|
Flooding (computer Networking)
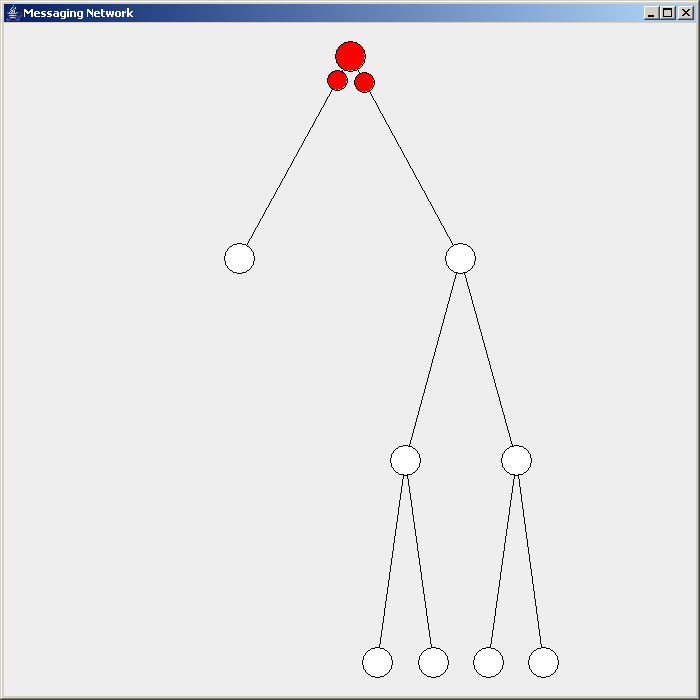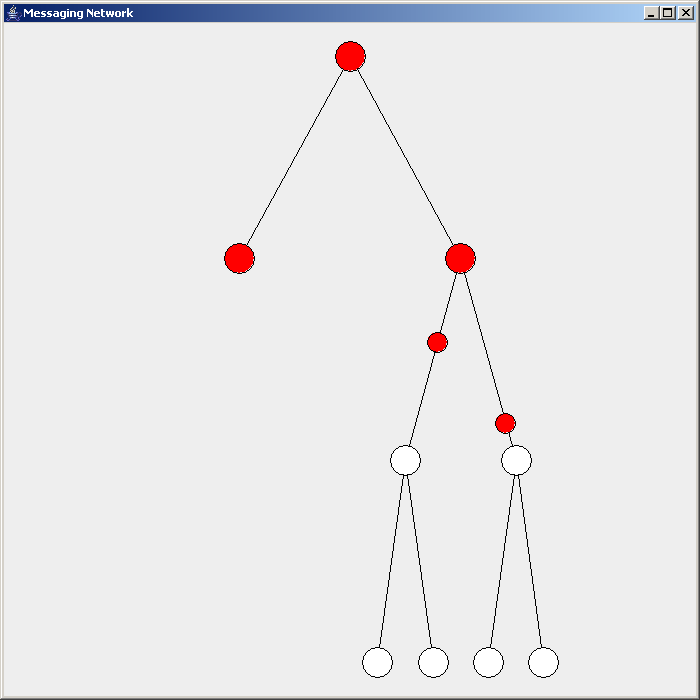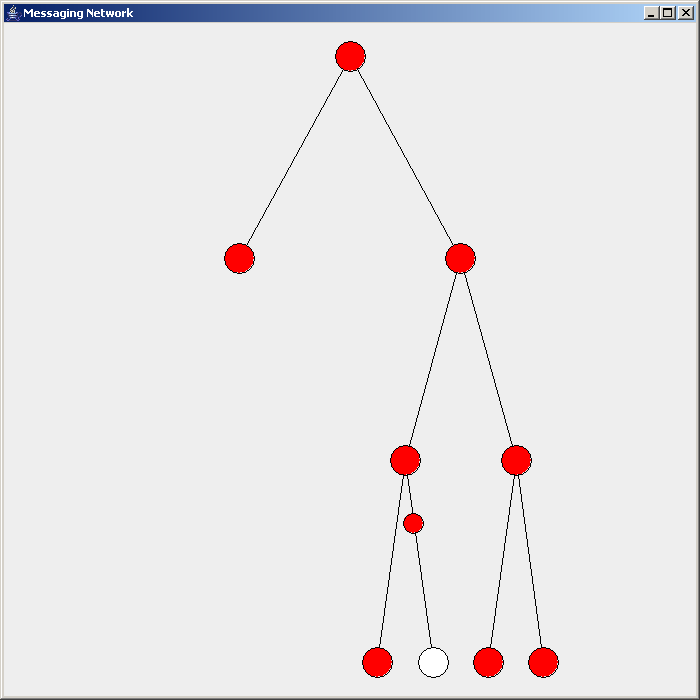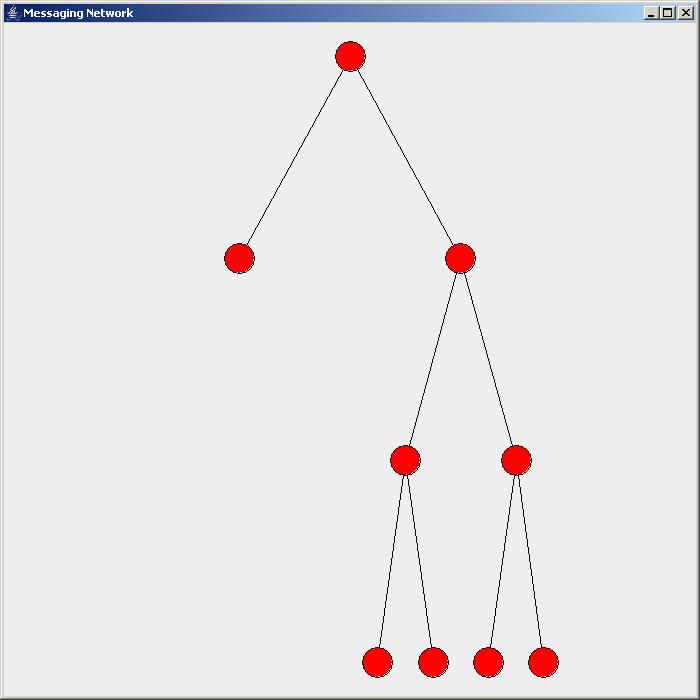
Flooding is used in computer networks routing algorithm in which every incoming packet is sent through every outgoing link except the one it arrived on. Flooding is used in bridging and in systems such as Usenet and peer-to-peer file sharing and as part of some routing protocols, including OSPF, DVMRP, and those used in ad-hoc wireless networks (WANETs). Types There are generally two types of flooding available, uncontrolled flooding and controlled flooding. In ''uncontrolled flooding'' each node unconditionally distributes packets to each of its neighbors. Without conditional logic to prevent indefinite recirculation of the same packet, broadcast storms are a hazard. ''Controlled flooding'' has its own two algorithms to make it reliable, SNCF ( Sequence Number Controlled Flooding) and RPF (reverse-path forwarding). In SNCF, the node attaches its own address and sequence number to the packet, since every node has a memory of addresses and sequence numbers. If it receives ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Flooding Routing
A flood is an overflow of water ( or rarely other fluids) that submerges land that is usually dry. In the sense of "flowing water", the word may also be applied to the inflow of the tide. Floods are an area of study of the discipline hydrology and are of significant concern in agriculture, civil engineering and public health. Human changes to the environment often increase the intensity and frequency of flooding, for example land use changes such as deforestation and removal of wetlands, changes in waterway course or flood controls such as with levees, and larger environmental issues such as climate change and sea level rise. In particular climate change's increased rainfall and extreme weather events increases the severity of other causes for flooding, resulting in more intense floods and increased flood risk. Flooding may occur as an overflow of water from water bodies, such as a river, lake, or ocean, in which the water overtops or breaks levees, resulting in some of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Network
A computer network is a set of computers sharing resources located on or provided by network nodes. The computers use common communication protocols over digital interconnections to communicate with each other. These interconnections are made up of telecommunication network technologies, based on physically wired, optical, and wireless radio-frequency methods that may be arranged in a variety of network topologies. The nodes of a computer network can include personal computers, servers, networking hardware, or other specialised or general-purpose hosts. They are identified by network addresses, and may have hostnames. Hostnames serve as memorable labels for the nodes, rarely changed after initial assignment. Network addresses serve for locating and identifying the nodes by communication protocols such as the Internet Protocol. Computer networks may be classified by many criteria, including the transmission medium used to carry signals, bandwidth, communications pro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
University Of Alberta
The University of Alberta, also known as U of A or UAlberta, is a Public university, public research university located in Edmonton, Alberta, Canada. It was founded in 1908 by Alexander Cameron Rutherford,"A Gentleman of Strathcona – Alexander Cameron Rutherford", Douglas R. Babcock, 1989, The University of Calgary Press, 2500 University Drive NW, Calgary, Alberta, Canada, the first premier of Alberta, and Henry Marshall Tory,"Henry Marshall Tory, A Biography", originally published 1954, current edition January 1992, E.A. Corbett, Toronto: Ryerson Press, the university's first president. It was enabled through the Post-secondary Learning Act''.'' The university is considered a "comprehensive academic and research university" (CARU), which means that it offers a range of academic and professional programs that generally lead to undergraduate and graduate level credentials. The university comprises four campuses in Edmonton, an Augustana Campus in Camrose, Alberta, Camrose, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pearson Education
Pearson Education is a British-owned education publishing and assessment service to schools and corporations, as well for students directly. Pearson owns educational media brands including Addison–Wesley, Peachpit, Prentice Hall, eCollege, Longman, Scott Foresman, and others. Pearson is part of Pearson plc, which formerly owned the ''Financial Times''. It claims to have been formed in 1840, with the current incarnation of the company created when Pearson plc purchased the education division of Simon & Schuster (including Prentice Hall and Allyn & Bacon) from Viacom and merged it with its own education division, Addison-Wesley Longman, to form Pearson Education. Pearson Education was rebranded to Pearson in 2011 and split into an International and a North American division. Although Pearson generates approximately 60 percent of its sales in North America, it operates in more than 70 countries. Pearson International is headquartered in London, and maintains offices across ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spanning Tree Protocol
The Spanning Tree Protocol (STP) is a network protocol that builds a loop-free logical topology for Ethernet networks. The basic function of STP is to prevent bridge loops and the broadcast radiation that results from them. Spanning tree also allows a network design to include backup links providing fault tolerance if an active link fails. As the name suggests, STP creates a spanning tree that characterizes the relationship of nodes within a network of connected layer-2 bridges, and disables those links that are not part of the spanning tree, leaving a single active path between any two network nodes. STP is based on an algorithm that was invented by Radia Perlman while she was working for Digital Equipment Corporation. In 2001, the IEEE introduced Rapid Spanning Tree Protocol (RSTP) as 802.1w. RSTP provides significantly faster recovery in response to network changes or failures, introducing new convergence behaviors and bridge port roles to do this. RSTP was designed to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Multicast
In computer networking, multicast is group communication where data transmission is addressed to a group of destination computers simultaneously. Multicast can be one-to-many or many-to-many distribution. Multicast should not be confused with physical layer point-to-multipoint communication. Group communication may either be application layer multicast or network-assisted multicast, where the latter makes it possible for the source to efficiently send to the group in a single transmission. Copies are automatically created in other network elements, such as routers, switches and cellular network base stations, but only to network segments that currently contain members of the group. Network assisted multicast may be implemented at the data link layer using one-to-many addressing and switching such as Ethernet multicast addressing, Asynchronous Transfer Mode (ATM), point-to-multipoint virtual circuits (P2MP) or InfiniBand multicast. Network-assisted multicast may also be imp ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Flood Search Routing
In a telephone network, flood search routing is non-deterministic routing in which a dialed number received at a switch is transmitted to all switches, ''i.e.,'' flooded, in the area code directly connected to that switch; if the dialed number is not an affiliated subscriber at that switch, the number is then retransmitted to all directly connected switches, and then routed through the switch that has the dialed number corresponding to the particular user end instrument affiliated with it. All digits of the numbering plan are used to identify a particular subscriber. Flood search routing allows subscribers to have telephone numbers independent of switch codes. Flood search routing provides the highest probability that a telephone call will go through even though a number of switches and links fail. Flood search routing is used in military telecommunication systems, such as the mobile subscriber equipment (MSE) system. See also *Flooding (computer networking) Flooding is use ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Broadcasting (networking)
In computer networking, telecommunication and information theory, broadcasting is a method of transferring a message to all recipients simultaneously. Broadcasting can be performed as a high-level operation in a program, for example, broadcasting in Message Passing Interface, or it may be a low-level networking operation, for example broadcasting on Ethernet. All-to-all communication is a computer communication method in which each sender transmits messages to all receivers within a group. In networking this can be accomplished using broadcast or multicast. This is in contrast with the point-to-point method in which each sender communicates with one receiver. Addressing methods There are four principal addressing methods in the Internet Protocol: Overview In computer networking, broadcasting refers to transmitting a packet that will be received by every device on the network. In practice, the scope of the broadcast is limited to a broadcast domain. Broadcasting is th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Digital Addressable Lighting Interface
Digital Addressable Lighting Interface (DALI) is a trademark for network-based products that control lighting. The underlying technology was established by a consortium of lighting equipment manufacturers as a successor for 1-10 V/ lighting control systems, and as an open standard alternative to several proprietary protocols. The DALI, DALI-2 and D4i trademarks are owned by the lighting industry alliance, DiiADigital Illumination Interface Alliance. DALI is specified by a series of technical standards in IEC 62386. Standards conformance ensures that equipment from different manufacturers will interoperate. The DALI trademark is allowed on devices that comply with the DiiA testing and certification requirements, and are listed as either registered (DALI version-1) or certifiedDALI-2 on the DiiA website - an extension of DALI-2 - was added by DiiA in November 2019. Members of the AG DALI were allowed to use the DALI trademark until the DALI working party was dissolved on 30 M ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bluetooth Mesh Networking
Bluetooth Mesh is a computer mesh networking standard based on Bluetooth Low Energy that allows for many-to-many communication over Bluetooth radio. The Bluetooth Mesh specifications were defined in the Mesh Profile and Mesh Model specifications by the Bluetooth Special Interest Group (Bluetooth SIG). Bluetooth Mesh was conceived in 2014 and adopted on . Overview Bluetooth Mesh is a mesh networking standard that operates on a flood network principle. It's based on the nodes relaying the messages: every relay node that receives a network packet that authenticates against a known network key that is not in message cache, that has a TTL ≥ 2 can be retransmitted with TTL = TTL - 1. Message caching is used to prevent relaying messages recently seen. Communication is carried in the messages that may be up to 384 bytes long, when using Segmentation and Reassembly (SAR) mechanism, but most of the messages fit in one segment, that is 11 bytes. Each message starts with an opcode, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Link-state Advertisement
The link-state advertisement (LSA) is a basic communication means of the OSPF routing protocol for the Internet Protocol (IP). It communicates the router's local routing topology to all other local routers in the same OSPF area. OSPF is designed for scalability, so some LSAs are not flooded out on all interfaces, but only on those that belong to the appropriate area. In this way detailed information can be kept localized, while summary information is flooded to the rest of the network. The original IPv4-only OSPFv2 and the newer IPv6-compatible OSPFv3 have broadly similar LSA types. Types The LSA types defined in OSPF are as follows: The opaque LSAs, types 9, 10, and 11, are designated for upgrades to OSPF for application-specific purposes. For example, OSPF-TE has traffic engineering extensions to be used by RSVP-TE in Multiprotocol Label Switching (MPLS). Opaque LSAs are used to flood link color and bandwidth information. Standard link-state database (LSDB) flooding mechanisms ar ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Routing Loop
A routing loop is a common problem with various types of networks, particularly computer networks. They are formed when an error occurs in the operation of the routing algorithm, and as a result, in a group of nodes, the path to a particular destination forms a loop. In the simplest version, a routing loop of size two, node A thinks that the path to some destination (call it C) is through its neighbouring node, node B. At the same time, node B thinks that the path to C starts at node A. Thus, whenever traffic for C arrives at either A or B, it will loop endlessly between A and B, unless some mechanism exists to prevent that behaviour. How a routing loop can form For example, in this illustration, node A is transmitting data to node C via node B. If the link between nodes B and C goes down and B has not yet informed node A about the breakage, node A transmits the data to node B assuming that the link A-B-C is operational and of lowest cost. Node B knows of the broken link and trie ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |