|
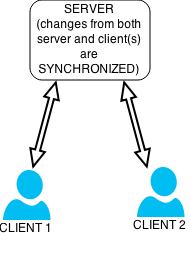
File Synchronization
File synchronization (or syncing) in computing is the process of ensuring that computer files in two or more locations are updated via certain rules. In ''one-way file synchronization'', also called Web mirror, mirroring, updated files are copied from a source location to one or more target locations, but no files are copied back to the source location. In ''two-way file synchronization'', updated files are copied in both directions, usually with the purpose of keeping the two locations identical to each other. In this article, the term synchronization refers exclusively to two-way file synchronization. File system, File synchronization is commonly used for home backups on external hard drives or updating for transport on USB flash drives. BitTorrent Sync, Dropbox (service), Dropbox, Skysite, SKYSITE, Nextcloud, OneDrive, Google Drive and iCloud are prominent products. Some backup software also support real-time file sync. The automatic process prevents copying already identical fi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer File
A computer file is a System resource, resource for recording Data (computing), data on a Computer data storage, computer storage device, primarily identified by its filename. Just as words can be written on paper, so too can data be written to a computer file. Files can be shared with and transferred between computers and Mobile device, mobile devices via removable media, Computer networks, networks, or the Internet. Different File format, types of computer files are designed for different purposes. A file may be designed to store a written message, a document, a spreadsheet, an Digital image, image, a Digital video, video, a computer program, program, or any wide variety of other kinds of data. Certain files can store multiple data types at once. By using computer programs, a person can open, read, change, save, and close a computer file. Computer files may be reopened, modified, and file copying, copied an arbitrary number of times. Files are typically organized in a file syst ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet
The Internet (or internet) is the Global network, global system of interconnected computer networks that uses the Internet protocol suite (TCP/IP) to communicate between networks and devices. It is a internetworking, network of networks that consists of Private network, private, public, academic, business, and government networks of local to global scope, linked by a broad array of electronic, Wireless network, wireless, and optical networking technologies. The Internet carries a vast range of information resources and services, such as the interlinked hypertext documents and Web application, applications of the World Wide Web (WWW), email, electronic mail, internet telephony, streaming media and file sharing. The origins of the Internet date back to research that enabled the time-sharing of computer resources, the development of packet switching in the 1960s and the design of computer networks for data communication. The set of rules (communication protocols) to enable i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
List Of Backup Software
This is a list of notable backup software that performs data backups. Archivers, transfer protocols, and version control systems are often used for backups but only software focused on backup is listed here. See Comparison of backup software for features. Free and open-source software Proprietary Defunct software See also * Comparison of file synchronization software * Comparison of online backup services * Data recovery * File synchronization * List of data recovery software * Remote backup service * Tape management system Notes References {{Reflist * Backup software In information technology, a backup, or data backup is a copy of computer data taken and stored elsewhere so that it may be used to restore the original after a data loss event. The verb form, referring to the process of doing so, is " back up ... * ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Shared File Access
In computing, a shared resource, or network share, is a computer resource made available from one host to other hosts on a computer network. It is a device or piece of information on a computer that can be remotely accessed from another computer transparently as if it were a resource in the local machine. Network sharing is made possible by inter-process communication over the network. Some examples of shareable resources are computer programs, data, storage devices, and printers. E.g. shared file access (also known as disk sharing and folder sharing), shared printer access, shared scanner access, etc. The shared resource is called a shared disk, shared folder or shared document The term ''file sharing'' traditionally means shared file access, especially in the context of operating systems and LAN and Intranet services, for example in Microsoft Windows documentation. Though, as BitTorrent and similar applications became available in the early 2000s, the term ''file sharing'' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Remote Backup Service
A remote, online, or managed backup service, sometimes marketed as cloud backup or backup-as-a-service, is a service that provides users with a system for the backup, storage, and recovery of computer files. Online backup providers are companies that provide this type of service to end users (or clients). Such backup services are considered a form of cloud computing. Online backup systems are typically built for a client software program that runs on a given schedule. Some systems run once a day, usually at night while computers aren't in use. Other newer cloud backup services run continuously to capture changes to user systems nearly in real-time. The online backup system typically collects, compresses, encrypts, and transfers the data to the remote backup service provider's servers or off-site hardware. There are many products on the market – all offering different feature sets, service levels, and types of encryption. Providers of this type of service frequently target ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Synchronization
Data synchronization is the process of establishing consistency between source and target data stores, and the continuous harmonization of the data over time. It is fundamental to a wide variety of applications, including file synchronization and mobile device synchronization. Data synchronization can also be useful in encryption for synchronizing public key servers. Data synchronization is needed to update and keep multiple copies of a set of data coherent with one another or to maintain data integrity, Figure 3. For example, database replication is used to keep multiple copies of data synchronized with database servers that store data in different locations. Examples Examples include: * File synchronization, such as syncing a hand-held MP3 player to a desktop computer; * Cluster file systems, which are file systems that maintain data or indexes in a coherent fashion across a whole computing cluster; * Cache coherency, maintaining multiple copies of data in sync across ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Comparison
Editing documents, program code, or any data always risks introducing errors. Displaying the differences between two or more sets of data, file comparison tools can make computing simpler, and more efficient by focusing on new data and ignoring what did not change. Generically known as a diff after the Unix diff utility, there are a range of ways to compare data sources and display the results. Some widely used file comparison programs are diff, cmp, FileMerge, WinMerge, Beyond Compare, and File Compare. Because understanding changes is important to writers of code or documents, many text editors and word processors include the functionality necessary to see the changes between different versions of a file or document. Method types The most efficient method of finding differences depends on the source data, and the nature of the changes. One approach is to find the longest common subsequence between two files, then regard the non-common data as an insertion, or a delet ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Comparison Of Online Backup Services
This is a comparison of online backup services. Online backup is a special kind of online storage service; however, various products that are designed for file storage may not have features or characteristics that others designed for backup have. Online Backup usually requires a backup client program. A browser-only online storage service is usually not considered a valid online backup service. Online folder sync services can be used for backup purposes. However, some Online Folder Sync services may not provide a safe Online Backup. If a file is accidentally locally corrupted or deleted, it depends on the versioning features of a Folder Sync service, whether this file will still be retrievable. Comparison Legend *Windows/Linux/Mac/iOS/ Android/BlackBerry: Supported operating systems for thick client (native binary application), which provide background data transmission and setting services. *Zero knowledge: The service provider has no knowledge of the user's encryption key, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Comparison Of File Synchronization Software
Comparison or comparing is the act of evaluating two or more things by determining the relevant, comparable characteristics of each thing, and then determining which characteristics of each are similar to the other, which are different, and to what degree. Where characteristics are different, the differences may then be evaluated to determine which thing is best suited for a particular purpose. The description of similarities and differences found between the two things is also called a comparison. Comparison can take many distinct forms, varying by field: To compare things, they must have characteristics that are similar enough in relevant ways to merit comparison. If two things are too different to compare in a useful way, an attempt to compare them is colloquially referred to in English as "comparing apples and oranges." Comparison is widely used in society, in science and the arts. General usage Comparison is a natural activity, which even animals engage in when decidin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Backup Software
In information technology, a backup, or data backup is a copy of computer data taken and stored elsewhere so that it may be used to restore the original after a data loss event. The verb form, referring to the process of doing so, is " back up", whereas the noun and adjective form is " backup". Backups can be used to recover data after its loss from data deletion or corruption, or to recover data from an earlier time. Backups provide a simple form of IT disaster recovery; however not all backup systems are able to reconstitute a computer system or other complex configuration such as a computer cluster, active directory server, or database server. A backup system contains at least one copy of all data considered worth saving. The data storage requirements can be large. An information repository model may be used to provide structure to this storage. There are different types of data storage devices used for copying backups of data that is already in secondary storage on ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
HTTPS
Hypertext Transfer Protocol Secure (HTTPS) is an extension of the Hypertext Transfer Protocol (HTTP). It uses encryption for secure communication over a computer network, and is widely used on the Internet. In HTTPS, the communication protocol is encrypted using Transport Layer Security (TLS) or, formerly, Secure Sockets Layer (SSL). The protocol is therefore also referred to as HTTP over TLS, or HTTP over SSL. The principal motivations for HTTPS are authentication of the accessed website and protection of the privacy and integrity of the exchanged data while it is in transit. It protects against man-in-the-middle attacks, and the bidirectional block cipher encryption of communications between a client and server protects the communications against eavesdropping and tampering. The authentication aspect of HTTPS requires a trusted third party to sign server-side digital certificates. This was historically an expensive operation, which meant fully authenticated HTTPS conn ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
End-to-end Encryption
End-to-end encryption (E2EE) is a method of implementing a secure communication system where only communicating users can participate. No one else, including the system provider, telecom providers, Internet providers or malicious actors, can access the cryptographic keys needed to read or send messages. End-to-end encryption prevents data from being read or secretly modified, except by the true sender and intended recipients. Frequently, the messages are relayed from the sender to the recipients by a service provider. However, messages are encrypted by the sender and no third party, including the service provider, has the means to decrypt them. The recipients retrieve the encrypted messages and decrypt them independently. Since third parties cannot decrypt the data being communicated or stored, services that provide end-to-end encryption are better at protecting user data when they are affected by data breaches. Such services are also unable to share user data with governm ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |