|
Embedded HTTP Server
An embedded HTTP server is an HTTP server used in an embedded system. The HTTP server is usually implemented as a software component of an application (embedded) system that controls and/or monitors a machine with mechanical and/or electrical parts. The HTTP server implements the HTTP protocol in order to allow communications with one or more local or remote users using a browser. The aim is to let users to interact with information provided by the embedded system (user interface, data monitoring, data logging, data configuration, etc.) via network, without using traditional peripherals required for local user interfaces ( display, keyboard, etc.). In some cases the functionalities provided via HTTP server allow also program-to-program communications, e.g. to retrieve data logged about the monitored machine, etc. Usages Examples of usage within an embedded application might be (e.g.): * to provide a thin client interface for a traditional application; * to provide indexin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
2453 IP Video Server
__NOTOC__ Year 453 ( CDLIII) was a common year starting on Thursday (link will display the full calendar) of the Julian calendar. At the time, it was known as the Year of the Consulship of Opilio and Vincomalus (or, less frequently, year 1206 '' Ab urbe condita''). The denomination 453 for this year has been used since the early medieval period, when the Anno Domini calendar era became the prevalent method in Europe for naming years. Events By place Byzantium * July – Empress Pulcheria dies of natural causes at Constantinople. She has commissioned many new churches in the city during her reign. Her death leaves Flavius Aspar (''magister militum'') as the dominant influence on her husband, Marcian. * Anthemius marries Marcia Euphemia, daughter of Marcian, and is elevated to the rank of ''comes''. He is sent to the Danubian frontier to rebuild the border defences. * The late Attila's other sons Dengizich and Ernakh, establish their kingdoms north of the Black S ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Debugging
In computer programming and software development, debugging is the process of finding and resolving '' bugs'' (defects or problems that prevent correct operation) within computer programs, software, or systems. Debugging tactics can involve interactive debugging, control flow analysis, unit testing, integration testing, log file analysis, monitoring at the application or system level, memory dumps, and profiling. Many programming languages and software development tools also offer programs to aid in debugging, known as '' debuggers''. Etymology The terms "bug" and "debugging" are popularly attributed to Admiral Grace Hopper in the 1940s. While she was working on a Mark II computer at Harvard University, her associates discovered a moth stuck in a relay and thereby impeding operation, whereupon she remarked that they were "debugging" the system. However, the term "bug", in the sense of "technical error", dates back at least to 1878 and Thomas Edison who describes the " ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Operating System
An operating system (OS) is system software that manages computer hardware, software resources, and provides common services for computer programs. Time-sharing operating systems schedule tasks for efficient use of the system and may also include accounting software for cost allocation of processor time, mass storage, printing, and other resources. For hardware functions such as input and output and memory allocation, the operating system acts as an intermediary between programs and the computer hardware, although the application code is usually executed directly by the hardware and frequently makes system calls to an OS function or is interrupted by it. Operating systems are found on many devices that contain a computer from cellular phones and video game consoles to web servers and supercomputers. The dominant general-purpose personal computer operating system is Microsoft Windows with a market share of around 74.99%. macOS by Apple Inc. is in second place (14.84%), ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cross Compilation
A cross compiler is a compiler capable of creating executable code for a platform other than the one on which the compiler is running. For example, a compiler that runs on a PC but generates code that runs on an Android smartphone is a cross compiler. A cross compiler is useful to compile code for multiple platforms from one development host. Direct compilation on the target platform might be infeasible, for example on embedded systems with limited computing resources. Cross compilers are distinct from source-to-source compilers. A cross compiler is for cross-platform software generation of machine code, while a source-to-source compiler translates from one coding language to another in text code. Both are programming tools. Use The fundamental use of a cross compiler is to separate the build environment from target environment. This is useful in several situations: * Embedded computers where a device has highly limited resources. For example, a microwave oven will h ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Read-only Memory
Read-only memory (ROM) is a type of non-volatile memory used in computers and other electronic devices. Data stored in ROM cannot be electronically modified after the manufacture of the memory device. Read-only memory is useful for storing software that is rarely changed during the life of the system, also known as firmware. Software applications (like video games) for programmable devices can be distributed as plug-in cartridges containing ROM. Strictly speaking, ''read-only memory'' refers to memory that is hard-wired, such as diode matrix or a mask ROM integrated circuit (IC), which cannot be electronically changed after manufacture. Although discrete circuits can be altered in principle, through the addition of bodge wires and/or the removal or replacement of components, ICs cannot. Correction of errors, or updates to the software, require new devices to be manufactured and to replace the installed device. Floating-gate ROM semiconductor memory in the form of erasab ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Random-access Memory
Random-access memory (RAM; ) is a form of computer memory that can be read and changed in any order, typically used to store working data and machine code. A random-access memory device allows data items to be read or written in almost the same amount of time irrespective of the physical location of data inside the memory, in contrast with other direct-access data storage media (such as hard disks, CD-RWs, DVD-RWs and the older magnetic tapes and drum memory), where the time required to read and write data items varies significantly depending on their physical locations on the recording medium, due to mechanical limitations such as media rotation speeds and arm movement. RAM contains multiplexing and demultiplexing circuitry, to connect the data lines to the addressed storage for reading or writing the entry. Usually more than one bit of storage is accessed by the same address, and RAM devices often have multiple data lines and are said to be "8-bit" or "16-bit", etc. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ubiquitous Computing
Ubiquitous computing (or "ubicomp") is a concept in software engineering, hardware engineering and computer science where computing is made to appear anytime and everywhere. In contrast to desktop computing, ubiquitous computing can occur using any device, in any location, and in any format. A user interacts with the computer, which can exist in many different forms, including laptop computers, tablets, smart phones and terminals in everyday objects such as a refrigerator or a pair of glasses. The underlying technologies to support ubiquitous computing include Internet, advanced middleware, operating system, mobile code, sensors, microprocessors, new I/O and user interfaces, computer networks, mobile protocols, location and positioning, and new materials. This paradigm is also described as pervasive computing, ambient intelligence, or "everyware". Each term emphasizes slightly different aspects. When primarily concerning the objects involved, it is also known as physical ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Home Network
A home network or home area network (HAN) is a type of computer network that facilitates communication among devices within the close vicinity of a home. Devices capable of participating in this network, for example, smart devices such as network printers and handheld mobile computers, often gain enhanced emergent capabilities through their ability to interact. These additional capabilities can be used to increase the quality of life inside the home in a variety of ways, such as automation of repetitive tasks, increased personal productivity, enhanced home security, and easier access to entertainment. Origins Establishing this kind of network is often necessary for sharing residential Internet access to all networked devices. Based on techniques to mitigate IPv4 address exhaustion, most Internet service providers provide only a single wide area network-facing IP address for each residential customer. Therefore, such networks require network address translation in the network ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Web Browser
A web browser is application software for accessing websites. When a user requests a web page from a particular website, the browser retrieves its files from a web server and then displays the page on the user's screen. Browsers are used on a range of devices, including desktops, laptops, tablets, and smartphones. In 2020, an estimated 4.9 billion people used a browser. The most used browser is Google Chrome, with a 65% global market share on all devices, followed by Safari with 18%. A web browser is not the same thing as a search engine, though the two are often confused. A search engine is a website that provides links to other websites. However, to connect to a website's server and display its web pages, a user must have a web browser installed. In some technical contexts, browsers are referred to as user agents. Function The purpose of a web browser is to fetch content from the World Wide Web or from local storage and display it on a user's device. This proce ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Router (computing)
A router is a networking device that forwards data packets between computer networks. Routers perform the traffic directing functions between networks and on the global Internet. Data sent through a network, such as a web page or email, is in the form of data packets. A packet is typically forwarded from one router to another router through the networks that constitute an internetwork (e.g. the Internet) until it reaches its destination node. A router is connected to two or more data lines from different IP networks. When a data packet comes in on one of the lines, the router reads the network address information in the packet header to determine the ultimate destination. Then, using information in its routing table or routing policy, it directs the packet to the next network on its journey. The most familiar type of IP routers are home and small office routers that simply forward IP packets between the home computers and the Internet. More sophisticated routers, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
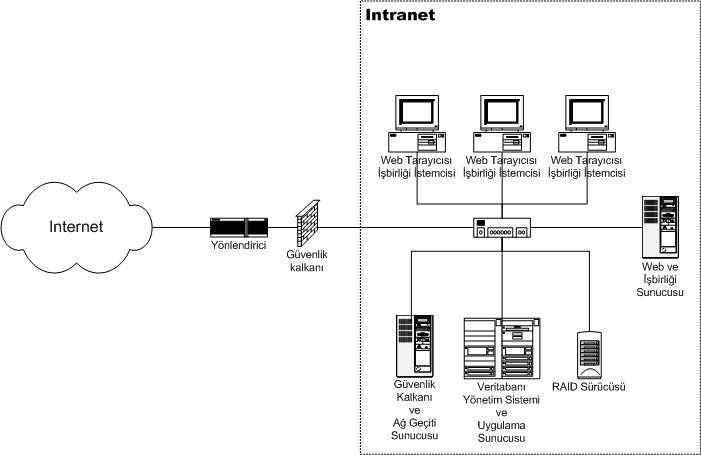
Intranet
An intranet is a computer network for sharing information, easier communication, collaboration tools, operational systems, and other computing services within an organization, usually to the exclusion of access by outsiders. The term is used in contrast to public networks, such as the Internet, but uses the same technology based on the Internet protocol suite. An organization-wide intranet can constitute an important focal point of internal communication and collaboration, and provide a single starting point to access internal and external resources. In its simplest form, an intranet is established with the technologies for local area networks (LANs) and wide area networks (WANs). Many modern intranets have search engines, user profiles, blogs, mobile apps with notifications, and events planning within their infrastructure. An intranet is sometimes contrasted to an extranet. While an intranet is generally restricted to employees of the organization, extranets may also be accesse ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Firewall (computing)
In computing, a firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted network and an untrusted network, such as the Internet. History The term '' firewall'' originally referred to a wall intended to confine a fire within a line of adjacent buildings. Later uses refer to similar structures, such as the metal sheet separating the engine compartment of a vehicle or aircraft from the passenger compartment. The term was applied in the late 1980s to network technology that emerged when the Internet was fairly new in terms of its global use and connectivity. The predecessors to firewalls for network security were routers used in the late 1980s. Because they already segregated networks, routers could apply filtering to packets crossing them. Before it was used in real-life computing, the term appeared in the 1983 computer-hacking movi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |