|
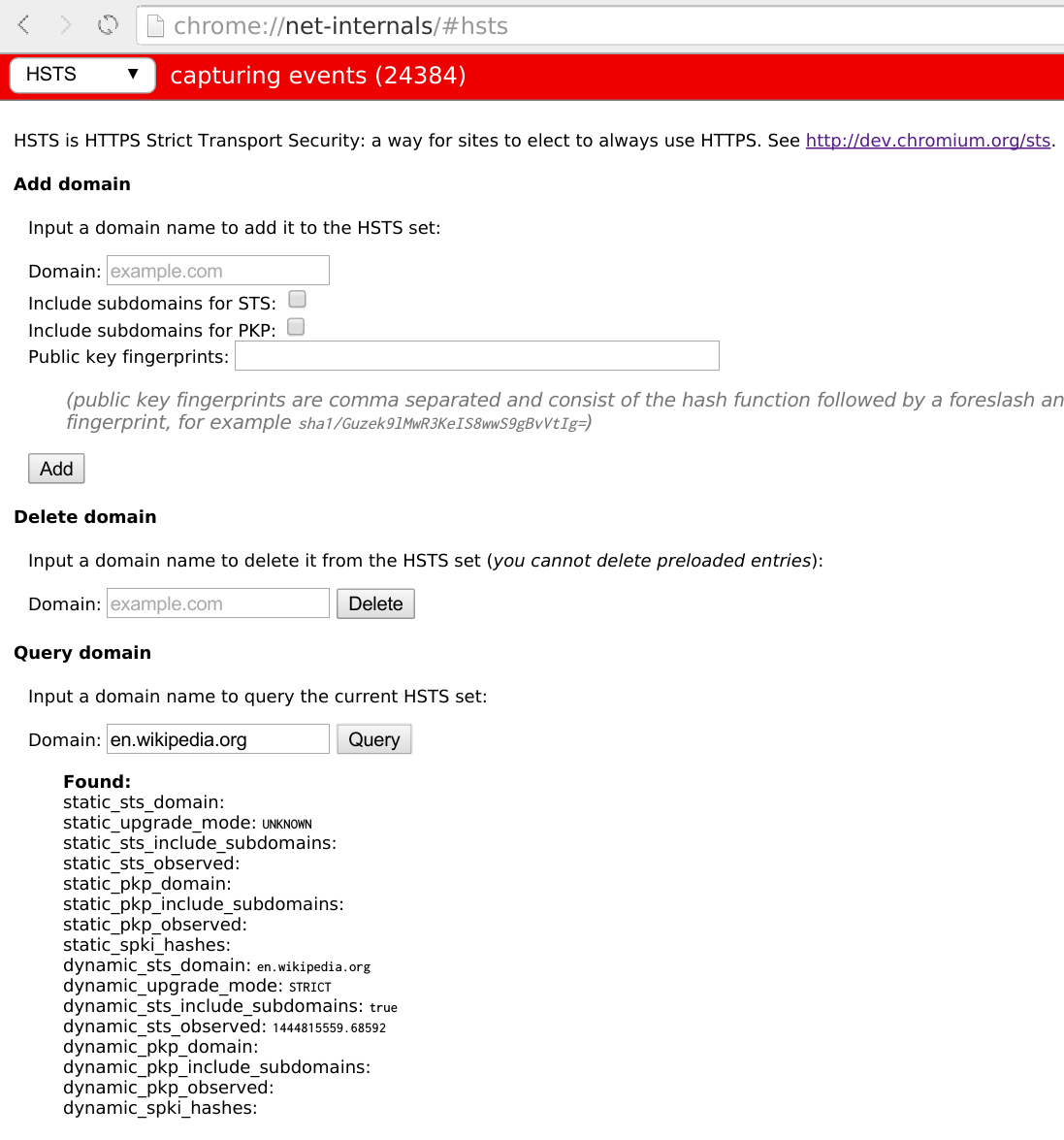
HTTP Strict Transport Security
HTTP Strict Transport Security (HSTS) is a policy mechanism that helps to protect websites against man-in-the-middle attacks such as protocol downgrade attacks and cookie hijacking. It allows web servers to declare that web browsers (or other complying user agents) should automatically interact with it using only HTTPS connections, which provide Transport Layer Security (TLS/SSL), unlike the insecure HTTP used alone. HSTS is an IETF standards track protocol and is specified in . The HSTS Policy is communicated by the server to the user agent via an HTTP response header field named Strict-Transport-Security. HSTS Policy specifies a period of time during which the user agent should only access the server in a secure fashion. Websites using HSTS often do not accept clear text HTTP, either by rejecting connections over HTTP or systematically redirecting users to HTTPS (though this is not required by the specification). The consequence of this is that a user-agent not capable of do ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Man-in-the-middle Attack
In cryptography and computer security, a man-in-the-middle (MITM) attack, or on-path attack, is a cyberattack where the attacker secretly relays and possibly alters the communications between two parties who believe that they are directly communicating with each other, where in actuality the attacker has inserted themselves between the two user parties. One example of a MITM attack is active eavesdropping, in which the attacker makes independent connections with the victims and relays messages between them to make them believe they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. In this scenario, the attacker must be able to intercept all relevant messages passing between the two victims and inject new ones. This is straightforward in many circumstances; for example, an attacker within range of a Wi-Fi access point hosting a network without encryption could insert themselves as a man in the middle. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
PayPal
PayPal Holdings, Inc. is an American multinational financial technology company operating an online payments system in the majority of countries that support E-commerce payment system, online money transfers; it serves as an electronic alternative to traditional Banknote, paper methods such as cheque, checks and money orders. The company operates as a payment processor for online vendors, auction sites and many other commercial and company users, for which it charges an international addition bank charges fee. Established in 1998 as Confinity, PayPal went public through an initial public offering, IPO in 2002. It became a wholly owned subsidiary of eBay later that year, valued at $1.5 billion. In 2015 eBay corporate spin-off, spun off PayPal to its shareholders, and PayPal became an independent company again. The company was ranked 143rd on the 2022 Fortune 500, ''Fortune'' 500 of the largest United States corporations by revenue. Since 2023, PayPal is a member of the MACH Al ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Uniform Resource Identifier
A Uniform Resource Identifier (URI), formerly Universal Resource Identifier, is a unique sequence of characters that identifies an abstract or physical resource, such as resources on a webpage, mail address, phone number, books, real-world objects such as people and places, concepts. URIs are used to identify anything described using the Resource Description Framework (RDF), for example, concepts that are part of an ontology defined using the Web Ontology Language (OWL), and people who are described using the Friend of a Friend vocabulary would each have an individual URI. URIs which provide a means of locating and retrieving information resources on a network (either on the Internet or on another private network, such as a computer filesystem or an Intranet) are Uniform Resource Locators (URLs). Therefore, URLs are a subset of URIs, i.e. every URL is a URI (and not necessarily the other way around). Other URIs provide only a unique name, without a means of locating or retr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Network Time Protocol
The Network Time Protocol (NTP) is a networking protocol for clock synchronization between computer systems over packet-switched, variable-Network latency, latency data networks. In operation since before 1985, NTP is one of the oldest Internet protocols in current use. NTP was designed by David L. Mills of the University of Delaware. NTP is intended to synchronize participating computers to within a few milliseconds of Coordinated Universal Time (UTC). It uses the intersection algorithm, a modified version of Marzullo's algorithm, to select accurate time servers and is designed to mitigate the effects of variable network latency. NTP can usually maintain time to within tens of milliseconds over the public Internet, and can achieve better than one millisecond accuracy in local area networks under ideal conditions. Asymmetric Routing, routes and network congestion can cause errors of 100 ms or more. The protocol is usually described in terms of a client–server model, bu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Firesheep
Firesheep was an extension for the Firefox web browser to hijack sessions. It used a packet sniffer to intercept unencrypted session cookies from websites such as Facebook and Twitter. The plugin eavesdropped on Wi-Fi communications, listening for session cookies. When it detected a session cookie, the tool used this cookie to obtain the identity belonging to that session. The collected identities (victims) are displayed in a side bar in Firefox. By clicking on a victim's name, the victim's session is taken over by the attacker. The extension was released October 2010 as a demonstration of the security risk of session hijacking vulnerabilities to users of web sites that only encrypt the login process and not the cookie(s) created during the login process. It has been warned that the use of the extension to capture login details without permission would violate wiretapping laws and/or computer security laws in some countries. Despite the security threat surrounding Firesheep, r ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Microsoft Edge
Microsoft Edge is a Proprietary Software, proprietary cross-platform software, cross-platform web browser created by Microsoft and based on the Chromium (web browser), Chromium open-source project, superseding Edge Legacy. In Windows 11, Edge is the only browser available from Microsoft. First made available only for Android (operating system), Android and iOS in 2017, in late 2018, Microsoft announced it would completely rebuild Edge as a Chromium (web browser), Chromium-based browser with Blink (browser engine), Blink and V8 (JavaScript engine), V8 engines, which allowed the browser to be ported from Windows 10 to macOS. The new Edge was publicly released in January 2020, and on Xbox as well as Linux in 2021. Edge was also available on Windows 7 and Windows 8, 8/Windows 8.1, 8.1 until early 2023. In February 2023, according to StatCounter, Microsoft Edge became the Usage share of web browsers, third most popular browser in the world, behind Safari (web browser), Safari and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Internet Explorer
Internet Explorer (formerly Microsoft Internet Explorer and Windows Internet Explorer, commonly abbreviated as IE or MSIE) is a deprecation, retired series of graphical user interface, graphical web browsers developed by Microsoft that were used in the Microsoft Windows, Windows line of operating systems. While IE has been discontinued on most Windows editions, it remains supported on certain editions of Windows, such as Windows 10 editions#Organizational editions, Windows 10 LTSB/LTSC. Starting in 1995, it was first released as part of the add-on package Microsoft Plus!, Plus! for Windows 95 that year. Later versions were available as free downloads or in-service packs and included in the original equipment manufacturer (OEM) service releases of Windows 95 and later versions of Windows. Microsoft spent over per year on Internet Explorer in the late 1990s, with over 1,000 people involved in the project by 1999. In 2016, Microsoft Edge (series of web browsers), Microsoft Edge w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Firefox
Mozilla Firefox, or simply Firefox, is a free and open-source web browser developed by the Mozilla Foundation and its subsidiary, the Mozilla Corporation. It uses the Gecko rendering engine to display web pages, which implements current and anticipated web standards. Firefox is available for Windows 10 or later versions of Windows, macOS, and Linux. Its unofficial ports are available for various Unix and Unix-like operating systems, including FreeBSD, OpenBSD, NetBSD, and other operating systems, such as ReactOS. Firefox is also available for Android and iOS. However, as with all other iOS web browsers, the iOS version uses the WebKit layout engine instead of Gecko due to platform requirements. An optimized version is also available on the Amazon Fire TV as one of the two main browsers available with Amazon's Silk Browser. Firefox is the spiritual successor of Netscape Navigator, as the Mozilla community was created by Netscape in 1998, before its acqui ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Google Chrome
Google Chrome is a web browser developed by Google. It was first released in 2008 for Microsoft Windows, built with free software components from Apple WebKit and Mozilla Firefox. Versions were later released for Linux, macOS, iOS, iPadOS, and also for Android (operating system), Android, where it is the default browser. The browser is also the main component of ChromeOS, where it serves as the platform for web applications. Most of Chrome's source code comes from Google's free and open-source software project Chromium (web browser), Chromium, but Chrome is licensed as proprietary freeware. WebKit was the original Browser engine, rendering engine, but Google eventually Fork (software development), forked it to create the Blink (browser engine), Blink engine; all Chrome variants except iOS used Blink as of 2017. , StatCounter estimates that Chrome has a 65% worldwide usage share of web browsers, browser market share (after peaking at 72.38% in November 2018) on personal comput ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Black Hat Briefings
Black Hat Briefings (commonly referred to as Black Hat) is a computer security conference that provides security consulting, training, and briefings to hackers, corporations, and government agencies around the world. Black Hat brings together a variety of people interested in information security ranging from non-technical individuals, executives, hackers, and security professionals. The conference takes place regularly in Las Vegas, Barcelona, London and Riyadh but has also been hosted in Amsterdam, Tokyo, and Washington, D.C. in the past. History The first Black Hat was held July 7-10, 1997 in Las Vegas, immediately prior to DEF CON 5. The conference was aimed at the computer industry, promising to give them privileged insight into the minds and motivations of their hacker adversaries. Its organizers stated: "While many conferences focus on information and network security, only the Black Hat Briefings will put your engineers and software programmers face-to-face with to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Moxie Marlinspike
Moxie Marlinspike is an American entrepreneur, cryptographer, and computer security researcher. Marlinspike is the creator of Signal (messaging app), Signal, co-founder of the Signal Technology Foundation, and served as the first CEO of Signal Messenger LLC. He is also a co-author of the Signal Protocol encryption used by Signal, WhatsApp, Messages (Google), Google Messages, Facebook Messenger, and Skype. Marlinspike is a former head of the security team at Twitter, Inc., Twitter and the author of a proposed SSL authentication system replacement called Convergence (SSL), Convergence. He previously maintained a cloud-based Wi-Fi Protected Access, WPA cracking service and a targeted anonymity service called GoogleSharing. Career Marlinspike began his career working for several technology companies, including enterprise infrastructure software maker BEA Systems, BEA Systems Inc. In 2010, Marlinspike was the chief technology officer and co-founder of Whisper Systems, an enterprise ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |