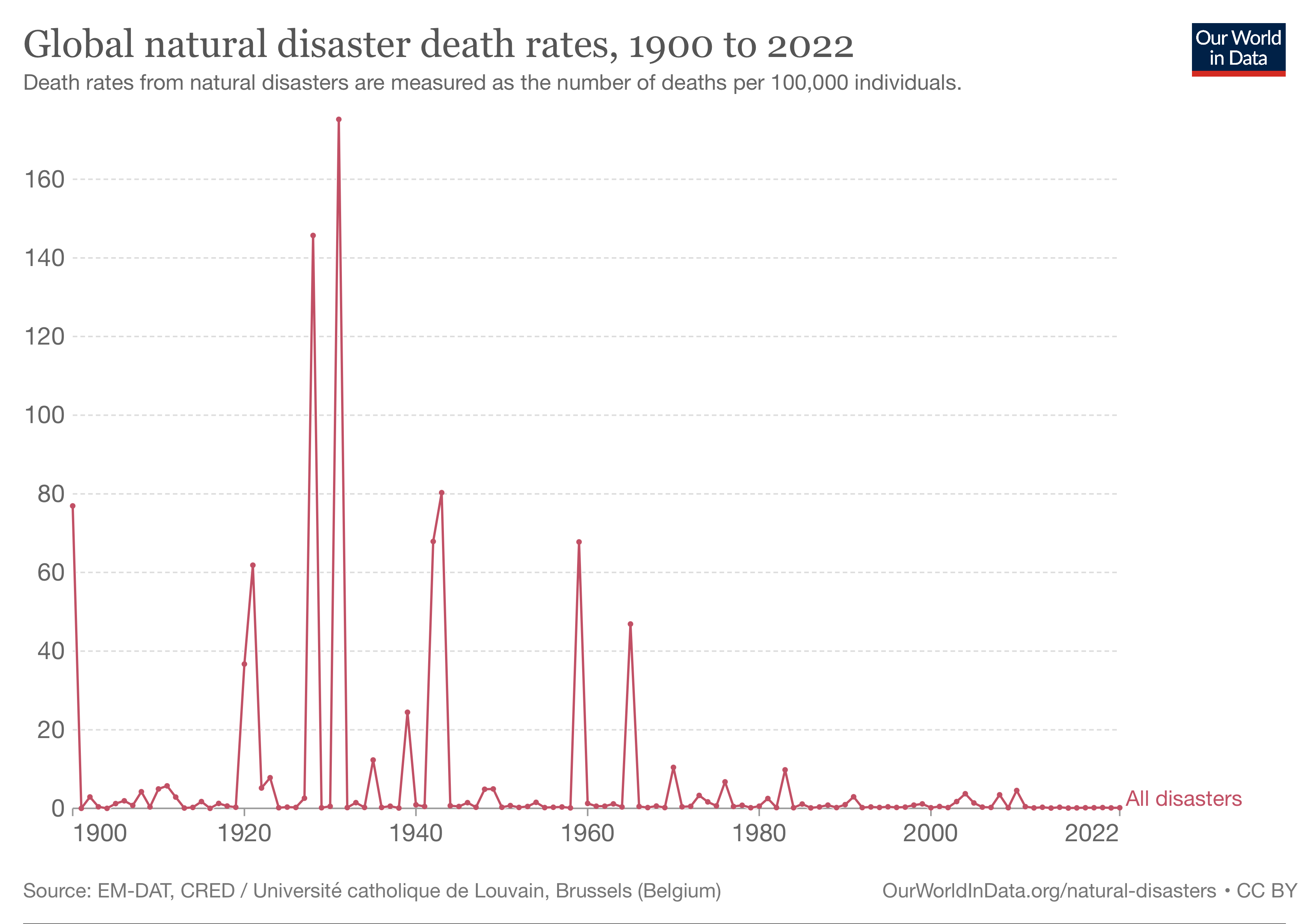
Natural Disaster
A natural disaster is "the negative impact following an actual occurrence of natural hazard in the event that it significantly harms a community". A natural disaster can cause loss of life or damage property, and typically leaves some economic damage in its wake. The severity of the damage depends on the affected population's resilience and on the infrastructure available. Examples of natural hazards include: avalanche, coastal flooding, cold wave, drought, earthquake, hail, heat wave, hurricane ( tropical cyclone), ice storm, landslide, lightning, riverine flooding, strong wind, tornado, typhoon, tsunami, volcanic activity, wildfire, winter weather. In modern times, the divide between natural, man-made and man-accelerated disasters is quite difficult to draw. Human choices and activities like architecture, fire, resource management or even climate change potentially play a role in causing "natural disasters". In fact, the term "natural disaster" has been calle ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cyberattacks During The 2008 South Ossetia War
During the Russo-Georgian War a series of cyberattacks swamped and disabled websites of numerous South Ossetian, Georgian, Russian and Azerbaijani organisations. The attacks were initiated three weeks before the shooting war began. Attacks On 20 July 2008, weeks before the Russian invasion of Georgia, "zombie" computers were already on the attack against Georgia. The website of the Georgian president Mikheil Saakashvili was targeted, resulting in overloading the site. The traffic directed at the website included the phrase "win+love+in+Rusia". The site then was taken down for 24 hours. On 5 August 2008, the websites for OSInform News Agency and OSRadio were hacked. The OSinform website at osinform.ru kept its header and logo, but its content was replaced by the content of Alania TV website. Alania TV, a Georgian government supported television station aimed at audiences in South Ossetia, denied any involvement in the hacking of the rival news agency website. Dmitry Medoy ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
2007 Cyberattacks On Estonia
Beginning on 27 April 2007, a series of cyberattacks targeted websites of Estonian organizations, including Estonian parliament, banks, ministries, newspapers and broadcasters, amid the country's disagreement with Russia about the relocation of the Bronze Soldier of Tallinn, an elaborate Soviet-era grave marker, as well as war graves in Tallinn. Most of the attacks that had any influence on the general public were distributed denial of service type attacks ranging from single individuals using various methods like ping floods to expensive rentals of botnets usually used for spam distribution. Spamming of bigger news portals commentaries and defacements including that of the Estonian Reform Party website also occurred. Research has also shown that large conflicts took place to edit the English-language version of the Bronze Soldier's Wikipedia page. Some observers reckoned that the onslaught on Estonia was of a sophistication not seen before. The case is studied intensively by ma ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Warfare
Information warfare (IW) (as different from cyber warfare that attacks computers, software, and command control systems) is a concept involving the battlespace use and management of information and communication technology (ICT) in pursuit of a competitive advantage over an opponent. Information warfare is the manipulation of information trusted by a target without the target's awareness so that the target will make decisions against their interest but in the interest of the one conducting information warfare. As a result, it is not clear when information warfare begins, ends, and how strong or destructive it is. Information warfare may involve the collection of tactical information, assurance(s) that one's information is valid, spreading of propaganda or disinformation to demoralize or manipulate the enemy and the public, undermining the quality of the opposing force's information and denial of information-collection opportunities to opposing forces. Information warfare is ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
People's Alliance For Democracy
The People's Alliance for Democracy (PAD; th, พันธมิตรประชาชนเพื่อประชาธิปไตย, Phanthamit Prachachon Pheu Prachathipatai; commonly known as "Yellow Shirts") is a Thai reactionary, monarchist political movement and pressure group. It was originally a coalition of protesters against Thaksin Shinawatra, the former Prime Minister of Thailand. Its leaders included media-mogul Sondhi Limthongkul and Major General Chamlong Srimuang. The PAD was a chief player in the political crisis of 2005–2006, the 2008 crisis, and the Cambodian–Thai border stand-off. Its membership consisted mainly of ultra-royalist middle-class and working-class Bangkok residents and anti-Thaksin Southerners, supported by some factions of the Thai Army, some leaders of Democrat Party, and the members of the state-enterprise labor unions. Name The movement is also called the National Liberation Alliance (กลุ่มพันธมิ� ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Sabotage
Sabotage is a deliberate action aimed at weakening a polity, effort, or organization through subversion, obstruction, disruption, or destruction. One who engages in sabotage is a ''saboteur''. Saboteurs typically try to conceal their identities because of the consequences of their actions and to avoid invoking legal and organizational requirements for addressing sabotage. Etymology The English word derives from the French word , meaning to "bungle, botch, wreck or sabotage"; it was originally used to refer to labour disputes, in which workers wearing wooden shoes called interrupted production through different means. A popular but incorrect account of the origin of the term's present meaning is the story that poor workers in the Belgian city of Liège would throw a wooden into the machines to disrupt production. One of the first appearances of and in French literature is in the of d'Hautel, edited in 1808. In it the literal definition is to 'make noise with sabots' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Metal Theft
Metal theft is "the theft of items for the value of their constituent metals". It usually increases when worldwide prices for scrap metal rise, as has happened dramatically due to rapid industrialization in India and China. Apart from precious metals like gold and silver, the metals most commonly stolen are non-ferrous metals such as copper, aluminium, brass, and bronze. However, even cast iron and steel are seeing higher rates of theft due to increased scrap metal prices. One defining characteristic of metal theft is the motivation. Whereas other items are generally stolen for their extrinsic value, items involved in metal theft are stolen for their intrinsic value as raw material or commodities. Thefts often have negative consequences much greater than the value of the metal stolen, such as the destruction of valuable statues, power interruptions, and the disruption of railway traffic. Items often stolen Anything made of metal has value as scrap metal, and can be stolen: ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Theft
Theft is the act of taking another person's property or services without that person's permission or consent with the intent to deprive the rightful owner of it. The word ''theft'' is also used as a synonym or informal shorthand term for some crimes against property, such as larceny, robbery, embezzlement, extortion, blackmail, or receiving stolen property. In some jurisdictions, ''theft'' is considered to be synonymous with '' larceny'', while in others, ''theft'' is defined more narrowly. Someone who carries out an act of theft may be described as a "thief" ( : thieves). ''Theft'' is the name of a statutory offence in California, Canada, England and Wales, Hong Kong, Northern Ireland, the Republic of Ireland, and the Australian states of South Australia Theft (and receiving). and Victoria. Theft. Elements The '' actus reus'' of theft is usually defined as an unauthorized taking, keeping, or using of another's property which must be accompanied by a ''mens rea'' of di ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
November 2008 Mumbai Attacks
The 2008 Mumbai attacks (also referred to as 26/11, pronounced "twenty six eleven") were a series of terrorist attacks that took place in November 2008, when 10 members of Lashkar-e-Taiba, an Islamist terrorist organisation from Pakistan, carried out 12 coordinated shooting and bombing attacks lasting four days across Mumbai. The attacks, which drew widespread global condemnation, began on Wednesday 26 November and lasted until Saturday 29 November 2008. A total of 175 people died, including nine attackers, and more than 300 were wounded. Eight of the attacks occurred in South Mumbai: at Chhatrapati Shivaji Terminus, the Oberoi Trident, the Taj Palace & Tower, the Leopold Cafe, the Cama Hospital, the Nariman House, the Metro Cinema, and in a lane behind the ''Times of India'' building and St. Xavier's College. There was also an explosion at Mazagaon, in Mumbai's port area, and in a taxi at Vile Parle. By the early morning of 28 November, all sites except for the Taj Hotel ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |