|
Hacks At The Massachusetts Institute Of Technology
Hacks at the Massachusetts Institute of Technology are practical jokes and pranks meant to prominently demonstrate technical aptitude and cleverness, and/or to commemorate popular culture and historical topics. The pranks are anonymously installed at night by hackers, usually, but not exclusively, undergraduate students. The hackers' actions are governed by an informal yet extensive body of precedent, tradition and ethics. Hacks can occur anywhere across campus, and occasionally off campus; many make use of the iconic Great Dome, Little Dome, Green Building tower, or other prominent architectural features of the MIT campus. Well-known hacker alumni include Nobel Laureates Richard P. Feynman and George F. Smoot. In October 2009, US President Barack Obama made a reference to the MIT hacking tradition during an on-campus speech about clean energy. In recent years, MIT students have employed hacks to protest MIT's collaborations with the Israeli military and arms suppliers dur ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
MIT Simmons Smiles
The Massachusetts Institute of Technology (MIT) is a Private university, private research university in Cambridge, Massachusetts, United States. Established in 1861, MIT has played a significant role in the development of many areas of modern technology and science. In response to the increasing Technological and industrial history of the United States, industrialization of the United States, William Barton Rogers organized a school in Boston to create "useful knowledge." Initially funded by a land-grant universities, federal land grant, the institute adopted a Polytechnic, polytechnic model that stressed laboratory instruction in applied science and engineering. MIT moved from Boston to Cambridge in 1916 and grew rapidly through collaboration with private industry, military branches, and new federal basic research agencies, the formation of which was influenced by MIT faculty like Vannevar Bush. In the late twentieth century, MIT became a leading center for research in compu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Harvard–Yale Football Rivalry
The Harvard–Yale football rivalry is renewed annually with The Game, an American college football match between the Crimson football team of Harvard University and the Bulldogs football team of Yale University. Though the winner does not take possession of a physical prize, the matchup is usually considered the most important and anticipated game of the year for both teams, regardless of their season records. The Game is scheduled annually as the last contest of the year for both teams; as the Ivy League does not participate in postseason play for football, The Game is the final outing for each team's graduating seniors. Some years, the rivalry carries the additional significance of deciding the Ivy League championship. The weekend of The Game includes more than just the varsity matchup; the respective Yale residential college football teams compete against "sister" Harvard house teams the day before. The Game is third among most-played NCAA Division I football rivalries ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Apollo Lunar Module
The Apollo Lunar Module (LM ), originally designated the Lunar Excursion Module (LEM), was the lunar lander spacecraft that was flown between lunar orbit and the Moon's surface during the United States' Apollo program. It was the first crewed spacecraft to operate exclusively in the airless vacuum of space, and remains the only crewed vehicle to land anywhere beyond Earth. Structurally and aerodynamically incapable of flight through Earth's atmosphere, the Multistage rocket , two-stage Lunar Module was ferried to lunar orbit attached to the Apollo command and service module (CSM), about twice its mass. Its crew of two flew the Lunar Module from lunar orbit to the Moon's surface. During takeoff, the spent descent stage was used as a launch pad for the ascent stage which then Lunar orbit rendezvous, flew back to the command module, after which it was also discarded. Overseen by Grumman, the LM's development was plagued with problems that delayed its first uncrewed flight by about ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Urban Exploration
Urban exploration (often shortened as UE, urbex, and sometimes known as roof and tunnel hacking) is the exploration of manmade structures, usually abandoned ruins or hidden components of the manmade environment. Photography and historical interest/documentation are heavily featured in the hobby, sometimes involving trespassing onto private property. Urban exploration is also called draining (a specific form of urban exploration where storm drains or sewers are explored), urban spelunking, urban rock climbing, urban caving, building hacking, or Mouse-holing, mousing. The activity presents various risks, including physical danger, the possibility of arrest and punishment if done illegally and/or without permission, and the risk of encountering Squatting, squatters. Some activities associated with urban exploration may violate local or regional laws, certain broadly interpreted Anti-terrorism legislation, anti-terrorism laws, or can be considered trespassing or invasion of privacy ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Roof And Tunnel Hacking
Roof and tunnel hacking is the unauthorized exploration of roof and utility tunnel spaces. The term carries a strong collegiate connotation, stemming from its use at MIT and at the U.S. Naval Academy, where the practice has a long history. It is a form of urban exploration. Some participants use it as a means of carrying out collegiate pranks, by hanging banners from high places or, in one notable example from MIT, placing a life-size model police car on top of a university building. Others are interested in exploring inaccessible and seldom-seen places; that such exploration is unauthorized is often part of the thrill. Roofers, in particular, may be interested in the skyline views from the highest points on a campus. On August 1, 2016, Red Bull TV launched the documentary series '' URBEX – Enter At Your Own Risk'', which also chronicles roof and tunnel hacking. Vadding Vadding is a verb which has become synonymous with urban exploration. The word comes from MI ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cyberculture
Internet culture refers to culture developed and maintained among frequent and active users of the Internet (also known as netizens) who primarily communicate with one another as members of online communities; that is, a culture whose influence is "mediated by computer screens" and information communication technology, specifically the Internet. Internet culture arises from the frequent interactions between members within various online communities and the use of these communities for communication, entertainment, business, and recreation. Studied aspects of Internet culture include anonymity/pseudonymity, social media, gaming and specific communities, such as fandoms. History The Internet developed in parallel with rapid and sustained technological advances in computing and data communication. Widespread access to the Internet emerged as the cost of infrastructure dropped by several orders of magnitude with consecutive technological improvements. Though Internet cultur ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hacker Ethic
The hacker ethic is a philosophy and set of moral values within hacker culture. Practitioners believe that sharing information and data with others is an ethical imperative. The hacker ethic is related to the concept of freedom of information, as well as the political theories of anti-authoritarianism, anarchism, and libertarianism. While some tenets of the hacker ethic were described in other texts like '' Computer Lib/Dream Machines'' (1974) by Ted Nelson, the term ''hacker ethic'' is generally attributed to journalist Steven Levy, who appears to have been the first to document both the philosophy and the founders of the philosophy in his 1984 book titled '' Hackers: Heroes of the Computer Revolution.'' History The hacker ethic originated at the Massachusetts Institute of Technology in the 1950s–1960s. The term "hacker" has long been used there to describe college pranks that MIT students would regularly devise, and was used more generally to describe a project undertake ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Culture Jamming
Culture jamming (sometimes also guerrilla communication) is a form of protest used by many anti-consumerist social movements to disrupt or subvert media culture and its mainstream cultural institutions, including corporate advertising. It attempts to "expose the methods of domination" of mass society. Culture jamming employs techniques originally associated with Letterist International, and later Situationist International known as ''détournement.'' It uses the language and rhetoric of mainstream culture to subversively critique the social institutions that produce that culture. Tactics include editing company logos to critique the respective companies, products, or concepts they represent, or wearing fashion statements that criticize the current fashion trends by deliberately clashing with them.Boden, Sharon and Williams, Simon J. (2002) "Consumption and Emotion: The Romantic Ethic Revisited", Sociology 36(3):493–512 Culture jamming often entails using mass media to pr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hacker (computer Security)
A security hacker or security researcher is someone who explores methods for breaching or bypassing defenses and exploiting weaknesses in a computer system or network. Hackers may be motivated by a multitude of reasons, such as profit, protest, sabotage, information gathering, challenge, recreation, or evaluation of a system weaknesses to assist in formulating defenses against potential hackers. Longstanding controversy surrounds the meaning of the term "hacker". In this controversy, computer programmers reclaim the term ''hacker'', arguing that it refers simply to someone with an advanced understanding of computers and computer networks, and that ''cracker'' is the more appropriate term for those who break into computers, whether computer criminals ( black hats) or computer security experts ( white hats). A 2014 article noted that "the black-hat meaning still prevails among the general public". The subculture that has evolved around hackers is often referred to as the "co ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hacker Culture
The hacker culture is a subculture of individuals who enjoy—often in collective effort—the intellectual challenge of creatively overcoming the limitations of software systems or electronic hardware (mostly digital electronics), to achieve novel and clever outcomes. The act of engaging in activities (such as programming or other media) in a spirit of playfulness and exploration is termed ''hacking''. However, the defining characteristic of a hacker is not the activities performed themselves (e.g. programming), but how it is done and whether it is exciting and meaningful. Activities of playful cleverness can be said to have "hack value" and therefore the term "hacks" came about, with early examples including pranks at MIT done by students to demonstrate their technical aptitude and cleverness. The hacker culture originally emerged in academia in the 1960s around the Massachusetts Institute of Technology (MIT)'s Tech Model Railroad Club (TMRC) and MIT Artificial ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
September 11 Attacks
The September 11 attacks, also known as 9/11, were four coordinated Islamist terrorist suicide attacks by al-Qaeda against the United States in 2001. Nineteen terrorists hijacked four commercial airliners, crashing the first two into the Twin Towers of the World Trade Center in New York City and the third into the Pentagon (headquarters of the U.S. Department of Defense) in Arlington County, Virginia. The fourth plane crashed in a rural Pennsylvania field during a passenger revolt. The attacks killed 2,977 people, making it the deadliest terrorist attack in history. In response to the attacks, the United States waged the global war on terror over multiple decades to eliminate hostile groups deemed terrorist organizations, as well as the foreign governments purported to support them. Ringleader Mohamed Atta flew American Airlines Flight 11 into the North Tower of the World Trade Center complex at 8:46 a.m. Seventeen minutes later at 9:03 a.m., United Airlines Flig ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
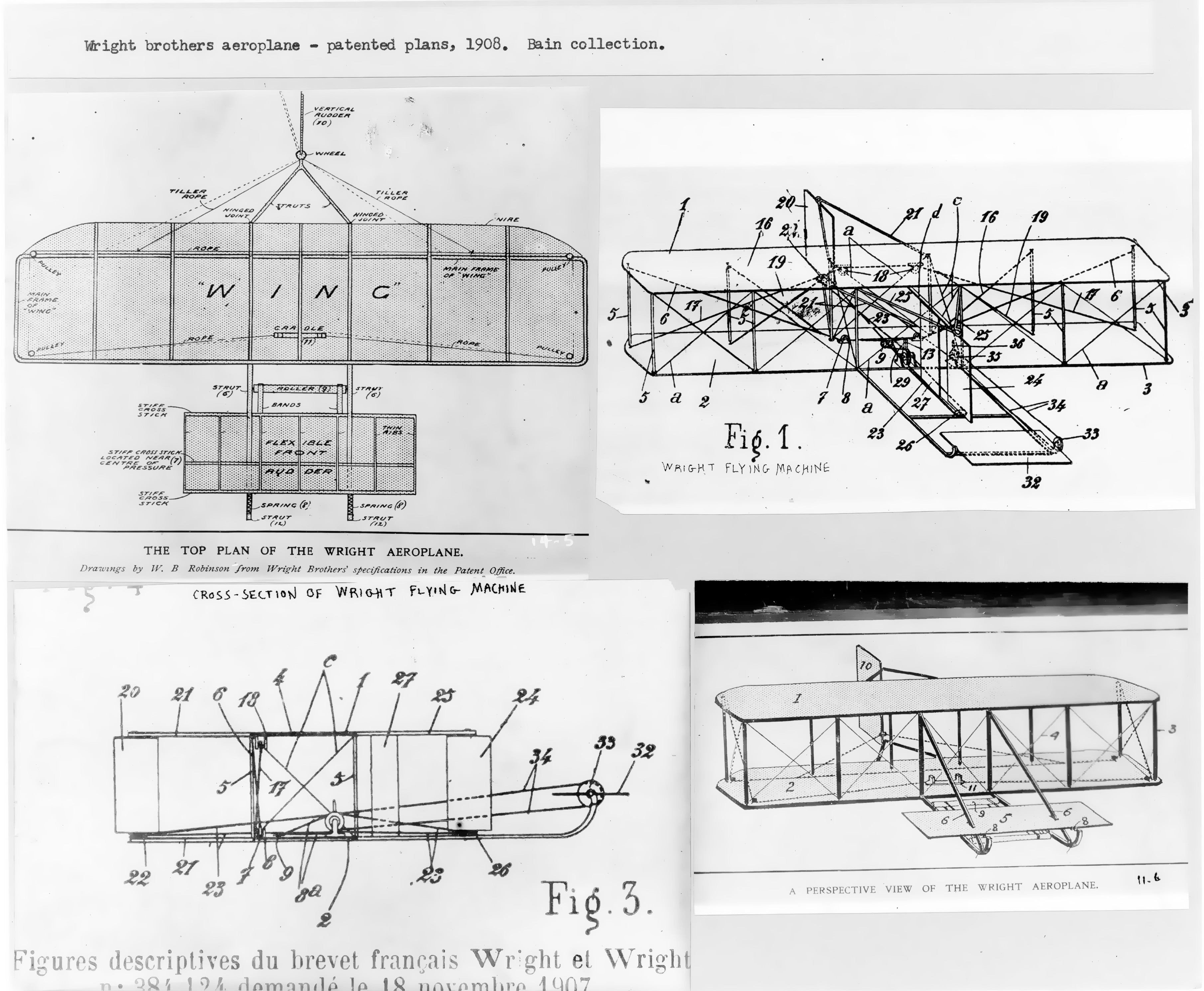
Wright Flyer
The ''Wright Flyer'' (also known as the ''Kitty Hawk'', ''Flyer'' I or the 1903 ''Flyer'') made the first sustained flight by a manned heavier-than-air powered and controlled aircraft on December 17, 1903. Invented and flown by brothers Wright brothers, Orville and Wilbur Wright, it marked the beginning of the Aviation in the pioneer era, pioneer era of aviation. The aircraft is a single-place biplane design with Dihedral (aeronautics)#Anhedral and polyhedral, anhedral (drooping) wings, front double Elevator (aeronautics), elevator (a canard (aeronautics), canard) and rear double rudder. It used a gasoline engine powering two pusher propellers. Employing "wing warping", it was relatively unstable and very difficult to fly. The Wright brothers flew it four times in a location now part of the town of Kill Devil Hills, North Carolina, Kill Devil Hills, about south of Kitty Hawk, North Carolina. The airplane flew on its fourth and final flight, but was damaged on landing, and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |