|
Device Driver Synthesis And Verification
Device drivers are programs which allow software or higher-level computer programs to interact with a computer hardware, hardware device. These software components act as a link between the devices and the operating systems, communicating with each of these systems and executing commands. They provide an abstraction layer for the software above and also mediate the communication between the operating system kernel and the devices below. Usually the operating systems comes with a support for the common device drivers and usually the hardware vendors provide the device driver for their hardware devices for most platforms. The aggressive scaling of the hardware devices and the complex software components has made the device driver development process cumbersome and complex. When the size and Function (engineering), functionality of the drivers started increasing the device drivers became a key factor in defining the reliability (engineering), reliability of the system. This has cre ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Linux
Linux ( or ) is a family of open-source Unix-like operating systems based on the Linux kernel, an operating system kernel first released on September 17, 1991, by Linus Torvalds. Linux is typically packaged as a Linux distribution, which includes the kernel and supporting system software and libraries, many of which are provided by the GNU Project. Many Linux distributions use the word "Linux" in their name, but the Free Software Foundation uses the name "GNU/Linux" to emphasize the importance of GNU software, causing some controversy. Popular Linux distributions include Debian, Fedora Linux, and Ubuntu, the latter of which itself consists of many different distributions and modifications, including Lubuntu and Xubuntu. Commercial distributions include Red Hat Enterprise Linux and SUSE Linux Enterprise. Desktop Linux distributions include a windowing system such as X11 or Wayland, and a desktop environment such as GNOME or KDE Plasma. Distributions inten ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Daniel Kroening
Daniel Kroening (born 6 November 1975) is a German computer scientist, Professor in computer science at the University of Oxford, and Chief Science Officer at the company he co-founded, Diffblue Ltd. He is a fellow of Magdalen College. Early life Kroening was born in Mainz, Rhineland-Palatinate, Germany. He attended Marie-Therese-Gymnasium, Erlangen, Bavaria from 1986 to 1990 and Rotenbühl Gymnasium, Saarbrücken, Saarland from 1990 to 1995. Kroening's early work in those highschool years includes implementations of data transfer protocols and a bulletin board system (BBS) software package with Internet access management for small ISPs, which he released under free/open source licenses. In 1992, Kroening joined Handshake e.V., a local non-profit ISP. From 1993, he hosted and operated Handshake's main BBS system and by the end of 1994, it was running his software. Since 1996, he was also involved in Handshake's executive management. After high school, Kroening completed his compul ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
BLAST Model Checker
The Berkeley Lazy Abstraction Software verification Tool (BLAST) is a software model checking tool for C programs. The task addressed by BLAST is the need to check whether software satisfies the behavioral requirements of its associated interfaces. BLAST employs counterexample-driven automatic abstraction refinement to construct an abstract model that is then model-checked for safety properties. The abstraction is constructed on the fly, and only to the requested precision. Achievements BLAST came first in the category DeviceDrivers64 in the 1st Competition on Software Verification (2012) that was held at TACAS 2012 in Tallinn. BLAST came third (category DeviceDrivers64) in the 2nd Competition on Software Verification (2013) that was held at TACAS 2013 in Rome. BLAST came first in the category DeviceDrivers64 in the 3rd Competition on Software Verification (2014) that was held at TACAS 2014 in Grenoble lat, Gratianopolis , commune status = Prefecture and commune , ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Metacompiler
In computer science, a compiler-compiler or compiler generator is a programming tool that creates a parser, interpreter, or compiler from some form of formal description of a programming language and machine. The most common type of compiler-compiler is more precisely called a parser generator. It only handles syntactic analysis. The input of a parser generator is a grammar file, typically written in Backus–Naur form (BNF) or extended Backus–Naur form (EBNF) that defines the syntax of a target programming language. The output is the source code of a parser for the programming language. The output of the (compiled) parser source code is a parser. It may be either standalone or embedded. This parser takes as an input the source code of the target programming language source and performs some action or outputs an abstract syntax tree (AST). Parser generators do not handle the semantics of the AST, or the generation of machine code for the target machine."A Syntax Directe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Memory Safety
safety is the state of being protected from various software bugs and security vulnerabilities when dealing with memory access, such as buffer overflows and dangling pointers. For example, Java is said to be memory-safe because its runtime error detection checks array bounds and pointer dereferences. In contrast, C and C++ allow arbitrary pointer arithmetic with pointers implemented as direct memory addresses with no provision for bounds checking, and thus are potentially memory-unsafe. History Memory errors were first considered in the context of resource management and time-sharing systems, in an effort to avoid problems such as fork bombs. Developments were mostly theoretical until the Morris worm, which exploited a buffer overflow in fingerd. The field of computer security developed quickly thereafter, escalating with multitudes of new attacks such as the return-to-libc attack and defense techniques such as the non-executable stack and address space layout randomizati ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Type Safety
In computer science, type safety and type soundness are the extent to which a programming language discourages or prevents type errors. Type safety is sometimes alternatively considered to be a property of facilities of a computer language; that is, some facilities are type-safe and their usage will not result in type errors, while other facilities in the same language may be type-unsafe and a program using them may encounter type errors. The behaviors classified as type errors by a given programming language are usually those that result from attempts to perform operations on values that are not of the appropriate data type, e.g., adding a string to an integer when there's no definition on how to handle this case. This classification is partly based on opinion. Type enforcement can be static, catching potential errors at compile time, or dynamic, associating type information with values at run-time and consulting them as needed to detect imminent errors, or a combination of both ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SLAM Project
The SLAM project, which was started in 1999 by Thomas Ball and Sriram Rajamani of Microsoft Research, aimed at verifying software safety properties using model checking techniques. It was implemented in OCaml, and has been used to find many bugs in Windows Device Drivers. It is distributed as part of the Microsoft Windows Driver Foundation development kit as the Static Driver Verifier (SDV). "SLAM originally was an acronym but we found it too cumbersome to explain. We now prefer to think of 'slamming' the bugs in a program."Ball, Thomas; Cook, Byron; Levin, Vladimir; and Rajamani, Sriram K.''SLAM and Static Driver Verifier: Technology Transfer of Formal Methods inside Microsoft'' Lecture Notes in Computer Science (LNCS), Vol. 2999: Boiten, Eerke A.; Derrick, John; and Smith, Graeme; eds.; ''Fourth International Conference on Integrated Formal Methods (IFM 2004), 4–7 April 2004, Canterbury, GB'', Springer, Berlin/Heidelberg, pp. 1–20 It initially stood for "software (specificatio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Technical Support
Technical support (abbreviated as tech support) is a call centre type customer service provided by companies to advise and assist registered users with issues concerning their technical products. Traditionally done on the phone, technical support can now be conducted online or through chat. At present, most large and mid-size companies have outsourced their tech support operations. Many companies provide discussion boards for users of their products to interact; such forums allow companies to reduce their support costs without losing the benefit of customer feedback. Outsourcing technical support With the increasing use of technology in modern times, there is a growing requirement to provide technical support. Many organizations locate their technical support departments or call centers in countries or regions with lower costs. Dell was amongst the first companies to outsource their technical support and customer service departments to India in 2001. There has also been a grow ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Specifications
A specification often refers to a set of documented requirements to be satisfied by a material, design, product, or service. A specification is often a type of technical standard. There are different types of technical or engineering specifications (specs), and the term is used differently in different technical contexts. They often refer to particular documents, and/or particular information within them. The word ''specification'' is broadly defined as "to state explicitly or in detail" or "to be specific". A requirement specification is a documented requirement, or set of documented requirements, to be satisfied by a given material, design, product, service, etc. It is a common early part of engineering design and product development processes in many fields. A functional specification is a kind of requirement specification, and may show functional block diagrams. A design or product specification describes the features of the ''solutions'' for the Requirement Specification, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
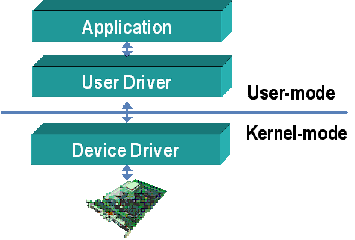
Kernel Mode
In computer science, hierarchical protection domains, often called protection rings, are mechanisms to protect data and functionality from faults (by improving fault tolerance) and malicious behavior (by providing computer security). Computer operating systems provide different levels of access to resources. A protection ring is one of two or more hierarchical ''levels'' or ''layers'' of privilege within the architecture of a computer system. This is generally hardware-enforced by some CPU architectures that provide different CPU modes at the hardware or microcode level. Rings are arranged in a hierarchy from most privileged (most trusted, usually numbered zero) to least privileged (least trusted, usually with the highest ring number). Ring 0 is the level with the most privileges and allows direct interaction with the physical hardware such as certain CPU functionality and chips on the motherboard. Special call gates between rings are provided to allow an outer ring to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Windows XP
Windows XP is a major release of Microsoft's Windows NT operating system. It was released to manufacturing on August 24, 2001, and later to retail on October 25, 2001. It is a direct upgrade to its predecessors, Windows 2000 for high-end and business users and Windows Me for home users, available for any devices running Windows NT 4.0, Windows 98, Windows 2000 and Windows Me that meet the new Windows XP system requirements. Development of Windows XP began in the late 1990s under the codename "Neptune", built on the Windows NT kernel explicitly intended for mainstream consumer use. An updated version of Windows 2000 was also initially planned for the business market. However, in January 2000, both projects were scrapped in favor of a single OS codenamed "Whistler", which would serve as a single platform for both consumer and business markets. As a result, Windows XP is the first consumer edition of Windows not based on the Windows 95 kernel and MS-DOS. Windows XP removed supp ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
.jpg)