|
Hosted NAT Traversal
Network address translation traversal is a computer networking technique of establishing and maintaining Internet protocol connections across gateways that implement network address translation (NAT). NAT traversal techniques are required for many network applications, such as peer-to-peer file sharing and Voice over IP. Network address translation NAT devices allow the use of private IP addresses on private networks behind routers with a single public IP address facing the Internet. The internal network devices communicate with hosts on the external network by changing the source address of outgoing requests to that of the NAT device and relaying replies back to the originating device. This leaves the internal network ill-suited for hosting servers, as the NAT device has no automatic method of determining the internal host for which incoming packets are destined. This is not a problem for general web access and email. However, applications such as peer-to-peer file sharing, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Protocol
The Internet Protocol (IP) is the network layer communications protocol in the Internet protocol suite for relaying datagrams across network boundaries. Its routing function enables internetworking, and essentially establishes the Internet. IP has the task of delivering packets from the source host to the destination host solely based on the IP addresses in the packet headers. For this purpose, IP defines packet structures that encapsulate the data to be delivered. It also defines addressing methods that are used to label the datagram with source and destination information. IP was the connectionless datagram service in the original Transmission Control Program introduced by Vint Cerf and Bob Kahn in 1974, which was complemented by a connection-oriented service that became the basis for the Transmission Control Protocol (TCP). The Internet protocol suite is therefore often referred to as ''TCP/IP''. The first major version of IP, Internet Protocol Version 4 (IPv4), is the do ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Traversal Using Relays Around NAT
Traversal Using Relays around NAT (TURN) is a protocol that assists in traversal of network address translators (NAT) or firewalls for multimedia applications. It may be used with the Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). It is most useful for clients on networks masqueraded by symmetric NAT devices. TURN does not aid in running servers on well known ports in the private network through a NAT; it supports the connection of a user behind a NAT to only a single peer, as in telephony, for example. TURN is specified by . The TURN URI scheme is documented in {{IETF RFC, 7065. Introduction NATs, while providing benefits, also come with drawbacks. The most troublesome of those drawbacks is the fact that they break many existing IP applications, and make it difficult to deploy new ones. Guidelines have been developed that describe how to build "NAT friendly" protocols, but many protocols simply cannot be constructed according to those guidelines. Exampl ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Application-level Gateway
An application-level gateway (ALG, also known as application layer gateway, application gateway, application proxy, or application-level proxy) is a security component that augments a firewall or NAT employed in a computer network. It allows customized NAT traversal filters to be plugged into the gateway to support address and port translation for certain application layer "control/data" protocols such as FTP, BitTorrent, SIP, RTSP, file transfer in IM applications. In order for these protocols to work through NAT or a firewall, either the application has to know about an address/port number combination that allows incoming packets, or the NAT has to monitor the control traffic and open up port mappings ('' firewall pinholes'') dynamically as required. Legitimate application data can thus be passed through the security checks of the firewall or NAT that would have otherwise restricted the traffic for not meeting its limited filter criteria. Functions An ALG may offer t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Port Control Protocol
Port Control Protocol (PCP) is a computer networking protocol that allows hosts on IPv4 or IPv6 networks to control how the incoming IPv4 or IPv6 packets are translated and forwarded by an upstream router that performs network address translation (NAT) or packet filtering. By allowing hosts to create explicit port forwarding rules, handling of the network traffic can be easily configured to make hosts placed behind NATs or firewalls reachable from the rest of the Internet (so they can also act as network servers), which is a requirement for many applications. Additionally, explicit port forwarding rules available through PCP allow hosts to reduce the amount of generated traffic by eliminating workarounds in form of outgoing NAT keepalive messages, which are required for maintaining connections to servers and for various NAT traversal techniques such as TCP hole punching. At the same time, less generated traffic reduces the power consumption, directly improving the battery r ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NAT Port Mapping Protocol
NAT Port Mapping Protocol (NAT-PMP) is a network protocol for establishing network address translation (NAT) settings and port forwarding configurations automatically without user effort. The protocol automatically determines the external IPv4 address of a NAT gateway, and provides means for an application to communicate the parameters for communication to peers. Apple introduced NAT-PMP in 2005 by as part of the Bonjour specification, as an alternative to the more common ISO Standard Internet Gateway Device Protocol implemented in many NAT routers. The protocol was published as an informational Request for Comments (RFC) by the Internet Engineering Task Force (IETF) in RFC 6886. NAT-PMP runs over the User Datagram Protocol (UDP) and uses port number 5351. It has no built-in authentication mechanisms because forwarding a port typically does not allow any activity that could not also be achieved using STUN methods. The benefit of NAT-PMP over STUN is that it does not require a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Small Office/home Office
Small office/home office (or single office/home office; sometimes short SOHO) refers to the category of business or cottage industry that involves from 1 to 10 workers. In New Zealand, the Ministry of Business, Innovation and Employment (MBIE) defines a small office as 6–19 employees and a micro office as 1–5. History Before the 19th century, and the spread of the industrial revolution around the globe, nearly all offices were small offices and/or home offices, with only a few exceptions. Most businesses were small, and the paperwork that accompanied them was limited. The industrial revolution aggregated workers in factories, to mass-produce goods. In most circumstances, the white collar counterpart—office work—was aggregated as well in large buildings, usually in cities or densely populated suburban areas. Beginning in the mid-1980s, the advent of the personal computer and fax machine, plus breakthroughs in telecommunications, created opportunities for office workers ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Gateway Device Protocol
The Internet (or internet) is the global system of interconnected computer networks that uses the Internet protocol suite (TCP/IP) to communicate between networks and devices. It is a '' network of networks'' that consists of private, public, academic, business, and government networks of local to global scope, linked by a broad array of electronic, wireless, and optical networking technologies. The Internet carries a vast range of information resources and services, such as the inter-linked hypertext documents and applications of the World Wide Web (WWW), electronic mail, telephony, and file sharing. The origins of the Internet date back to the development of packet switching and research commissioned by the United States Department of Defense in the 1960s to enable time-sharing of computers. The primary precursor network, the ARPANET, initially served as a backbone for interconnection of regional academic and military networks in the 1970s to enable resource sharing. The ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
UPnP
Universal Plug and Play (UPnP) is a set of networking protocols that permits networked devices, such as personal computers, printers, Internet gateways, Wi-Fi access points and mobile devices to seamlessly discover each other's presence on the network and establish functional network services. UPnP is intended primarily for residential networks without enterprise-class devices. The UPnP protocols were promoted by the UPnP Forum, a computer industry initiative to enable simple and robust connectivity to standalone devices and personal computers from many different vendors. The Forum consisted of more than 800 vendors involved in everything from consumer electronics to network computing. Since 2016, all UPnP efforts have been managed by the Open Connectivity Foundation (OCF). UPnP assumes the network runs Internet Protocol (IP) and then leverages HTTP, on top of IP, in order to provide device/service description, actions, data transfer and event notification. Device search reques ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Interactive Connectivity Establishment
Interactive Connectivity Establishment (ICE) is a technique used in computer networking to find ways for two computers to talk to each other as directly as possible in peer-to-peer networking. This is most commonly used for interactive media such as Voice over Internet Protocol (VoIP), peer-to-peer communications, video, and instant messaging. In such applications, communicating through a central server would be slow and expensive, but direct communication between client applications on the Internet is very tricky due to network address translators (NATs), firewalls, and other network barriers. ICE is developed by the Internet Engineering Task Force MMUSIC working group and is published as RFC 8445, as of August 2018, and has obsolesced both RFC 5245 and RFC 4091.RFC 4091, ''The Alternative Network Address Types (ANAT) Semantics for the Session Description Protocol (SDP) Grouping Framework'', G. Camarillo, J. Rosenberg (June 2005) Overview Network address translation (NAT) becam ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
STUN
STUN (Session Traversal Utilities for NAT; originally Simple Traversal of User Datagram Protocol (UDP) through Network Address Translators) is a standardized set of methods, including a network protocol, for traversal of network address translator (NAT) gateways in applications of real-time voice, video, messaging, and other interactive communications. STUN is a tool used by other protocols, such as Interactive Connectivity Establishment (ICE), the Session Initiation Protocol (SIP), and WebRTC. It provides a tool for hosts to discover the presence of a network address translator, and to discover the mapped, usually public, Internet Protocol (IP) address and port number that the NAT has allocated for the application's User Datagram Protocol (UDP) flows to remote hosts. The protocol requires assistance from a third-party network server (STUN server) located on the opposing (public) side of the NAT, usually the public Internet. STUN was first announced in RFC 3489; the title was ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
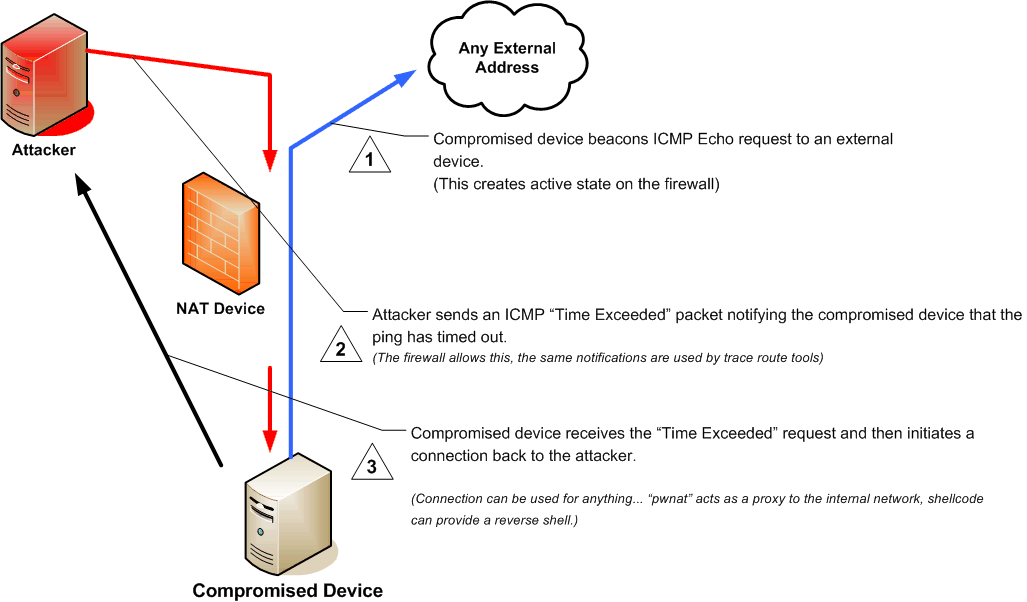
ICMP Hole Punching
ICMP hole punching is a technique employed in network address translator (NAT) applications for maintaining Internet Control Message Protocol (ICMP) packet streams that traverse the NAT. NAT traversal techniques are typically required for client-to-client networking applications on the Internet involving hosts connected in private networks, especially in peer-to-peer and Voice over Internet Protocol (VoIP) deployments. ICMP hole punching establishes connectivity between two hosts communicating across one or more network address translators in either a peer-to-peer or client–server model. Typically, third party hosts on the public transit network are used to establish UDP or TCP port states that may be used for direct communications between the communicating hosts, however ICMP hole punching requires no third party involvement to pass information between one or more NATs by exploiting a NAT's loose acceptance of inbound ICMP Time Exceeded packets. Once an ICMP Time Exc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |