|
Exec Shield
Exec Shield is a project started at Red Hat, Inc in late 2002 with the aim of reducing the risk of worm or other automated remote attacks on Linux systems. The first result of the project was a security patch for the Linux kernel that emulates an NX bit on x86 CPUs that lack a native NX implementation in hardware. While the Exec Shield project has had many other components, some people refer to this first patch as Exec Shield. The first Exec Shield patch attempts to flag data memory as non-executable and program memory as non-writeable. This suppresses many security exploits, such as those stemming from buffer overflows and other techniques relying on overwriting data and inserting code into those structures. Exec Shield also supplies some address space layout randomization for the mmap() and heap base. The patch additionally increases the difficulty of inserting and executing shellcode, rendering most exploits ineffective. No application recompilation is necessary to fully u ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Red Hat
Red Hat, Inc. is an American software company that provides open source software products to enterprises. Founded in 1993, Red Hat has its corporate headquarters in Raleigh, North Carolina, with other offices worldwide. Red Hat has become associated to a large extent with its enterprise operating system Red Hat Enterprise Linux. With the acquisition of open-source enterprise middleware vendor JBoss, Red Hat also offers Red Hat Virtualization (RHV), an enterprise virtualization product. Red Hat provides storage, operating system platforms, middleware, applications, management products, and support, training, and consulting services. Red Hat creates, maintains, and contributes to many free software projects. It has acquired several proprietary software product codebases through corporate mergers and acquisitions and has released such software under open source licenses. , Red Hat is the second largest corporate contributor to the Linux kernel version 4.14 after Intel. On ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Position-independent Code
In computing, position-independent code (PIC) or position-independent executable (PIE) is a body of machine code that, being placed somewhere in the primary memory, executes properly regardless of its absolute address. PIC is commonly used for shared libraries, so that the same library code can be loaded in a location in each program address space where it does not overlap with other memory in use (for example, other shared libraries). PIC was also used on older computer systems that lacked an MMU, so that the operating system could keep applications away from each other even within the single address space of an MMU-less system. Position-independent code can be executed at any memory address without modification. This differs from absolute code, which must be loaded at a specific location to function correctly, and load-time locatable (LTL) code, in which a linker or program loader modifies a program before execution so it can be run only from a particular memory location. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Linux
Linux ( or ) is a family of open-source Unix-like operating systems based on the Linux kernel, an operating system kernel first released on September 17, 1991, by Linus Torvalds. Linux is typically packaged as a Linux distribution, which includes the kernel and supporting system software and libraries, many of which are provided by the GNU Project. Many Linux distributions use the word "Linux" in their name, but the Free Software Foundation uses the name "GNU/Linux" to emphasize the importance of GNU software, causing some controversy. Popular Linux distributions include Debian, Fedora Linux, and Ubuntu, the latter of which itself consists of many different distributions and modifications, including Lubuntu and Xubuntu. Commercial distributions include Red Hat Enterprise Linux and SUSE Linux Enterprise. Desktop Linux distributions include a windowing system such as X11 or Wayland, and a desktop environment such as GNOME or KDE Plasma. Distributions intended for ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
StackGuard
Buffer overflow protection is any of various techniques used during software development to enhance the security of executable programs by detecting buffer overflows on stack-allocated variables, and preventing them from causing program misbehavior or from becoming serious security vulnerabilities. A stack buffer overflow occurs when a program writes to a memory address on the program's call stack outside of the intended data structure, which is usually a fixed-length buffer. Stack buffer overflow bugs are caused when a program writes more data to a buffer located on the stack than what is actually allocated for that buffer. This almost always results in corruption of adjacent data on the stack, which could lead to program crashes, incorrect operation, or security issues. Typically, buffer overflow protection modifies the organization of stack-allocated data so it includes a '' canary'' value that, when destroyed by a stack buffer overflow, shows that a buffer preceding it in memo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Openwall
The Openwall Project is a source for various software, including Openwall GNU/*/Linux (Owl), a security-enhanced Linux distribution designed for servers. Openwall patches and security extensions have been included into many major Linux distributions. As the name implies, Openwall GNU/*/Linux draws source code and design concepts from numerous sources, most importantly to the project is its usage of the Linux kernel and parts of the GNU userland, others include the BSDs, such as OpenBSD for its OpenSSH suite and the inspiration behind its own Blowfish-based crypt for password hashing, compatible with the OpenBSD implementation. Public domain software The Openwall project maintains also a list of algorithms and source code which is public domain software. Openwall GNU/*/Linux releases LWN.net reviewed Openwall Linux 3.0. They wrote: ''PoC, , GTFO'' Issues of the ''International Journal of Proof-of-Concept or Get The Fuck Out'' (''PoC, , GTFO'') are mirrored by th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ulrich Drepper
Ulrich (), is a German given name, derived from Old High German ''Uodalrich'', ''Odalric''. It is composed of the elements '' uodal-'' meaning "(noble) heritage" and ''-rich'' meaning "rich, powerful". Attested from the 8th century as the name of Alamannic nobility, the name is popularly given from the high medieval period in reference to Saint Ulrich of Augsburg (canonized 993). There is also a surname Ulrich. It is most prevalent in Germany and has the highest density in SwitzerlandThis last name was found in the United States around the year 1840Most Americans with the last name were concentrated in Pennsylvania, which was home to many Pennsylvania Dutch, German immigrant communities. Nowadays in the United States, the name is distributed largely in the Pennsylvania-Ohio regio History Documents record the Old High German name ''Oadalrich'' or ''Uodalrich'' from the later 8th century in Alamannia. The related name ''Adalric'' (Anglo-Saxon cognate '' Æthelric'') is attested fr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fedora (operating System)
Fedora Linux is a Linux distribution developed by the Fedora Project. Fedora contains software distributed under various free and open-source licenses and aims to be on the leading edge of open-source technologies. Fedora is the upstream source for Red Hat Enterprise Linux. Since the release of Fedora 35, six different editions are made available tailored to personal computer, server, cloud computing, container and Internet of Things installations. A new version of Fedora Linux is released every six months. , Fedora Linux has an estimated 1.2 million users, including Linus Torvalds (), creator of the Linux kernel. Features Fedora has a reputation for focusing on innovation, integrating new technologies early on and working closely with upstream Linux communities. Making changes upstream instead of specifically for Fedora Linux ensures that the changes are available to all Linux distributions. Fedora Linux has a relatively short life cycle: each version is usually supported ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
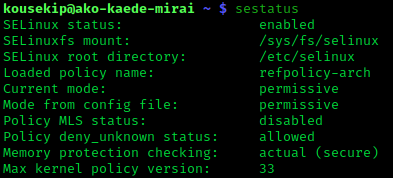
Security-Enhanced Linux
Security-Enhanced Linux (SELinux) is a Linux kernel security module that provides a mechanism for supporting access control security policies, including mandatory access controls (MAC). SELinux is a set of kernel modifications and user-space tools that have been added to various Linux distributions. Its architecture strives to separate enforcement of security decisions from the security policy, and streamlines the amount of software involved with security policy enforcement. The key concepts underlying SELinux can be traced to several earlier projects by the United States National Security Agency (NSA). Overview The NSA Security-enhanced Linux Team describes NSA SELinux as a set of patches to the Linux kernel and utilities to provide a strong, flexible, mandatory access control (MAC) architecture into the major subsystems of the kernel. It provides an enhanced mechanism to enforce the separation of information based on confidentiality and integrity requirements, which allows ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mprotect
Memory protection is a way to control memory access rights on a computer, and is a part of most modern instruction set architectures and operating systems. The main purpose of memory protection is to prevent a process from accessing memory that has not been allocated to it. This prevents a bug or malware within a process from affecting other processes, or the operating system itself. Protection may encompass all accesses to a specified area of memory, write accesses, or attempts to execute the contents of the area. An attempt to access unauthorized memory results in a hardware fault, e.g., a segmentation fault, storage violation exception, generally causing abnormal termination of the offending process. Memory protection for computer security includes additional techniques such as address space layout randomization and executable space protection. Methods Segmentation Segmentation refers to dividing a computer's memory into segments. A reference to a memory location incl ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Virtual Memory
In computing, virtual memory, or virtual storage is a memory management technique that provides an "idealized abstraction of the storage resources that are actually available on a given machine" which "creates the illusion to users of a very large (main) memory". The computer's operating system, using a combination of hardware and software, maps memory addresses used by a program, called '' virtual addresses'', into ''physical addresses'' in computer memory. Main storage, as seen by a process or task, appears as a contiguous address space or collection of contiguous segments. The operating system manages virtual address spaces and the assignment of real memory to virtual memory. Address translation hardware in the CPU, often referred to as a memory management unit (MMU), automatically translates virtual addresses to physical addresses. Software within the operating system may extend these capabilities, utilizing, e.g., disk storage, to provide a virtual address space that c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Buffer Overflow Protection
Buffer overflow protection is any of various techniques used during software development to enhance the security of executable programs by detecting buffer overflows on stack-allocated variables, and preventing them from causing program misbehavior or from becoming serious security vulnerabilities. A stack buffer overflow occurs when a program writes to a memory address on the program's call stack outside of the intended data structure, which is usually a fixed-length buffer. Stack buffer overflow bugs are caused when a program writes more data to a buffer located on the stack than what is actually allocated for that buffer. This almost always results in corruption of adjacent data on the stack, which could lead to program crashes, incorrect operation, or security issues. Typically, buffer overflow protection modifies the organization of stack-allocated data so it includes a '' canary'' value that, when destroyed by a stack buffer overflow, shows that a buffer preceding it in memo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
.jpg)