|
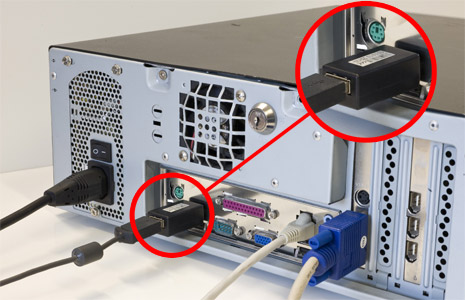
Hardware Keylogger
Hardware keyloggers are used for keystroke logging, a method of capturing and recording computer users' keystrokes, including sensitive passwords. They can be implemented sala madarevel firmware, or alternatively, via a device plugged inline between a computer keyboard and a computer. They log all keyboard activity to their internal memory. Description Hardware keyloggers have an advantage over software keyloggers as they can begin logging from the moment a computer is turned on (and are therefore able to intercept passwords for the BIOS or disk encryption software). All hardware keylogger devices have to have the following: * A microcontroller - this interprets the datastream between the keyboard and computer, processes it, and passes it to the non-volatile memory * A non-volatile memory device, such as flash memory - this stores the recorded data, retaining it even when power is lost Generally, recorded data is retrieved by typing a special password into a computer text edi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
USB Hardware Keylogger
Universal Serial Bus (USB) is an industry standard that establishes specifications for cables, connectors and protocols for connection, communication and power supply (interfacing) between computers, peripherals and other computers. A broad variety of USB hardware exists, including 14 different connector types, of which USB-C is the most recent and the only one not currently deprecated. First released in 1996, the USB standards are maintained by the USB Implementers Forum (USB-IF). The four generations of USB are: USB 1.''x'', USB 2.0, USB 3.''x'', and USB4. Overview USB was designed to standardize the connection of peripherals to personal computers, both to communicate with and to supply electric power. It has largely replaced interfaces such as serial ports and parallel ports, and has become commonplace on a wide range of devices. Examples of peripherals that are connected via USB include computer keyboards and mice, video cameras, printers, portable media players, mob ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Keyboard (computing)
A computer keyboard is a peripheral input device modeled after the typewriter keyboard which uses an arrangement of buttons or keys to act as mechanical levers or electronic switches. Replacing early punched cards and paper tape technology, interaction via teleprinter-style keyboards have been the main input method for computers since the 1970s, supplemented by the computer mouse since the 1980s. Keyboard keys (buttons) typically have a set of characters engraved or printed on them, and each press of a key typically corresponds to a single written symbol. However, producing some symbols may require pressing and holding several keys simultaneously or in sequence. While most keys produce characters (letters, numbers or symbols), other keys (such as the escape key) can prompt the computer to execute system commands. In a modern computer, the interpretation of key presses is generally left to the software: the information sent to the computer, the scan code, tells it only wh ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Sting Operation
In law enforcement, a sting operation is a deceptive operation designed to catch a person attempting to commit a crime. A typical sting will have an undercover law enforcement officer, detective, or co-operative member of the public play a role as criminal partner or potential victim and go along with a suspect's actions to gather evidence of the suspect's wrongdoing. Mass media journalists occasionally resort to sting operations to record video and broadcast to expose criminal activity. Sting operations are common in many countries, such as the United States, but they are not permitted in some countries, such as Sweden or France. There are prohibitions on conducting certain types of sting operations, such as in the Philippines, where it is illegal for law enforcers to pose as drug dealers to apprehend buyers of illegal drugs. Examples * Offering free sports or airline tickets to lure fugitives out of hiding. * Deploying a bait car (also called a honey trap) to catch a car thief ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Keystroke Logging
Keystroke logging, often referred to as keylogging or keyboard capturing, is the action of recording (logging) the keys struck on a keyboard, typically covertly, so that a person using the keyboard is unaware that their actions are being monitored. Data can then be retrieved by the person operating the logging program. A keystroke recorder or keylogger can be either software or hardware. While the programs themselves are legal, with many designed to allow employers to oversee the use of their computers, keyloggers are most often used for stealing passwords and other confidential information. Keylogging can also be used to study keystroke dynamics or human-computer interaction. Numerous keylogging methods exist, ranging from hardware and software-based approaches to acoustic cryptanalysis. Application of keylogger Software-based keyloggers A software-based keylogger is a computer program designed to record any input from the keyboard. Keyloggers are used in IT organizatio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Physical Access
Physical access is a term in computer security that refers to the ability of people to physically gain access to a computer system. According to Gregory White, "Given physical access to an office, the knowledgeable attacker will quickly be able to find the information needed to gain access to the organization's computer systems and network." Attacks and countermeasures Attacks Physical access opens up a variety of avenues for hacking. Michael Meyers notes that "the best network software security measures can be rendered useless if you fail to physically protect your systems," since an intruder could simply walk off with a server and crack the password at his leisure. Physical access also allows hardware keyloggers to be installed. An intruder may be able to boot from a CD or other external media and then read unencrypted data on the hard drive. They may also exploit a lack of access control in the boot loader; for instance, pressing F8 while certain versions of Microsoft Windows ar ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
International Data Group
International Data Group (IDG, Inc.) is a market intelligence and demand generation company focused on the technology industry. IDG, Inc.’s mission is centered around supporting the technology industry through research, data, marketing technology, and insights that help create and sustain relationships between businesses. IDG, Inc. is wholly owned by Blackstone and is led by Mohamad Ali, who was appointed CEO of the company in 2019. Ali serves on IDG, Inc.’s leadership team along with IDC President Crawford Del Prete, IDG, Inc.’s Chief Financial Officer Donna Marr, and Foundry President Kumaran Ramanathan. IDG, Inc. is headquartered in Needham, MA and is parent company to both International Data Corporation (IDC) and Foundry (formerly IDG Communications). History International Data Group was initially founded as International Data Corporate (IDC) in 1964 by Patrick Joseph McGovern, shortly after he had graduated from the Massachusetts Institute of Technology (MIT). Bas ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
PS/2 Connector
The PS/2 port is a 6-pin mini-DIN connector used for connecting keyboards and mice to a PC compatible computer system. Its name comes from the IBM Personal System/2 series of personal computers, with which it was introduced in 1987. The PS/2 mouse connector generally replaced the older DE-9 RS-232 "serial mouse" connector, while the PS/2 keyboard connector replaced the larger 5-pin/180° DIN connector used in the IBM PC/AT design. The PS/2 keyboard port is electrically and logically identical to the IBM AT keyboard port, differing only in the type of electrical connector used. The PS/2 platform introduced a second port with the same design as the keyboard port for use to connect a mouse; thus the PS/2-style keyboard and mouse interfaces are electrically similar and employ the same communication protocol. However, unlike the otherwise similar Apple Desktop Bus connector used by Apple, a given system's keyboard and mouse port may not be interchangeable since the two devices use d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Balun
A balun (from "balanced to unbalanced", originally, but now dated from "balancing unit") is an electrical device that allows balanced and unbalanced lines to be interfaced without disturbing the impedance arrangement of either line. A balun can take many forms and may include devices that also transform impedances but need not do so. Sometimes, in the case of transformer baluns, they use magnetic coupling but need not do so. Common-mode chokes are also used as baluns and work by eliminating, rather than rejecting, common mode signals. Types of balun Classical transformer type In classical transformers, there are two electrically separate windings of wire coils around the transformer's core. The advantage of transformer-type over other types of balun is that the electrically separate windings for input and output allow these baluns to connect circuits whose ground-level voltages are subject to ground loops or are otherwise electrically incompatible; for that reason they ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Electromagnetic Compatibility
Electromagnetic compatibility (EMC) is the ability of electrical equipment and systems to function acceptably in their electromagnetic environment, by limiting the unintentional generation, propagation and reception of electromagnetic energy which may cause unwanted effects such as electromagnetic interference (EMI) or even physical damage in operational equipment. The goal of EMC is the correct operation of different equipment in a common electromagnetic environment. It is also the name given to the associated branch of electrical engineering. EMC pursues three main classes of issue. Emission is the generation of electromagnetic energy, whether deliberate or accidental, by some source and its release into the environment. EMC studies the unwanted emissions and the countermeasures which may be taken in order to reduce unwanted emissions. The second class, susceptibility, is the tendency of electrical equipment, referred to as the victim, to malfunction or break down in the presen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Keystroke Logging
Keystroke logging, often referred to as keylogging or keyboard capturing, is the action of recording (logging) the keys struck on a keyboard, typically covertly, so that a person using the keyboard is unaware that their actions are being monitored. Data can then be retrieved by the person operating the logging program. A keystroke recorder or keylogger can be either software or hardware. While the programs themselves are legal, with many designed to allow employers to oversee the use of their computers, keyloggers are most often used for stealing passwords and other confidential information. Keylogging can also be used to study keystroke dynamics or human-computer interaction. Numerous keylogging methods exist, ranging from hardware and software-based approaches to acoustic cryptanalysis. Application of keylogger Software-based keyloggers A software-based keylogger is a computer program designed to record any input from the keyboard. Keyloggers are used in IT organizatio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Byte
The byte is a unit of digital information that most commonly consists of eight bits. Historically, the byte was the number of bits used to encode a single character of text in a computer and for this reason it is the smallest addressable unit of memory in many computer architectures. To disambiguate arbitrarily sized bytes from the common 8-bit definition, network protocol documents such as The Internet Protocol () refer to an 8-bit byte as an octet. Those bits in an octet are usually counted with numbering from 0 to 7 or 7 to 0 depending on the bit endianness. The first bit is number 0, making the eighth bit number 7. The size of the byte has historically been hardware-dependent and no definitive standards existed that mandated the size. Sizes from 1 to 48 bits have been used. The six-bit character code was an often-used implementation in early encoding systems, and computers using six-bit and nine-bit bytes were common in the 1960s. These systems often had memory words ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |