|
Ident Protocol
The Ident Protocol (Identification Protocol, Ident), specified iRFC 1413 is an Internet protocol that helps identify the user of a particular TCP connection. One popular daemon program for providing the ident service is identd. Function The Ident Protocol is designed to work as a server daemon, on a user's computer, where it receives requests to a specified TCP port, generally 113. In the query, a client specifies a pair of TCP ports (a local and a remote port), encoded as ASCII decimals and separated by a comma (,). The server then sends a response that identifies the username of the user who runs the program that uses the specified pair of TCP ports, or specifies an error. Suppose host A wants to know the name of the user who is connecting to its TCP port 23 (Telnet) from the client's (host B) port 6191. Host A would then open a connection to the ident service on host B, and issue the following query: 6191, 23 As TCP connections generally use one unique local port (619 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
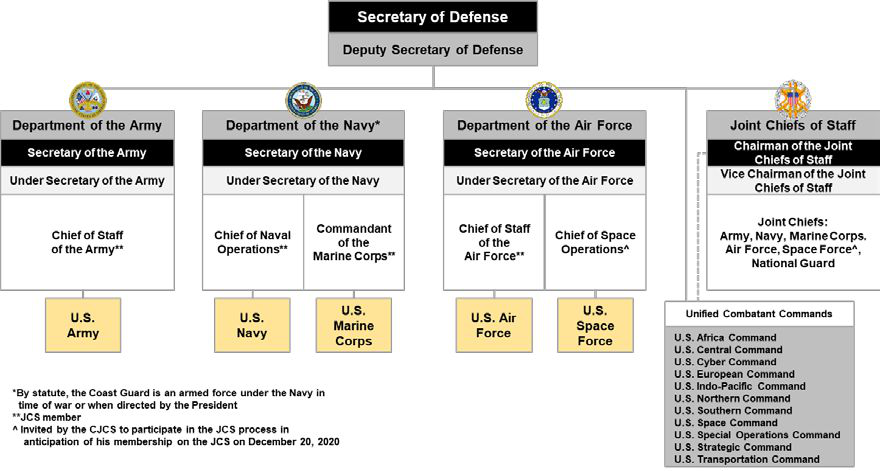
United States Department Of Defense
The United States Department of Defense (DoD, USDOD, or DOD) is an United States federal executive departments, executive department of the federal government of the United States, U.S. federal government charged with coordinating and supervising the six U.S. armed services: the United States Army, Army, United States Navy, Navy, United States Marine Corps, Marines, United States Air Force, Air Force, United States Space Force, Space Force, the United States Coast Guard, Coast Guard for some purposes, and related functions and agencies. As of November 2022, the department has over 1.4 million active-duty uniformed personnel in the six armed services. It also supervises over 778,000 National Guard (United States), National Guard and reservist personnel, and over 747,000 civilians, bringing the total to over 2.91 million employees. Headquartered at the Pentagon in Arlington County, Virginia, just outside Washington, D.C., the Department of Defense's stated mission is "to provid ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SuEXEC
Apache suEXEC is a feature of the Apache web server. It allows users to run Common Gateway Interface (CGI) and Server Side Includes (SSI) applications as a different user. Normally, all web server processes run as the default web server user (often wwwrun, www-data, apache or nobody). The suEXEC feature consists of a module for the web server and a binary executable which acts as a wrapper. suEXEC was introduced in Apache 1.2 and is often included in the default Apache package provided by most Linux distribution A Linux distribution, often abbreviated as distro, is an operating system that includes the Linux kernel for its kernel functionality. Although the name does not imply product distribution per se, a distro—if distributed on its own—is oft ...s. If a client requests a CGI and suEXEC is activated, it will call the suEXEC binary which then wraps the CGI scripts and executes it under the user account of the server process (virtual host) defined in the virtual hos ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Secure Shell
The Secure Shell Protocol (SSH Protocol) is a cryptographic network protocol for operating network services securely over an unsecured network. Its most notable applications are remote login and command-line execution. SSH was designed for Unix-like operating systems as a replacement for Telnet and unsecured remote Unix shell protocols, such as the Berkeley Remote Shell (rsh) and the related rlogin and rexec protocols, which all use insecure, plaintext methods of authentication, like passwords. Since mechanisms like Telnet and Remote Shell are designed to access and operate remote computers, sending the authentication tokens (e.g. username and password) for this access to these computers across a public network in an unsecured way poses a great risk of 3rd parties obtaining the password and achieving the same level of access to the remote system as the telnet user. Secure Shell mitigates this risk through the use of encryption mechanisms that are intended to hide th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network News Transfer Protocol
The Network News Transfer Protocol (NNTP) is an application Protocol (computing), protocol used for transporting Usenet news articles (''netnews'') between news servers, and for reading/posting articles by the end user client applications. Brian Kantor of the University of California, San Diego, and Phil Lapsley of the University of California, Berkeley, wrote , the specification for the Network News Transfer Protocol, in March 1986. Other contributors included Stan O. Barber from the Baylor College of Medicine and Erik Fair of Apple Computer. Usenet was originally designed based on the UUCP network, with most article transfers taking place over direct Point-to-point (telecommunications), point-to-point telephone links between news servers, which were powerful time-sharing systems. Readers and posters logged into these computers reading the articles directly from the local disk. As local area networks and Internet participation proliferated, it became desirable to allow News cli ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Simple Mail Transfer Protocol
The Simple Mail Transfer Protocol (SMTP) is an Internet standard communication protocol for electronic mail transmission. Mail servers and other message transfer agents use SMTP to send and receive mail messages. User-level email clients typically use SMTP only for sending messages to a mail server for relaying, and typically submit outgoing email to the mail server on port 465 or 587 per . For retrieving messages, IMAP (which replaced the older POP3) is standard, but proprietary servers also often implement proprietary protocols, e.g., Exchange ActiveSync. SMTP's origins began in 1980, building on concepts implemented on the ARPANET since 1971. It has been updated, modified and extended multiple times. The protocol version in common use today has extensible structure with various extensions for authentication, encryption, binary data transfer, and internationalized email addresses. SMTP servers commonly use the Transmission Control Protocol on port number 25 (between se ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Oidentd
oidentd is an RFC 1413 compliant ident daemon which runs on Linux, FreeBSD, OpenBSD, NetBSD, DragonFly BSD, and some versions of Darwin and Solaris. It can handle IP masqueraded or NAT connections, and has a flexible mechanism for specifying ident responses. Users can be granted permission to specify their own ident responses, hide responses for connections owned by them, or return random ident responses. Responses can be specified according to host and port pairs. One of the most notable capabilities is spoofed ident responses or ident spoofing. The oidentd.conf configuration file can be used to specify the amount of control users have over the responses ''oidentd'' returns upon successful lookups for connections owned by them, while the ''$HOME/.oidentd.conf'' file allows a user to specify what ident response will be returned for specific connections. See also * Internet Relay Chat IRC (Internet Relay Chat) is a text-based chat system for instant messaging. IRC is d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Superuser
In computing, the superuser is a special user account used for system administration. Depending on the operating system (OS), the actual name of this account might be root, administrator, admin or supervisor. In some cases, the actual name of the account is not the determining factor; on Unix-like systems, for example, the user with a user identifier (UID) of zero is the superuser .e., uid=0 regardless of the name of that account; and in systems which implement a r model, any user with the role of superuser (or its synonyms) can carry out all actions of the superuser account. The principle of least privilege recommends that most users and applications run under an ordinary account to perform their work, as a superuser account is capable of making unrestricted, potentially adverse, system-wide changes. Unix and Unix-like In Unix-like computer OSes (such as Linux), ''root'' is the conventional name of the user who has all rights or permissions (to all files and programs) in all mod ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Open Proxy
An open proxy is a type of proxy server that is accessible by any Internet user. Generally, a proxy server only allows users within a network group (i.e. a closed proxy) to store and forward Internet services such as Domain Name System, DNS or web pages to reduce and control the bandwidth (computing), bandwidth used by the group. With an open proxy, however, any user on the Internet can use this forwarding service. Advantages An anonymous open proxy is useful to those looking for online anonymity and privacy, as it can help users hide their IP address from web servers since the server requests appear to originate from the proxy server. It makes it harder to reveal their identity and thereby helps preserve their perceived security while browsing World Wide Web, the web or using other internet services. Real anonymity and extensive internet security might not be achieved by this measure alone as website operators can use Client (computing), client-side scripts to determine the brow ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bounce (network)
A BNC (short for Bounced Network Connection) is a piece of software that is used to relay traffic and connections in computer networks, much like a proxy. Using a BNC allows a user to hide the original source of the user's connection, providing privacy as well as the ability to route traffic through a specific location. A BNC can also be used to hide the true target to which a user connects.Lederer, Christian (phrozen77). (December 22, 2009)"IRC bouncer comparison". IRC-Junkie. December 22, 2009. IRC One common usage is over Internet Relay Chat (IRC) via a BNC running on remote servers. In such an environment, where it is very easy to ascertain a user's IP address a BNC may help to hide the original connection source, as well as providing the opportunity for " vhosts" or "virtual hosts". The use of a vhost does not conceal the connection any better but merely adds a statement as the hostname. Many BNCs remain connected to an IRC server in the event the client should disconnec ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Relay Chat
IRC (Internet Relay Chat) is a text-based chat system for instant messaging. IRC is designed for Many-to-many, group communication in discussion forums, called ''#Channels, channels'', but also allows one-on-one communication via instant messaging, private messages as well as Direct Client-to-Client, chat and data transfer, including file sharing. Internet Relay Chat is implemented as an application layer protocol to facilitate communication in the form of text. The chat process works on a Client–server model, client–server networking model. Users connect, using a clientwhich may be a Web application, web app, a Computer program, standalone desktop program, or embedded into part of a larger programto an IRC server, which may be part of a larger IRC network. Examples of ways used to connect include the programs Mibbit, KiwiIRC, mIRC and the paid service IRCCloud. IRC usage has been declining steadily since 2003, losing 60 percent of its users by 2012. In April 2011, the t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Gibberish
Gibberish, also known as jibber-jabber or gobbledygook, is speech that is (or appears to be) nonsense: ranging across speech sounds that are not actual words, pseudowords, language games and specialized jargon that seems nonsensical to outsiders. "Gibberish" is also used as an imprecation to denigrate or tar ideas or opinions the user disagrees with or finds irksome, a rough equivalent of "nonsense", " folderol", "balderdash", or " claptrap". The implication is that the criticized expression or proposition lacks substance or congruence, as opposed to being a differing view. The related word ''jibber-jabber'' refers to rapid talk that is difficult to understand. Etymology The etymology of ''gibberish'' is uncertain. The term was seen in English in the early 16th century. It is generally thought to be an onomatopoeia imitative of speech, similar to the words ''jabber'' (to talk rapidly) and ''gibber'' (to speak inarticulately). It may originate from the word '' jib'', w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Node (networking)
In Computer network, networking, a node (, ‘knot’) is either a redistribution point or a communication endpoint within telecommunication networks. A physical network node is an electronic device that is attached to a network, and is capable of creating, receiving, or transmitting information over a communication channel. In data communication, a physical network node may either be data communication equipment (such as a modem, Network hub, hub, Network bridge, bridge or Network switch, switch) or data terminal equipment (such as a digital telephone handset, a printer or a host computer). A Passivity (engineering), passive distribution point such as a distribution frame or patch panel is not a node. Computer networks In data communication, a physical network node may either be data communication equipment (DCE) such as a modem, Network hub, hub, Network bridge, bridge or Network switch, switch; or data terminal equipment (DTE) such as a digital telephone handset, a printe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |