|
GE 645
The GE 645 mainframe computer was a development of the GE 635 for use in the Multics project. This was the first computer that implemented a configurable hardware protected memory system. The original CTSS was implemented on a modified IBM 7094 with two banks of memory and bank-switching between user and supervisor mode, i.e. programs running in the A-core memory bank had access to instructions that programs running in the B-core bank did not. The Multics operating system implemented multilevel security (MLS) on a GE 635 by running a simulator of the 645 starting on October 18, 1965, in the MIT Tech Center. This simulated environment was replaced by the first 645 hardware in 1967. The GECOS operating system was fully replaced by Multics in 1969 with the Multics supervisor (master mode now known as kernel mode) separated by protection rings with "gates" allowing access from user mode. A later generation in the form of the 645F (F for follow-on) wasn't completed by the time the div ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mainframe Computer
A mainframe computer, informally called a mainframe or big iron, is a computer used primarily by large organizations for critical applications like bulk data processing for tasks such as censuses, industry and consumer statistics, enterprise resource planning, and large-scale transaction processing. A mainframe computer is large but not as large as a supercomputer and has more processing power than some other classes of computers, such as minicomputers, servers, workstations, and personal computers. Most large-scale computer-system architectures were established in the 1960s, but they continue to evolve. Mainframe computers are often used as servers. The term ''mainframe'' was derived from the large cabinet, called a ''main frame'', that housed the central processing unit and main memory of early computers. Later, the term ''mainframe'' was used to distinguish high-end commercial computers from less powerful machines. Design Modern mainframe design is characterized less by ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
GE 635
The GE-600 series was a family of 36-bit mainframe computers originating in the 1960s, built by General Electric (GE). When GE left the mainframe business the line was sold to Honeywell, which built similar systems into the 1990s as the division moved to Groupe Bull and then NEC. The system is perhaps best known as the hardware used by the Dartmouth Time Sharing System (DTSS) and the Multics operating system. Multics was supported by virtual memory additions made to later versions of the series. Architecture The 600 series used 36-bit words and 18-bit addresses. They had two 36-bit accumulators, eight 18-bit index registers, and one 8-bit exponent register. It supported floating point in both 36-bit single-precision and 2 x 36-bit double precision, the exponent being stored separately, allowing up to 71 bits of precision and one bit being used for the sign. It had an elaborate set of addressing modes, many of which used indirect words, some of which were auto-incrementing or ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
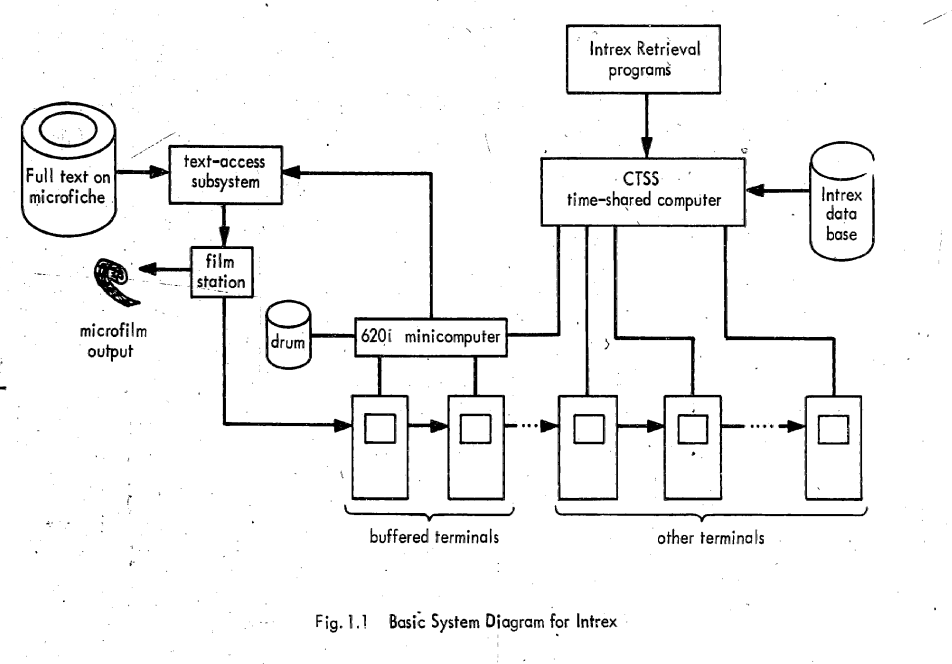
Multics
Multics ("Multiplexed Information and Computing Service") is an influential early time-sharing operating system based on the concept of a single-level memory.Dennis M. Ritchie, "The Evolution of the Unix Time-sharing System", Communications of the ACM, Vol. 17, 1984, pp. 365-375. Nathan Gregory writes that Multics "has influenced all modern operating systems since, from microcomputers to mainframes." Initial planning and development for Multics started in 1964, in Cambridge, Massachusetts. Originally it was a cooperative project led by MIT (Project MAC with Fernando Corbató) along with General Electric and Bell Labs. It was developed on the GE 645 computer, which was specially designed for it; the first one was delivered to MIT in January 1967. GE offered their earlier 635 systems with an early timesharing system known as "Mark I" and intended to offer the 645 with Multics as a larger successor. Bell withdrew from the project in 1969 as it became clear it would not deliver a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Compatible Time-Sharing System
The Compatible Time-Sharing System (CTSS) was the first general purpose time-sharing operating system. Compatible Time Sharing referred to time sharing which was compatible with batch processing; it could offer both time sharing and batch processing concurrently. CTSS was developed at the MIT Computation Center ("Comp Center"). CTSS was first demonstrated on MIT's modified IBM 709 in November 1961. The hardware was replaced with a modified IBM 7090 in 1962 and later a modified IBM 7094 called the "blue machine" to distinguish it from the Project MAC CTSS IBM 7094. Routine service to MIT Comp Center users began in the summer of 1963 and was operated there until 1968. A second deployment of CTSS on a separate IBM 7094 that was received in October 1963 (the "red machine") was used early on in Project MAC until 1969 when the red machine was moved to the Information Processing Center and operated until July 20, 1973. CTSS ran on only those two machines however there were remote CT ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Multilevel Security
Multilevel security or multiple levels of security (MLS) is the application of a computer system to process information with incompatible classifications (i.e., at different security levels), permit access by users with different security clearances and needs-to-know, and prevent users from obtaining access to information for which they lack authorization. There are two contexts for the use of multilevel security. One is to refer to a system that is adequate to protect itself from subversion and has robust mechanisms to separate information domains, that is, trustworthy. Another context is to refer to an application of a computer that will require the computer to be strong enough to protect itself from subversion and possess adequate mechanisms to separate information domains, that is, a system we must trust. This distinction is important because systems that need to be trusted are not necessarily trustworthy. Trusted operating systems An MLS operating environment often requ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
GECOS
General Comprehensive Operating System (GCOS, ; originally GECOS, General Electric Comprehensive Operating Supervisor) is a family of operating systems oriented toward the 36-bit GE/Honeywell mainframe computers. The original version of GCOS was developed by General Electric beginning in 1962. The operating system is still used today in its most recent versions (GCOS 7 and GCOS 8) on servers and mainframes produced by Groupe Bull, primarily through emulation, to provide continuity with legacy mainframe environments. GCOS 7 and GCOS 8 are separate branches of the operating system and continue to be developed alongside each other. History GECOS The GECOS operating system was developed by General Electric for the 36-bit GE-600 series in 1962–1964; GE released GECOS I (with a prototype 635) in April 1965, GECOS II in November 1965 and GECOS III (with time-sharing) in 1967. It bore a close resemblance architecturally to IBSYS on the IBM 7094 and less to DOS/360 on the System/360. H ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Kernel Mode
In computer science, hierarchical protection domains, often called protection rings, are mechanisms to protect data and functionality from faults (by improving fault tolerance) and malicious behavior (by providing computer security). Computer operating systems provide different levels of access to resources. A protection ring is one of two or more hierarchical ''levels'' or ''layers'' of privilege within the architecture of a computer system. This is generally hardware-enforced by some CPU architectures that provide different CPU modes at the hardware or microcode level. Rings are arranged in a hierarchy from most privileged (most trusted, usually numbered zero) to least privileged (least trusted, usually with the highest ring number). Ring 0 is the level with the most privileges and allows direct interaction with the physical hardware such as certain CPU functionality and chips on the motherboard. Special call gates between rings are provided to allow an outer ring to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Protection Ring
In computer science, hierarchical protection domains, often called protection rings, are mechanisms to protect data and functionality from faults (by improving fault tolerance) and malicious behavior (by providing computer security). Computer operating systems provide different levels of access to resources. A protection ring is one of two or more hierarchical ''levels'' or ''layers'' of privilege within the architecture of a computer system. This is generally hardware-enforced by some CPU architectures that provide different CPU modes at the hardware or microcode level. Rings are arranged in a hierarchy from most privileged (most trusted, usually numbered zero) to least privileged (least trusted, usually with the highest ring number). Ring 0 is the level with the most privileges and allows direct interaction with the physical hardware such as certain CPU functionality and chips on the motherboard. Special call gates between rings are provided to allow an outer ring to acce ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Honeywell
Honeywell International Inc. is an American publicly traded, multinational conglomerate corporation headquartered in Charlotte, North Carolina. It primarily operates in four areas of business: aerospace, building technologies, performance materials and technologies (PMT), and safety and productivity solutions (SPS). Honeywell is a Fortune 100 company, ranked 94th in 2021. In 2021 the corporation had a global workforce of approximately 99,000 employees, down from 113,000 in 2019. The current chairman and chief executive officer (CEO) is Darius Adamczyk. The corporation's current name, Honeywell International Inc., is a product of the merger of Honeywell Inc. and AlliedSignal in 1999. The corporation headquarters were consolidated with AlliedSignal's headquarters in Morristown, New Jersey; however, the combined company chose the name "Honeywell" because of the considerable brand recognition. Honeywell was a component of the Dow Jones Industrial Average index from 1999 to 2 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Honeywell 6180
The Honeywell 6000 series computers were rebadged versions of General Electric's 600-series mainframes manufactured by Honeywell International, Inc. from 1970 to 1989. Honeywell acquired the line when it purchased GE's computer division in 1970 and continued to develop them under a variety of names for many years. The high-end model was the 6080, with performance approximately 1 MIPS. Smaller models were the 6070, 6060, 6050, 6040, and 6030. In 1973 a low-end 6025 was introduced. The even-numbered models included an ''Enhanced Instruction Set'' feature (EIS), which added decimal arithmetic and storage-to-storage operations to the original word-oriented architecture. In 1973 Honeywell introduced the 6180, a 6000-series machine with addressing modifications to support the Multics operating system. In 1974 Honeywell released the 68/80 which added cache memory in each processor and support for a large (2-8 million word) directly addressable memory. In 1975 the 6000-series ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Time-sharing
In computing, time-sharing is the sharing of a computing resource among many users at the same time by means of multiprogramming and multi-tasking.DEC Timesharing (1965), by Peter Clark, The DEC Professional, Volume 1, Number 1 Its emergence as the prominent model of computing in the 1970s represented a major technological shift in the history of computing. By allowing many users to interact concurrently with a single computer, time-sharing dramatically lowered the cost of providing computing capability, made it possible for individuals and organizations to use a computer without owning one, and promoted the interactive use of computers and the development of new interactive applications. History Batch processing The earliest computers were extremely expensive devices, and very slow in comparison to later models. Machines were typically dedicated to a particular set of tasks and operated by control panels, the operator manually entering small programs via switches in order ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intel 80286
The Intel 80286 (also marketed as the iAPX 286 and often called Intel 286) is a 16-bit microprocessor that was introduced on February 1, 1982. It was the first 8086-based CPU with separate, non- multiplexed address and data buses and also the first with memory management and wide protection abilities. The 80286 used approximately 134,000 transistors in its original nMOS (HMOS) incarnation and, just like the contemporary 80186, it could correctly execute most software written for the earlier Intel 8086 and 8088 processors. The 80286 was employed for the IBM PC/AT, introduced in 1984, and then widely used in most PC/AT compatible computers until the early 1990s. In 1987, Intel shipped its five-millionth 80286 microprocessor. History and performance Intel's first 80286 chips were specified for a maximum clockrate of 5, 6 or 8 MHz and later releases for 12.5 MHz. AMD and Harris later produced 16 MHz, 20 MHz and 25 MHz parts, respectively. Inters ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |