|
Hard Coding
Hard coding (also hard-coding or hardcoding) is the software development practice of embedding data directly into the source code of a program or other executable object, as opposed to obtaining the data from external sources or generating it at runtime. Hard-coded data typically can be modified only by editing the source code and recompiling the executable, although it can be changed in memory or on disk using a debugger or hex editor. Data that is hard-coded is best suited for unchanging pieces of information, such as physical constants, version numbers, and static text elements. Soft-coded data, on the other hand, encodes arbitrary information through user input, text files, INI files, HTTP server responses, configuration files, preprocessor macros, external constants, databases, command-line arguments, and is determined at runtime. Overview Hard coding requires the program's source code to be changed any time the input data or desired format changes, when it might b ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Source Code
In computing, source code, or simply code or source, is a plain text computer program written in a programming language. A programmer writes the human readable source code to control the behavior of a computer. Since a computer, at base, only understands machine code, source code must be Translator (computing), translated before a computer can Execution (computing), execute it. The translation process can be implemented three ways. Source code can be converted into machine code by a compiler or an assembler (computing), assembler. The resulting executable is machine code ready for the computer. Alternatively, source code can be executed without conversion via an interpreter (computing), interpreter. An interpreter loads the source code into memory. It simultaneously translates and executes each statement (computer science), statement. A method that combines compilation and interpretation is to first produce bytecode. Bytecode is an intermediate representation of source code tha ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Execution (computing)
Execution in computer and software engineering is the process by which a computer or virtual machine interprets and acts on the instructions of a computer program. Each instruction of a program is a description of a particular action which must be carried out, in order for a specific problem to be solved. Execution involves repeatedly following a " fetch–decode–execute" cycle for each instruction done by the control unit. As the executing machine follows the instructions, specific effects are produced in accordance with the semantics of those instructions. Programs for a computer may be executed in a batch process without human interaction or a user may type commands in an interactive session of an interpreter. In this case, the "commands" are simply program instructions, whose execution is chained together. The term run is used almost synonymously. A related meaning of both "to run" and "to execute" refers to the specific action of a user starting (or ''launching'' or ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
End-user License Agreement
An end-user license agreement or EULA () is a legal contract between a software supplier and a customer or end-user. The practice of selling licenses to rather than copies of software predates the recognition of software copyright, which has been recognized since the 1970s in the United States. Initially, EULAs were often printed as shrink wrap contracts, where tearing the shrink wrap indicated acceptance. Software distributed via the internet is more commonly licensed via clickwrap (where the user clicks to agree to the license) or browsewrap (continuing to browse the website indicates agreement). Most companies prefer to sell licenses rather than copies of the software because it enables them to enforce stricter terms on the end user in a number of domains, especially by prohibiting transfer of ownership or use on multiple computers, and by asserting ownership of the copyright of derivative works, such as user-generated content in video games. Enforceability of EULAs has ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
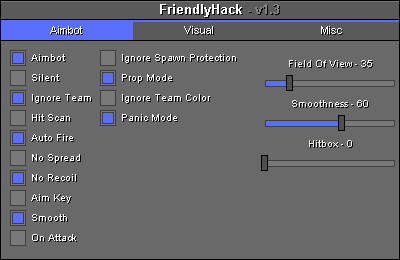
Anti-cheat
On online games, cheating subverts the rules or mechanics of the games to gain an unfair advantage over other players, generally with the use of Third-party software component, third-party software. What constitutes cheating is dependent on the game in question, its rules, and Consensus decision-making, consensus opinion as to whether a particular activity is considered to be cheating. Cheating is present in most Multiplayer video game, multiplayer online games, but it is difficult to measure. Various methods of cheating in online games can take the form of software assistance, such as scripts and bots, and various forms of unsporting play taking advantage of exploits within the game. The Internet and Darknet, darknets can provide players with the methodology necessary to cheat in online games, with software often available for purchase. As methods of cheating have advanced, video game publishers have similarly increased methods of anti-cheating, but are still limited in thei ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Binary Code
A binary code represents plain text, text, instruction set, computer processor instructions, or any other data using a two-symbol system. The two-symbol system used is often "0" and "1" from the binary number, binary number system. The binary code assigns a pattern of binary digits, also known as bits, to each character, instruction, etc. For example, a binary string (computer science), string of eight bits (which is also called a byte) can represent any of 256 possible values and can, therefore, represent a wide variety of different items. In computing and telecommunications, binary codes are used for various methods of encoding data, such as character strings, into bit strings. Those methods may use fixed-width or variable-length code, variable-width strings. In a fixed-width binary code, each letter, digit, or other character is represented by a bit string of the same length; that bit string, interpreted as a binary number, is usually displayed in code tables in octal, decimal ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Software
Software consists of computer programs that instruct the Execution (computing), execution of a computer. Software also includes design documents and specifications. The history of software is closely tied to the development of digital computers in the mid-20th century. Early programs were written in the machine language specific to the hardware. The introduction of high-level programming languages in 1958 allowed for more human-readable instructions, making software development easier and more portable across different computer architectures. Software in a programming language is run through a compiler or Interpreter (computing), interpreter to execution (computing), execute on the architecture's hardware. Over time, software has become complex, owing to developments in Computer network, networking, operating systems, and databases. Software can generally be categorized into two main types: # operating systems, which manage hardware resources and provide services for applicat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Reverse-engineering
Reverse engineering (also known as backwards engineering or back engineering) is a process or method through which one attempts to understand through deductive reasoning how a previously made device, process, system, or piece of software accomplishes a task with very little (if any) insight into exactly how it does so. Depending on the system under consideration and the technologies employed, the knowledge gained during reverse engineering can help with repurposing obsolete objects, doing security analysis, or learning how something works. Although the process is specific to the object on which it is being performed, all reverse engineering processes consist of three basic steps: information extraction, modeling, and review. Information extraction is the practice of gathering all relevant information for performing the operation. Modeling is the practice of combining the gathered information into an abstract model, which can be used as a guide for designing the new object or syst ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Decompiling
A decompiler is a computer program that translates an executable file back into high-level source code. Unlike a compiler, which converts high-level code into machine code, a decompiler performs the reverse process. While disassemblers translate executables into assembly language, decompilers go a step further by reconstructing the disassembly into higher-level languages like C. Due to the one-way nature of the compilation process, decompilers usually cannot perfectly recreate the original source code. They often produce obfuscated and less readable code. Introduction Decompilation is the process of transforming executable code into a high-level, human-readable format using a decompiler. This process is commonly used for tasks that involve reverse-engineering the logic behind executable code, such as recovering lost or unavailable source code. Decompilers face inherent challenges due to the loss of critical information during the compilation process, such as variable names, com ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
FLOSS
Free and open-source software (FOSS) is software available under a license that grants users the right to use, modify, and distribute the software modified or not to everyone free of charge. FOSS is an inclusive umbrella term encompassing free software and open-source software. The rights guaranteed by FOSS originate from the "Four Essential Freedoms" of '' The Free Software Definition'' and the criteria of '' The Open Source Definition''. All FOSS can have publicly available source code, but not all source-available software is FOSS. FOSS is the opposite of proprietary software, which is licensed restrictively or has undisclosed source code. The historical precursor to FOSS was the hobbyist and academic public domain software ecosystem of the 1960s to 1980s. Free and open-source operating systems such as Linux distributions and descendants of BSD are widely used, powering millions of servers, desktops, smartphones, and other devices. Free-software licenses and open-sourc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Backdoor (computing)
A backdoor is a typically covert method of bypassing normal authentication or encryption in a computer, product, embedded device (e.g. a home router), or its embodiment (e.g. part of a cryptosystem, algorithm, chipset, or even a "homunculus computer"—a tiny computer-within-a-computer such as that found in Intel's AMT technology). Backdoors are most often used for securing remote access to a computer, or obtaining access to plaintext in cryptosystems. From there it may be used to gain access to privileged information like passwords, corrupt or delete data on hard drives, or transfer information within autoschediastic networks. In the United States, the 1994 Communications Assistance for Law Enforcement Act forces internet providers to provide backdoors for government authorities. In 2024, the U.S. government realized that China had been tapping communications in the U.S. using that infrastructure for months, or perhaps longer; China recorded presidential candidate campaign offi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
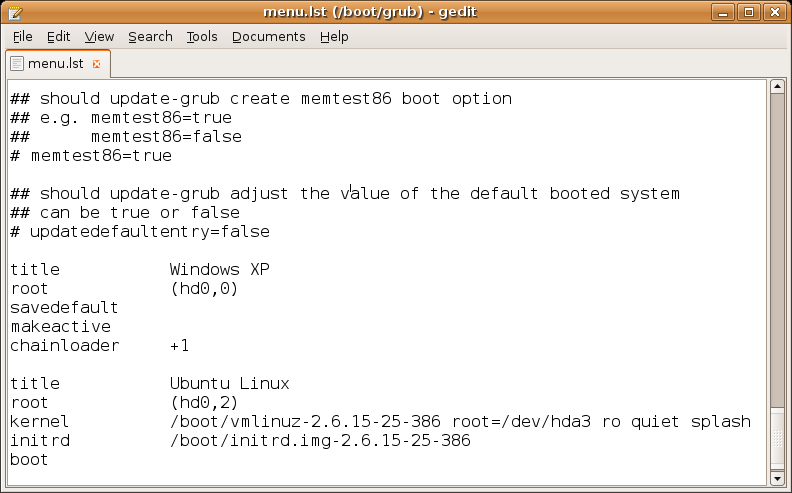
Configuration File
A configuration file, a.k.a. config file, is a computer file, file that stores computer data, data used to configure a software system such as an application software, application, a server (computing), server or an operating system. Some applications provide a tool to create, modify, and verify the syntax of their configuration files sometimes via graphical user interface (GUI). For context, system administrators may be expected to create and modify plain text, text config files via a text editor. For server processes and operating-system settings, there is often no standard tool, but operating systems may provide graphical interfaces such as YaST or debconf. Some computer programs only read their configuration files at Booting, startup. Others periodically check the configuration files for changes. Users can instruct some programs to re-read the configuration files and apply the changes to the current process, or indeed to read arbitrary files as a configuration file. There ar ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Server (computing)
A server is a computer that provides information to other computers called " clients" on a computer network. This architecture is called the client–server model. Servers can provide various functionalities, often called "services", such as sharing data or resources among multiple clients or performing computations for a client. A single server can serve multiple clients, and a single client can use multiple servers. A client process may run on the same device or may connect over a network to a server on a different device. Typical servers are database servers, file servers, mail servers, print servers, web servers, game servers, and application servers. Client–server systems are usually most frequently implemented by (and often identified with) the request–response model: a client sends a request to the server, which performs some action and sends a response back to the client, typically with a result or acknowledgment. Designating a computer as "server-class hardwa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |