|
Double Hashing
Double hashing is a computer programming technique used in conjunction with open addressing in hash tables to resolve hash collisions, by using a secondary hash of the key as an offset when a collision occurs. Double hashing with open addressing is a classical data structure on a table T. The double hashing technique uses one hash value as an index into the table and then repeatedly steps forward an interval until the desired value is located, an empty location is reached, or the entire table has been searched; but this interval is set by a second, independent hash function. Unlike the alternative collision-resolution methods of linear probing and quadratic probing, the interval depends on the data, so that values mapping to the same location have different bucket sequences; this minimizes repeated collisions and the effects of clustering. Given two random, uniform, and independent hash functions h_1 and h_2, the ith location in the bucket sequence for value k in a hash table of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Computer Programming
Computer programming or coding is the composition of sequences of instructions, called computer program, programs, that computers can follow to perform tasks. It involves designing and implementing algorithms, step-by-step specifications of procedures, by writing source code, code in one or more programming languages. Programmers typically use high-level programming languages that are more easily intelligible to humans than machine code, which is directly executed by the central processing unit. Proficient programming usually requires expertise in several different subjects, including knowledge of the Domain (software engineering), application domain, details of programming languages and generic code library (computing), libraries, specialized algorithms, and Logic#Formal logic, formal logic. Auxiliary tasks accompanying and related to programming include Requirements analysis, analyzing requirements, Software testing, testing, debugging (investigating and fixing problems), imple ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Bloom Filter
In computing, a Bloom filter is a space-efficient probabilistic data structure, conceived by Burton Howard Bloom in 1970, that is used to test whether an element is a member of a set. False positive matches are possible, but false negatives are not – in other words, a query returns either "possibly in set" or "definitely not in set". Elements can be added to the set, but not removed (though this can be addressed with the counting Bloom filter variant); the more items added, the larger the probability of false positives. Bloom proposed the technique for applications where the amount of source data would require an impractically large amount of memory if "conventional" error-free hashing techniques were applied. He gave the example of a hyphenation algorithm for a dictionary of 500,000 words, out of which 90% follow simple hyphenation rules, but the remaining 10% require expensive disk accesses to retrieve specific hyphenation patterns. With sufficient core memory, an error- ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
2-choice Hashing
2-choice hashing, also known as 2-choice chaining, is "a variant of a hash table in which keys are added by hashing with two hash functions. The key is put in the array position with the fewer (colliding) keys. Some collision resolution scheme is needed, unless keys are kept in buckets. The average-case cost of a successful search is O(2 + (m - 1) / n), where m is the number of keys and n is the size of the array. The most collisions is \log_2 \ln n + \theta(m/n) with high probability." How it works 2-choice hashing utilizes two hash functions ''h''1(''x'') and ''h''2(''x'') which work as hash functions are expected to work (i.e. mapping integers from the universe into a specified range). The two hash functions should be independent and have no correlation to each other. Having two hash functions allows any key ''x'' to have up to two potential locations to be stored based on the values of the respective outputs, ''h''1(''x'') and ''h''2(''x''). It is important to note that, a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Cuckoo Hashing
Cuckoo hashing is a scheme in computer programming for resolving hash collisions of values of hash functions in a table, with worst-case constant lookup time. The name derives from the behavior of some species of cuckoo, where the cuckoo chick pushes the other eggs or young out of the nest when it hatches in a variation of the behavior referred to as brood parasitism; analogously, inserting a new key into a cuckoo hashing table may push an older key to a different location in the table. History Cuckoo hashing was first described by Rasmus Pagh and Flemming Friche Rodler in a 2001 conference paper. The paper was awarded the European Symposium on Algorithms Test-of-Time award in 2020. Operations Cuckoo hashing is a form of open addressing in which each non-empty cell of a hash table contains a key or key–value pair. A hash function is used to determine the location for each key, and its presence in the table (or the value associated with it) can be found by examining that c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Forward Difference
A finite difference is a mathematical expression of the form . Finite differences (or the associated difference quotients) are often used as approximations of derivatives, such as in numerical differentiation. The difference operator, commonly denoted \Delta, is the operator that maps a function to the function \Delta /math> defined by \Delta x) = f(x+1)-f(x). A difference equation is a functional equation that involves the finite difference operator in the same way as a differential equation involves derivatives. There are many similarities between difference equations and differential equations. Certain recurrence relations can be written as difference equations by replacing iteration notation with finite differences. In numerical analysis, finite differences are widely used for approximating derivatives, and the term "finite difference" is often used as an abbreviation of "finite difference approximation of derivatives". Finite differences were introduced by Brook Taylor ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Tetrahedral Number
A tetrahedral number, or triangular pyramidal number, is a figurate number that represents a pyramid (geometry), pyramid with a triangular base and three sides, called a tetrahedron. The th tetrahedral number, , is the sum of the first triangular numbers, that is, : Te_n = \sum_^n T_k = \sum_^n \frac = \sum_^n \left(\sum_^k i\right) The tetrahedral numbers are: :1, 4, 10, 20 (number), 20, 35 (number), 35, 56 (number), 56, 84 (number), 84, 120 (number), 120, 165 (number), 165, 220 (number), 220, ... Formula The formula for the th tetrahedral number is represented by the 3rd rising factorial of divided by the factorial of 3: :Te_n= \sum_^n T_k = \sum_^n \frac = \sum_^n \left(\sum_^k i\right)=\frac = \frac The tetrahedral numbers can also be represented as binomial coefficients: :Te_n=\binom. Tetrahedral numbers can therefore be found in the fourth position either from left or right in Pascal's triangle. Proofs of formula This proof uses the fact that the th triangular num ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
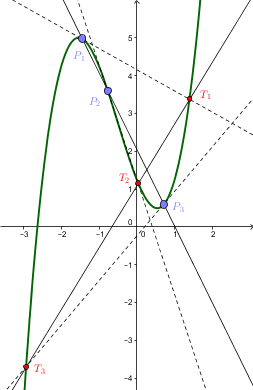
Cubic Function
In mathematics, a cubic function is a function of the form f(x)=ax^3+bx^2+cx+d, that is, a polynomial function of degree three. In many texts, the ''coefficients'' , , , and are supposed to be real numbers, and the function is considered as a real function that maps real numbers to real numbers or as a complex function that maps complex numbers to complex numbers. In other cases, the coefficients may be complex numbers, and the function is a complex function that has the set of the complex numbers as its codomain, even when the domain is restricted to the real numbers. Setting produces a cubic equation of the form :ax^3+bx^2+cx+d=0, whose solutions are called roots of the function. The derivative of a cubic function is a quadratic function. A cubic function with real coefficients has either one or three real roots ( which may not be distinct); all odd-degree polynomials with real coefficients have at least one real root. The graph of a cubic function always has a single ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Triangular Number
A triangular number or triangle number counts objects arranged in an equilateral triangle. Triangular numbers are a type of figurate number, other examples being square numbers and cube numbers. The th triangular number is the number of dots in the triangular arrangement with dots on each side, and is equal to the sum of the natural numbers from 1 to . The first 100 terms sequence of triangular numbers, starting with the 0th triangular number, are Formula The triangular numbers are given by the following explicit formulas: where \textstyle is notation for a binomial coefficient. It represents the number of distinct pairs that can be selected from objects, and it is read aloud as " plus one choose two". The fact that the nth triangular number equals n(n+1)/2 can be illustrated using a visual proof. For every triangular number T_n, imagine a "half-rectangle" arrangement of objects corresponding to the triangular number, as in the figure below. Copying this arrangement ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Michael N
Michael may refer to: People * Michael (given name), a given name * he He ..., a given name * Michael (surname), including a list of people with the surname Michael Given name * Michael (bishop elect)">Michael (surname)">he He ..., a given name * Michael (surname), including a list of people with the surname Michael Given name * Michael (bishop elect), English 13th-century Bishop of Hereford elect * Michael (Khoroshy) (1885–1977), cleric of the Ukrainian Orthodox Church of Canada * Michael Donnellan (fashion designer), Michael Donnellan (1915–1985), Irish-born London fashion designer, often referred to simply as "Michael" * Michael (footballer, born 1982), Brazilian footballer * Michael (footballer, born 1983), Brazilian footballer * Michael (footballer, born 1993), Brazilian footballer * Michael (footballer, born February 1996), Brazilian footballer * Michael (footballer, born March 1996), Brazilian footballer * Michael (footballer, born 1999), Brazilian footballe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Open Addressing
Open addressing, or closed hashing, is a method of Hash table#Collision resolution, collision resolution in hash tables. With this method a hash collision is resolved by probing, or searching through alternative locations in the array (the ''probe sequence'') until either the target record is found, or an unused array slot is found, which indicates that there is no such key in the table. Well-known probe sequences include: ; Linear probing : in which the interval between probes is fixed — often set to 1. ; Quadratic probing : in which the interval between probes increases linearly (hence, the indices are described by a quadratic function). ; Double hashing : in which the interval between probes is fixed for each record but is computed by another hash function. The main trade offs between these methods are that linear probing has the best Locality of reference, cache performance but is most sensitive to Primary clustering, clustering, while double hashing has poor cache perf ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Universal Hash
In mathematics and computing, universal hashing (in a randomized algorithm or data structure) refers to selecting a hash function at random from a family of hash functions with a certain mathematical property (see definition below). This guarantees a low number of collisions in expectation, even if the data is chosen by an adversary. Many universal families are known (for hashing integers, vectors, strings), and their evaluation is often very efficient. Universal hashing has numerous uses in computer science, for example in implementations of hash tables, randomized algorithms, and cryptography. Introduction Assume we want to map keys from some universe U into m bins (labelled = \). The algorithm will have to handle some data set S \subseteq U of , S, =n keys, which is not known in advance. Usually, the goal of hashing is to obtain a low number of collisions (keys from S that land in the same bin). A deterministic hash function cannot offer any guarantee in an adversarial sett ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Primary Clustering
In computer programming, primary clustering is a phenomenon that causes performance degradation in linear-probing hash tables. The phenomenon states that, as elements are added to a linear probing hash table, they have a tendency to cluster together into long runs (i.e., long contiguous regions of the hash table that contain no free slots). If the hash table is at a load factor of 1 - 1/x for some parameter x \ge 2 , then the expected length of the run containing a given element u is \Theta(x^2). This causes insertions and negative queries to take expected time \Theta(x^2) in a linear-probing hash table. Causes of primary clustering Primary clustering has two causes: * Winner keeps winning: The longer that a run becomes, the more likely it is to accrue additional elements. This causes a positive feedback loop that contributes to the clustering effect. However, this alone would not cause the quadratic blowup. * Joining of runs: A single insertion may not only increase the length ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |